Networking Essentials Lesson 7: Configuring and Troubleshooting Routers
1/55
Earn XP
Description and Tags
Configuring and Troubleshooting Routers
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
56 Terms
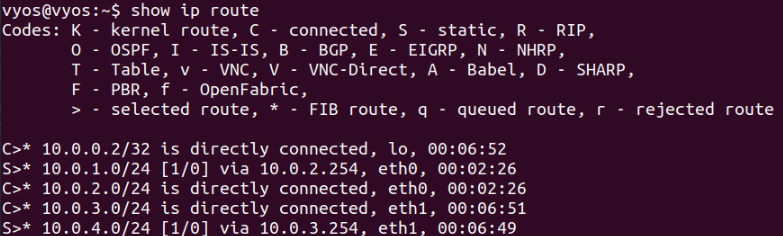
Routing Tables and Path Selection
Protocol
Source of the route
Destination
Can be defined to specific hosts but more generally directed to network IDs
most specific dest. prefix will be selected as the forwarding path if there’s more than one match
Network/host address and prefix
Interface
The local interface to use to forward a packet along the chosen route
Outgoing interface
Might be represented as the IP address of the interface or as a layer 2 interface ID
Gateway/next hop
The IP address of next router along the path to the destination
(Photo is a routing table on a VyOS router showing connected and static route entries.)
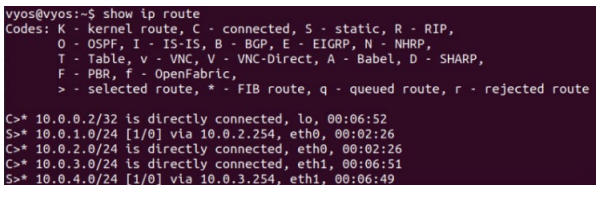
Static and Default Routes
4 categories of routing table entries:
Direct network routes (for subnets to which the router is directly attached)
Paths to remote network routes (for subnets and IP networks that are not directly attached)
Host routes (for routes to a specific IP address) (a host route has a /32 network prefix)
Default route (used when an exact match for a network or host route is not found)
Directly connected routes
IP network/subnet for each active interface
Automatically added to the routing table
Static routes
Added manually to the routing table by administrator
Only changes if edited by the admin
Default route
Identifies the next hop router for a destination that cannot be matched by another routing table entry
Static route used if no other match
0.0.0.0/0 (IPv4) or ::/0 (IPv6)
Simplest way for an edge router o forward traffic to an ISP’s routers
Routing Table Example
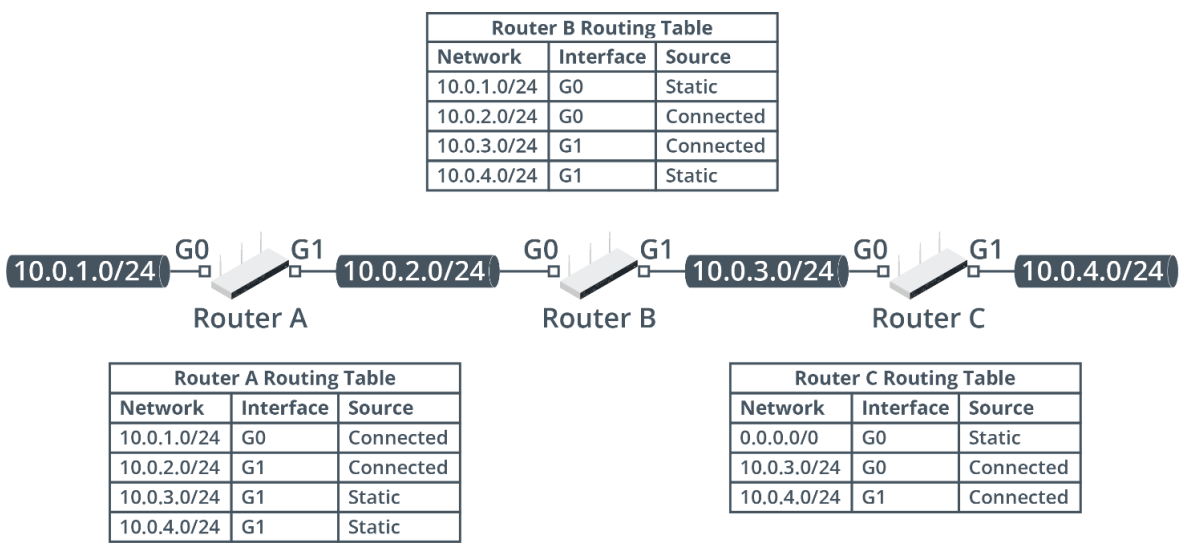
As examples of directly connected, static, and default route entries that might appear in a routing table, consider the following example of three routers connected in a series.
First, consider the routing table of router A:
The router is directly connected to networks 10.0.1.0/24 (via interface G0) and 10.0.2.0/24 (via interface G1).
The router has been configured with static routes to 10.0.3.0/24 and 10.0.4.0/24, both of which are reachable via interface G1.
Router B has been configured in the same way, but here the networks 10.0.2.0/24 and 10.0.3.0/24 are directly connected and the paths to 10.0.1.0/24 and 10.0.4.0/24 are configured as static entries.
Router C has been configured differently. It is directly connected to 10.0.3.0/24 and 10.0.4.0/24, but the only static route configured is for 0.0.0.0/0. This is a default route. While the router has no specific knowledge of networks 10.0.1.0/24 and 10.0.2.0/24, it will forward packets for these destinations over its G0 interface.
Packet Forwarding
When a router receives a packet, it reads the destination address in the packet and looks up a matching destination network IP address and prefix in its routing table
If there’s a match, the router will forward the packet out of one of it’s interfaces by encapsulating the packet in a new frame.
If packet can be delivered to a directly connected network via an Ethernet interface, the router use ARP (IPv4) or Neighbor Discovery (ND in IPv6) to determine the interface address of the destination host.
If packet can be forwarded via a gateway over an Ethernet interface, it inserts the next hop router’s MAC address into the new frame.
If the packet can be forwarded via a gateway over another type of interface (leased line or DSL, for instance), the router encapsulates the packet in an appropriate frame type.
If the destination address cannot be matched to a route entry, the packet is either forwarded via the default route or dropped (and the source host is notified that it was undeliverable).
