Quiz 3 Transport Layer
1/15
Earn XP
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
16 Terms
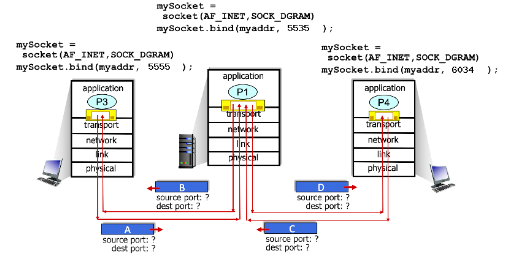
In the scenario, the left and right clients communicate with a server using UDP sockets. The same socket at the server is used to communicate with both clients. The Python code used to create the sockets is shown in the figure. Consider the four transport-layer packets – A, B, C and D – shown in the figure below. What are the source and destination ports for each packet?
Packet A:
Source Port: 5555
Destination Port: 5535
Packet B:
Source Port: 5535
Destination Port: 5555
Packet C:
Source Port: 6034
Destination Port: 5535
Packet D:
Source Port: 5535
Destination Port: 6034
Consider the two 16-bit words (shown in binary) below. Recall that to compute the Internet checksum of a set of 16-bit words, we compute the one's complement sum [1] of the two words. That is, we add the two numbers together, making sure that any carry into the 17th bit of this initial sum is added back into the 1's place of the resulting sum); we then take the one's complement of the result. Compute the Internet checksum value for these two 16-bit words:
11010000 11100001 this binary number is 53473 decimal (base 10)
01101000 11000101 this binary number is 26821 decimal (base 10)
What is the sum of these two 16 bit numbers? Using the sum, what is the checksum?
