OCR Computer Science 1.4 Network Security
1/18
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
19 Terms
Malware
software that is intended to damage or disable computers and computer systems.

Virus
A piece of code that is capable of copying itself and typically has a detrimental effect, such as corrupting the system or destroying data

Worm
a software program capable of reproducing itself that can spread from one computer to the next over a network, without any human interacction.

Keylogger
a malicious program that records keystrokes.

Social Engineering
hackers use their social skills to trick people into revealing access credentials or other valuable information

Shoulder surfing
Gaining compromising information through observation (as in looking over someone's shoulder).

Phishing
An attack that sends an email or displays a Web announcement that falsely claims to be from a legitimate enterprise in an attempt to trick the user into surrendering private information

Brute force attack
the password cracker tries every possible combination of characters

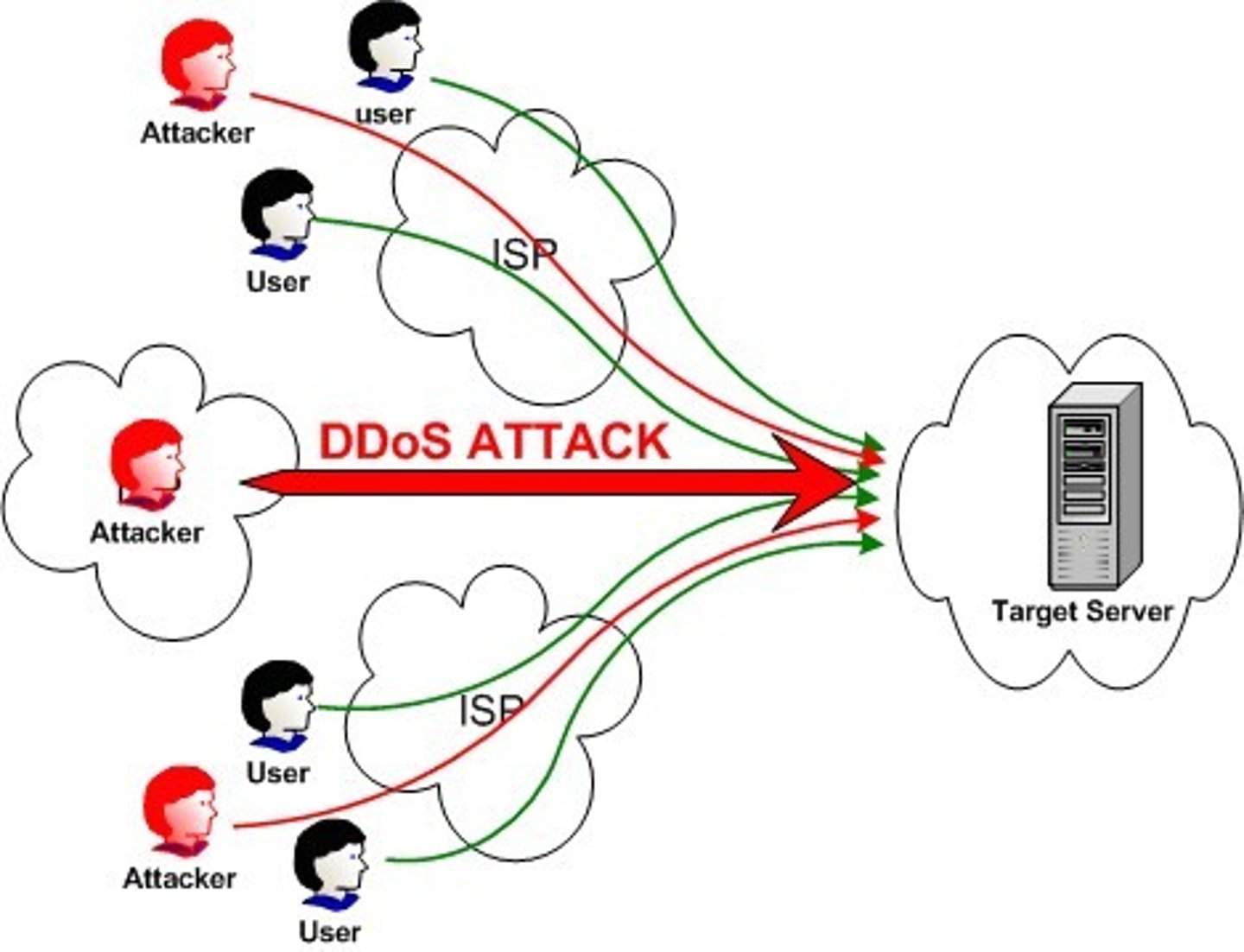
denial of service attack
a cyber attack in which an attacker sends a flood of data packets to the target computer, with the aim of overloading its resources