Encapsulation for interface data link protocol
Hop count
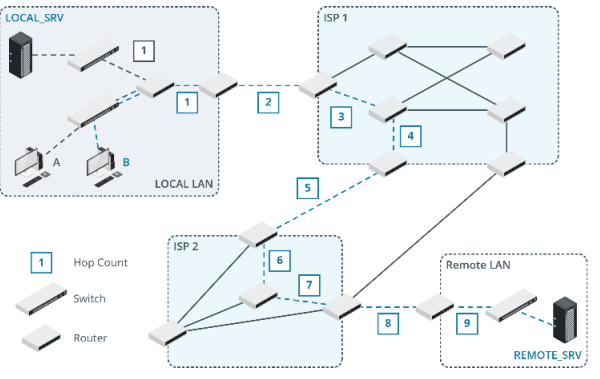
If the packet is forwarded via a gateway, this process is repeated at each router to deliver the packet through the internetwork. Each router along the path counts as one hop.
For example, in the network shown in the figure, host A takes 1 hop to communicate with LOCAL_SRV via a directly connected interface on the LAN router. Note that the switches do not count as hops. Host B takes multiple hops (9) to communicate with REMOTE_SRV, with traffic routed via two ISP networks. Also, observe the alternative routes that could be taken. Do any have a lower hop count?
Time to Live (TTL)
At each router, the Time to Live (TTL) IP header field is decreased by at least 1. This could be greater if the router is congested.
The TTL is nominally the number of seconds a packet can stay on the network before being discarded.
While TTL is defined as a unit of time (seconds), in practice, it is interpreted as a maximum hop count.
When the TTL is 0, the packet is discarded.
This prevents badly addressed packets from permanently circulating the network.
Fragmentation
IP is unreliable, connectionless delivery mechanism
Packets might be lost, delivered out of sequence, duplicated, or delayed
ID, flags, and fragment offset fields record sequence and fragmentation
Fragmentation to fit layer 2 frame maximum transmission unit (MTU)
MTU path discovery
Most systems try to avoid IP fragmentation.
IPv6 does not allow routers to perform fragmentation. Instead, the host performs path MTU discovery to work out the MTU supported by each hop and crafts IP datagrams that will fit the smallest MTU.
Routing Table
Data store on an IP host used to determine the interface over which to forward a packet.
Datagram
Datagrams are data packets which contain adequate header information so that they can be individually routed by all intermediate network switching devices to the destination.
Which of the parameters in the following routing table entry represents the gateway? R 192.168.1.0/24 [120/1] via 198.51.100.254, GigabitEthernet0/1
198.51.100.254-the gateway is the address of the next hop router. 192.168.1.0/24 is the destination and GigabitEthernet0/1 is the interface that the packet should be forwarded out of to reach the gateway.
What type of routing table entry is shown below? S* 0.0.0.0/0 [1/0] via 192.0.2.1
This is a static entry for the default route. The destination 0.0.0.0/0 represents an unknown network and will be matched if there is no match to a more specific destination. 192.0.2.1 is the gateway or next hop router for the default route.
True or false: A router will not forward a packet when the TTL field is 0.
True.
Dynamic Routing Protocols
Build routing information base (RIB)
Share information with other routers (learned routes)
Topology and metrics
Distance vector versus link state
Metrics assess similar routes for use of least-cost path in IP routing table
Algorithm determines nature of metrics
Convergence
All routers agree on network topology
Interior vs. Exterior Gateway Protocols
Routing protocols can be classified according to the way they deal with administrative boundaries.
Interior Gateway Protocol (IGP)
Routing within an autonomous system (AS)
Identifies routes within an AS
Exterior Gateway Protocol (EGP)
Routing between autonomous systems
Classless vs. classful protocols
IPv6 support
Legacy classful protocols do not use subnet masks or network prefixes. They determine an IPv4 network ID based on the value of the first three bits of the address.
Some older protocol versions support IPv4 only.
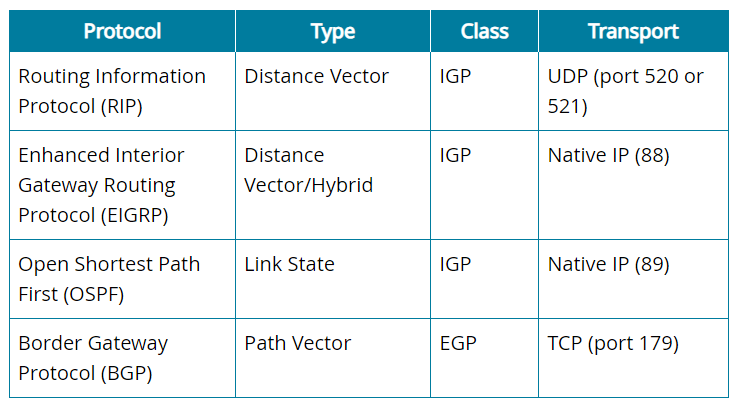
Routing Information Protocol (RIP)
Distance vector routing protocol
Next hop (vector)
Hop count (distance)
Considers only one metric: route w/lowest hop count
Slow convergence and inefficient updates
Maximum hop count of 15
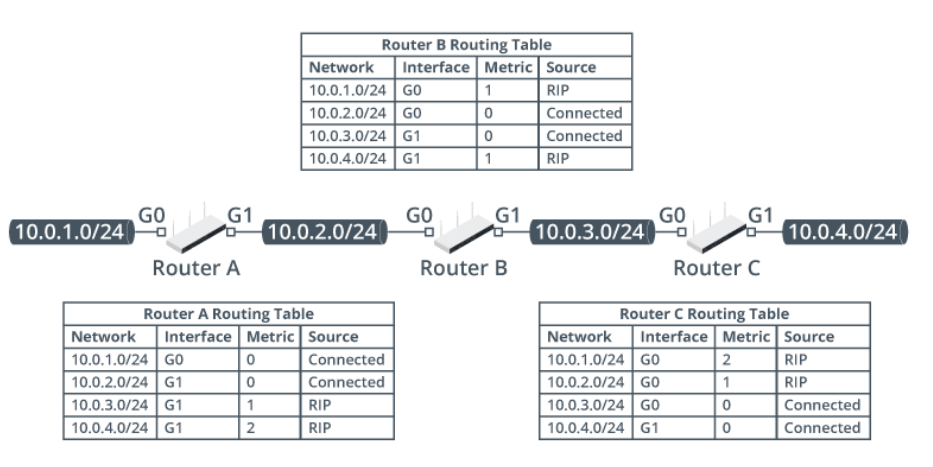
In the following figure, RIP has been used to propagate route information between three routers connected in a chain. Router A learns about networks 10.0.3.0/24 and 10.0.4.0/24 from Router B. It adds 1 to the hop count metric of these routes. Router B learns about 10.0.1.0/24 from Router A and about 10.0.4.0/24 from Router C. Router A and Router C do not exchange any information directly. The distance vector process by which Router A learns about Router C's networks is often referred to as "routing by rumor."
