p1 hardware based attacks and defenses
1/13
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
14 Terms
slides 2-6:
list the possible side channels
fault injection options
Possible side channels (slides 2–5)
Power consumption
Execution time (timing)
Electromagnetic (EM) radiation
Sound (e.g. fan, coil noise)
Temperature (device or environment)
Shared microarchitectural resources (cache, branch predictor), hier laat de aanvaller zijn eigen software parallel lopen met de victim software
Possible fault injection / fault induction methods (slide 4)
Voltage manipulation (glitching)
Temperature manipulation (overheating/cooling)
Clock manipulation (clock glitching)
Radiation / light (EM, laser, alpha/gamma rays)
Definitions
side channel attack: launch own software and have it executed concurrently with the victim software
observe aspects of ther own software’s behavior, zoals exe time dat afhangt vd bits van de assetin de victim software
→ moeten wel contended resource sharen tijdens exe
slides 2-6:
define
side channels,
covert channels
fault injection attacks;
Side channel
Unintended information leakage through physical or microarchitectural effects of computation (not the functional output) that depend on secret data.
Fault injection attack
An attack where the adversary deliberately induces faults in hardware or execution (via voltage, clock, temperature, radiation, …) so that incorrect behavior or side-channel leakage reveals information about secrets.
Covert channel
A side channel used intentionally by cooperating software components to transmit sensitive data in violation of security policies, typically by modulating shared resources and observing their effects.
slide 9:
explain the essence or main principle of side channel attacks:
the relation to SNR
explain what
leakage free
high leakage
low leakage processes
look like when sampled;
Essentie van side-channel attacks (timing): relatie met SNR
Uitvoeringstijd is stochastisch → elke bitwaarde geeft een distributie van tijden
sampelen van veel executions
(p1 voor bit=0, p2 voor bit=1).
wilt de waarde van bit vinden wanneer het programma uitgevoerd is op spec input
runnen en execution time meten
SNR: hoe bruikbaar een meting is
hoge SNR: duidelijk verschil tussen de metingen
attacker can deduct what bit value was used
Leakage-free proces
p1 = p2 (identieke distributies).
Volledige overlap → SNR = 0.
Geen enkele hoeveelheid samples geeft informatie over de bit.
Timing lekt niets.

High leakage
p1 en p2 zijn duidelijk gescheiden (weinig of geen overlap).
Groot verschil t.o.v. ruis → hoge SNR.
Eén of zeer weinig samples volstaan om de bit te bepalen.
Zeer lek proces.

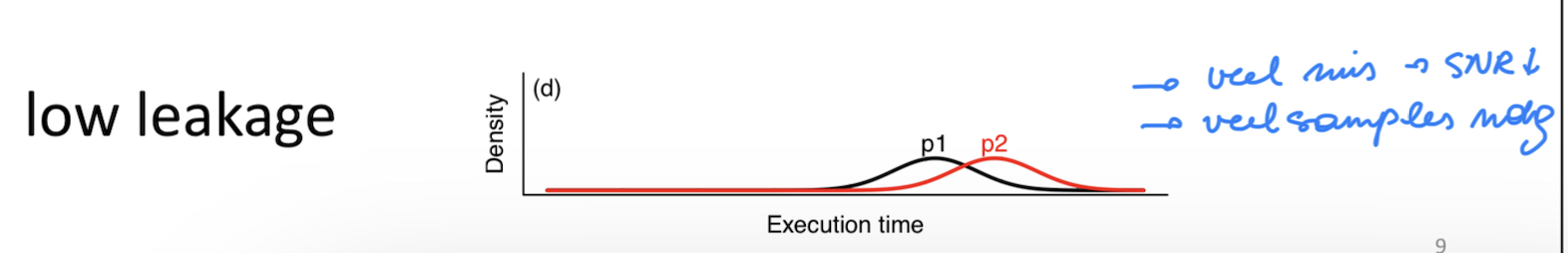
Low leakage
p1 en p2 zijn verschoven maar sterk overlappend.
Signaal aanwezig, maar veel ruis → lage SNR.
Individuele samples weinig informatief; veel herhalingen nodig.