1101000 11100001 + 01101000 11100001 = 100111001 10100110
100111001 10100110 + 1 = 00111001 1010011
Sum: 00111001 10100111
Checksum: 11000110 01011000 (complement of the sum)

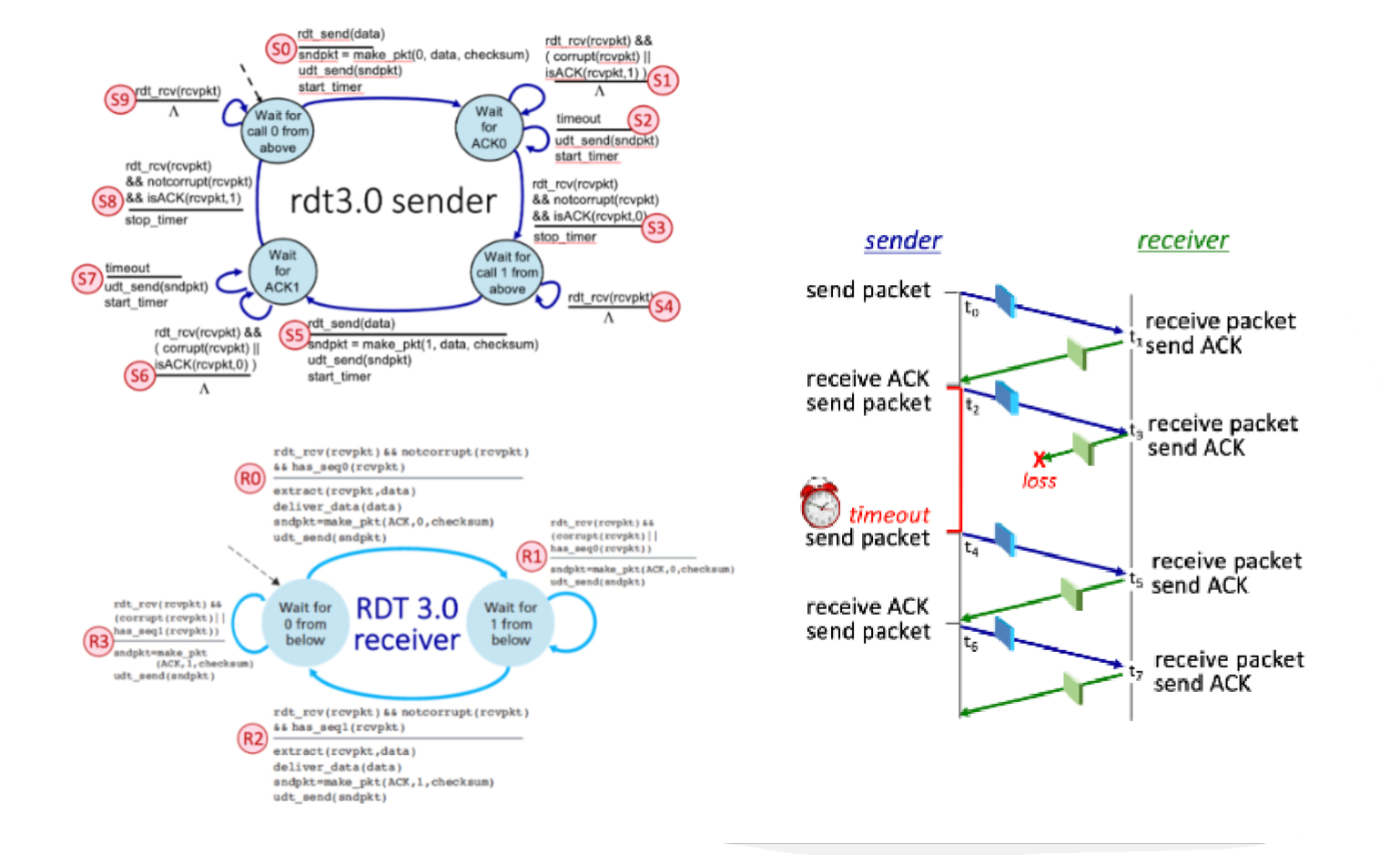
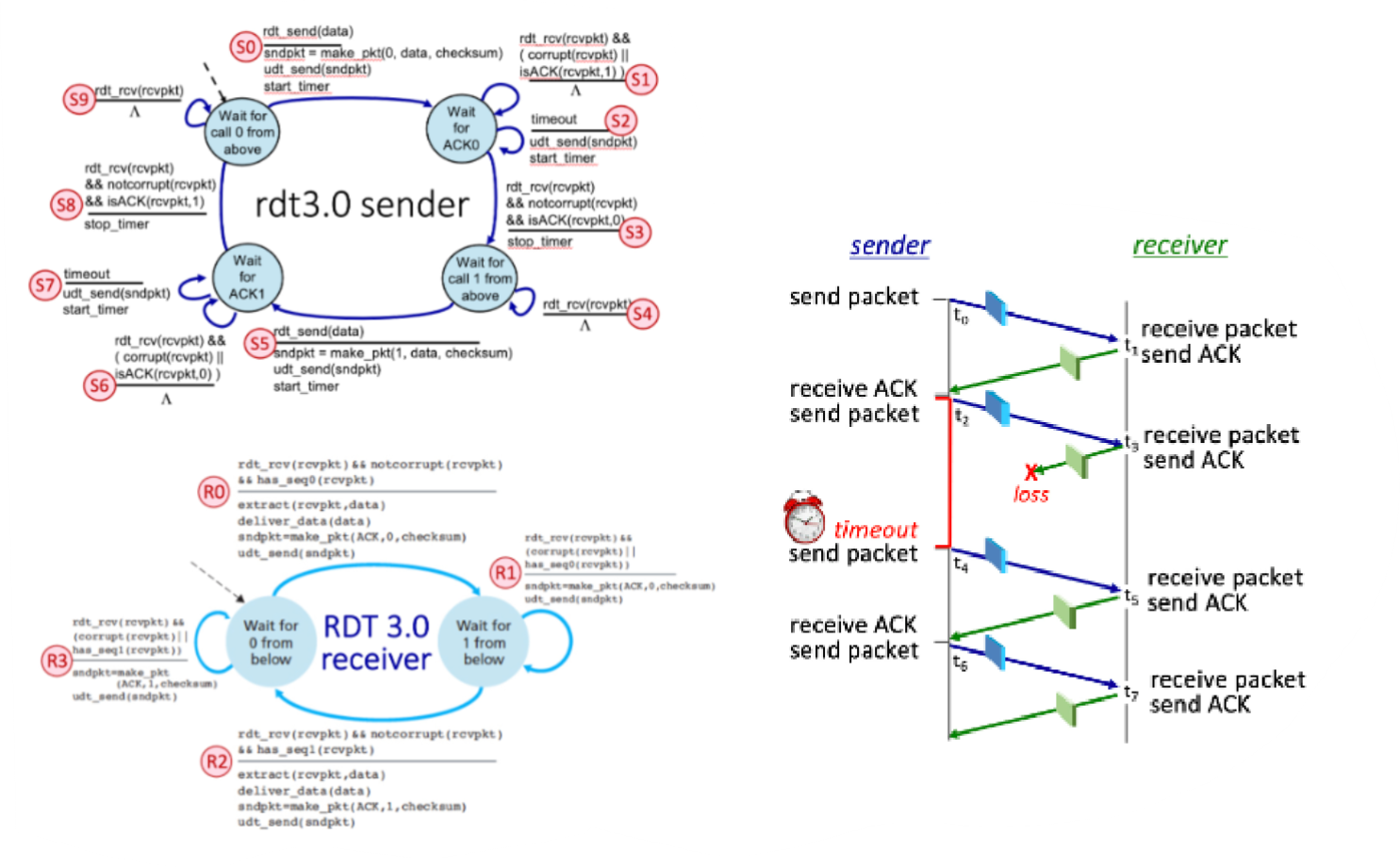
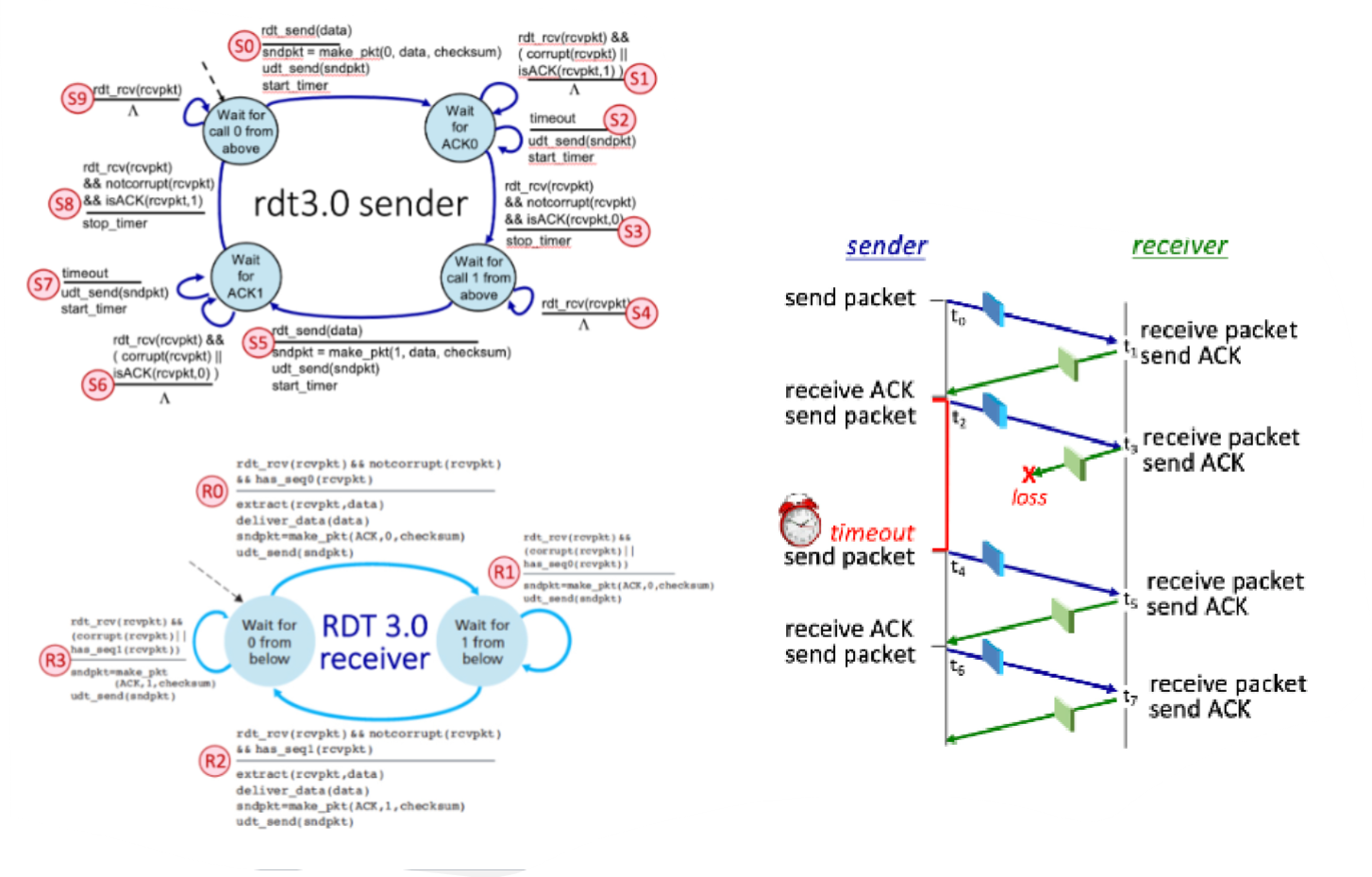
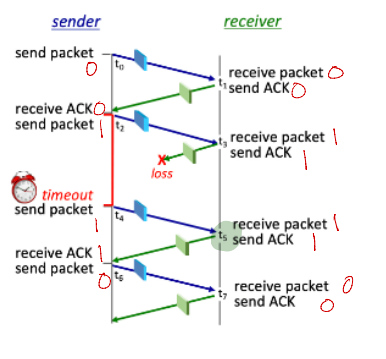
Consider the RDT 3.0 protocol, for reliably communicating data from a sender to receiver over a channel that can lose or corrupt packets in either direction, and when the maximum delay from sender to receiver and back is not known. The FSMs for the sender and receiver are shown below, with their transitions labeled as SX and RY, respectively.
