CCNA 200-301 Lab
1/68
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
69 Terms
how to use type 9 hasing
enable algorithm-type scrypt secret (secretname here)
how to time users out
exec-timeout minutes seconds
Enter interface config mode
(config)# interface g/0
Human readable link description
(config-if)# description Link to Somehost
Add IPv4 address to interface
(config-if)# ip address 10.23.42.5 255.255.0.0
Overwrite MAC Address
(config-if)# mac address 1234.5678.90AB
Remove MAC Address
(config-if)# no mac address
Add IPv6 address to interface.
(config-if)# ipv6 address 2001:41d0:8:e115::ccc/64
Add IPv6 address based on MAC to interface.
(config-if)# ipv6 address 2001:41d0:8:e115::/64 eui-64
Get IPv4 address via dhcp.
(config-if)# ip address dhcp
Get IPv6 address [and default route] via autoconfig
(config-if)# ipv6 address autoconfig [default]
Set hostname transmitted as dhcp client to SW2
(config-if)# ip dhcp client client-id asccii SW2
Configure both interfaces at once.
(config)# interface g1/0 - 2
En- or Disable interface. Often shutdown is the default.
(config-if)# [no] shutdown
Set 10.23.42.1 as the default gateway
(config)# ip default-gateway 10.23.42.1
Add static route via next hop or interface
(config)# ip route 10.20.30.0 255.255.255.0 {1.2.3.4,e0/0} [ad]
Next hop is required for Ethernet interface in IPv6
(config)# ipv6 route 2001:41d0:8:e115::/64 [g1/1] [next hop]
Create a static host entry on this device.
(config)# ip host the-space.agency 178.32.222.21
Globally enable ipv6 routing.
(config)# ipv6 unicast-routing
Replaces the startup config with the active config when the Cisco network device initializes
copy running-config startup-config
Merges the startup config with the currently active config in RAM
copy startup-config running-config
Deletes the startup config
write erase
erase startup-config
Lists summary (or detailed) information about each neighbor connected to the device
show cdp neighbors[detail]
Shows whether CDP is enabled globally
show cdp
Lists the current VLAN Trunk Protocol (VTP) status, including the current mode
show vtp status
Show routes and how they were learned.
# show ip[v6] route [static]
Show interfaces ip/arp/icmp/nd... configuration
# show ip[v6] interface [if-name]
Only show ip, status and operational status
# show ip[v6] interface brief [if-name]
Show {ip,ipx,appletalk}-mac bindings
# show arp
Show the mac address table of a switch.
# show mac address-table
Clear the dynamically learned mac address table entries.
# clear mac address-table [dynamic]
Remove arp entry for ip
clear [ip] arp 192.168.1.1
En/Disable port-security
(config-if)# [no] switchport port-security
Number of allowed MACs.
(config-if)# switchport port-security maximum 1
Manually allow a MAC on this port.
(config-if)# switchport port-security mac-address 1234.5678.9abc
port status, violation mode, max/total MACs,...
# show port-security [interface g1/1]
enter interface config mode
(config)# interface vlan 23
set device ip in vlan 23
(config-if)# ip address 1.2.3.4 255.255.255.0
delete vlan 23
(config)# no vlan 23
Create subinterface g1/1.10 on g1/1
(config)# interface g1/1.10
Enable portfast on this interface
(config-if)# spanning-tree portfast
Who's the root and how do I get there?
# show spanning-tree [vlan 1]
Is global portfast/bpduguard configured?
# show spanning-tree summary
Put etherchannel 1 in trunk mode
(config-if)# switchport mode trunk
Add tagged vlans 10,20,30 on etherchannel 1
(config-if)# switchport trunk allowed vlan 10,20,30
Add both interfaces to etherchannel 1 (PAgP)
(config-if-range)# channel-group 1 mode {auto, desirable}
Add both interfaces to etherchannel 1 (LACP)
(config-if-range)# channel-group 1 mode {active, passive}
Add both interfaces to etherchannel 1 (Static)
(config-if-range)# channel-group 1 mode on
Create ACL #23 or append a rule to ACL #23, allow 1.2.x.x
(config)# access-list 23 permit 1.2.3.4 [0.0.255.255]
Create ACL and/or enter config mode for ACL #23
(config)# ip access-list {standard, extended} 23
Append rule to standard ACL 'local_only'
(config-std-nac1)# permit 10.20.30.0 0.0.0.255
Append rule to ACL at sequence number 5.