Beperkte maar niet-nul lekken.
hint: for all examples mentioned below, explaining how an attack works requires
explaining at least the capabilities that an attacker relies upon as well as
explaining what correlation exists between the type of sensitive data is being stolen/leaked and the observations made by the attacker,
so you should be able to give the goals and capabilities of the attacker as well as the exploited correlation;
time example 1: present and discuss the time-based side-channel attack on simple password checks implemented with strcmp;
hint: for all examples mentioned below, explaining how an attack works requires
explaining at least the capabilities that an attacker relies upon as well as
explaining what correlation exists between the type of sensitive data is being stolen/leaked and the observations made by the attacker,
so you should be able to give the goals and capabilities of the attacker as well as the exploited correlation;
Time-based side-channel via strcmp
Goal
Het geheime wachtwoord achterhalen.
Capabilities
Remote toegang tot de password check.
Vrij kiezen van inputs (password guesses).
Nauwkeurige timingmetingen van de uitvoering.
Exploited correlation
Uitvoeringstijd ←> aantal gelijke begintekens tussen input en geheim.
Meer correcte prefixbits ⇒ langere uitvoering.
Attack idea
Kies telkens het teken dat de uitvoeringstijd maximaliseert.
Herhaal per positie ⇒ wachtwoord lekt teken per teken.
time example 2: explain, in general, the various ways in which program execution time can depend on operand values;
hint: for all examples mentioned below, explaining how an attack works requires
explaining at least the capabilities that an attacker relies upon as well as
explaining what correlation exists between the type of sensitive data is being stolen/leaked and the observations made by the attacker,
so you should be able to give the goals and capabilities of the attacker as well as the exploited correlation;
Time-based side channel: modular exponentiation (general theory)
Goal
steal private key to which no direct access is available
Capabilities
Remote toegang.
force messages to be decrypted
measure decryption time
Exploited correlations
(execution time < - > operand values)
Programuitvoeringstijd kan afhangen van data door:
Control flow: conditionele branches afhankelijk van bits (if/else).
Aantal operaties: extra multiplications bij bepaalde bitwaarden.
Hamming weight / bitpatroon: meer ‘1’-bits ⇒ meer werk.
Branch prediction: onregelmatige bitpatronen ⇒ meer mispredictions.
time example 3: explain older mechanisms by which information could be obtained about someone's typing rate, and how that information relates to security-sensitive characters being typed;
hint: for all examples mentioned below, explaining how an attack works requires
explaining at least the capabilities that an attacker relies upon as well as
explaining what correlation exists between the type of sensitive data is being stolen/leaked and the observations made by the attacker,
so you should be able to give the goals and capabilities of the attacker as well as the exploited correlation;
Time-based side channel: keystroke events (older mechanisms)
Goal
Wachtwoorden of andere gevoelige toetsaanslagen afleiden.
Capabilities
Netwerktoegang en passief sniffen.
lokale user access met leesrechten op process/system info.
Mogelijkheid om timing tussen events nauwkeurig te meten.
Older mechanisms
SSH (vroeger):
Eén netwerkpakket per ingedrukte toets.
Aanvaller observeert pakket-timing ⇒ typing rate.
Unix/Linux process info (slechte configuraties):
Onprivileged users konden timing, EIP/ESP, CPU-tijd lezen via
/proc.Zichtbaar wanneer een proces wacht op keyboard input.
Exploited correlation
Tijd tussen keystrokes ←> type karakter(s).
Typing rate is niet uniform:
Sommige lettercombinaties trager/sneller.
Pauzes, correcties, enter-toets, etc.
Statistische correlatie tussen timingpatronen en mogelijke wachtwoorden.
Gevolg
Zoekruimte van wachtwoorden wordt sterk verkleind via timinginformatie.
power example 1: explain how a simple power attack works;
hint: for all examples mentioned below, explaining how an attack works requires
explaining at least the capabilities that an attacker relies upon as well as
explaining what correlation exists between the type of sensitive data is being stolen/leaked and the observations made by the attacker,
so you should be able to give the goals and capabilities of the attacker as well as the exploited correlation;
Simple Power Analysis (SPA)
Goal
Geheime data achterhalen (bv. cryptografische sleutels).
Capabilities
acquire power consumption traces of the device
Hoge-resolutie power traces tijdens uitvoering.
Kennis van implementatie of typische verbruikspatronen.
Exploited correlation
Vermogen hangt af van aantal bitflips en type operatie.
