1_Basic Device Configuration
1/166
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
167 Terms
IP address, subnet mask
To prepare a switch for remote management access, the switch must be configured with an _____ and a _____.
default gateway
To manage the switch from a remote network, the switch must be configured with a _____.
switch virtual interface (SVI)
the _____ on S1 should be assigned an IP address.
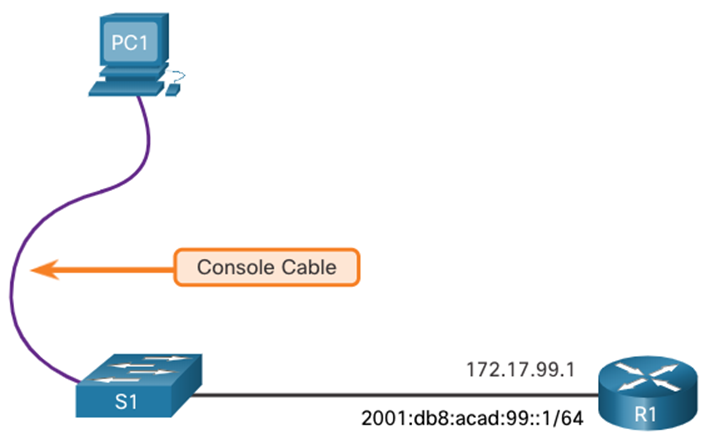
console cable
is used to connect to a PC so that the switch can be initially configured.
VLAN 1
By default, the switch is configured to have its management controlled through _____
VLAN 1
All ports are assigned to _____ by default.
management VLAN
For security purposes, it is considered a best practice to use a VLAN other than VLAN 1 for the _____.
configure the management interface,
configure the default gateway,
verify configuration
3 steps for switch svi configuration
VLAN interface configuration mode,
management SVI
Step 1: Configure the Management Interface: From _____, an IPv4 address and subnet mask is applied to the _____ of the switch.
SVI for VLAN 99
The _____ will not appear as “up/up” until VLAN 99 is created and there is a device connected to a switch port associated with VLAN 99.
IPv6
The switch may need to be configured for _____.
S1(config)# interface vlan 99
Enter interface configuration mode for the SVI.
S1(config-if)# ip address ip address subnet mask
Configure the management interface IPv4/IPV6 address.
S1(config-if)# no shutdown
Enable the management interface
S1(config-if)# end
Return to the privileged EXEC mode.
S1# copy running-config startup-config
Save the running config to the startup config.
router advertisement (RA) message
A switch will receive its default gateway information from a _____.
IPv6 default gateway
the switch does not require an _____.
show ip interface brief, show ipv6 interface brief
2 commands that are useful for determining the status of both physical and virtual interfaces.
route Layer 3 packets
An IP address applied to the SVI is only for remote management access to the switch; this does not allow the switch to _____.
Full-duplex communication
increases bandwidth efficiency by allowing both ends of a connection to transmit and receive data simultaneously.
bidirectional communication
Full-duplex communication is also known as _____.
microsegmentation
Full-duplex communication requires _____.
microsegmented LAN
is created when a switch port has only one device connected and is operating in full-duplex mode.
no collision domain
There is _____ associated with a switch port operating in full-duplex mode.
half-duplex communication
is unidirectional.
half-duplex communication
creates performance issues because data can flow in only one direction at a time, often resulting in collisions.
Gigabit Ethernet and 10 Gb NICs
require full-duplex connections to operate
collision detection circuit
In full-duplex mode, the _____ on the NIC is disabled.
Full-duplex
offers 100 percent efficiency in both directions (transmitting and receiving).
This results in a doubling of the potential use of the stated bandwidth.
Switch ports
____ can be manually configured with specific duplex and speed settings.
10 or 100 Mbps
The 10/100/1000 ports operate in either half- or full-duplex mode when they are set to _____.
1000 Mbps (1 Gbps)
The 10/100/1000 ports operate only in full-duplex mode when it is set to _____.
Autonegotiation
is useful when the speed and duplex settings of the device connecting to the port are unknown or may change.
manually,
speed and duplex settings
When connecting to known devices such as servers, dedicated workstations, or network devices, a best practice is to _____ set the _____.
troubleshooting switch port issues
When _____, it is important that the duplex and speed settings are checked.
connectivity issues
Mismatched settings for the duplex mode and speed of switch ports can cause ______.
mismatched settings
Autonegotiation failure creates _____.
