Malicious Updates & Operating System Vulnerabilities & SQL Injection
1/10
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
11 Terms
Software Updates
Keeping your operating system and applications up to date is crucial for maintaining security.
Often include important bug fixes and security patches that protect against vulnerabilities in older code.
However, not every update is equally secure, and installing updates is akin to adding a new application
May inadvertently allow attackers to embed malicious code in the update.
To minimize risks during the update process, follow best practices:
Always maintain a known-good backup to restore the system if something goes wrong.
Install updates only from trusted sources to ensure their integrity.
Update Example
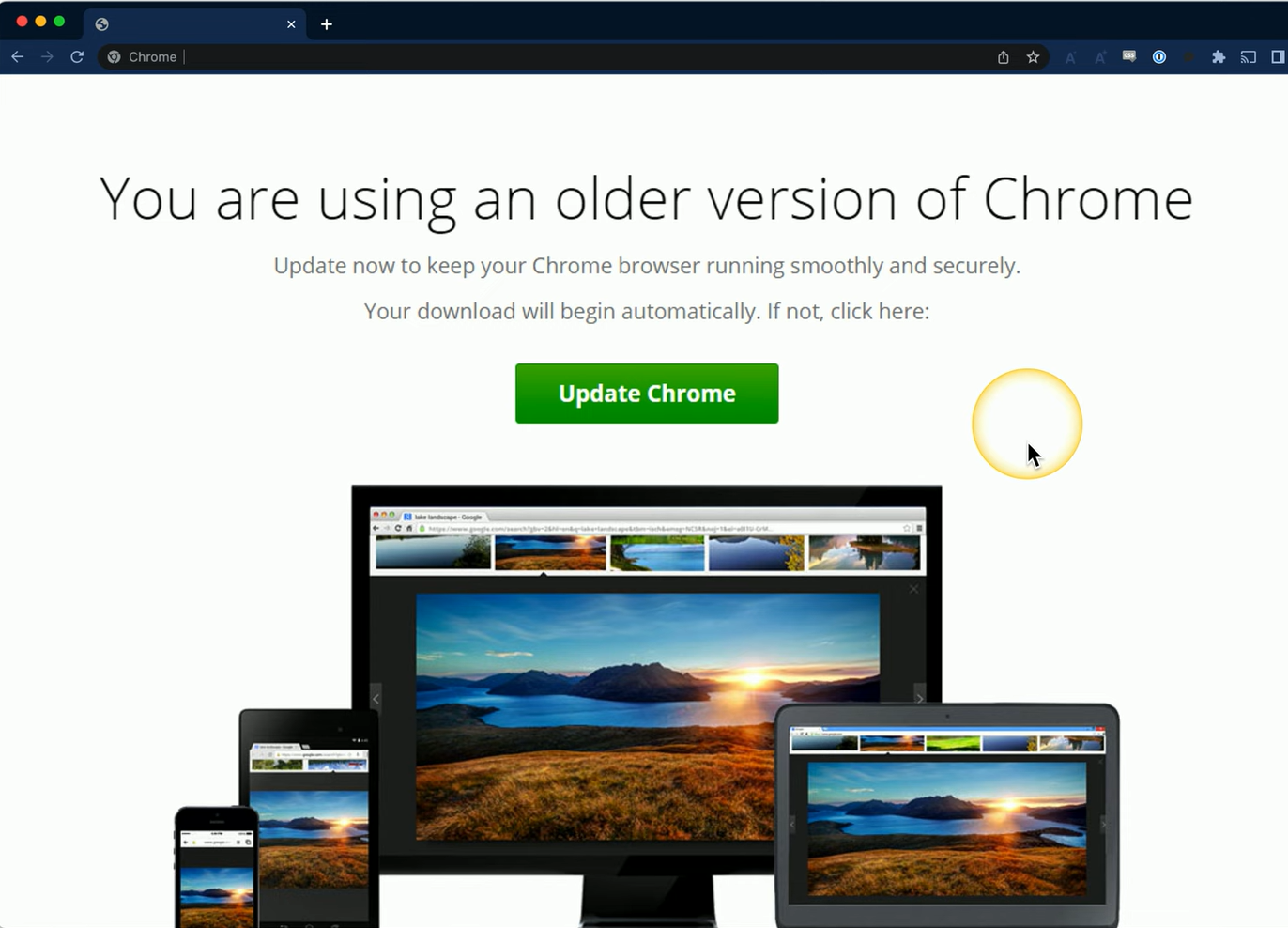
When you start Chrome, a message might appear saying
"You are using an older version. Update now to keep your Chrome browser running smoothly and securely. Your download will begin automatically. If not, click here."
