Cryptography
When is the oldest date showing the use of cryptography?
1900 BC
What is the Caesar cipher?
transposition/shifting of the letters of the alphabet + substitution
1/25
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
26 Terms
When is the oldest date showing the use of cryptography?
1900 BC
What is the Caesar cipher?
transposition/shifting of the letters of the alphabet + substitution
What is the main use of cryptography?
protecting the confidentiality of messages
What does steganography do?
hides the presence of a message
What is an example of a rotor machine?
Enigma machine
What is symmetric encryption?
The encryption and decryption happen using the same (secret) key on a piece of information x. This ensures its confidentiality.
What is asymmetric encryption?
Encryption where the encryption and decryption use two different keys.
What is an example of symmetric encryption?
Advanced Encryption Standard
How does asymmetric encryption work?
Each user has a pair of keys - one public and one private.
The sender encrypts the info x with the public key of the recipient.
The recipient decrypts with its private key
What are the main applications of asymmetric encryption?
symmetric key distribution and digital signatures
What are some examples of asymmetric encryption?
RSA, DSA
How does are public and private keys generated in RSA?
The sender creates two keys by:
Choosing two prime numbers p and q
Computing N where N = p x q
Computing T where T = (p-1) x (q-1)
Picking e and d such that (e x d ) mod T = 1
Public key = (N, e)
Private key = (N, d)
How is a message encrypted and decrypted in RSA?
To encrypt the message it is: (message)^e mod N where (N, e) is the public key of the recipient.
To decrypt the message it is (encryptedMessage)^d mod N where (N,d) is the private key of the recipient.
What formula do you use to calculate the number of keys needed for bidirectional communication with asymmetric encryption?
2 x number of nodes
What formula do you use to calculate the number of keys needed for bidirectional communication with symmetric encryption?
(n(n-1))/2
where n is the number of nodes
How is a message authenticated?
Using a digital signature that works by:
The sender encryption information x with their private key.
The recipient decrypting the message with the senders public key.
If they match the message is authenticated
What are example algorithms to use with digital signatures / authentications?
RSA, DSA
What is the need for digital signatures?
they guarantee the integrity of the sent message, source authentication, and non-repudiation
For symmetric encryption how can the secret keys be shared?
• Public-key cryptography
• Diffie-Hellman key exchange protocol
How does key distribution with public key encryption work?
Alice sends her public key (PUₐ) and identity to Bob.
Bob generates a secret key (Kₛ) for secure communication.
Bob encrypts Kₛ using Alice’s public key: Encrypt(Kₛ, PUₐ).
Alice receives the encrypted message and decrypts it with her private key to retrieve Kₛ.
➡ This allows both parties to share a symmetric secret key securely.
How can a man-in-the-middle (MITM) attack be carried out with public key encryption key distribution?
Charlie (the attacker) intercepts Alice’s public key and ID intended for Bob.
Charlie sends his own public key (PU꜀) and Alice’s ID to Bob, pretending to be Alice.
Bob encrypts the secret key Kₛ with PU꜀ (Charlie’s key), thinking it's Alice’s.
Charlie decrypts the message with his private key to obtain Kₛ.
Charlie then re-encrypts Kₛ with Alice’s actual public key and sends it to her.
➡ Now Alice, Bob, and Charlie all share the same secret key Kₛ — allowing Charlie to eavesdrop.
What is the purpose of the Diffie-Helmen key exchange protocol?
to enable two users to securely exchange a key that can then be used for subsequent symmetric encryption of messages
What does the effectiveness of the Diffie-helman key exchange protocol depend on?
the difficulty of computing discrete logarithms
How does the Diffie-Hellman key exchange work?
Here:
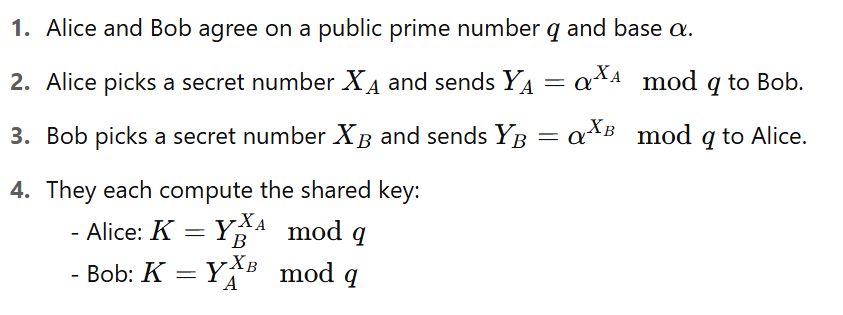
How can a man-in-the-middle attack occur in the Diffie-Hellman protocol?
An attacker intercepts the public keys and sends their own to both parties.
Alice thinks she’s talking to Bob but is talking to the attacker.
The attacker forms two separate shared keys with Alice and Bob, allowing them to read and modify messages.
How can man-in-the-middle attacks be prevented in Diffie-Hellman?
The solution is for the sender to put the signature • But to verify the signature you need the public key of the sender which is acquired using the Public Key Infastructure.