Now let’s consider the sequence of sender and receiver transitions that would happen when one or more of the following complications occur: a packet (data or ACK) is lost, a timer times out (prematurely or not), or a message is corrupted. One or more of these events has occurred to produce the sequence of transitions below. In the sequence below, one transition has been omitted and replaced with a "*".
Transition Sequence: S0, R0, S3, S5, R1, S6, S7, *, S8
What is the missing transition? To indicate the missing transition, enter S or R, followed by an index.
The missing transition is: R2
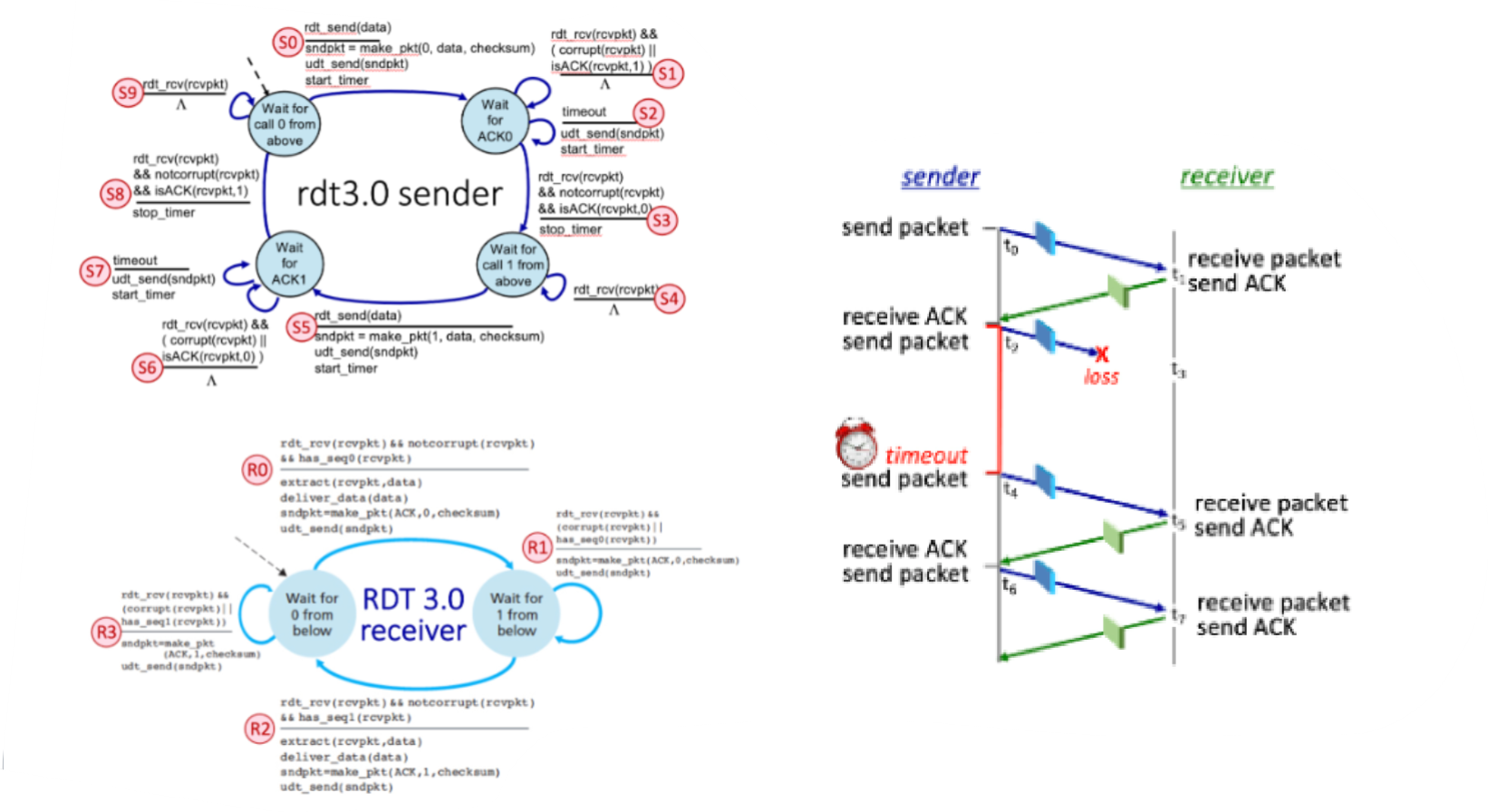
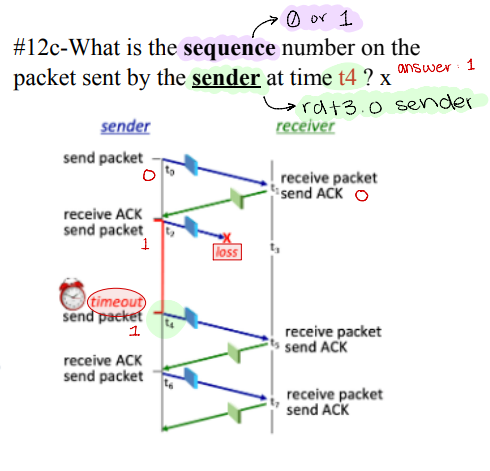
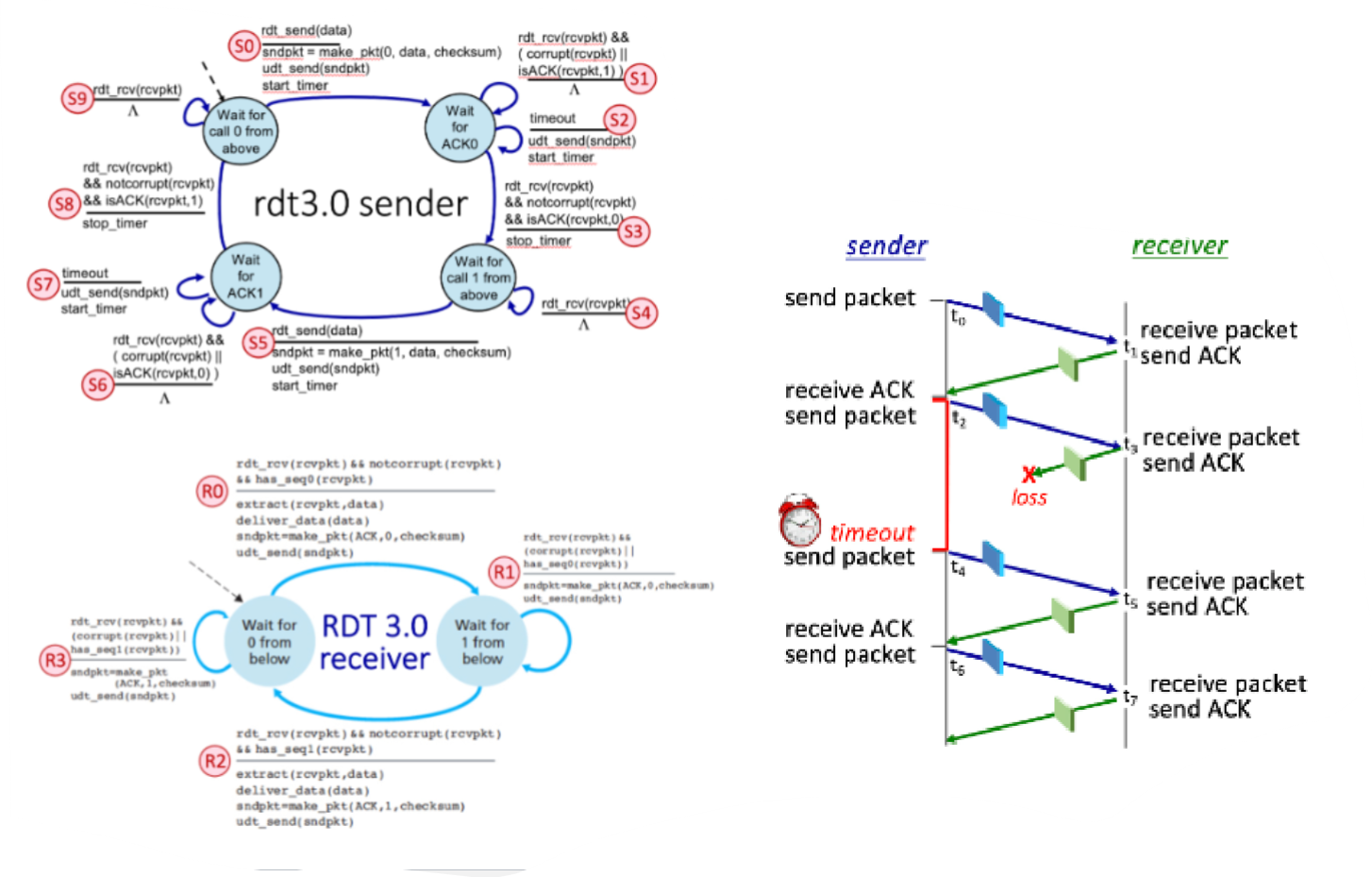
What is the sequence number on the packet sent by the sender at time t4?
