SSE Quiz 2 and 3
1/26
Earn XP
Description and Tags
Secure Software (CEN4033) Final Exam Study Flashcards Quiz 2 and Quiz 3 Answers
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No study sessions yet.
27 Terms
Select all possible outcomes of the buffer overflow attack on software application written in C/C++ programming language.
Program Continues normally, nothing bad or anomalous happens
Segmentation Fault, Memory Error
Overwriting return address with the address of a malicious functino/payload such that the program workflow jumps to the malicious code
Write the hexadecimal address 0x0804AABB in the Little Endian format. Start your answer with 0x.
0xBBAA0408
Java is a memory-unsafe programming language.
False
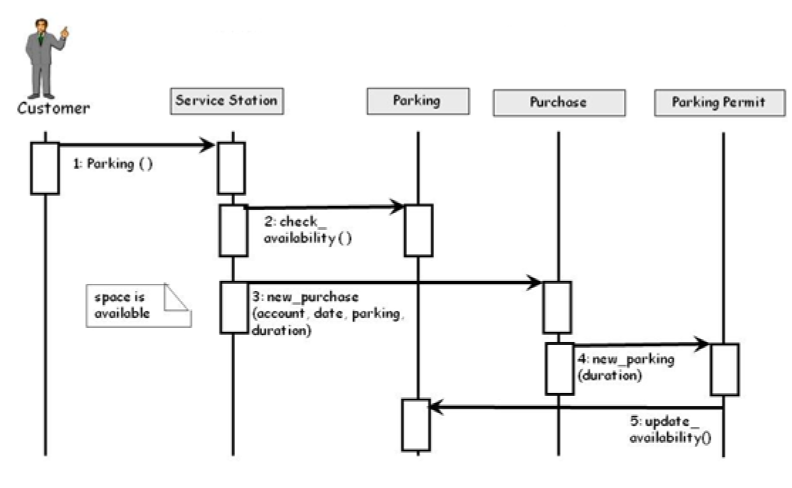
For the sequence diagram shown below, what is the average operation size to purchase the parking permit, based on Travassos metrics for the Object-oriented design?
5 (with margin: 0)
Explain the key difference between "composition" and "aggregation" types of relationships between classes.
Your answer should explain whether it is possible for the child class object to exist without a parent class object for both "composition" and "aggregation" types of relationships between classes .
In composition, the child class object cannot exist independently of the parent class object. When the parent class object is destroyed, so are the child class objects. On the other hand, in aggregation, the child class object can exist independently of the parent class object. Even if the parent class object is destroyed, the child class objects can still exist.
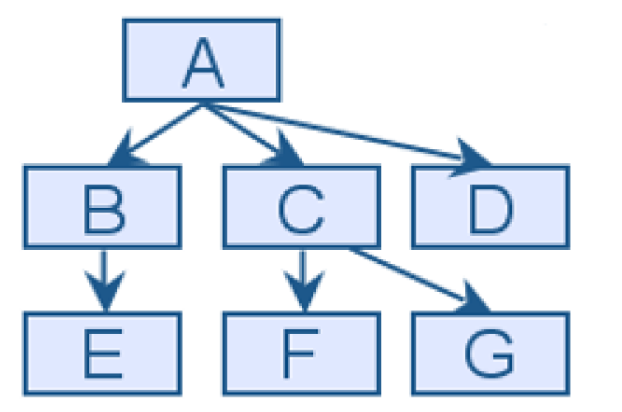
In the Uses Graph shown below, what is the fan-out number for the software unit A?
3
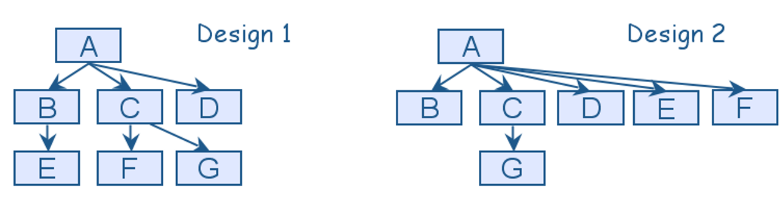
For two alternatives of the object-oriented design shown as Uses Graphs below, which design is better according to Incremental Development design principle? Select one most appropriate option.
