Zero Trust
1/13
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
14 Terms
Zero trust
Policy requiring authentication for access to every network resource
Everything is subject to security checks
Includes firewalls, encryption, mfa, system perms, monitoring/analytics, etc
Planes of operation
Split security devices (physical, virtual and cloud) into separate components
Data plane
Device performing security process such as switch, router or firewall
Process frames, packets and network data and processing forwarding, trunking, encrypting, NAT (helps move data between networks)
Physical ports on a router, switch or firewall
Control Plane
Manages actions of data plane (policies or rules for data moving across the network. Routing, session and NAT tables). Forwarding policies or how data should be routed
Configuration of router, switch or firewall
Adaptive Identity
Security controls based on info gathered during identification process.
Looking at source of request such as geographical location
Risk indicators such as relationship to organization such as full/part time, employee/contractor, type of connection, IP address, etc
Strengthen authentication if needed
threat scope reduction
Limit number of possible entry points into network such as restricting access unless in the building or going through a VPN
Policy driven access control
Combine data from adaptive identity and threat scope reduction to form a security policy for that user/device.
Security zones
Where user is connecting from and where they are trying to connect
Coming from untrusted to trusted or internal to external (deny access coming from an untrusted zone)
Create VPNs/groups for each department within the organization and set access rules for each VPN/group
Implicitly Trusted - Device/user coming from a trusted zone going to an internal zone has implicit trust
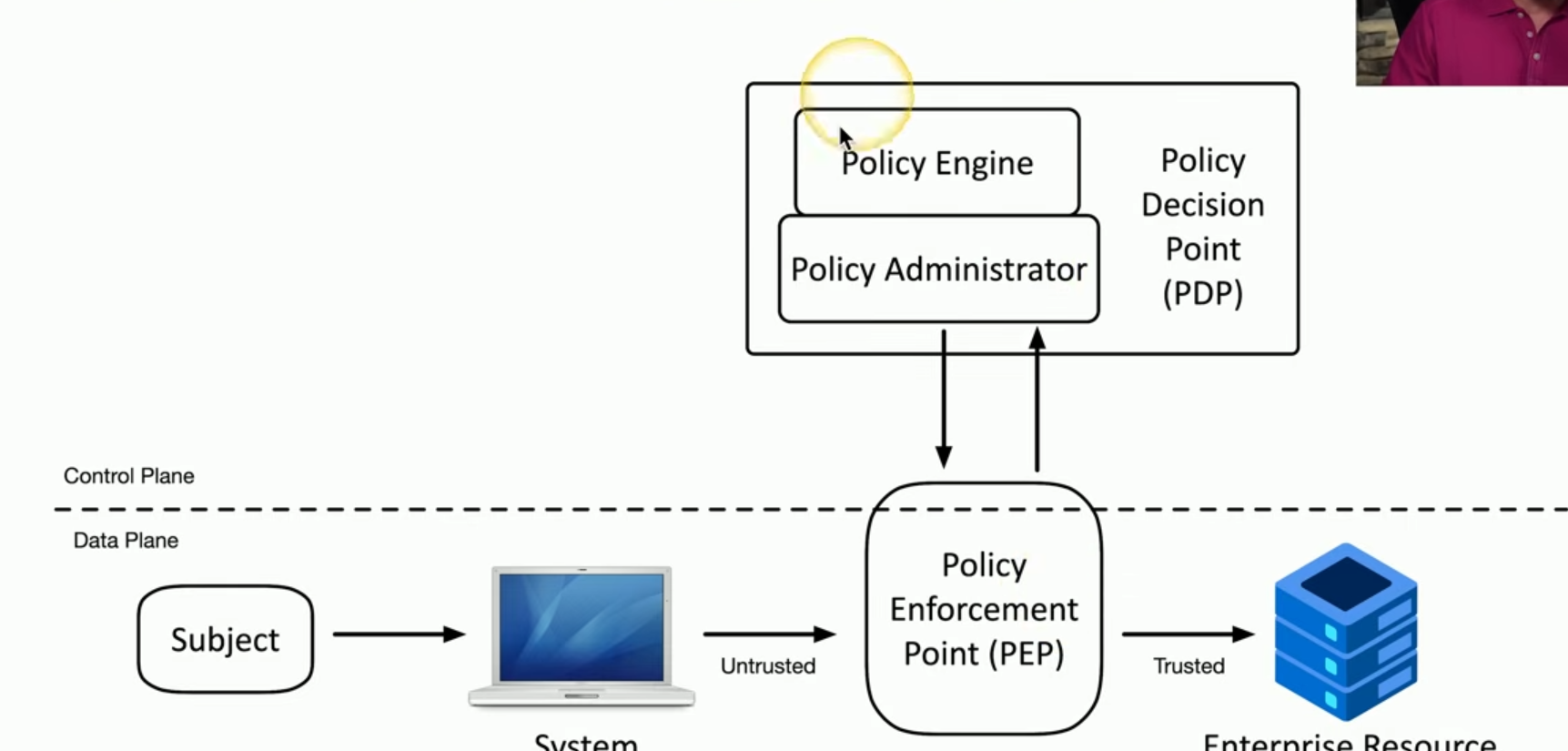
PEP
Policy Enforcement Point (enforces established rules) - Gatekeeper between data coming from a system requesting access to a resource. Can be multiple components working together. Club bouncer ensuring only qualified personnel are allowed entry.