Routing Information Protocol (RIP part 2)
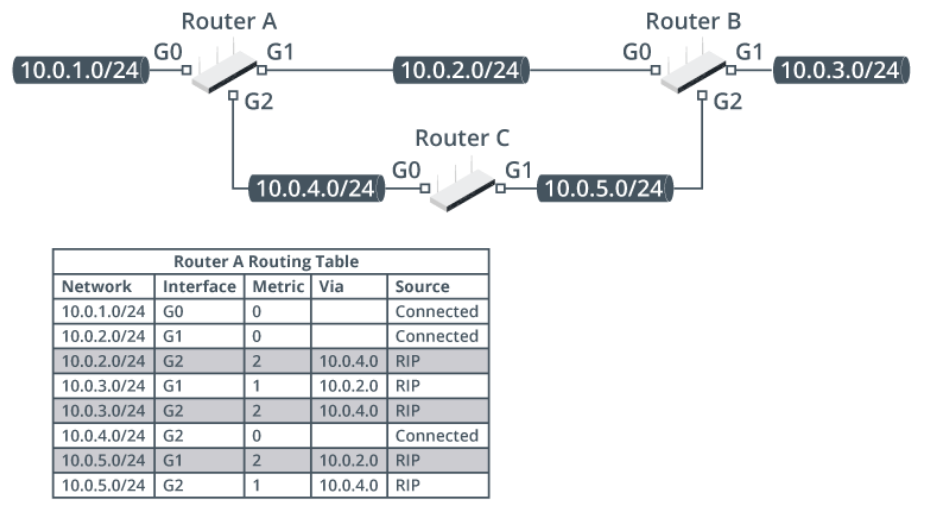
The following example illustrates a mesh topology where there are multiple paths between networks. Router A has two possible paths to network 10.0.3.0/24, which it learns from Router B and Router C. It can forward a packet out of its G1 interface over network 10.0.2.0/24, which will take one hop to reach the destination. It could also forward the packet out of G2 and reach the destination via Router C and then Router B. This takes two hops and so is not used as the preferred route.
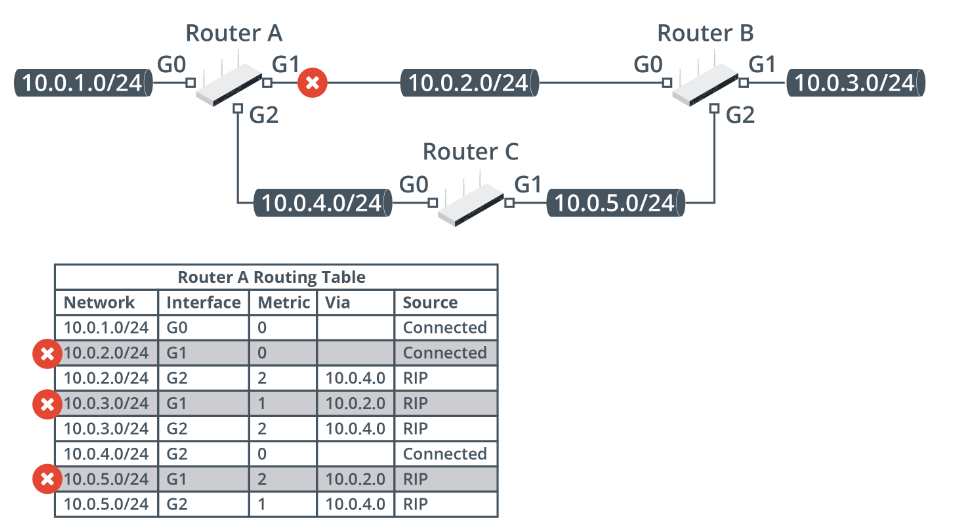
If Router A's G1 link goes down, those entries will be removed from the routing table and the alternative routes via 10.0.4.0/24 will be selected:
To help prevent looping, the maximum hop count allowed is 15. Consequently, this limits the maximum size of a RIP network, since networks that have a hop count of 16 or higher are unreachable.
RIP Versions
RIPv1
Classful and uses inefficient broadcasts to communicate updates over UDP port 520
RIPv2
Classless and uses more efficient multicasts over UDP port 520.
Supports authentication
RIPng
IPv6 support over UDP port 521
The simplicity of RIP makes it suited to small networks with limited failover routes.
Distance vector algorithms require that routers periodically propagate their entire routing table to their immediate neighbors.
This is not scalable to environments with large numbers of networks.
Distance vector algorithms provide for slower convergence than link state algorithms.
For more complex networks with redundant paths, other dynamic routing protocols should be considered.
Enhanced Interior Gateway Routing Protocol (EIGRP)
Update to Interior Gateway Protocol to support classless addressing
Advanced distance vector/hybrid with administrator weighted metric
Like RIP, EIGRP is a distance vector protocol because it relies on neighboring routers to report paths to remote networks.
Bandwidth
Delay
Best convergence performance
Runs over IP directly (protocol number 88) using multicasts
Encapsulated directly in IP datagrams, rather than using TCP or UDP
RIP sends periodic updates of its entire routing information base
EIGRP sends a full update when it first establishes contact with a neighbor and thereafter only sends updates when there is a topology change.
This is more efficient and less disruptive to large networks, giving it the best convergence performance in many scenarios.
