IT Fundamentals: Buffies
1/27
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
28 Terms
OSI Model
Otherwise known as the Open Systems Interconnection Model, this describes how data moves from one device to another over a network. It has seven layers, from the closest to the user (Layer 7) to the closest to the hardware (Layer 1).
Physical Layer
Layer 1 —> Transmits raw bits over physical media (the actual wires and signals carrying data)
Examples: Cables (Ethernet, fiber), Wi-Fi signals, Network interface cards
Application
Presentation
Session
Transport
Network
Data Link
Physical
“All People Should Take Noble Data Processing”
Data Link Layer
Layer 2 → Handles node-to-node data transfer over a single physical network link and handles error detection/correction, using MAC addresses and frames; In other words, it makes sure data can move correctly between two directly connected devices (like your computer to your router)
How does the Data Link Layer do this?
Breaks the raw bits from the Physical Layer into frames (structured chunks of data)
Adds headers and trailers so the device knows when a frame starts and ends
MAC addresses are used to identify source and destination devices
(Local street delivery between nearby houses)
Includes the Ethernet (for LAN), and Point-to-Point Protocol (for direct connections between two network nodes)
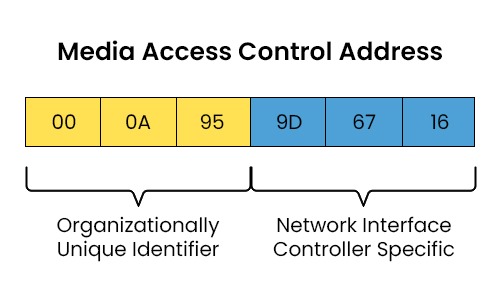
MAC Addresses
Media Access Control address that is assigned to a network interface controller (NIC); it is a 12-digit hexadecimal number that serves as the physical hardware address for devices on a network —> allowing them to communicate with one another on a local network segment
Network
Layer 3 —> Determines how data gets from one network to another through routing and logical addressing
IP addresses, routers, ICMP
Determines the best physical path for data to reach its destination based on network conditions, the priority of service, and other factors
Headers and Trailers
Control data added to the beginning (header) and end (trailer) of a data block for management, routing, and error checking
Transport
Layer 4 —> Ensures complete data transfer, error recovery, and flow control between hosts. This layer segments and reassembles data for efficient transmission and provides reliability with an error detection and correction mechanism
Session
Layer 5 —> Manages and controls the connections between computers. It establishes, maintains, and terminates connections, ensuring that data exchanges occur efficiently and in an organized manner.
Presentation
Layer 6 —> Responsible for translating data between the application layer and the network format. Ensures data is in a usable format for the Application layer, focused on data translation, encryption and decryption, and both compression and decompression
Application
Layer 7 —> Serves as the interface between the end-user applications and the underlying network services, providing network services directly to end-user applications. (examples: web browsers, emails)
Network Protocol
Provides the rules by which the layers of a network communicate with each other.
This, in turn, provides rules by which different networks can communicate with each other.
This also informs network programmers and administrators how to implement, manage, and maintain a network.
TCP/IP
The most commonly used Internet protocol sets the requirements of all computers that communicate over the Internet. Thus, every computer may run other network protocols, but it is a requirement that they run TCP/IP (Transmission Control Protocol/Internet Protocol)
What are some rules of TCP/IP?
Each device on a TCP/IP network must be uniquely identifiable
Large data is split into small packets before transmission.
IPv4
Version of the Internet Protocol (IP), where their main job is to identify devices on a network and route data to the correct destination.; simple and remains widely used today
This version is the older and original IP addressing system, introduced in the early 1980s, where the address format is written as four numbers separated by dots.
About how many unique addresses? 4.3 billion
Checksum
A simple piece of data that, with high probability, tells you whether a message was received correctly; they are often used to verify data integrity but are not relied upon to verify data authenticity
Ping Program
A network diagnostic program that is used to determine whether another computer, or device, is available and reachable over a network.
Sends a small message called an ICMP Echo Request to a target device
Waits for an ICMP Echo Reply
Modulo
Circuit Switching
A communication mechanism that establishes a path between a sender and receiver with guaranteed isolation from paths used by other pairs of senders and receivers.
OLAP Model
Stands for Online Analytical Processing, a category of software tools used to analyze large volumes of data from multiple perspectives.
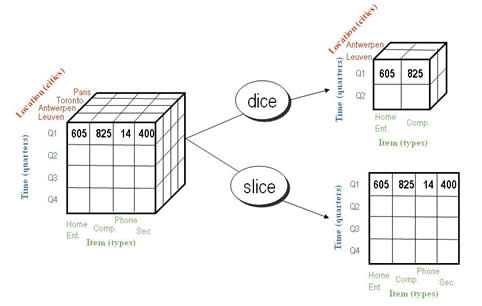
Slicing
Part of OLAP operations, involves creating a subset of the data by reducing the data from multiple dimensions to one dimension.
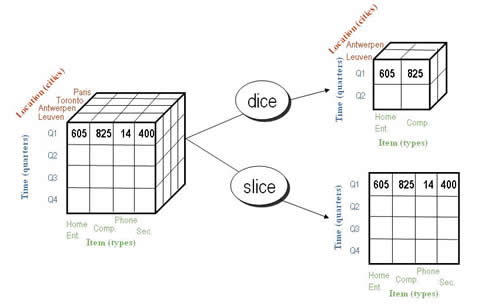
Dicing
Part of OLAP operations; Same as slicing except that the result can be in multiple dimensions, but still obtaining a subset of the data.
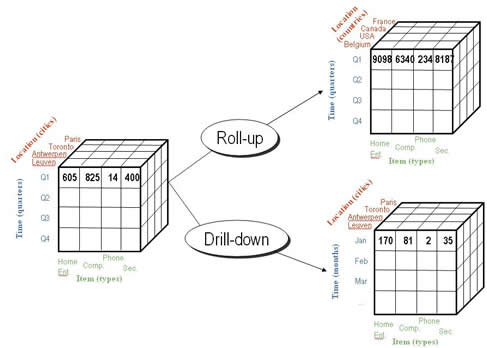
Drilling Up / Down
Part of OLAP operations; exclusively only shifts the view of the data
______ Down: Provides more detail
_______ Up: Provides summarized data
Rolling Up: Provides summarized data but also collapses the data from multiple items into a single value
RAID
Redundant Array of Independent (or Inexpensive) Disks; a data storage technology that combines multiple physical hard drives into one logical unit to improve performance, fault tolerance, or both.
Pivoting
Part of OLAP operations, lets you swap rows and columns (or dimensions) to analyze the same data in a new way.
Example: Rows = Years, Columns = Regions --> Rows = Regions, Columns = Years
Domain Name System
Translates human-friendly website names into IP addresses that computers use to find each other on a network.
Network Port
A logical communication endpoint identified by a number (0-65535) that tells a computer which application or service should receive incoming network data
They work with the IP address, the IP address identifies the device, and the port number identifies the application on that device
Three-Way Network Handshake
A core process that TCP/IP uses to establish a reliable connection between two devices before any data is sent, where it 1)
Network Address Translation (NAT)
This is a process where a router or firewall maps private (internal) IP addresses to a public IP address so that devices (ON A PRIVATE NETWORK) can communicate with external networks like the Internet while conserving the public IP addresses - thereby adding an extra level of security