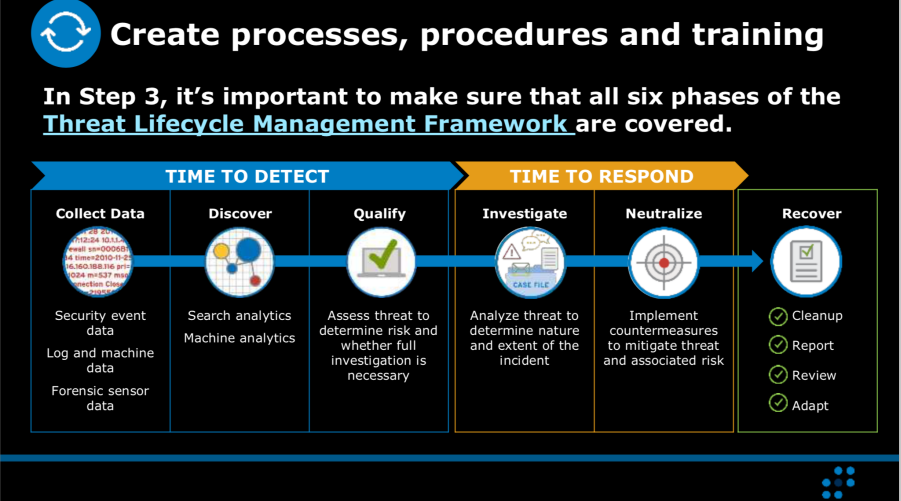
SECURITY OPERATIONS CENTER (SOC) ( Chapter 5)
1/28
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
29 Terms
A centralized function within an organization employing people, processes, and technology to continuously monitor and improve an organization's security posture while preventing, detecting, analyzing, and responding to cybersecurity incidents
Security Operations Center (SOC)
What Makes a SOC Effective?
people, processes, and technology
work primarily in the monitoring and detection phases of a SO
Security analysts
Incident responder tasks may include:
Conducting deeper analysis of suspicious security events using:
Search analytics capabilities •
Threat intelligence sources
Basic forensics techniques
Malware analysis tools
Performing response activities whenever an incident necessitates •
Keeping management apprised of the status of incident response efforts
is typically someone within the security organization with a deep understanding of the organization’s security program and infrastructure.
Security architect
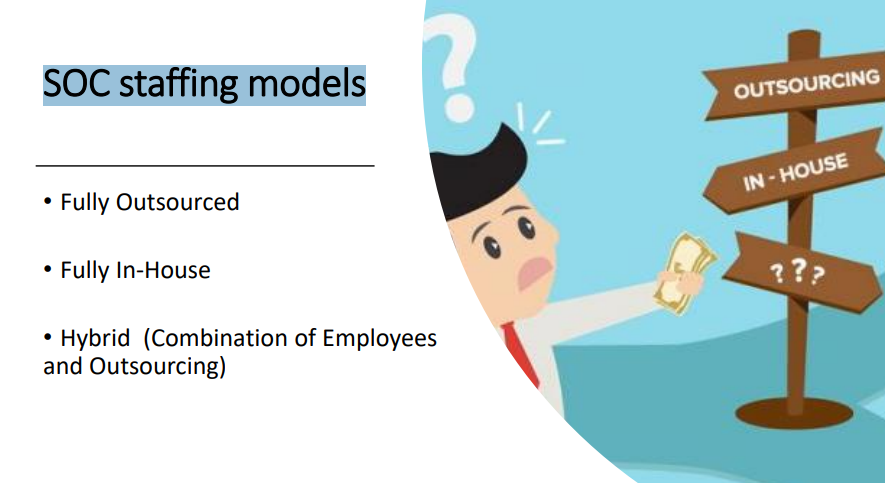
SOC staffing models
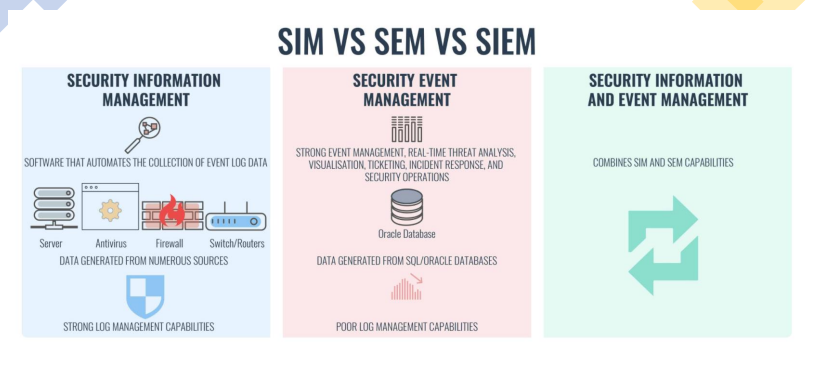
is the collection, monitoring, and analysis of security-related data from computer logs. Also referred to as log management.