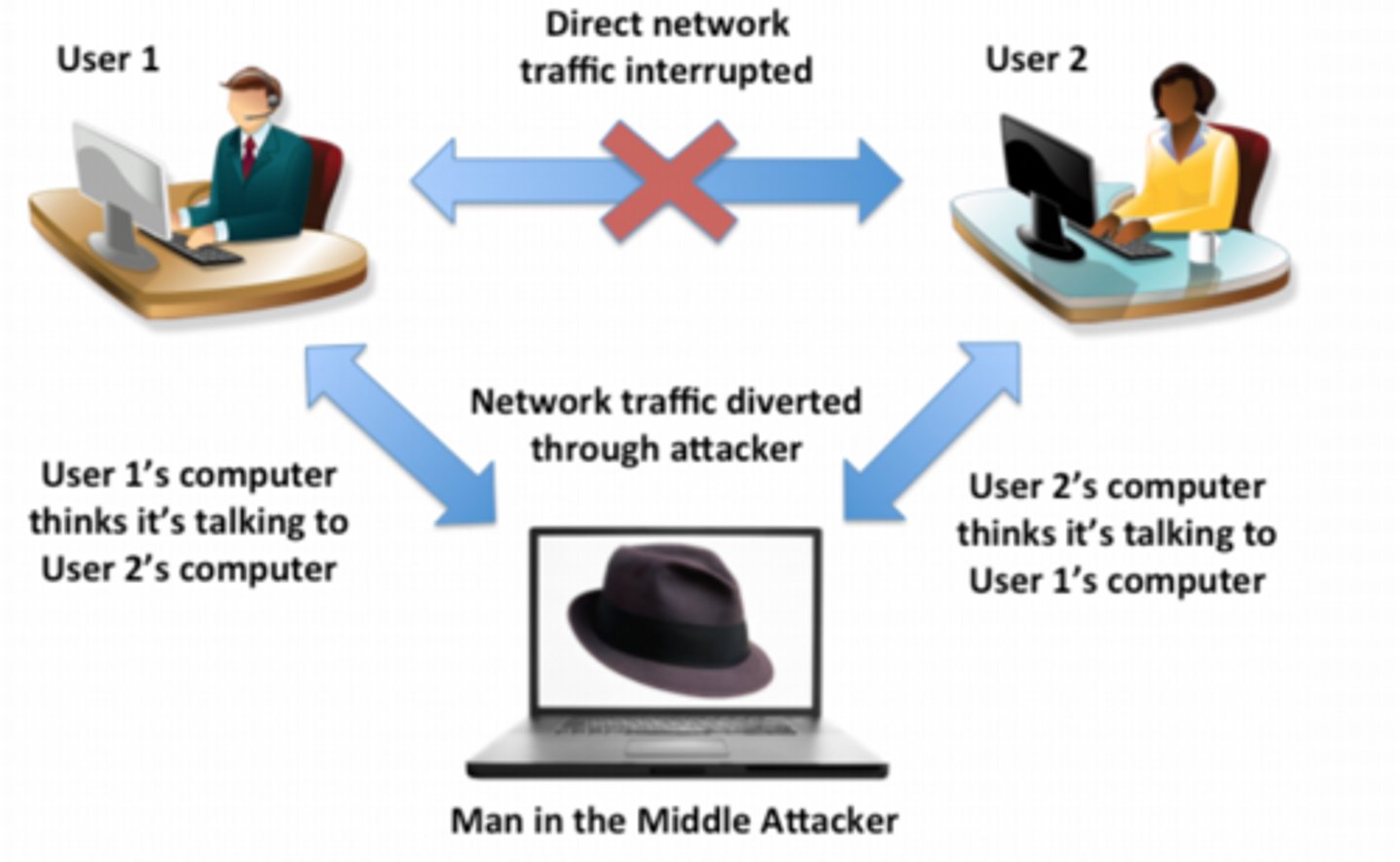
Man in the middle attack
a hacker placing himself between a client and a host to intercept communications between them
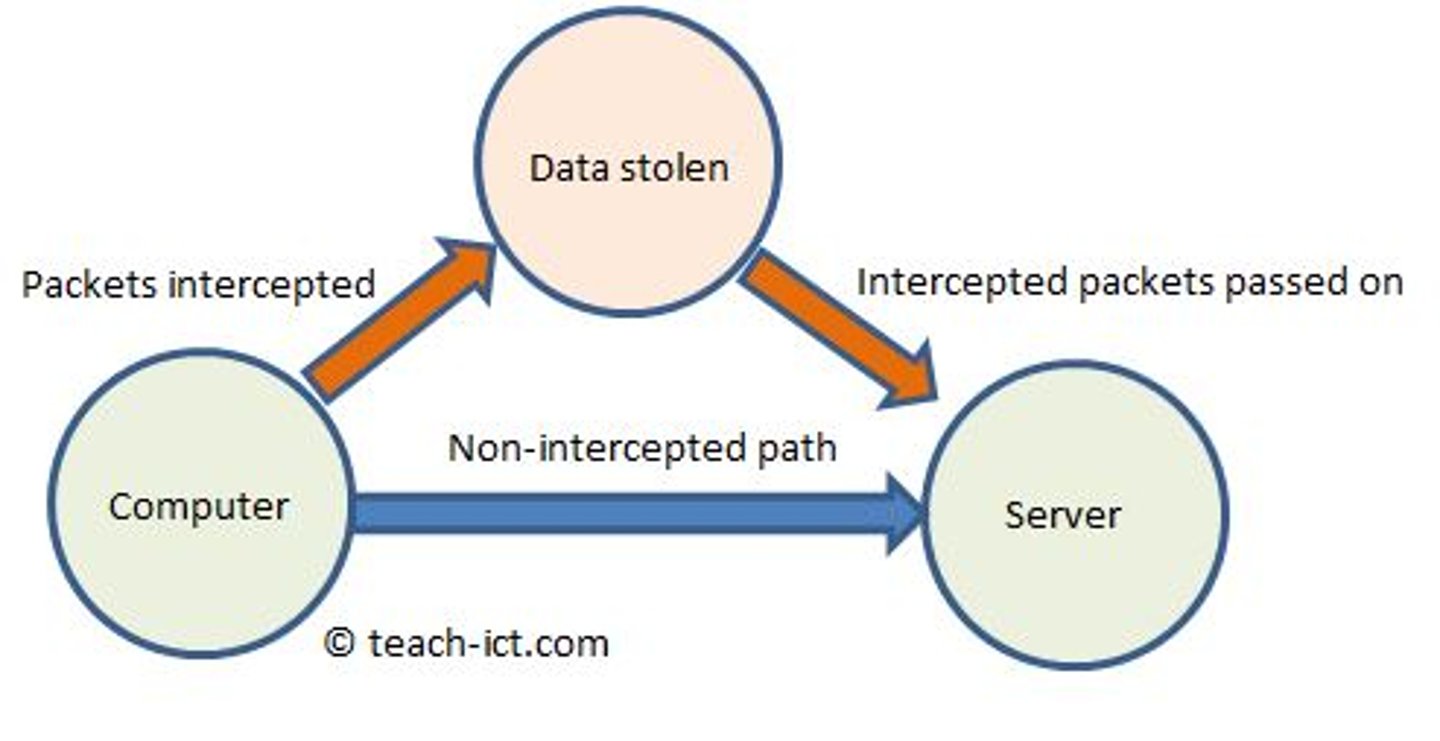
Data interception
Listening' to data as it passes from one device to another
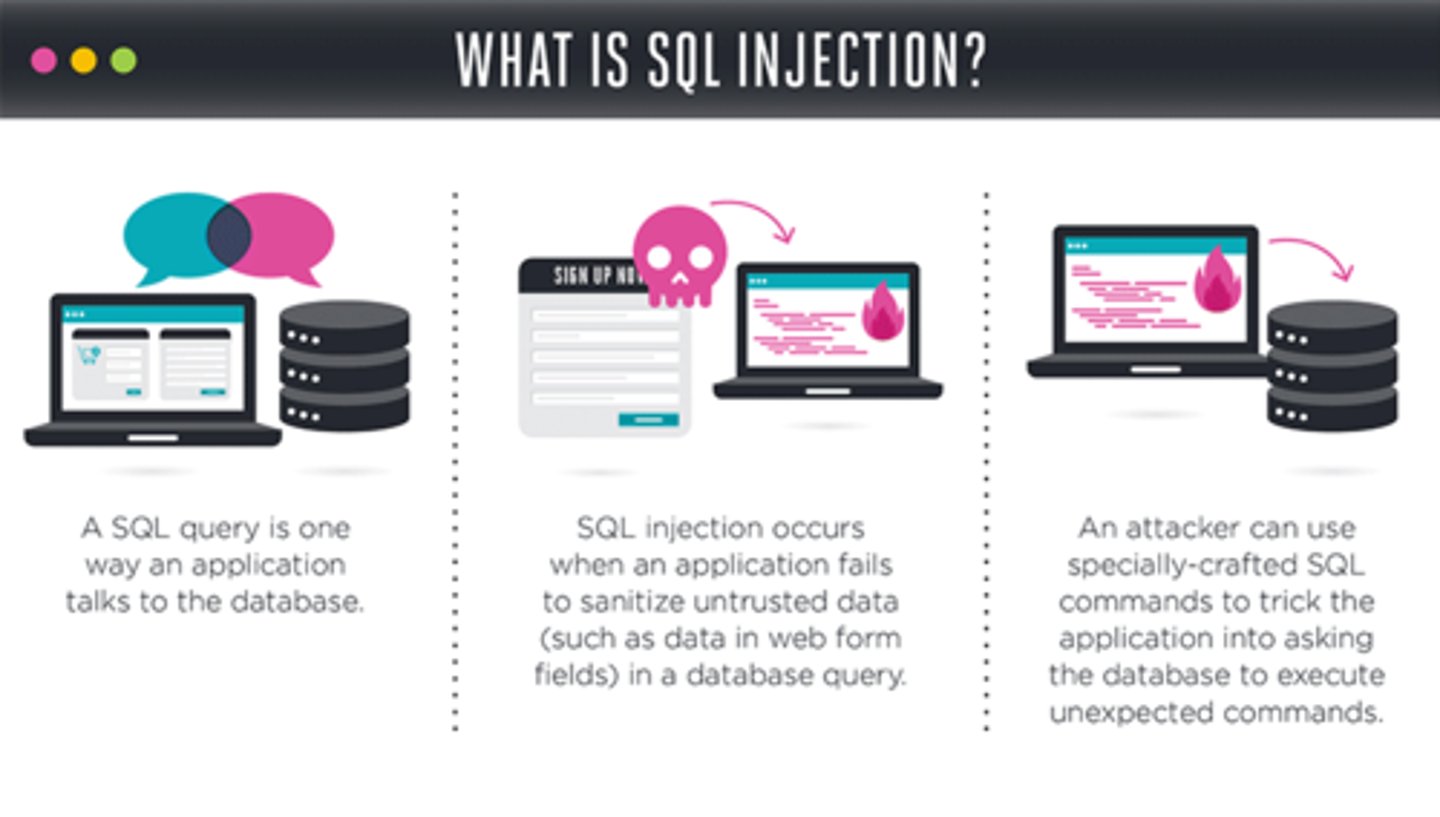
SQL Injection
An attack that targets SQL servers by injecting commands to be manipulated by the database.