Verschillende operaties of operandwaarden veroorzaken herkenbare patronen.
Attack idea
Meet power trace tijdens uitvoering.
Herken patronen die overeenkomen met specifieke stappen (bv. key-dependent branches).
Leid bits van het geheim af uit het waargenomen verbruik.
power example 2:
explain how a differential power attack works;
explain why such an attack (when it is feasible in some scenario) is much harder to defend against than a simple power attack
(i.e., that any correlation suffices between power consumption and internal bits, even if the attacker does not know a priori what the correlation looks like);
briefly discuss the practical issues that make this type of attack feasible only in limited scenarios;
hint: for all examples mentioned below, explaining how an attack works requires
explaining at least the capabilities that an attacker relies upon as well as
explaining what correlation exists between the type of sensitive data is being stolen/leaked and the observations made by the attacker,
so you should be able to give the goals and capabilities of the attacker as well as the exploited correlation;
Differential Power Analysis (DPA)
Goal
Volledige geheime sleutel reconstrueren (bv. crypto key).
Capabilities
Veel power traces meten van hetzelfde apparaat.
Keuze of kennis van inputs (chosen / known plaintexts).
Basiskennis van het algoritme (niet van hardware details).
How the attack works
Verzamel veel power traces voor dezelfde sleutel.
Kies een intern bit (b) (afhankelijk van kleine subset key bits).
Voor elke mogelijke subkey-guess:
compute some intermediate result bit b for all possible last round subkey bits that affect bit b
Splits traces in twee groepen: (b=0) en (b=1).
Neem het gemiddelde per groep en trek ze van elkaar af.
De juiste subkey-guess geeft een duidelijke piek/vallei in het verschil.
Exploited correlation
Power consumption ←> waarde van een intern bit (0 vs 1).
Exacte vorm van de correlatie is niet nodig, ze moet enkel bestaan.
Why harder to defend than SPA
SPA vereist herkenbare, zichtbare patronen.
DPA werkt met statistiek:
eender welke kleine correlatie volstaat;
geen kennis nodig van waar of hoe het lek precies zit.
“Noise” wordt weggefilterd door averaging over veel traces.
Practical limitations
Veel traces nodig.
Traces moeten correct tijd-aligned zijn.
Moeilijk op complexe, snelle CPUs (out-of-order, caches).
Vooral haalbaar op eenvoudige, trage devices (bv. smart cards).
Kerninzicht
Als power ook maar minimaal afhangt van geheime bits, kan DPA die bits statistisch blootleggen.
example 3: explain how an accelerometer can be used to steal sensitive data;
hint: for all examples mentioned below, explaining how an attack works requires
explaining at least the capabilities that an attacker relies upon as well as
explaining what correlation exists between the type of sensitive data is being stolen/leaked and the observations made by the attacker,
so you should be able to give the goals and capabilities of the attacker as well as the exploited correlation;
Accelerometer side channel
Goal
steal secret data such as passwords bein typed
Capabilities
run malicious app concurrently with victim app
Toegang tot accelerometer (vroeger zonder speciale permissies).
Exploited correlation
when users type on a virtual keyboard on screen, they make the device accelerate diferenctly for the different keys
Attack idea
Meet accelerometerdata tijdens typen.
Classificeer signalen per toetsaanslag.
Reconstrueer ingevoerde tekst (volledig of gedeeltelijk).
Kerninzicht
Niet-gevoelige sensoren kunnen toch input lekken via fysische correlaties.
example 4: explain how a multiplier in an simultaneous multithreading core's execution pipeline can be used as a covert channel,
including why attackers may want to use such covert channels;
hint: for all examples mentioned below, explaining how an attack works requires
explaining at least the capabilities that an attacker relies upon as well as
explaining what correlation exists between the type of sensitive data is being stolen/leaked and the observations made by the attacker,
so you should be able to give the goals and capabilities of the attacker as well as the exploited correlation;
Covert channel via shared multiplier (SMT core)
Goal
steal or pass secret data from victim or insider thread / process
Capabilities
attacker can run chosen process on hardware sharing resources with victim
Aanvaller kan eigen uitvoeringstijd meten.