Up to 255 hops
Open Shortest Path First (OSPF)
Link state interior gateway protocol suited to complex private networks
Group related networks by area hierarchy
Supports classless addressing
Runs over IP directly (protocol number 89) using multicasts
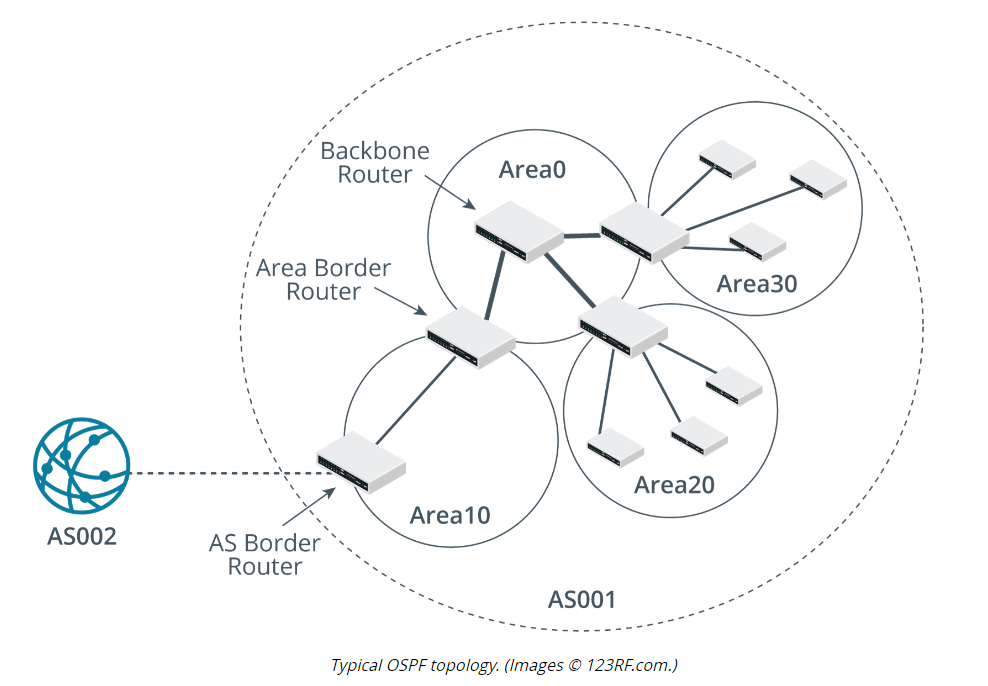
Border Gateway Protocol
Classed as hybrid or path vector
Usually deployed as an Exterior Gateway Protocol
Supports routing on the Internet
Autonomous Systems (ASes) hide internal network complexity from Internet routers
Autonomous System Number (ASN)
BGP routers exchange AS path data between Autonomous Systems
Supports classless addressing
Runs over TCP on port 179
BGP prioritizes stability and can be slow to converge.
BGP works with classless network prefixes called Network Layer Reachability Information (NLRI).
Path selection is based on multiple metrics, including hop count, weight, local preference, origin, and community.
BGP is not a pure distance vector algorithm.
In fact, BGP is more usually classed as a path vector routing protocol.
Administrative Distance
Longer prefixes preferred for path selection
198.51.100.0/24 g0
198.51.100.0/28 g1
If the router receives a packet for 198.51.100.1, the packet will be routed via g1 , as that has the longer and more specific prefix.
Protocols add one route per destination prefix to global IP routing table
Routing protocol uses metric to determine least-cost path
Router uses administrative distance to prefer paths to same destination learned by different protocols
This means, for example, that given identical prefix lengths, a static route will be preferred to anything other than directly connected networks and that a route discovered by OSPF would be preferred to one reported by RIP. The value of 255 for unknown routes means that they will not be used.
Conversely, a static route with a high AD could be defined to function as a backup if a learned route update fails. In normal circumstances, the router will prefer the learned route because it has a lower AD.
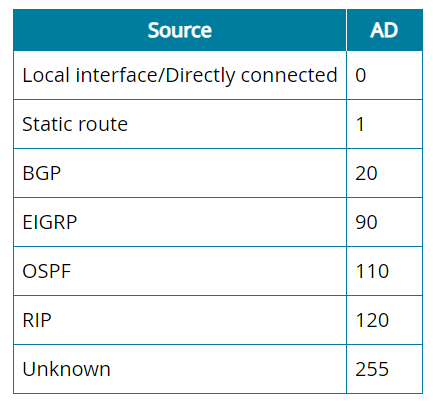
Distance Vector
Algorithm used by routing protocols that select a forwarding path based on the next hop router with the lowest hop count to the destination network.
Link state
Algorithm used by routing protocols that build a complete network topology to use to select optimum forwarding paths.
Convergence
The process whereby routers running dynamic routing algorithms agree on the network topology.
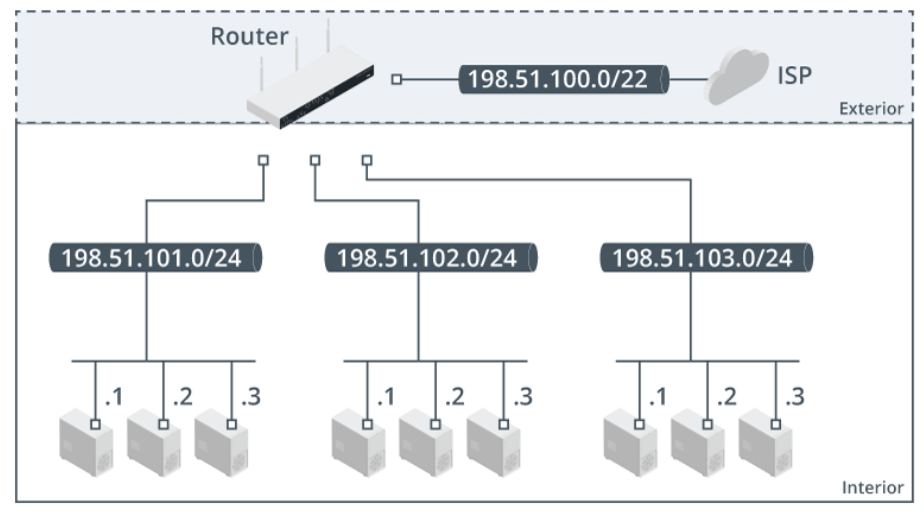
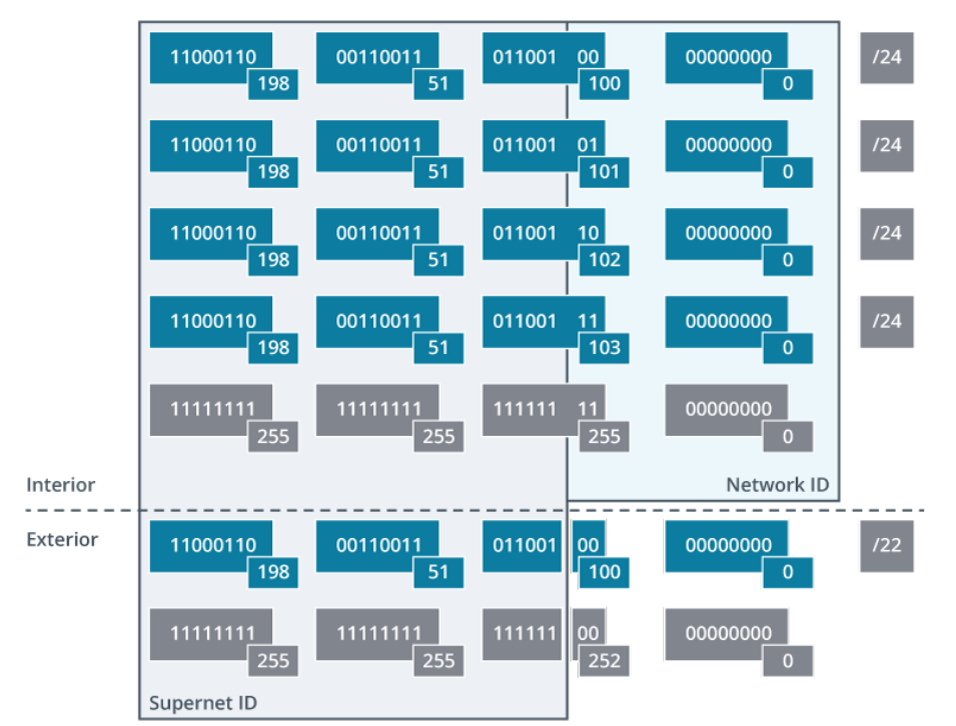
Classless Inter-domain Routing
Classless Inter-Domain Routing (CIDR) uses bits normally assigned to the network ID to mask the complexity of the subnet and host addressing scheme within that network. CIDR is also sometimes described as supernetting.