Security Information Management (SIM)
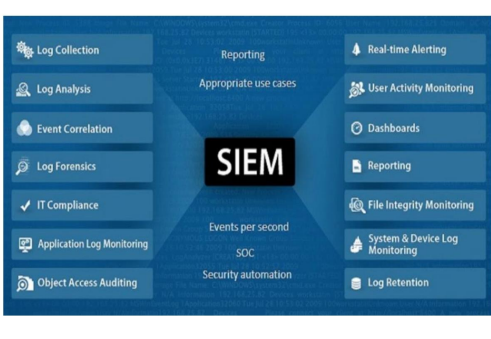
the practice of network event management including real-time threat analysis, visualization, and incident response.
Security Event Management (SEM)
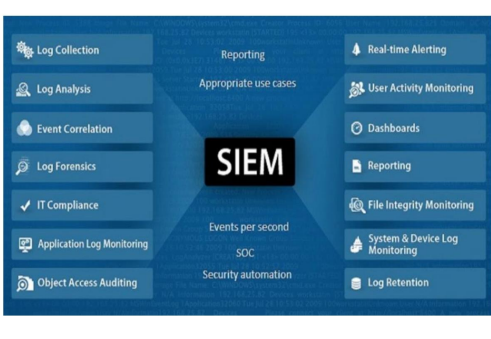
SIM vs SEM vs SIEM
One of the most competitive offerings on the market.
SolarWinds Security Event Manager (SEM)
One of the most popular SIEM management solutions in the world.
Splunk Enterprise Security
LogRhythm have long established themselves as pioneers within the SIEM solution sector.
LogRhythm NextGen SIEM Platform
a traditional SIEM product with built-in intrusion detection, behavioral monitoring, and vulnerability assessment.
AT&T Cybersecurity AlienVault Unified Security Management

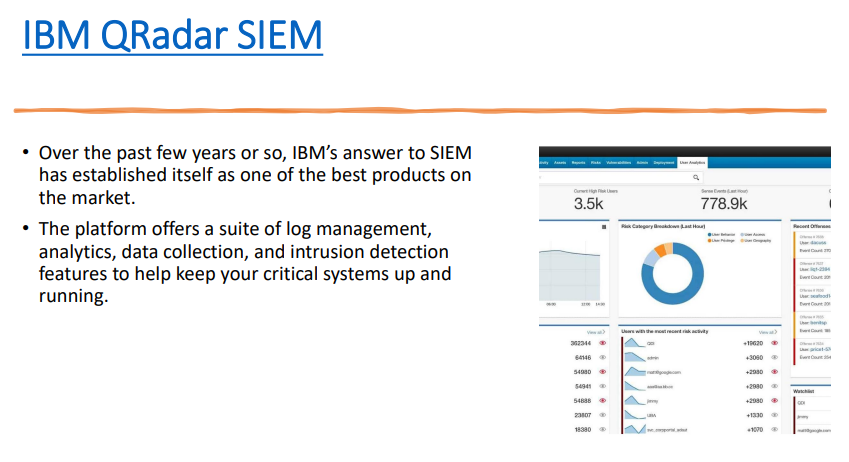
The platform offers a suite of log management, analytics, data collection, and intrusion detection features to help keep your critical systems up and running.