(config-std-nac1)# 5 permit 10.20.30.0 0.0.0.255
Apply ACL #23 to outgoing packets, not send by the router
(config-if)# ip access-group 23 out
Apply ACL #42 to incoming packets
(config-if)# ip access-group 42 in
Show all configured ACLs
# show [ip[v6]] access-lists
(NAT) Packets going out, need to change their src, incoming their dest ip.
(config)# int g1/2
(config-if)# ip address 10.10.23.1 255.255.255.0
(config-if)# ip nat outside
(NAT) Packets going out, need to change their dest, incoming their src ip.
(config)# int g1/2
(config-if)# ip address 10.10.23.1 255.255.255.0
(config-if)# ip nat inside
(DHCP) Don't distribute these IPs in leases
(config)# ip dhcp excluded-address 10.30.4.1 10.30.4.100
Creat and/or enter dhcp config for pool 'PCs'
Define Pool Addresses & Default Gateway
ip dhcp pool PCs
(dhcp-config)# network 10.30.4.0 /24
(dhcp-config)# default-router 10.2.1.1
(dhcp-config)# dns-server 10.30.4.1
(dhcp-config)# domain-name acme.com
(dhcp-config)# lease
Relay DHCP Requests for this host
(config-if)# ip helper-address 192.168.1.1
DHCP Troubleshooting Commands
# show dhcp lease
# show ip dhcp pool
# show ip dhcp binding
# sh run int g1/1
Join HSRP Group
Set prority of router
(config-if)# standby [group-number] ip
(config-if)# standby [group-number] priority
Create ip sla test #23 and enter its config mode.
Define icmp-echo test.
frequency in seconds.
Start test #23 now and until manually stopped.
(config)# ip sla 23 |
(config-ip-sla)# icmp-echo 1.2.3.4 |
(config-ip-sla)# frequency 42 |
(config)# ip sla schedule 23 life {forever, seconds} start-time now |
Active licenses
# show license
SSH
Required to generate SSH keys. |
Required to generate SSH keys. |
Generate keys like it's 1995! Potentially takes forever. |
Force SSHv2 |
Force ssh, disable telnet. |
SSH version, timeout time, auth retries.. |
List of active connections |
(config)# hostname Foobar |
(config)# ip domain-name example.com |
(config)# crypto key generate rsa modulus 2048 |
(config)# ip ssh version 2 |
(config-line)# transport input ssh |
# show ip ssh |
# show ssh |
Disable unused services
Show open ports |
Stop the http server (but not https). |
Stop CDP |
# show control-plane host open-ports |
(config)# no ip http server |
(config)# no cdp enable |
# auto secure |
SNMP
Contact email |
Where is the device |
Add community |
SNMP notifications recipient |
(config)# snmp-server contact admin@example.com |
(config)# snmp-server location RZ-Hamburg |
(config)# snmp-server community [ro, rw] |
(config)# snmp-server host 10.20.30.40 |
OSPF
1 is the pid, not the area. |
Defaults to highest IPv4 on lo, then other ifs. |
enable interfaces for ospf with matching IPs |
Stop in- and egress ospf hello packets. |
Mark all ifs passive by default. |
Advertise default routes into a normal area |
Change reference bandwidth speed |
Overwrite interface cost to 23 |
Change interface bandwidth |
(config)# router ospf 1 |
(config-router)# router-id 1.2.3.4 |
(config-router)# network 10.20.30.0 0.0.0.255 area 0 |
(config-router)# (no) passive-interface g1/1 |
(config-router)# passive-interface default |
(config-router)# default-information originate (always) |
(config-router)# auto-cost reference-bandwidth <refbw in Mb/s> |
(config-if)# ip ospf cost 23 |
(config-if)# bandwidth <bw in kb/s> |
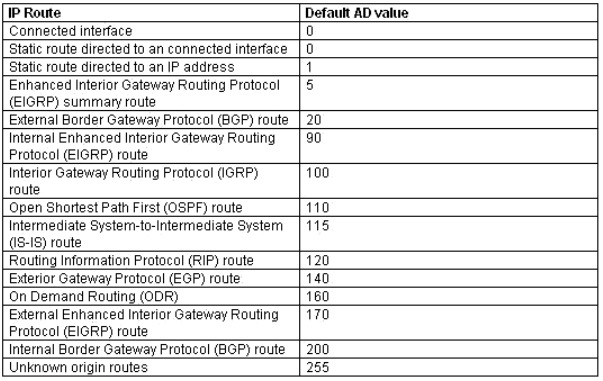
AD Value