How the covert channel works
Insider encodeert bits via resourcegebruik:
bit = 1 → actief multiplier bezetten (veel MUL-instructies).
bit = 0 → multiplier vrij laten.
observer voert code uit op zelfde thread
when the observer thread executes more slowly
can see in output from “get_time()” from observer
Contention ⇒ langere uitvoeringstijd.
Geen contention ⇒ kortere uitvoeringstijd.
Timingverschil decodeert de verzonden bit.
Exploited correlation
Uitvoeringstijd observer ←> beschikbaarheid multiplier ←> bitwaarde insider.
Gedeelde hardware resource fungeert als communicatiemedium.
Why attackers want covert channels
Rechtstreekse output (bv. netwerk, files) is vaak verboden.
Covert channels laten data lekken ondanks correcte OS-, memory- en privilege-isolatie.
Bruikbaar in cloud/VM-omgevingen met gedeelde hardware.
Kerninzicht
Gedeelde microarchitecturale resources kunnen bewust misbruikt worden als communicatiekanaal, zelfs zonder expliciet datalek.
example 5: explain how an AES shared cache attack works;
AES shared cache attack (Prime+Probe style)
Goal
steal or pass secret data from victim or insider thread / process
Capabilities
Aanvaller draait een eigen proces/thread op hardware die caches deelt met het slachtoffer.
Kan cache-timing meten (snelle vs trage geheugenaccesses).
Kennis van AES-implementatie (S-box lookup).
How the attack works
Prime: aanvaller vult specifieke cachelijnen met eigen array.
crypto thread evicts array elements from shared cache by performing lookups in s-box tables
Probe: aanvaller herleest zijn array en meet toegangstijden.
Trage accesses ⇒ cachelijn was verdrongen door victim.
attacker knows key
Exploited correlation
Toegang tot specifieke S-box entries <> geheime sleutel + plaintext.
Cache-evictions lekken welke S-box indices gebruikt zijn.
Result
Statistische analyse over vele encrypties onthult sleutelbits.
Kerninzicht
Gedeelde caches vormen een high-bandwidth side channel:
geheugen-toegangspatronen lekken cryptografische geheimen, zelfs bij correcte software-isolatie.
example 6: explain how the volume setting can be used as a covert channel, including why attackers may want to use such covert channels;
Covert channel via phone volume setting
Goal
steal or pass secret data from victims phone
Capabilities
running 2 malicious apps on same device
App A: toegang tot gevoelige data, geen netwerk.
App B: netwerktoegang, geen gevoelige data.
Beide hebben toegang tot volume-instellingen (globale resource).
How the covert channel works
App A encodeert geheime data door volume-niveaus of volumepatronen te zetten.
App B leest periodiek de volume-instelling.
App B decodeert de data en verstuurt ze via het netwerk.
Exploited correlation
Volume-instelling <> gecodeerde bits.
OS behandelt volume als niet-gevoelige, gedeelde staat.
Why attackers want covert channels
Om permissiemodellen te omzeilen.
Om gevoelige data te lekken zonder directe datastromen.
Om security checks te passeren terwijl elke app individueel “legitiem” lijkt.
Kerninzicht
Gedeelde, niet-beveiligde systeeminstellingen kunnen misbruikt worden als betrouwbare communicatiekanalen.
airgaps:
explain what airgapping is,
why it is normally used
give and briefly explain some concrete examples of options to use covert channels to bridge air gaps.
Airgapping
What it is
isolation fo hte most sensitive devices from the rest of the network that is connected to the internet and hence more susceptible to attacks
Why it is used
Bescherming van zeer gevoelige systemen (bv. militaire, industriële, crypto-keys).
Aanname: zonder netwerk is exfiltratie of remote aanval onmogelijk.
Covert channels to bridge air gaps (examples)
Electromagnetic
GPU, memory of USB-bus zendt RF-signalen uit.
Ontvangen door nabij toestel (radio, SDR).
Optical
HDD-LED, keyboard-LED, schermhelderheid of QR-codes.
Camera of visuele sensor leest gemoduleerde bits.
Acoustic
Speaker, HDD-geluid, fan noise.
Microfoon decodeert data uit geluidspatronen.
Others
Core insight
Airgapping reduceert het aanvalsoppervlak, maar elimineert geen side/covert channels.
Elk fysisch meetbaar effect kan misbruikt worden als datakanaal.