For example, rather than allocate a Class B (or /16) network address to a company, several contiguous Class C (or /24) addresses could be assigned. Four /24 network addresses gives 1,016 hosts.
However, this would mean complicated routing with many entries in the routing tables to represent four IP networks at the same location.
Using CIDR collapses these routing entries into one single entry. If the network addresses assigned to a company were 198.51.101.0 through to 198.51.103.0 and you wanted to view this as one network, you need to allocate two bits from the network address to summarize the four networks.
This makes the supernet prefix /22 or the subnet mask 255.255.252.0.
Variable Length Subnet Masks
Use address space in IPv4 network more efficiently
Rather than use the same mask for all subnets, use different mask lengths according to host numbers per subnet
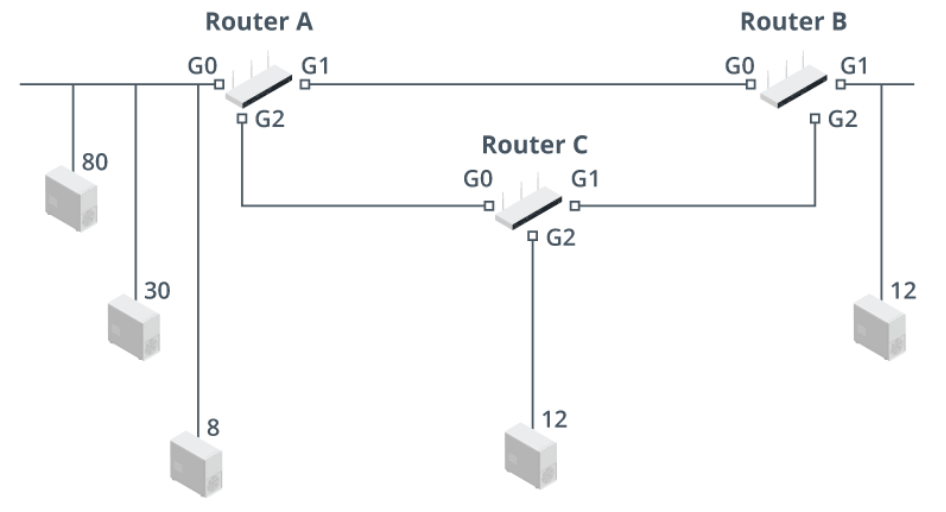
VLSM Design
Which factors are used by default in EIGRP to identify the least-cost path?
The lowest bandwidth link along the path and the sum of latency along the path.
What is ASN and how does it assist route aggregation?
An Autonomous System Number (ASN) identifies a group of network prefixes under the administrative control of a single entity (such as an ISP).
Imagine an AS as being like a town's post office. Mail goes from post office to post office until it reaches the right town, and that town's post office will then deliver the mail within that town.
Typically, each AS is operated by a single large organization, such as an Internet service provider (ISP), a large enterprise technology company, a university, or a government agency.
The AS can be advertised to other ASs through a single prefix (route aggregation), hiding the complexity of the internal network from other autonomous systems.
Similarly, data packets cross the Internet by hopping from AS to AS until they reach the AS that contains their destination Internet Protocol (IP) address. Routers within that AS send the packet to the IP address.
Of the routing protocols listed in the CompTIA Network+ syllabus, which has the highest default value AD and does that make it more or less trusted than other protocols?
Routing Information Protocol (RIP) has a default administrative distance (AD) value of 120. In AD, lower values are preferred, so RIP is less trusted than other protocols.
An IP network comprises hundreds of subnets deployed to offices in multiple geographical locations. Of the routing protocols listed in the CompTIA Network+ syllabus, which is best suited to this scale of network and why?
The hierarchical design of Open Shortest Path First (OSPF) means that it can divide the network into areas to represent different sites, reduce the size of routing tables, and ensure fast convergence. That said, Enhanced Interior Gateway Routing Protocol (EIGRP) can also support large networks and can have better convergence performance and so could be an equally good choice. Routing Information Protocol (RIP) is too limited to meet the requirements of a large network. Border Gateway Protocol (BGP) is not typically used on private networks as it is slower than OSPF or EIGRP and relatively complex to configure.
A company has eight networks, using the subnet addresses 192.168.0.0/24, 192.168.1.0/24 … 192.168.7.0/24. What network prefix and subnet mask can be used to summarize a supernet route to these networks?
It takes 3 bits to summarize eight networks (2^3 =8). Subtracting 3 bits from the existing network mask makes the supernet network prefix /21. The third octet of the mask will use 5 bits, which is 248 in decimal (25= 248), so the full mask is 255.255.248.0.
True or False? VLSM means using more than one mask to subnet an IP network.
True. By using different mask sizes, variable length subnet masking (VLSM) allows designers to match subnet sizes to requirements more precisely.
What is an ASN (autonomous system number)?
Each AS is assigned an official number, or autonomous system number (ASN), similar to how every business has a business license with an unique, official number. But unlike businesses, external parties often refer to ASes by their number alone.
AS numbers, or ASNs, are unique 16 bit numbers between 1 and 65534 or 32 bit numbers between 131072 and 4294967294. They are presented in this format: AS(number). For instance, Cloudflare's ASN is AS13335. According to some estimates, there are over 90,000 ASNs in use worldwide.
ASNs are only required for external communications with inter-network routers (see "What is BGP?" below). Internal routers and computers within an AS may not need to know that AS's number, since they are only communicating with devices within that AS.
