Computer Science-System Fundamentals
1/58
Earn XP
Description and Tags
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
59 Terms
\-in order to increase the productivity or quality of the system
\- reduce the errors and flaws of the existing
one
the process of thinking about various details and organizing the activities required to achieve the desired goal
*Planning should anticipate potential organization issues*
Lack of
-stakeholder and end user anticipation
-guiding organisational and business strategies
-attention to various organisation issues, such as culture
\-attention to required training
-end user ownership to a system
TF: can existing technology work in the new system
EF: will it be cost effective
\-do the existing organizational practices and procedures support the maintenance and operation of the new system
Schedule feasibility
how long will we wait


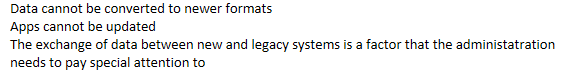
Data cannot be converted to newer formats
Apps cannot be updated
The exchange of data between new and legacy systems is a factor that the administration needs to pay special attention to
\-Replace both information systems to a new one(increased initial cost)
\-Select the best information systems from each and combine them (difficult for employees)
\-Select one and drop the other(policy issues)

\-pos: if the new system fails the company can revert to the old system
\-neg: running 2 systems simultaneously isn’t cost efficient, method may not also be efficient if the 2 systems are completely different
\--it is important to make sure staff are trained before implementing the new system
\--may also be issues if the new system doesn’t work as expected
neg: very risky method for the company, should only be done if the system isn’t critical
neg: very slow, adoption of the new system takes longer
\-requires few it technicians and few software updates
\-compatible with lots of devices/ a wide range of devices support it
\-there is data loss if a SaaS provider goes out of business
\-SaaS integration with other SaaS solutions or software is difficult
\
\-the product functions may not be as clear to the user as the users way of thinking may be different to the developers
\-this may lead to serious problems in the implementation/operation stages of the systems life cycle
\-users may not know how to use the product to its full capacity and even specialists may struggle
\-appropriate comments
\-appropriate code structuring and indentation
\-useful and meaningful variable names
\-appropriate use of data types defined by the user
\-appropriate module headers
List 6 methods of user documentatio
-Email support
-live chat sessions
-FAQ’s
-embedded/integrated user assistance
-manuals
-Online/web portals
Verification vs Validation
Validation: the process of evaluating whether data input follows appropriate specifications and is in reasonable limits
Verification: the process if ensuring the data input is the same as the original source.A way of ensuring this data verification is double entry
Types of testing: Functional Testing, Data Testing,
Functional Testing: Tests each element individually to confirm that they perform and function correctly.
Data testing: normal, abnormal and extreme data is put into the system
Normal:data should be accepted
Data at the limits:data at the boundary of being accepted
Extreme-data that is outside the normal limits, should be rejected when tested
Abnormal:data that is not expected to be entered
Alpha, Beta and Dry-run Testing
-done before the software is made available to the general public, will be carried out by the company that develops the software
-includes comments and suggestions of the users, users outside the company are involved too, this feedback is valuable and can also be used to fix defects and errors
-conducted by hand, the programmer mentally runs the algorithm, they then examine the source code and decide on an output
Integration, User-Acceptance Testing and Debugging
-The entire system is tested at the same time to verify that all components can work together
-determines if the system satisfies the customer needs and is conducted in user premises before accepting transfer of ownership
-the process of finding and correcting the number of bugs in a computer program, there are computer programs that automatically
Different methods of delivering user training
self instuction, formal classes or online training
→ the developers of the new system have to create clear educational material for solving any question that a user may have
→the ways that it may be executed depends on: number of students, availability of instructors, the size of the business and the training budget
Data Loss (Definition)
an error condition where data is lost or destroyed due to systems failure , storage negligence, or even transmission or processing errors
List 4 causes of data loss
-Accidental Deletion
-Physical damage
-Administrative errors
-Data Corruption
2 consequences of data loss
Retrieval can be time consuming
Retrieval may not be possible or can be impractical in some cases
Preventing data loss
-Regular System Backup
-Firewall installation
-Install antivirus
-Storing data in multiple locations
Ways in which updates can be made available
Patches-update software by fixing known bugs and vulnerabilities.However, they have side effects such as introducing new bugs
Updates-update software by adding new fuctionalities of fixing known bugs.Mostly free.