1

What is the ACK number on the packet sent by the receiver at time t1?
0
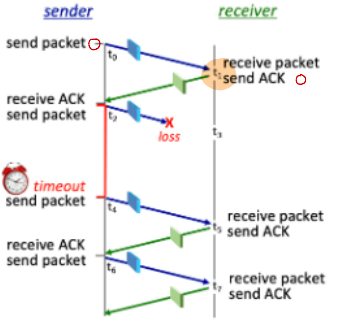
The receiver-to-sender ACK at t3 is lost. What is the ACK number on the packet sent by the receiver at time t1?
0
What is the ACK number on the packet sent by the receiver at time t7?
0
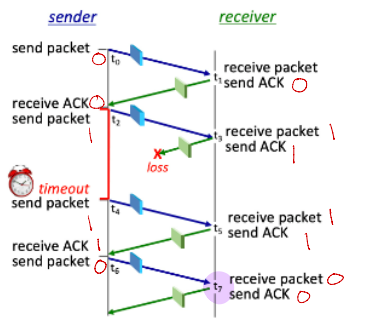
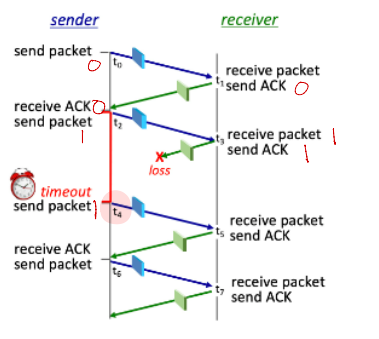
What is the sequence number on the packet sent by the sender at time t4?
1
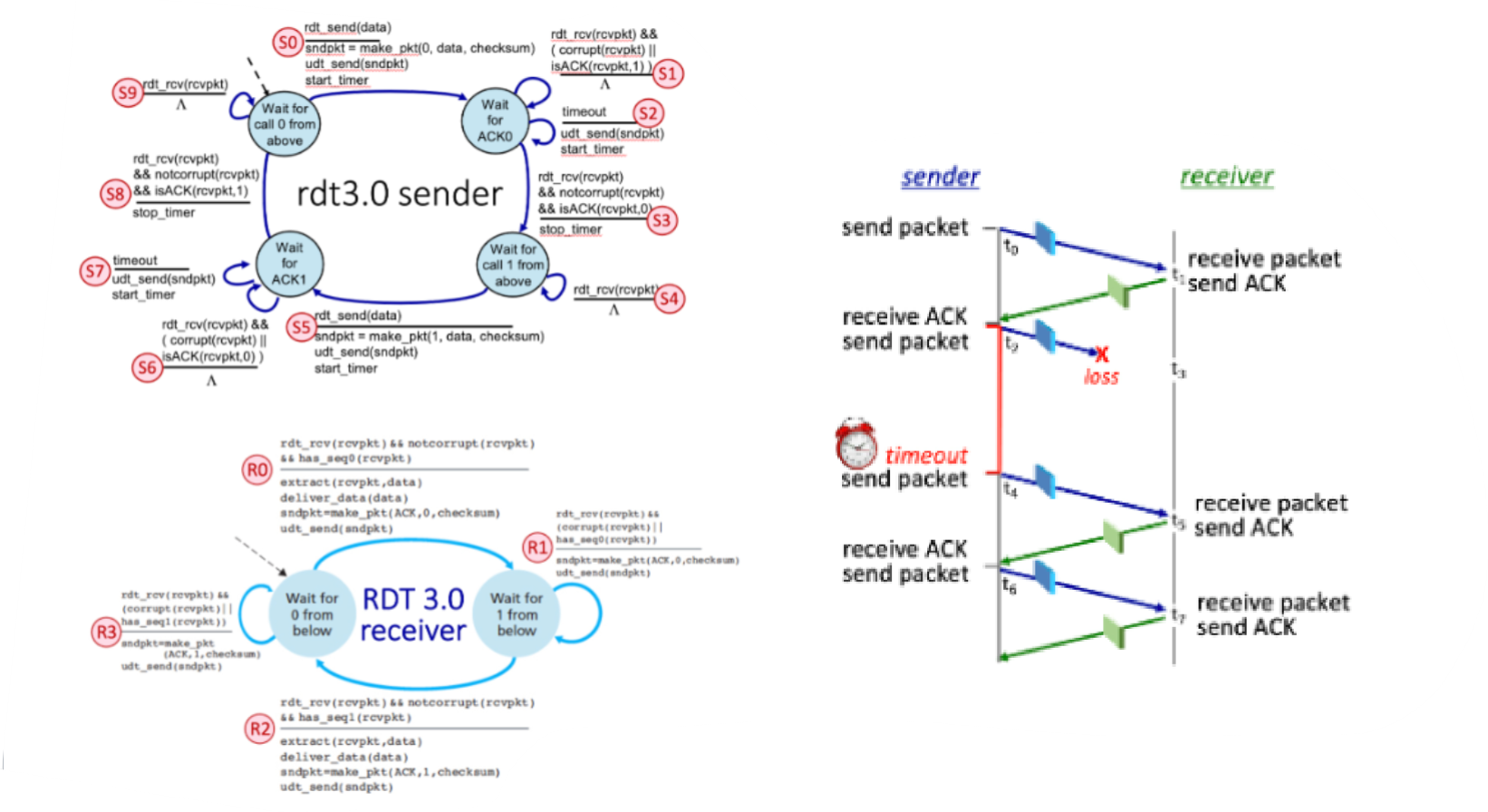
What FSM transition (S0 through S9) occurs at time t2, when the sender starts a timer and then transmits a packet?