Design 1
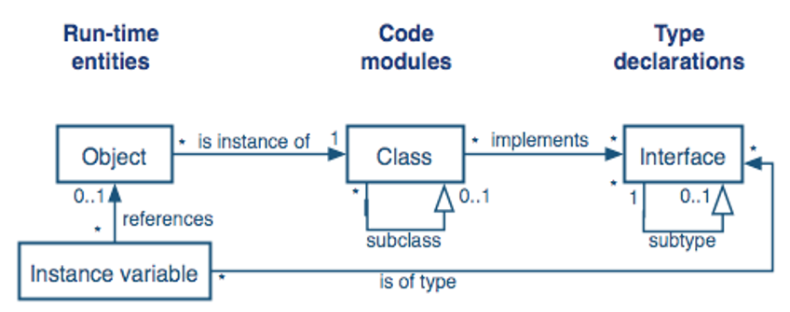
Based on the UML diagram shown below, each object can be an instance of how many classes?
An object is an instance of 1 class
Imagine that a game development company invested $100,000 in developing an educational mobile application (game) for Android and iOS platforms. The company's financial goal is to maximize the profit; and their business planning team started the cost-benefit analysis for the software product, in collaboration with the software development team. Select all the the correct statements from the list below.
The higher Return on Investment (ROI), the better
It is preferable to have shorter time before accumulative benefits recover the costs of software implementation
Developing reusable source code modules can reduce the cost of software development
Select good quality attributes for the software product that is planned to be developed. Select all the options that apply.
Ease of Use
Modifiability
High Return on Investment (ROI)
Robustness
Fault Tolerance
Performance
Reliability
Security
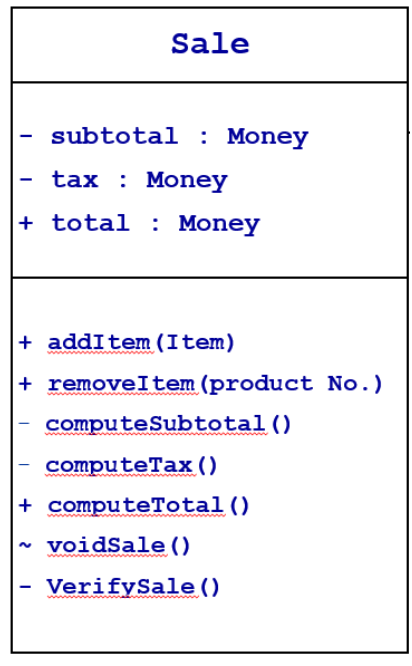
Class "Sale" is represented in the UML Class Diagram as shown below. Briefly explain (in 1-3 sentences) how the Information Hiding design principle would apply for implementation of this class.
The information-hiding design principle will apply to implement this class by hiding subtotals and taxes to allow for the showing of the total amount of money. Some aspects of the class will only sometimes be prominent for every sale, such as voiding the sale and removing the item.
What is the purpose of including the "constructor" method to the class definition? Briefly explain.
The "constructor" method in a class definition is a special method used to initialize objects of that class. It's called when an object of the class is created and can be used to set initial values for object attributes. This preparation of the new object for use often involves accepting arguments that the constructor uses to set required member variables
Explain what the following comment submitted on a web portal aims to do. Assume the web portal allows users to submit comments, stores the history of all the comments submitted in the past, and displays them in chronological order. Choose one most appropriate answer.
My humble opinion <script> var a = document.getElementsByTagName("h1"); a[0].innerHTML="Fake Title" </script>
Change the content of the header 1 (h1) element to "Fake Title" in order to deface the web page
The web portal has a password-based authentication, and asks user to enter username and password on the authentication page. User has entered the following input for "username" text box:
user1'; DROP TABLE orders; #
Select all the correct statements from the list below.
User is trying to run SQL injection attack and remove the table with name "orders"
Secure implementation of the web authentication must filter out any SQL statements from the user input entered in the "username" text box
Secure implementation of the web authentication must encode any special characters from the user input entered in the "username" text box
What is the binary representation of a negative eleven (-11), declared as a signed char variable in C application?
Note: 8 bits are allocated to store the value of a signed char variable in C program.
11110101
Select possible outcomes of "Format String" attack on C application. Select all the options that apply.