Allow, monitor and terminate connections
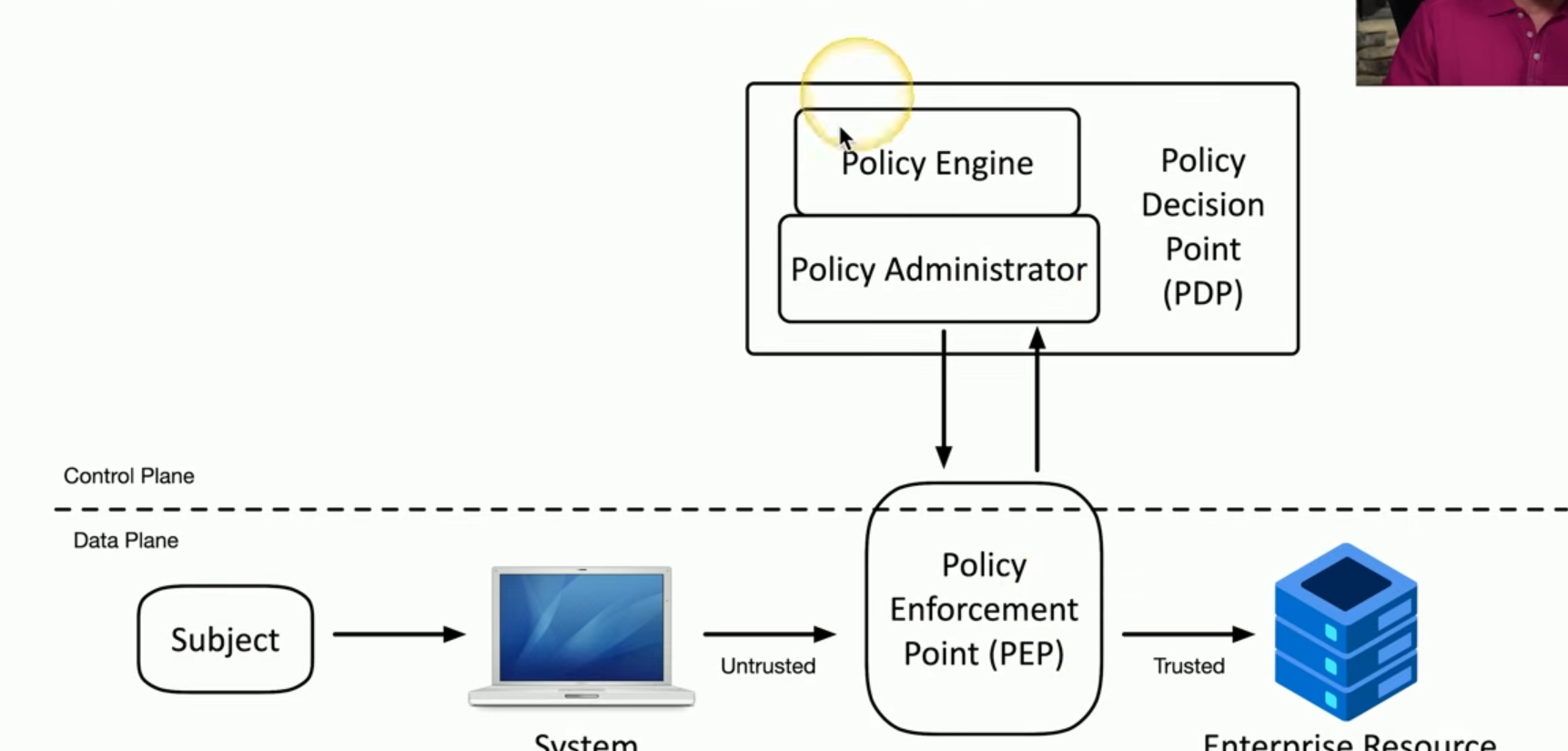
Policy Engine
(creates established rules) Examines requests and makes access decision based on predefined policies. Creates rules for bouncer to enforce