An AS has to meet certain qualifications before the governing bodies that assign ASNs will give it a number. It must have a distinct routing policy, be of a certain size, and have more than one connection to other ASes. There is a limited amount of ASNs available, and if they were given out too freely, the supply would run out and routing would become much more complex.

Edge Routers
Placement
Hosts in same IP network/subnet must not be separated by a router
Hosts in different IP networks/subnets must be separated by a router
Edge routers on network perimeter
Customer edge (CE) to provider edge (PE)
L1/L2 type (metro-optical, leased line, DSL, cable)
SOHO-class routers versus enterprise routers
(First image is an integrated services router. Customer edge. This is a combination of DSL internet w/ethernet switch, Wi-Fi, and VoIP. For smaller, simpler places, like a house, and holds probably about 26 devices.)
(Second image is an advanced services router. Provides network edge connectivity.)

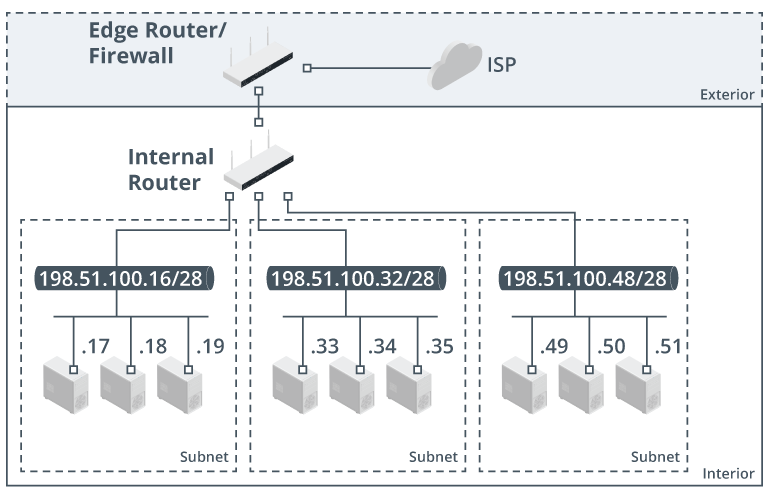
Internal Routers
Implement subnets and internal borders/areas
Subinterfaces
Split single physical connection to per-VLAN subinterfaces
(Second photo)
Layer 3 switches
Hardware optimized to forward between VLANS
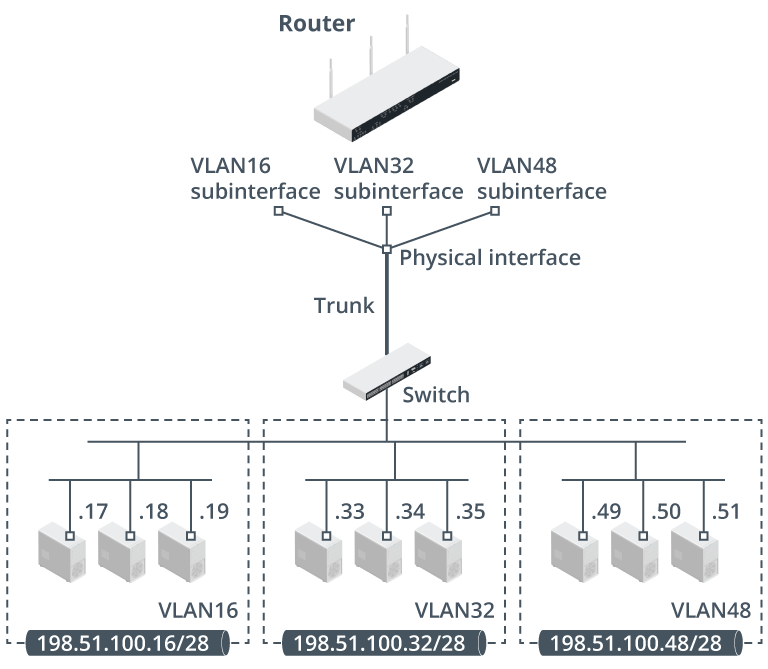
Router Configuration
Management interface
Console port
Loopback interface
Configure router interfaces
IP configuration
L2 configuration
Configure static routes and routing protocols
show route
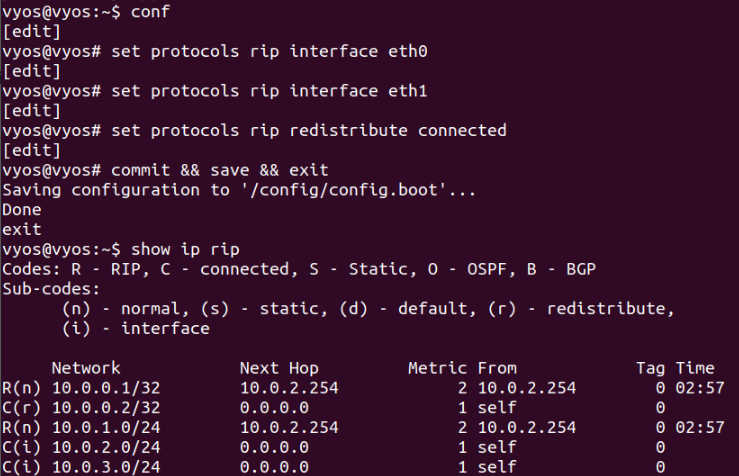
route
Trouble Windows and Linux hosts
Verify default gateway
Add static route
To add a route, the syntax for the Windows version of the tool is:
route [-f -p] add DestinationIP mask Netmask GatewayIP metric MetricValue if Interface
The variables in the syntax are defined as:
DestinationIP is a network or host address.
Netmask is the subnet mask for DestinationIP.
GatewayIP is the router to use to contact the network or host.
MetricValue is the cost of the route.
Interface is the adapter the host should use (used if the host is multihomed).