All fiber-optic ports
_____, such as 1000BASE-SX ports, operate only at one preset speed and are always full-duplex
automatic medium-dependent interface crossover (auto-MDIX)
When ____ is enabled, the switch interface automatically detects the required cable connection type (straight-through or crossover) and configures the connection appropriately.
straight-through cables
When connecting to switches without the auto-MDIX feature, _____ must be used to connect to devices such as servers, workstations, or routers
Crossover cables
When connecting to switches without the auto-MDIX feature, _____ must be used to connect to other switches or repeaters.
auto-MDIX enabled
With ____, either type of cable can be used to connect to other devices, and the interface automatically adjusts to communicate successfully.
mdix auto interface configuration mode
On newer Cisco switches, the ____ command enables the feature auto-mdix
interface speed and duplex
When using auto-MDIX on an interface, the _____ must be set to auto so that the feature operates correctly.
show controllers ethernet-controller, phy
To examine the auto-MDIX setting for a specific interface, use the _____ command with the _____ keyword.
include Auto-MDIX filter
To limit the output to lines referencing auto-MDIX, use the _____.
show interfaces [interface-id]
Display interface status and configuration.
show startup-config
Display current startup configuration.
show running-config
Display current running configuration.
show flash
Display information about flash file system.
show version
Display system hardware and software status.
show history
Display history of command entered.
show ip interface [interface-id], show ipv6 interface [interface-id]
Display IP information about an interface.
show mac-address-table, show mac address-table
Display the MAC address table.
show running-config
this command can be used to verify that the switch has been correctly configured
show interfaces
this command displays status and statistics information on the network interfaces of the switch
show interfaces
is frequently used when configuring and monitoring network devices.
show interfaces
is useful for detecting common media issues
show interfaces
One of the most important parts of this output is the display of the line and data link protocol status
first parameter
refers to the hardware layer and indicates whether the interface is receiving a carrier detect signal
second parameter
refers to the data link layer and indicates whether the data link layer protocol keepalives are being received.
interface is up and the line protocol is down
Network Access Layer Issues:
encapsulation type mismatch,
the interface on the other end could be error-disabled, there could be a hardware problem.
line protocol and the interface are both down
Network Access Layer Issues:
a cable is not attached,
some other interface problem exists
interface is administratively down
Network Access Layer Issues:
it has been manually disabled (the shutdown command has been issued) in the active configuration.
Input Errors,
Runts,
Giants,
CRC,
Output Errors,
Collisions,
Late Collisions
7 Error Types
Input Errors
Total number of errors.
Input errors
is the sum of all errors in datagrams that were received on the interface being examined.
Runts,
Giants,
Cyclic Redundancy Check error,
no buffer,
frame,
overrun,
ignored counts
7 Input errors
Runt Frames,
Giants,
CRC errors
The reported input errors from the show interfaces command include the following (3)
Runts
Packets that are discarded because they are smaller than the minimum packet size for the medium.
Runts
Ethernet frames that are shorter than the 64-byte minimum allowed length
Malfunctioning NICs
are the usual cause of excessive runt frames
collisions
can also cause of excessive runt frames
Giants
Packets that are discarded because they exceed the maximum packet size for the medium.
Giants
Ethernet frames that are larger than the maximum allowed size
Cyclic Redundancy Check error
are generated when the calculated checksum is not the same as the checksum received
Cyclic Redundancy Check error
usually indicate a media or cable error
electrical interference,
loose or damaged connections,
incorrect cabling
3 causes of CRC errors
too much noise on the link,
cable,
noise sources
If you see many CRC errors, there is _____ and you should inspect the _____. You should also search for and eliminate ____.
Output Errors
Sum of all errors that prevented the final transmission of datagrams out of the interface that is being examined.
Collisions,
Late collisions
The reported output errors from the show interfaces command include the following (2)
Collisions
Number of messages retransmitted because of an Ethernet collision.
Collisions
____ in half-duplex operations are normal.
Collisions
you should never see ____ on an interface configured for full-duplex communication.
Late Collisions
A collision that occurs after 512 bits of the frame have been transmitted
Excessive cable lengths
are the most common cause of late collisions.
duplex misconfiguration
Another common cause of late collisions.
TCP port 23
Telnet uses ____.
Telnet
It is an older protocol that uses unsecure plaintext transmission of both the login authentication (username and password) and the data transmitted between the communicating devices.
Wireshark
A threat actor can monitor packets using ____.
TCP port 22
Secure Shell (SSH) uses _____.
Secure Shell (SSH)
It provides a secure (encrypted) management connection to a remote device.
Secure Shell (SSH)
should replace Telnet for management connections.
Secure Shell (SSH)
provides security for remote connections by providing strong encryption when a device is authenticated (username and password) and also for the transmitted data between the communicating devices.
show version
command on the switch to see which IOS the switch is currently running
k9
An IOS filename that includes the combination “_____” supports cryptographic (encrypted) features and capabilities.
Verify SSH support,
Configure the IP domain,
Generate RSA key pairs,
Configure user authentication,
Configure the vty lines,
Enable SSH version 2
6 steps to configure ssh
show ip ssh
command to display the version and configuration data for SSH on the device that you configured as an SSH server
show ip ssh
If the switch is not running an IOS that supports cryptographic features, this command is unrecognized.