S5
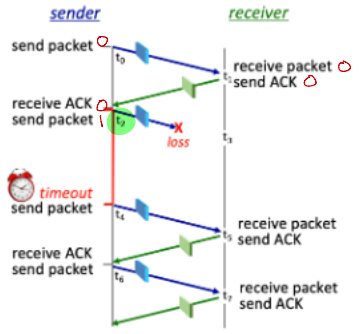
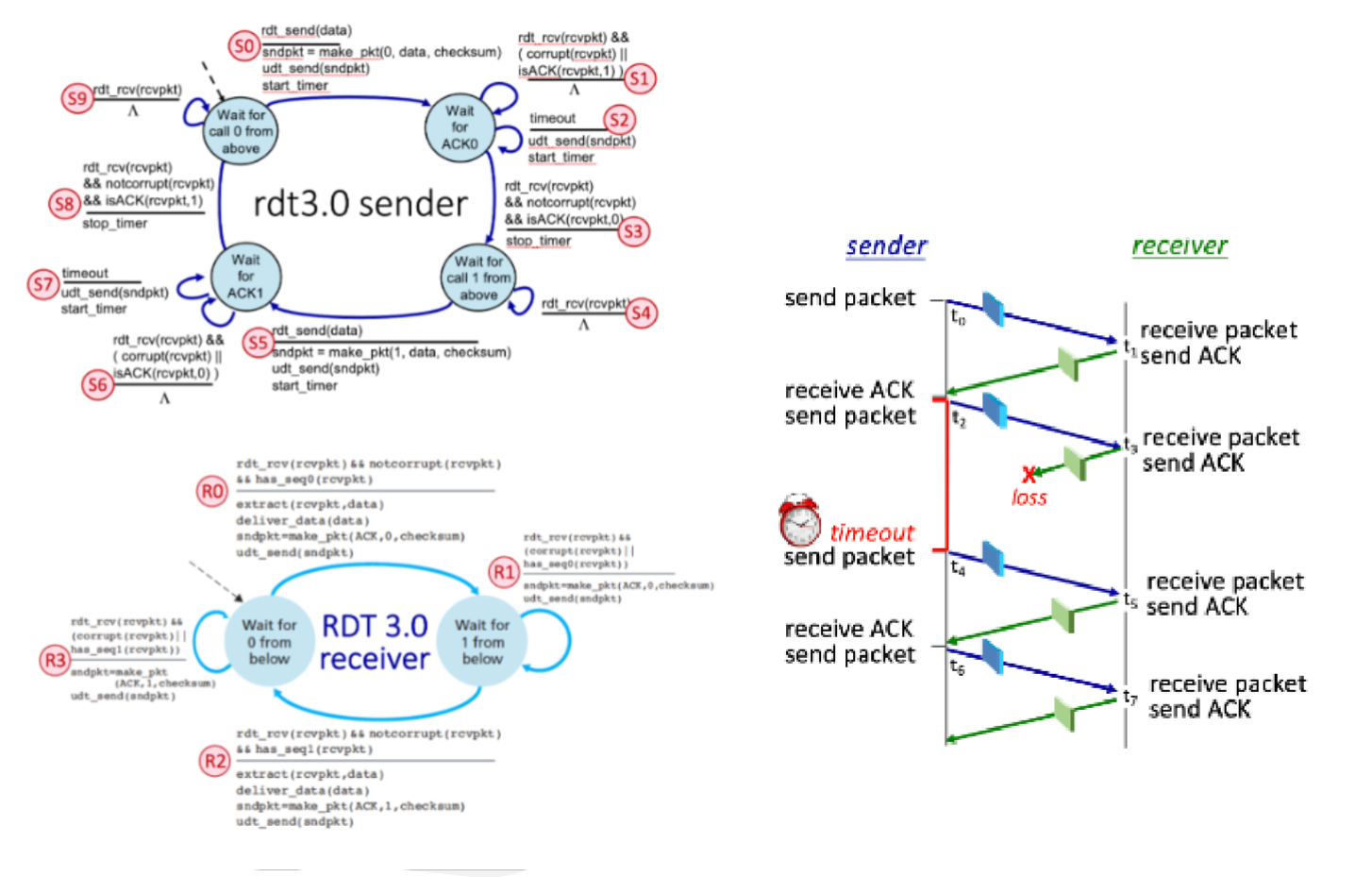
Which sender FSM transition occurs at time t4?
