ENCE361 - Term 1
1/79
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
80 Terms
What is the difference between Harvard and Von Neumann architecture?
Harvard architecture: separated program and data memory.
Von Neumann: shared program and data memory.
What does NVIC stand for, and what does the NVIC do?
NVIC: nested vector interrupt controller. It handles interrupt requests (IRQs) and organises them based on priority.
What does ARM stand for?
Advanced RISC (reduced instruction set computer) machine.
What does GPIO stand for, and what do GPIO pins do?
GPIO: general-purpose input/output.
GPIO pins are a basic input/output interface for MCUs. They can be either analogue or digital, and are extremely customisable. Can be analogue or digital.
What is the purpose of a pull-up or pull-down resistor on a GPIO pin?
When configured to take an input, the pin should be returned to a neutral state (either low or high) rather than being left “floating”. Pull-up and pull-down resistors provide this functionality.
What is the difference between an interrupt and an exception? Provide an example for each.
Interrupt: from an external peripheral e.g. rising or falling edges.
Exception: an interrupt from software, e.g. trying to access invalid memory locations.
What are the four steps involved in servicing an IRQ?
PROLOGUE
1a: Context switch. Current program context is pushed to stack.
1b: Vector table lookup: determine the interrupt’s priority. Steps 1a and 1b happen around the same time.
SERVICE
2: Service the interrupt, with its interrupt service routine (ISR).
EPILOGUE
3: Context restore. Pop program context from stack, return to previous thread.
What are the advantages and disadvantages of polling-based peripheral events?
Polling: checking regularly for peripheral events. Efficient in responding to regular/synchronous events, but a waste of CPU cycles otherwise because checking each peripheral in sequence takes time. With many different devices to check for any application, it becomes difficult to support any kind of real-time execution.
What are the advantages and disadvantages of interrupt-based peripheral events?
Interrupts: halt the background CPU thread to respond to peripheral events. More efficient for asynchronous events, but each interrupt will (generally) take longer to service than polled events due to the context switches required for each one.
On the Cortex-M0+, what are the three negative-priority events and what priorities can users set?
-3 priority: Reset. System reset.
-2 priority: NMI error. Failure of external clock.
-1 priority: HardFault. Software exceptions.
Users can set priorities from 0 to +3.
What is program context? When does it interact with the stack?
Program information, stored in a stack. Pushed prior to ISR, popped after. This is handled by hardware; no need to write separate code.
What is an interrupt vector?
Interrupt vector: the starting program address of the ISR for an interrupt.
What is tail-chaining?
Tail-chaining is an optimization technique in interrupt handling where multiple interrupts can be serviced sequentially, allowing the processor to handle the next interrupt immediately after returning from the current interrupt service routine (ISR), without additional overhead.I
If two of the same interrupts arrive and need servicing one after each other, preempt this and run the two interrupts straight after one another without the enormous time cost required to context switch each time.
Why is an ADC used?
Analogue signals can't be processed by an MCU. Instead, ADCs are used to quantise these values (and sometimes sample them as well) into digitised signals.
What is zero-order holding (ZOH)?
Simply consists of a capacitor to GND. If calibrated properly, the sampled signal will be held "constant" for long enough that the ADC can sample.
What is aliasing, and how does sampling above the Nyquist frequency prevent it?
Aliasing happens when the sampling rate is too low relative to the frequency of the signal; the sampling rate must be above the Nyquist frequency, or twice the signal frequency, to prevent incorrect signal reconstruction. If the sampling rate is at the Nyquist frequency, it could occur at all of the signal’s zero crossings and give a reconstructed function of zero.
Why is buffering used?
Data consumption is generally not synchronous with data generation, so need a way of "delaying" it. Batch-based data processing is also sometimes common, e.g. an FIR
(moving average) signal averaging filter.
What is a circular buffer? What are the problems that can arise from using a circular buffer?
Circular buffer: a list which returns to its first index when full. It overwrites the oldest index when full. However, circular buffers also introduce some data overrun possibilities as data will be lost if the current read index overlaps with the current write index.
What is a double buffer?