For example:
route add 192.168.3.0 mask 255.255.255.0 192.168.5.1 metric 2
![<ul><li><p>Trouble Windows and Linux hosts</p></li><li><p>Verify default gateway</p></li><li><p>Add static route</p><p></p></li><li><p>To add a route, the syntax for the Windows version of the tool is: </p><ul><li><p>route [-f -p] add DestinationIP mask Netmask GatewayIP metric MetricValue if Interface</p></li></ul></li></ul><p></p><ul><li><p>The variables in the syntax are defined as:</p><ul><li><p>DestinationIP is a network or host address.</p></li><li><p>Netmask is the subnet mask for DestinationIP.</p></li><li><p>GatewayIP is the router to use to contact the network or host.</p></li><li><p>MetricValue is the cost of the route.</p></li><li><p>Interface is the adapter the host should use (used if the host is multihomed).</p></li></ul></li></ul><p></p><ul><li><p>For example:</p><ul><li><p style="text-align: start"><span style="font-family: Cutive Mono, monospace">route add 192.168.3.0 mask 255.255.255.0 192.168.5.1 metric 2</span></p></li></ul></li></ul>](https://knowt-user-attachments.s3.amazonaws.com/ef373891-6d89-4379-bc31-0e6c90f39320.jpeg)
tracert and traceroute
traceroute
UDP probes to identify each hop in a path
Increments TTL with each iteration
Outputs number of hops, the IP address of the ingress interface of the router or host, and time taken in milliseconds (ms)
tracert
Windows
Uses ICMP
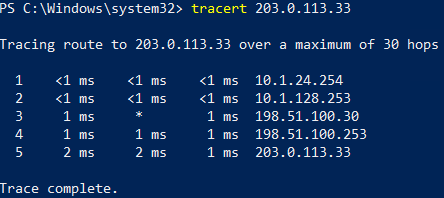
Missing Route Issues
Use ping and traceroute/tracert to identify where network path fails
Check routing table
Missing static route
Dynamic protocol failure
Device configuration review
Routing Loop Issues
Incorrect path information causes packet to circulate until TTL is exhausted
Use traceroute to diagnose
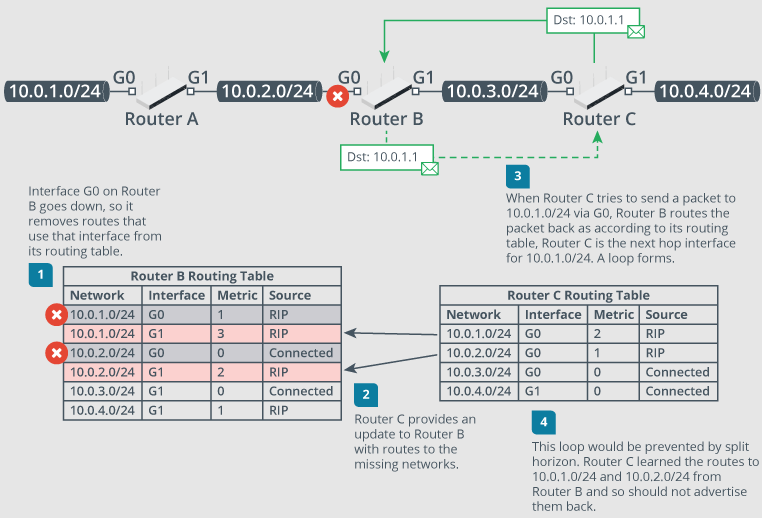
Asymmetrical Routing Issues
Return path different to forward path
Issues
Inconsistent latency
Security appliances dropping return packets
Analyze traceroute output and investigate routing tables
Low Optical Link Budget Issues
Consider PHY/data link layer issues when routing across WANs
Poor connectivity across fiber link
Loss budget expresses amount of loss from attenuation, connectors, and splices measured in dB
Loss budget must be less than power budget (transceiver transmit power and receive sensitivity)
A router must forward traffic received over a single physical interface connected to a switch trunk port to the appropriate virtual LAN (VLAN). What feature must be configured on the router?
A subinterface for each VLAN carried over the trunk. Each subinterface must be configured with an IP address and mask for the subnet mapped to the VLAN.
True or false? Layer 3 capable switches are interchangable with routers.
False. A layer 3 capable switch can perform fast routing and switching between subnets and virtual LANs (VLANs) on a local network. However, a layer 3 switch does not typically support WAN interface cards and so cannot be used as an edge router.
True or false? Any occurrence of an asterisk in traceroute output indicates that there is no connectivity to the destination along that path.
False. Some routers along the path might not respond to probes. If there is no route to the destination, an unreachable notification will be displayed.
Your network monitor is recording high numbers of ICMP Time Exceeded notifications. What type of routing issue does this typically indicate?
This is typical of a routing loop, where packets circulate between two routers until the time to live (TTL) is exceeded.
A campus to datacenter fiber optic link has been laid over 15 km of single-mode fiber with one fusion splice along this run. The termination at each end requires two connectors. You need to evaluate a proposal to use 10GBASE-LR transceiver modules for the router. The module specification quotes Tx power of –8.2 dBm and Rx sensitivity of –14.4 dBm. Assuming attenuation of 0.4 dB/km, 0.75 dB loss per connector, and 0.3 dB loss per splice, do these modules work within the expected loss budget?
The loss budget is (15 0.4 = 6) + (4 0.75 = 3.0) + (1 * 0.3 = 0.3) = 9.3 dB. The power budget is –8.2 - (-14.4 dBm) = 6.2 dB. Consequently, the power budget is insufficient. Note that 10GBASE-LR is rated for 10 km operation over single mode.
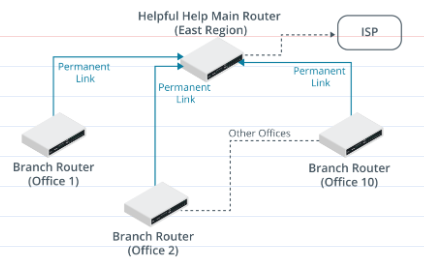
Helpful Help is a charitable organization that operates out of numerous small offices spread all over the country. Each office has a team of 10-20 people who currently use a network of PCs and Apple Macs running various applications. Each office is connected back to a main site, which has a connection to the Internet via an ISP. Staff at each local office uses the link for web access and to access an online email service. Each office has a 192.168.x.0/24 subnet allocated to it. The East region is shown in the graphic.
Given the current scenario of the charity, how would the routers at each local office be configured?
As the link is only used for web browsing and online email, the local office routers would just be configured with a static route/default gateway/gateway of last resort to forward all traffic to the main site, which would forward the web traffic on.
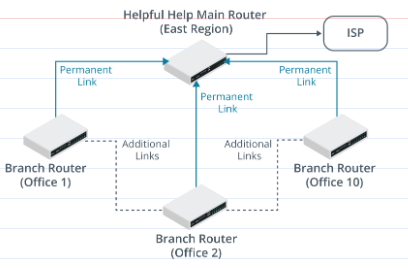
Presently, each local office of Helpful Help has several PSTN (landline) telephones. The plan is to replace these with a unified communications system for VoIP, conferencing, and messaging/information. This will require devices in each local office to be able to contact devices in other offices for direct media streaming. It is also anticipated that additional links may be added between branch offices where larger numbers of users are situated due to the increased bandwidth required by the new applications at this site. Here is the revised diagram:
With this new infrastructure in place, what changes would need to be made to the router’s configuration?