IBM QRadar SIEM
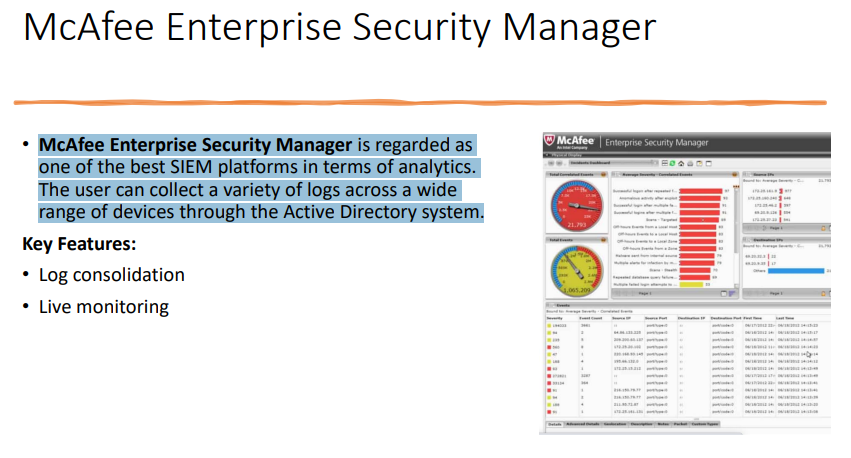
one of the best SIEM platforms in terms of analytics. The user can collect a variety of logs across a wide range of devices through the Active Directory system.
McAfee Enterprise Security Manager
THE BEST SIEM VENDORS

a free and open Linux distribution for threat hunting, enterprise security monitoring, and log management
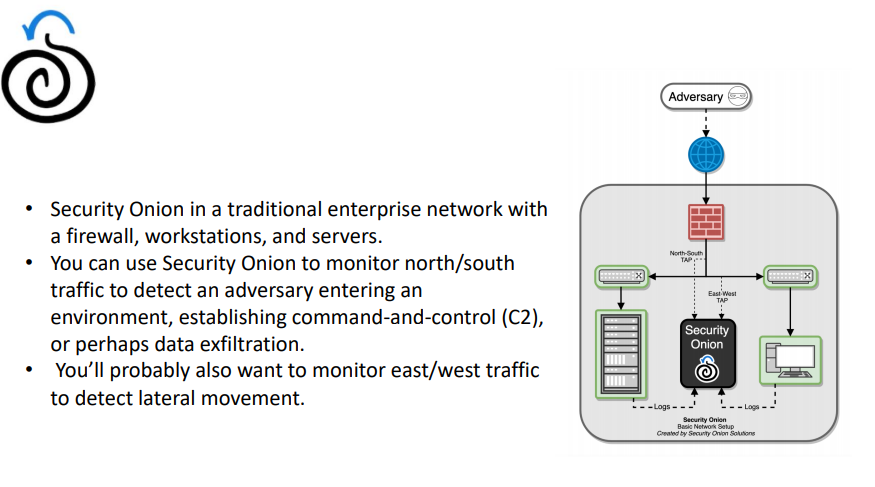
Security Onion
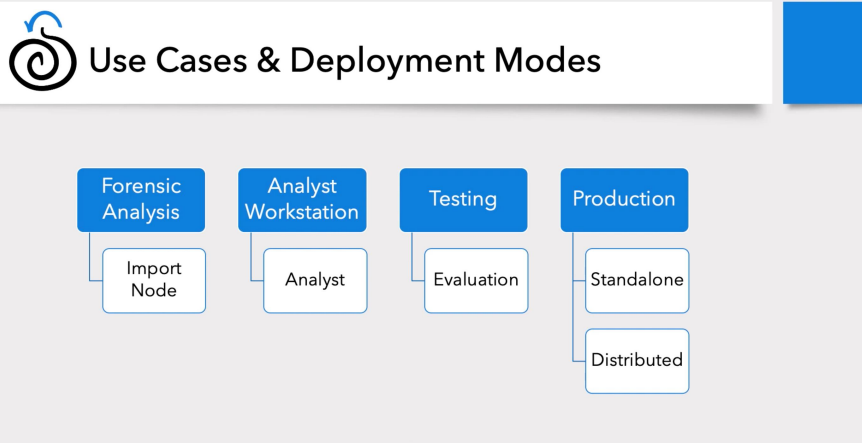
USE CASE AND DEPLOYMENT MODES
7 STEPS TO BUILDING A SOC WITH LIMITED RESOURCES