S7
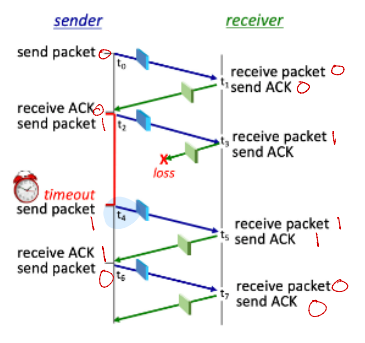

Which receiver FSM transition occurs at time t3?
R2
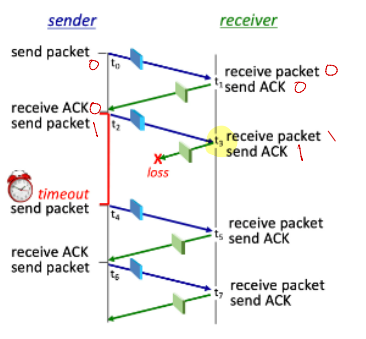
Which receiver FSM transition occurs at time t5?
R3
UDP Demultiplexing
uses destination port number only
TCP Demultiplexing
using 4-tuple:
source IP address
source port number
dest IP address
dest port number
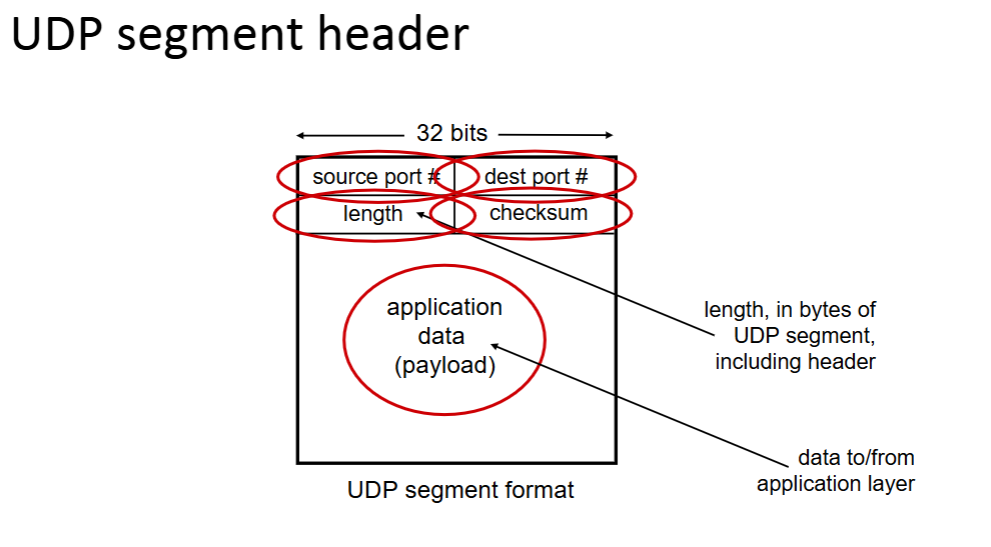
UDP: connectionless transport
“no frills,” “bare bones” Internet transport protocol
UDP segments may be lost or delivered out of order to app
no handshaking between UDP sender and receiver
each UDP segment handled independently of others
TCP: connection-oriented transport
point-to-point: one sender, one receiver
reliable, in-order byte steam: no “message boundaries”
full duplex data: bi-directional data flow in same connection
cumulative ACKs
pipelining: TCP congestion and flow control set window size
handshaking (exchange of control messages) initializes sender, receiver state before data exchange
flow controlled: sender will not overwhelm receiver