Double buffer: divides a circular buffer into two partitions. Batch-processes one partition, while writing data to the other. Provides protection against the data overrun errors found in a circular buffer.
What is switch bouncing?
When pressing a switch, need perfect mechanical contact. Most switches bounce a little (repeat connecting and separating) each time they are pressed. Very hard to predict how long a switch bounce will be for (anywhere between nanoseconds and milliseconds) -- can't really filter out!
What is SR latch debouncing for double-throw switches? What is the main disadvantage with it?
SR latch (consisting of two NAND gates connected, with the output of one going to the input of the other): when a switch bounces (e.g. from the set line), it will not bounce all the way back to the reset line. Thus, it can prevent bounces from disrupting input.
Not used often because double-throw switches are bulky.
What is RC circuit debouncing for single-throw switches?
Single-throw switch: can use an RC circuit with a Schmitt trigger. When open, a capacitor is the only charge to ground; when closed; the switch provides a path to ground and slowly discharges the capacitor. Slow, but requires the switch to be pressed for a certain amount of time to trigger the output. Schmitt trigger helps with this as well.
What is software debouncing? What is the main danger to be aware of when writing a software debouncer?
Software debouncing: uses an FSM. if the pin is read as PUSHED for N_1 consecutive reads, switch the output state to PUSHED. If need, can add similar functionality for releasing the button as well. Design considerations:
Choose a low value for N_1 (pushed): rapid response to button pressing.
Choose a large value for N_2 (released): reduce false release detections.
NB: Need a separate FSM for EACH button.
Be aware of active high and active low user switches, and the difference between them! Can simply translate into PUSHED and RELEASED values using a (very basic) HAL.
Where is the interrupt vector table stored?
Interrupt vector table is at the beginning of FLASH memory.
Where is interrupt priority stored?
Interrupt priority is stored in the interrupt priority register (IPR).
What are the two general-purpose tips for ISR function design?
Functions should be as short as possible
Functions should have no delay loop or halting operations
What is a race condition?
If an interrupt were to be called midway through a function’s execution, the data used in the function could change while the thread is halted, causing unwanted behaviour.
What is binary flag communication, and how does it mitigate race conditions?
Binary flag communication: simply set flag with interrupt (remember to clear it), and then poll the flag to handle it without disrupting anything else.
What is mailbox communication, and how does it differ from binary flag communication?
Mailbox communication: consists of a binary flag and shared data. Interrupt sets data and raises a flag; the data can then be "retrieved from the mailbox". Different from binary flag communication as the mailbox stores data whereas a flag is just a boolean (data would then need to be retrieved from elsewhere).
What is a critical section of code?
Critical section: a section of code which would cause problems if an interrupt were to be called during its execution, e.g. a function accessing and changing a variable, or a function using two variables to change behaviour (the second variable could change midway through the function).
How do you protect against race conditions for critical sections of code?
Generally, disable interrupts before the critical section of code and reenable them afterwards.
The STM32C071 series MCU has 6 timers. What are they?
General purpose timers: TIM2, 3, 14, 16, 17.
Advanced control timer: TIM1.
What are the two functions of a timer?
Functions of a timer:
Period estimation: known as input capture. Captures the value of a free-running counter when triggered, and stores that value in its own register.
Waveform estimation: compare the free-running counter to a user-programmed threshold. Known as output compare. Used to generate PWM. (NB: PWM uses a count-up/down timer generally).
What is a prescaler?
A prescaler extends the period of a timer by only incrementing its counter every 2, or every 4, or 8, etc… timer pulses.
What is the trigger frequency formula for a timer?
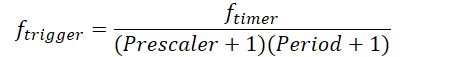
What is a watchdog timer?
Watchdog: acts against system hang. It consists of a downward-counting counter driven by an external clock, and is reset regularly. If the watchdog register reaches an "error" value (usually zero), the system will be reset.
What are the two types of watchdog timer?
Two types of watchdog:
Independent (IWDG): counts down continuously. If it hits zero, system is reset.
Window (WWDG): if the system refreshes too fast or too slow, the system is reset. Good for checking if the CPU has completed its tasks properly.
What is PWM?