Overwrite the return address of the vulnerable function with the address of a malicious code
Abnormal program termination with the "Segmentation Fault"
Change the content of a local variable, which the user is not supposed to access
Print out the content of local variables, which the user is not supposed to access, from the stack memory
For the following C source code:
#include <stdio.h>
#include <string.h>
int foo()
{
char name[128];
printf("Enter the file name: \n");
gets(name);
printf("File name has been entered \n");
return 1;
}
int main()
{
char str1[20];
foo();
printf("Returned from foo(). \n");
return 1;
}
select measures for preventing buffer overflow exploits. Assume this source code is public. Select all the options that apply.
Compile the program with the Address Sanitizer flag -fsanitize=address
Run the compiled executable from the "Valgrind" memory protection tool
Use fgets() C function instead of gets()
Write the 32-bit memory address 0x0408FD84 in Big Endian system. Use hexadecimal format and start your answer with 0x.
0x0408FD84
How many bytes are allocated in stack memory for a local variable of type integer declared in C application as follows:
int i = -1;
Note: assume the 32-bit system.
4 (with margin: 0)
For the unsigned short integer variable i = 32767, what is the result of i + 1 in C/C++ application?
32,768 (with margin: 0)
Using strlcpy() function instead of strcpy() function in C applications can help to prevent buffer overflow attacks.
True
Imagine you are a Chief Technology Officer (CTO) in a software development company. You are asked to organize a software development process to reduce the number of cyber vulnerabilities in the web-based online banking software that your company makes. Briefly (in 2-4 sentences) describe which two Secure Software Design practices you would implement in the company.
The two Secure Software Design Practices I would implement in the company include integration testing and backup testing. Integration testing allows for bugs to be tested and caught at different stages of the development program; testing these bugs allows for cyber vulnerabilities to be caught. Backup testing enables the product to be revisited after implementation to catch vulnerabilities with fresh eyes and see what attackers have tried to do to attack it.
Choose factors that you think should impact CVSS severity score assignment for a discovered software vulnerability registered as a Common Vulnerability and Exposure (CVE) in the public database of vulnerabilities. Select all the options that apply.
The popularity of the software with a discovered vulnerability
Potential damage, including monetary damage, that the software vulnerability exploitation may cause
The number of operating systems/platforms where the software vulnerability is exploitable
Easiness of the software vulnerability exploitation
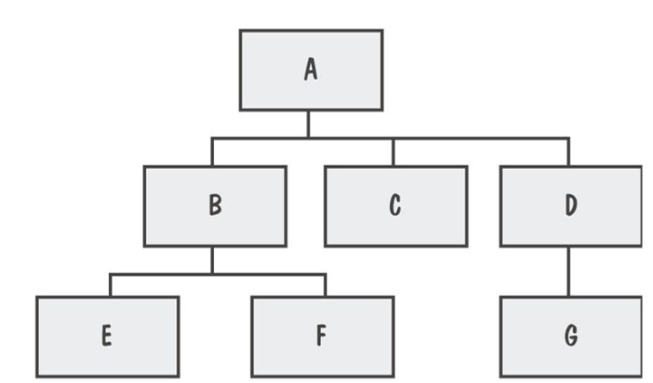
A software product includes seven software modules: A, B, C, D, E, F, G. The hierarchy of the software modules is shown below. Based on the feedback from programmers and software architects, the most problematic software module where the majority of bugs are anticipated is module E. Based on this information, choose one most appropriate integration testing type for the software.
Bottom-Up Integration Testing
Briefly explain why the software testing cannot be used to prove the correctness of software.
Software testing cannot be used to prove the correctness of the software because real-world implementation is needed to see all the possible ways that users use and abuse the software. Software testing cannot consider these ways; it can see if the software operates appropriately to the standards requested but not if it is correct.
Choose the types of software faults that may lead to software failure. Select all the options that apply.
Performance fault
Computation and precision fault
Algorithmic fault
Recovery faults
Stress or overload fault
Syntax fault (language specific)
Documentation fault
Briefly describe one example in which the software performance fault leads to the software failure.
One example of a software performance fault leading to software failure is the case of a system overload due to network congestion. If the software is not designed to handle high levels of network traffic, it can become overwhelmed, leading to slow response times or even a complete system crash. This performance fault, if not addressed, can result in a software failure, disrupting the service and impacting the user experience.