Penetration Testing
A live test of the effectiveness of security defenses through mimicking the actions of real-life attackers
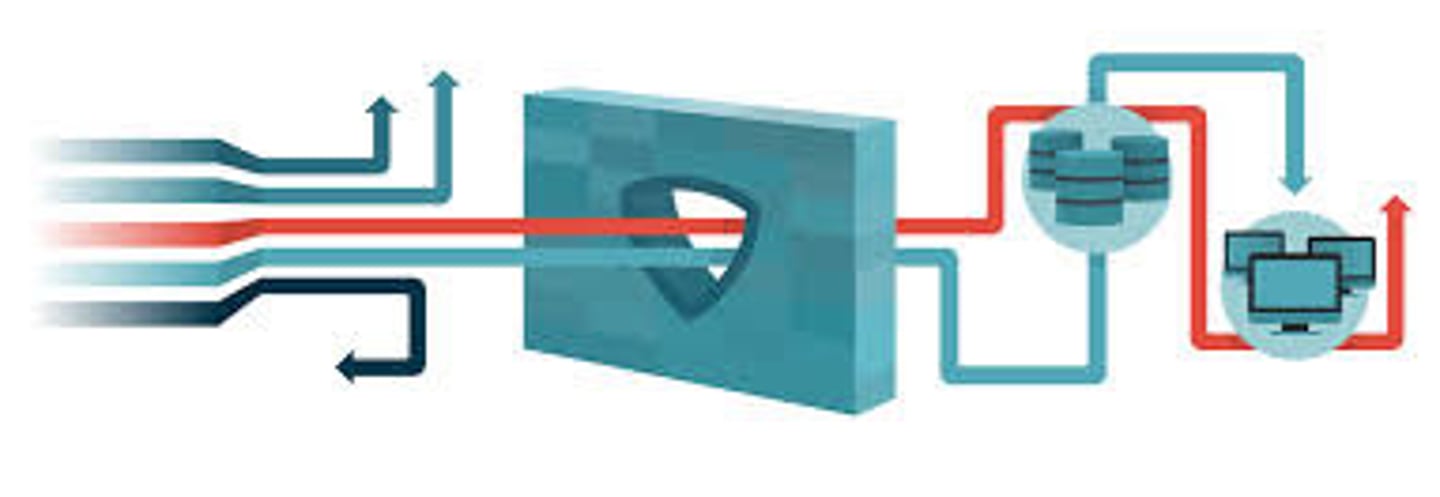
Anti malware software
Software designed to stop malware from damaging a computer or network

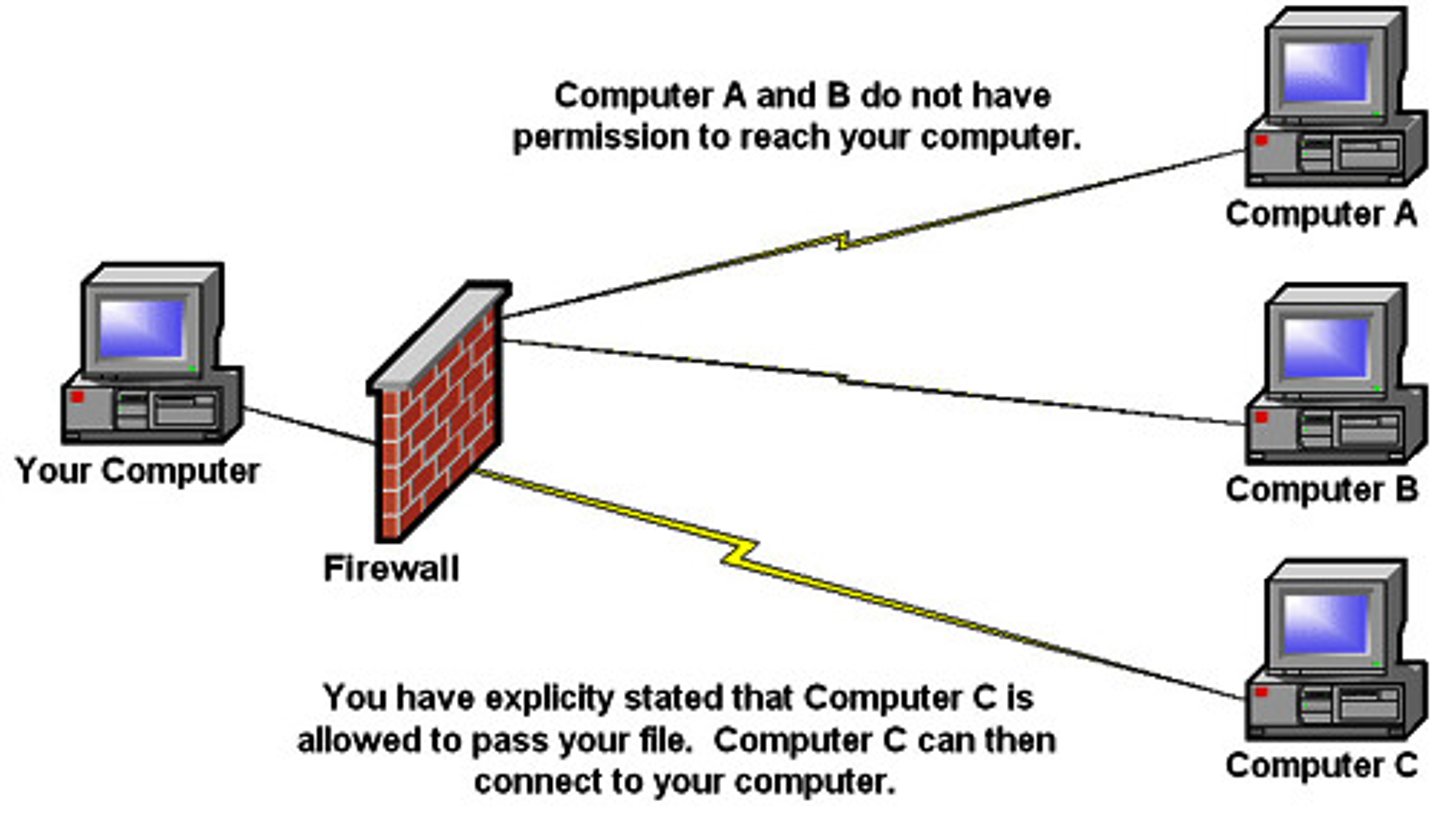
Firewall
a part of a computer system or network that is designed to block unauthorized access while permitting outward communication.