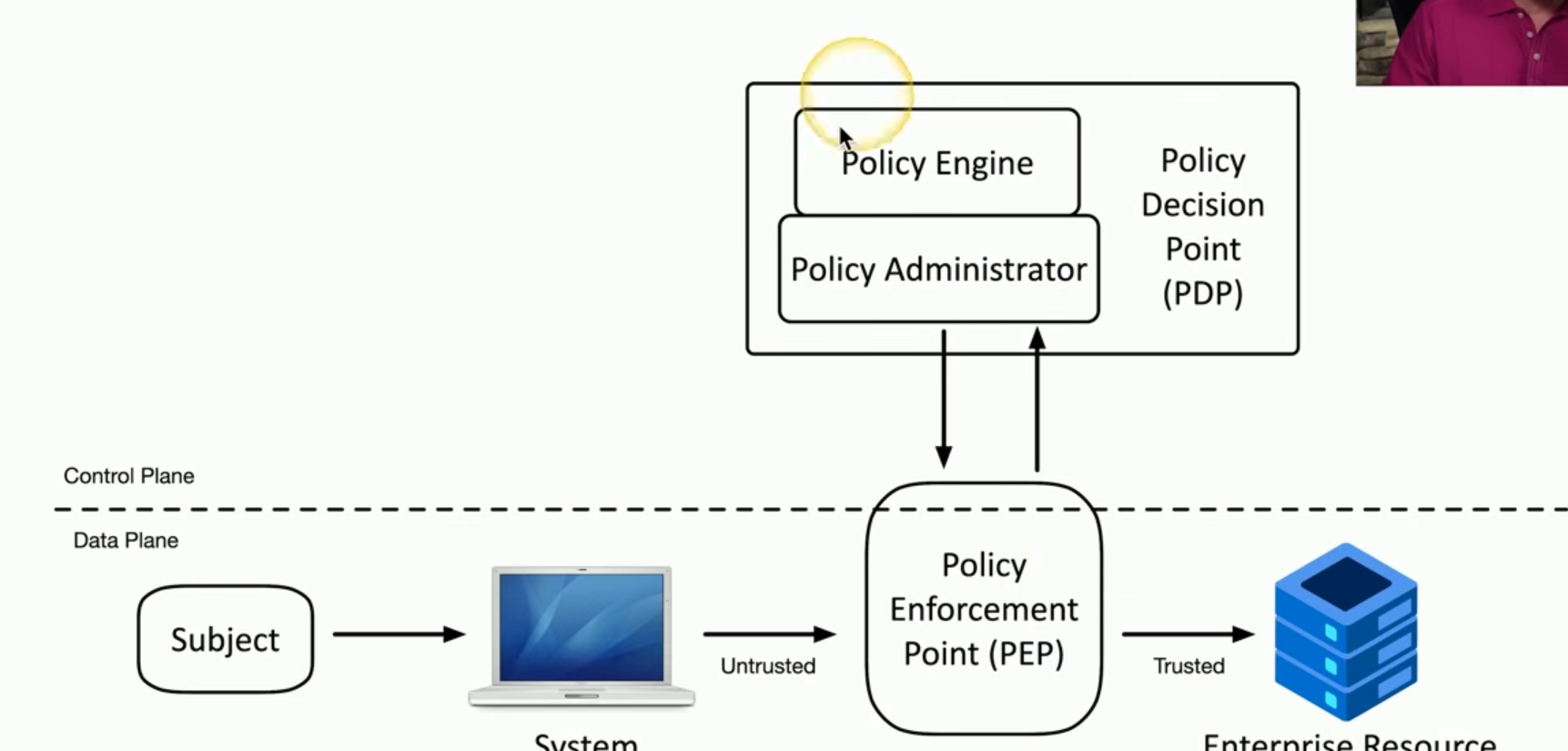
Policy Admin
Provides info from Policy Engine to PEP. Ensures PEP is following established rules. Supervisor ensuring bouncer is following protocol