Upgrade- always contain novel functionalities or characteristics as well as cumulative bug fixes.Mostly need to be bought
Releases-final woring versns of software. These have alrady gone through alpha and beta software testing
Hardware and Software
-the physical elements of a computer e.g screen, monitor, CPU etc.
-a series of instructions that can be understood by a CPU, it is comprised of both programs and data
Peripherals
any auxillary device that can communicate and work with a computer e.g mouse, keyboard, printer etc
Computer Networks and Human Resources
-A series of computer systems that are interconnnected and share resources and data eg LAN
-People who are used or could be in use in an organisation,business or economy
Roles that a computer can take in a network Client, thin client and email server
client: recieves data via the network
thin client: a relativeky low performance terminal, which is heavily dependent on the server
email server-manages the flow of email in and out of a network, essentiallly an epost office
Roles that a computer can take in a network Firewall, Router,DNS server, Dumb terminal
Firewall- hardware/software controls data flow access among network entities
Router- a networking device that accepts incoming quantities of devices
DNS server-attributes names to network addresses and therefore resolves namnes by assigning them to the appropriate network entity
Dumb Terminal-a device that usually consists oof a keyboard, a monitor and a network card that is connected to a server or powerful computer
Stakeholders(Definition)
-individuals, groups, teams or organisation that have an interest in the realisation oof a project or might be affected by its outcome
-can also be someone that uses the system often.They will be able to identify flaws and issues in the current system and propose improvements that can be vital to the update of the system
Applications Software (Definition)
Programs designed for the end user that ennable the completion of various tasks in order to increase productivity
Word Processors and Spreadsheets
- Used for the production of any document, and has tools for composition, editing, formatting and printing of documents
-used for the organisation and analysis of data, which is represented in cells organised in rows and collums
Database management systems and Web Browsers
-manages databases (an organised collection of data) and is designed to provide an interface between users and a database
-Used to access, retrieve and present content on the world wide web. Things acessed on web browsers may be identified with URLs, which connect to web servers and requests wanted information and send it back to the web browser
allows for the sending and receiving of digital messages from a single author to one or more recipients.In order for an email to be transferred SMTP is used
Computer Aided Design and Graphic processing software
-A software application that assists engineers to create, modify, analyse and optimise a design.It’s purpose is to increase productivity of the designer and the quality of the design.
-allows a user to manipulate visual images on a computer.Users can manipulate images in various ways such as moving, cropping and scaling
What is Data Migration
Transferring data between formats, storage types and/or computer systems when switching to a new system/ changing/ upgrading/ merging
4 types of incompatibility issues that can arise due to data migration
-Non-recognisable data structures and formats- result in a mismatch of data, e.g. in customer records
-Data lost or corrupted during transfer due to transmission faults/lack of adequate storage. Not usable at destination
-Data misinterpretation due to conventions in different countries e.g. date, measurements, currencies
-Different validation rules between companies- could lead to inconsistent/incorrect results Might not be able to use data while transferring, problem if it's large and takes long
Explain 3 methods of user documentation
-Help files: Easy to access, cheap, can't be misplaced, no internet needed
-Online documentation: Easier to use and search through, can have email support and can update documentation later. However, access limited by internet connection
- Manuals: Printed manuals can be accessed any time (even if system not yet installed) and not restricted by internet connection but can't be updated. Digital manuals more cost efficient and eco-friendlier but online ones restricted by internet connection.
Data Loss (Definition)
an error condition where data is lost or destroyed due to systems failure , storage negligence, or even transmission or processing errors
List 6 causes of data loss
Accidental Deletion
-Firmware corruption
-Physical damage
-Continued use after signs of failure
-Administrative errors
-Data Corruption
2 consequences of data loss
Retrieval can be time consuming
Retrieval may not be possible or can be impractical in some cases
Preventing data loss
-Regular System Backup
-Firewall installation
-Install antivirus
-Storing data in multiple locations