When this message appears before you visit any websites, it seems trustworthy.
However, if this message appears after clicking a link from a Google search or visiting a website, it's essential to be cautious.
In such cases, extra checks should be performed before clicking the "Update Chrome" button, as it could be a phishing attempt or a malicious pop-up disguised as a legitimate update.
Always verify the source of the message and ensure it is from a trusted source before proceeding.
Downloading & Updating
It's important to ensure that the source of the file is trusted. Often, updates are installed from files downloaded from third-party websites, which means it's crucial to verify the website you're downloading from.
A random pop-up during web browsing claiming to offer an update may not be legitimate
Always visit the developer’s official site directly to download updates, as this increases trust in the patch.
To ensure authenticity, many operating systems require apps to be digitally signed by the developer. The operating system validates this signature, which gives you a higher level of confidence that the update is legitimate.
Never trust random update buttons or files that appear unexpectedly.
Do not disable your security controls, as these help protect you from potential malicious updates.
Automatic Updates
Allow an app to update itself
Typically with built-in security checks and digital signatures to verify the update's legitimacy.
While you may not see the digital signature, the update process automatically performs the verification, giving a high level of trust as the update comes directly from the developer.
However, there is no 100% guarantee that the code being updated is legitimate.
A notable example is the SolarWinds Orion supply chain attack, reported in December 2020, where attackers gained access to the SolarWinds development system and inserted malicious code into their updates.
These compromised updates were then distributed to hundreds of government agencies and companies, giving attackers access to sensitive systems.
Operating Systems
A foundational platform that everyone uses, making it a prime target for finding vulnerabilities.
Are extremely complex, with millions of lines of code, and the larger the codebase, the greater the chance that security vulnerabilities will exist.
The OS you're using right now likely contains many security weaknesses, these vulnerabilities might not yet be discovered.
A Month of OS Updates
Each month, Windows releases updates on Patch Tuesday (the second Tuesday of every month), addressing various security vulnerabilities. On May 9th, 2023..
8 Elevation of Privilege Vulnerabilities
4 Security Feature Bypass Vulnerabilities
8 Information Disclosure Vulnerabilities
5 Denial of Service Vulnerabilities
1 Spoofing Vulnerability
Might seem significant, but the April 2023 Patch Tuesday had almost 100 patches. The number of vulnerabilities and the need for constant updates are both substantial.
Best Practices For OS Vulnerabilities
Plan for regular updates: Implement monthly or on-demand updates to address vulnerabilities as soon as they are discovered.
When a previously unknown vulnerability is announced, attackers will begin working to exploit it. It's a race to apply the patch before attackers can reverse-engineer and exploit the weakness.
In large, complex environments with hundreds or thousands of devices, it’s wise to test patches in a controlled environment before deploying them into production to ensure they don't cause issues elsewhere.
Some patches, especially those affecting core parts of the OS, may require a reboot to fully apply the fix.
Always save critical data and have a fallback plan in case issues arise post-patch. Having a backup of the system ensures you can revert if the update causes problems.
Code Injection
A common application attack where an attacker inserts malicious code into an application's input fields.
This vulnerability arises from poor programming practices, where input data isn't properly validated or sanitized.
Developers must implement checks in their code to ensure that only valid input is processed and to prevent malicious data from being injected.
Can affect various data types, including HTML, SQL, XML, and LDAP, among others, and can lead to serious security risks if not properly managed.
SQL Injection
A common attack where an attacker inserts malicious SQL queries into an application's input fields.
SQL, or Structured Query Language, is the standard language for managing relational databases.
When an application uses user input directly in database queries without proper validation, an attacker can manipulate the input to execute their own queries, potentially accessing, modifying, or deleting data.
Are often easy to exploit and can be done through a web browser by injecting malicious data into existing input fields.