Due to the need for offices and therefore routers to be able contact each other, additional routing table entries will be needed. This could be through more static routes, but a dynamic routing protocol would be better able to cope with any future changes to the topology.
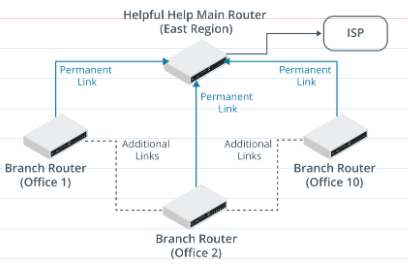
Presently, each local office of Helpful Help has several PSTN (landline) telephones. The plan is to replace these with a unified communications system for VoIP, conferencing, and messaging/information. This will require devices in each local office to be able to contact devices in other offices for direct media streaming. It is also anticipated that additional links may be added between branch offices where larger numbers of users are situated due to the increased bandwidth required by the new applications at this site. Here is the revised diagram:
Which protocol would be best here?
There are several choices. The network is relatively simple with only a few network hops so RIPv2 could be used as it is easier to configure.
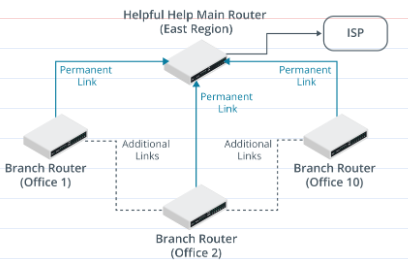
Presently, each local office of Helpful Help has several PSTN (landline) telephones. The plan is to replace these with a unified communications system for VoIP, conferencing, and messaging/information. This will require devices in each local office to be able to contact devices in other offices for direct media streaming. It is also anticipated that additional links may be added between branch offices where larger numbers of users are situated due to the increased bandwidth required by the new applications at this site. Here is the revised diagram:
What might you do to manage the much larger number of IP subnets?
It may be worth considering different OSPF areas to manage the size of the OSPF topology tables and use route summarization to reduce the router’s CPU load.
A network technician is attempting to prevent poorly addressed packets from permanently circulating the network. Which of the following will decrement when it passes through switches?
Neither hop count nor TTL
Hop count
TTL
Flow label
Answer: 1 (Neither hop count nor TTL)
Neither hop count nor TTL will decrement when passing through a switch, only when it passes through routers.
Each router along the path counts as one hop. Note that the switches do not count as hops.
At each router, the Time to Live (TTL) IP header field decreases by at least 1. TTL is a unit of time in seconds, but in practice, it is the maximum hop count.
The flow label is for quality of service (QoS) management, such as for real-time streams. The technician sets the flow label to 0 for packets not part of any delivery sequence or structure.
A network technician is looking at a router configuration. Which of the following is NOT a mechanism for preventing routing loops?
Maximum hop count
Convergence
Holddown timer
Split horizon
Answer: 2 (Convergence)
Convergence is the process where routers running dynamic routing algorithms agree on the network topology.
With maximum hop count, if the cost exceeds a certain value, such as 16 in Routing Internet Protocol (RIP), the network is deemed unreachable. A poison route is one advertised with a hop count of 16.
For a holddown timer, if a node declares a network unreachable, its neighbors start a holddown timer. Any updates about that route received from other nodes get discarded for the duration of the timer.
A split horizon prevents a routing update from being copied back to the source.
A network administrator is setting up an Exterior Gateway Protocol (EGP). Which of the following protocols is part of the EGP class?
RIP
BGP
EIGRP
OSPF
Answer: 2 (BGP)
The Border Gateway Protocol (BGP) is a path vector type that is part of the Exterior Gateway Protocol (EGP) class and runs over Transmission Control Protocol (TCP) port 179.
The Routing Information Protocol (RIP) is a distance-vector type that is not part of the EGP class and runs over User Datagram Protocol (UDP) ports 520 or 521.
The Enhanced Interior Gateway Routing Protocol (EIGRP) is a distance vector/hybrid type that is part of the Interior Gateway Protocol (IGP) class and runs over native IP (88).
The Open Shortest Path First (OSPF) is a link state type that is part of the IGP class and runs over native IP (89).
A network architect is researching distance vector protocols to use. Which of the following should the architect look into? (Select all that apply.)
RIP
OSPF
BGP
EIGRP
Answer: 1 and 4, RIP and EIGRP
The Routing Information Protocol (RIP) is a distance vector type that is part of the IGP class and runs over User Datagram Protocol (UDP) ports 520 or 521.
The Enhanced Interior Gateway Routing Protocol (EIGRP) is a distance vector/hybrid type that is part of the Interior Gateway Protocol (IGP) class and runs over native IP (88).
The Open Shortest Path First (OSPF) is a link state type that is part of the IGP class and runs over native IP (89).
The Border Gateway Protocol (BGP) is a path vector type that is part of the Exterior Gateway Protocol (EGP) class and runs over Transmission Control Protocol (TCP) port 179.
A network architect is looking at the topology and metrics used to build and update a routing information base. Most routing information bases get classified as which of the following? (Select all that apply.)
Convergence
Prefix discovery
Distance vector
Link state
Answer: 3 and 4 (Distance vector and Link state)
Distance vector is one of the most classed algorithms. Some protocols use a hybrid of different methods to perform path selection more efficiently.
Link state is also one of the most classed algorithms. The algorithms for path selection get built according to the topology and metrics that they use to build and update a routing information base.
Convergence is the process whereby routers running dynamic routing algorithms agree on the network topology.
Prefix discovery enables a host to discover the known network prefixes allocated to the local segment. This facilitates next-hop determination.
A Windows server administrator wants to view the routing table of end systems. Which command should the administrator use?
ip route show
route add 192.168.3.0 mask 255.255.255.0 192.168.5.1 metric 2
ip route w.x.y.z
route print
Answer: 4 (route print)
In Windows, to show the routing table, run route print. Apart from loopback addresses and the local subnet, the routing table for an end system generally contains a single entry for the default route.
The iproute2 suite of tools replaces deprecated legacy command-line tools in Linux. The administrator can use ip route show and ip route add to achieve the same ends.
The command route add 192.168.3.0 mask 255.255.255.0 192.168.5.1 metric 2 adds a route instead of displaying the routing table.
When inspecting a routing table, the administrator can use show ip route w.x.y.z to check for the presence of a route to a specific IP network.