User Access Levels
A network policy that defines which users can see which folders and files and the type of access they have to them. Eg: Read-Only or Read-Write.
Passwords
private phrases or words that give a particular user a unique access to a particular program or network

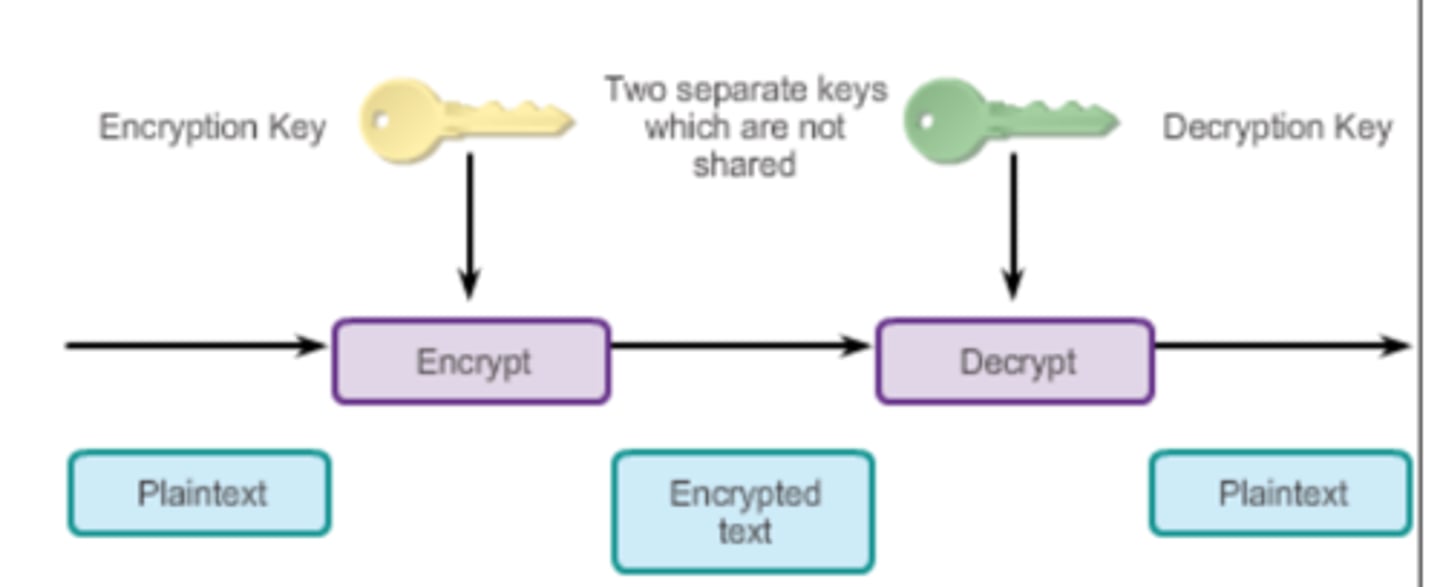
Encryption
Process of converting readable data into unreadable characters to prevent unauthorized access.
Physical security
tangible protection such as alarms, guards, fireproof doors, fences, and vaults