PWM: pulse-width modulation. Changes a periodic signal to carry information. The period of the signal remains constant, but PWM changes the proportion of this signal that is high to approximate an analogue signal or to convey information.
What is the duty cycle formula for PWM?
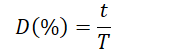
for pulse width t and pulse period T.
How can a user test the average voltage of a PWM circuit?
Can approximate an average analogue voltage using a DC voltmeter.
How can PWM vary the speed of a motor using an H-bridge?
H-bridge: by using PWM to control drive transistors, the motor speed can be varied as the DC motor takes average voltage values (due to its inductive properties).
How do you prevent short circuits when changing the drive direction on an H-bridge?
Short circuits on an H-bridge can occur if two transistors on the same side are turned on at the same time, causing a short to ground. Transistors can be faster to turn on than off, and so a "dead-band delay" is inserted between one transistor switching off and the other turning on to mitigate this.
What is the RMS (root-mean-square) formula for a voltage?

What is the RMS voltage of a sine wave of amplitude A?
Sine wave: .
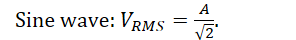
What does an optoisolator do?
An optoisolator can prevent the MCU from being damaged by the electromagnetic interference created by the DC motor.
How does a uniform quantiser work? What is the formula for a quantisation step?
N-bit uniform quantiser divides the input range into intervals (quantisation steps). Δ
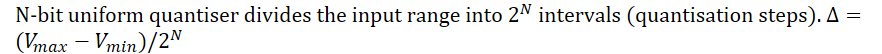
What is the formula for the discrete voltage returned by a uniform quantiser? Why does it include the extra 0.5 term?
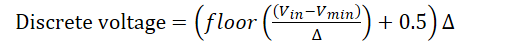
The extra 0.5 is to ensure that the quantised voltage is in the middle of the range of voltages that would trigger it, in order to minimise error.
What is the maximum error magnitude of a quantiser?
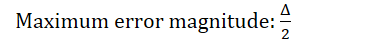
What is the formula for quantisation noise power?
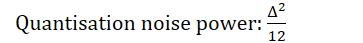
What is a SAR quantiser, and how does it work?
SAR quantiser: successive-approximation. Sends a binary code to a DAC, which produces a value for comparison. If the input is higher than the output, set the current bit to 1, else set it to 0. Move from MSB to LSB.
What is SHA circuitry?
SHA: sample and hold. Samples a voltage and holds it constant while it is quantised.
Describe a flash quantiser, and its advantages and disadvantages.
Flash quantiser: uses quantisers to find in a single clock cycle. Extremely fast, but unbelievably expensive.
Describe how a dual-slope quantiser works, and its pros and cons.
Dual-slope has two phases:
Reset and charge capacitor using the input voltage for a fixed (known) period.
Capacitor then discharges using a reference input, until its voltage reaches zero. By timing these values, the voltage can be determined.
Slow, but very accurate. Often used in multimeters.
What is DMA and what does it do?
DMA: direct memory access. Dedicated system peripheral. Enables data transfer between peripherals, between memory and peripherals, or within memory WITHOUT connecting to the CPU. This allows it to work in parallel with the CPU for significantly reduced overhead.
What are the (four) steps in the DMA handshaking process?
DMA handshaking:
Peripheral sends and holds DMA request.
DMA serves request then sends ACK to peripheral
Peripheral releases request
DMA releases ACK line.
What is the difference between synchronous and asynchronous communication?
Synchronous: a common reference clock tells when to sample the line. Transmission speed and duration determined by clock signal.
Asynchronous: transmitter and receiver agree prior as to transmission speed and duration.
Describe the three types of wired communication.
Simplex: one wire, one-directional. Transmit (Tx) buffer used at transmitter, Rx at receiver. Data transferred in packets.
Full-duplex: two wires, two directions simultaneously. Tx and Rx buffers at both ends.
Half-duplex: one wire, but bidirectional. Data rate is halved compared to full duplex, as wire transmission direction needs to be swapped every N units of time.
Describe the (six) steps in a USART transmission.