Building a SQL Injection
Suppose a website uses a query like this to fetch data from a database based on a user's input:
"SELECT * FROM users WHERE name = '" + userName + "'"; If a user inputs "Professor" into the application, the query looks like:
"SELECT * FROM users WHERE name = 'Professor'";An attacker can manipulate the input by adding malicious SQL code. For example, the input might be:
Professor' OR '1' = '1
Since 1 = 1 is always true, this query will retrieve all records from the users table, bypassing the security and returning data from the database that was not meant to be exposed.
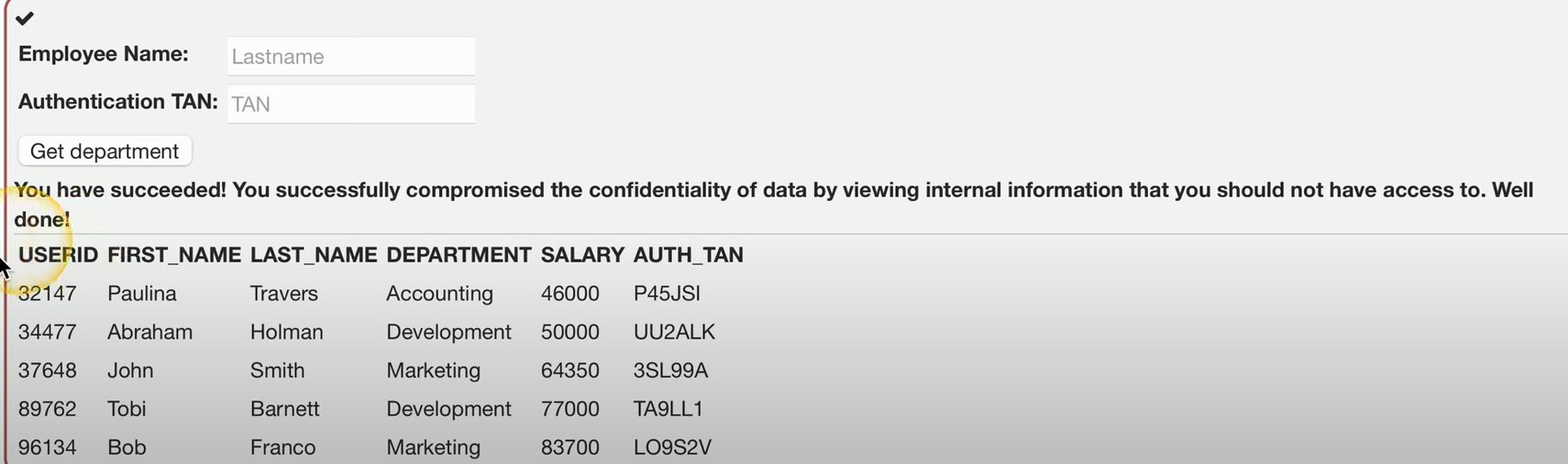
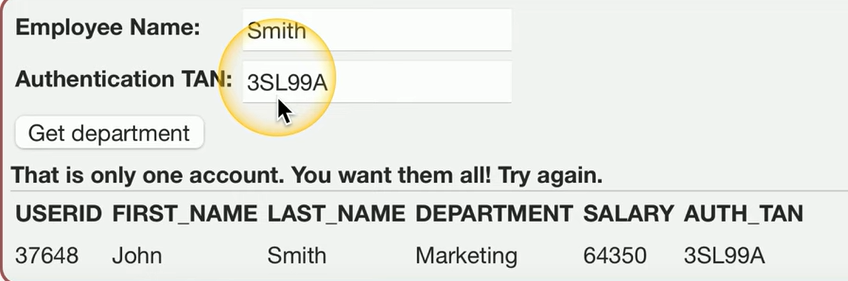
Example of SQL Injection
In this example of SQL injection, the application normally takes two pieces of information: an employee name (e.g., Smith) and a transaction authentication number (e.g., 3SL99A).
This query would return the department information for the employee Smith with the provided transaction number.
Now, if an attacker manipulates the input and injects the following into the transaction number field:
' OR '1' = '1
The injected part, ' OR '1' = '1, makes the OR '1' = '1' condition always true, which means the database will return all records for the employees table, bypassing the intended query restrictions. As a result, the attacker can view all the information in the database, not just the record for Smith with the specified transaction number.