Frame structure example:
Line is IDLE HIGH
Pulls down once for start bit
Reads message from LSB to MSB
Parity check (for the number of 1s in the transmission: even or odd?)
Stop bit - releases up.
Line returns to idle high.
What are the two modes of USART?
Two modes of USART:
Blocking: CPU thread waits for transmission and reception to complete. Relies on quick transmission.
Non-blocking: the thread is free from waiting, and an interrupt generated once the transmission ends. This uses DMA to move memory around, and has the highest throughput.
What does I2C stand for?
Inter-Integrated Circuit protocol.
Describe an open drain communication circuit format.
Open drain: all devices have a pull-down transistor, which they can activate to pull the whole line low for ALL peripherals. Any one device can pull the line low: only once all the devices release the line will it return high.
How many buses does I2C communication use? What are their names, and what are they used for?
Two buses: SDA and SCL. Data and clock line.
Why is I2C good for error prevention?
Good for error prevention due to ACK bits with every byte.
Describe the (eight) steps in an I2C transmission.
I2C transmission example:
Both SDA and SCL are IDLE HIGH.
Start condition: SCL high, SDA pulled low.
Peripheral address broadcast, all peripherals listen.
Read or write bit, all peripherals listen.
Selected peripheral (or master) that is RECEIVING data sends ACK by pulling SDA line low. NACK if left high.
Data sent
ACK bit for successful reception of data
Stop bit: SCL left high, SDA released.
What is clock stretching?
Clock stretching: if clock is too fast for slave, the slave will hold the clock line low. This will slow the master down to allow the slave to catch up.
Who sends ACK on I2C read and write instructions?
Slave acknowledges both times on WRITE instructions - always from the perspective of the master.
Slave acknowledges address, then master acknowledges on READ instructions, as it has received data.
What is the difference between interrupt latency, response, and recovery?
Interrupt latency: interval between any event and starting any activity related to servicing it.
Interrupt response: from event and start of ISR.
Interrupt recovery: time for processor to return to the interrupted code.
What is the formula for worst-case interrupt response?
Interrupt response is the maximum of either the longest period where interrupts are disabled (due to critical sections or servicing other interrupts) or any one instruction, and the time it takes to switch context.
What is preemption?
Preemptive ISR: lower and equal priority interrupts are "masked"; less important, so not serviced. Interrupts with higher priority can preempt to interrupt an interrupt.
What are the three file levels in Git? What are the names of the (four) transmissions between different Git file levels?
Three file levels in Git: the server remote repository, local repositories, and working copies.
Push: from local repo to remote repo
Pull: from remote to local
Commit: from working copy to local repo
Update: from local repo to working copy.
What are the (four) aspects of bad code?
Bad code:
Rigidity: changing single behaviour requires much more code to be changed
Fragility: changing single behaviour causes malfunctions
Inseparability: cannot reuse code elsewhere
Unreadability: self-explanatory.
What do naming conventions intend to do? When should you find a better name? (Four answers)
Naming conventions: need a name that REVEALS INTENT.
Find a better name if:
You need a comment to explain it
You need to read code to capture its intent
It is misleading
You can't pronounce it
When is the only time you should use comments?
Comments are only necessary if you’ve tried everything else to reveal your intent.
Why would you use functions? (Three answers)
Why to use functions?
Decrease code rigidity - fewer modifications needed later
Decrease code fragility - won't break code everywhere
Make code more readable
What is good programming practice when writing functions?
Make them small.
Describe layered architecture.
Modules are organised into hierarchical layers, which provides services to the layers above it and depends on the layers below it.
What is the purpose of module encapsulation? How would you share data between modules?
Module encapsulation:
To hide as much as possible from other modules.
Use getters and setters to share data. No globals.
What are the limitations of single-branch Git? (Three answers)
Limitations of single-branch Git:
Difficult to work in parallel
Main branch may be unstable
No separation between tested and untested code.
What are the advantages of feature-branch Git? (Three answers)
Feature branch Git:
Much easier to work in parallel
Main branch is always tested and robust
Quality control is inherent
What is a merge request? What should you make sure before filing a merge request?
Merge request:
When a feature has finished development and wants to be merged back into the main codebase.
Code should already be tested and robust before merging.