1.4 Hashing and Digital Signatures
1/8
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
9 Terms
Hashes
A short string of text that represents a piece of data—like a fingerprint for information.
It’s a one-way trip, meaning you can’t take it and reverse it to get the original information. This is different from encryption.
Just like you can’t recreate a person from their fingerprint, you can’t recreate the data from this.
Are commonly used to store passwords and protect confidentiality.
Helps verify integrity—for example, by checking that a downloaded file matches the original version posted online.
Can also be used as a digital signature, helping provide authentication, non-repudiation, and integrity.
Hash Example
This algorithm creates a 256-bit hash, which is shown as 64 hexadecimal characters (SHA-256).
If we take the sentence: “My name is Professor Messer.”
Its SHA-256 hash becomes:
19da9a2e26f3bff67f0522f962851c42542b8659333ac53397c8d65aa7a3f871Now, we change just one character in the sentence to: “My name is Professor Messer!”
The new hash is:
54381cae1eea10892d81c8688d06d1928b4ee8495061a792864f83092b033aea
Even though there was only a tiny change, it is completely different. This is a key feature —a small change in the input creates a big change in the output.
Collision
A good hash function should create a unique hash for every different input. If two different inputs produce the same hash, that’s called this, and it’s a problem.
One example is MD5, an older hashing algorithm. MD5 should not be used for anything important today.
You might have two text inputs that look almost identical. But when both are run through the MD5 algorithm, they produce the same hash value.
Are extremely rare with strong hashing algorithms
Practical Hashing
One common use of hashing is to verify a downloaded file.
Many websites post a hash value next to the file download link. After downloading the file, you can run the same hashing algorithm on your copy and compare the result to the posted hash.
If the hashes match, it means your download is exactly the same as the original—no tampering or corruption occurred.
Password Storage
Instead of saving your password in plain text or encrypting it (which could later be decrypted), the system stores a hash of your password.
When you log in, your entered password is converted to a hash and compared to the one on file. If they match, you’re allowed access—without ever storing or revealing the actual password.
Salt
Random data added to a password before it’s hashed. This extra data helps make the hash more unique and harder to crack using brute force attacks
Each user gets their own, and it’s usually stored along with the hashed password.
Even if two people use the same password, their hashes will look completely different because of this.
Rainbow tables are pre-made lists of possible passwords and their matching hashes. They work well on unsalted hashes, but adding a random salt to each password breaks this shortcut.
Doesn’t fully prevent brute force attacks, it slows them down significantly and adds a strong layer of protection.
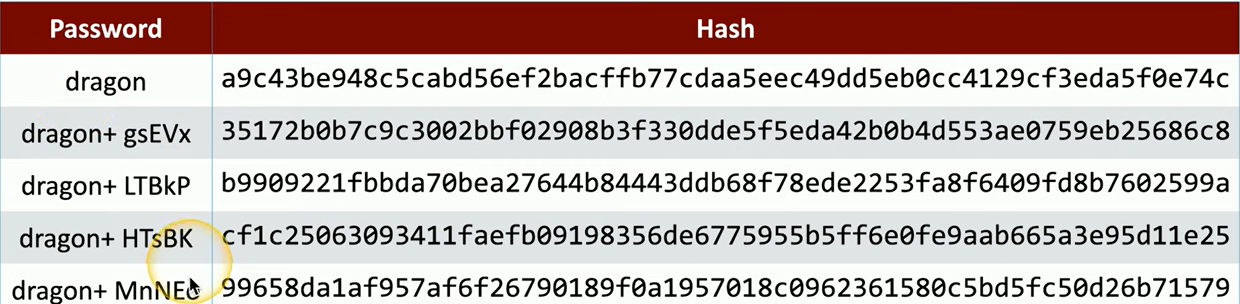
Salt Example:
Each user gets a different random value added to their password before hashing. So even if multiple users have the same password, the resulting hashes will be different.
For example, if the password is “dragon”, and we don’t use a salt, everyone’s hash will look the same. But if we add different random salts to "dragon" for each user, we end up with completely different hashes.
If an attacker gets the hashed password database, it might look like everyone has different passwords, when really, it’s the same password with different salts applied.
Digital Signatures
Help prove that a message wasn't changed (integrity), that it came from the right person (authentication), and that the sender can’t deny sending it (non-repudiation).
The sender uses their private key to sign the message. This is the opposite of encryption, where you'd usually use the receiver’s public key. When someone receives the signed message, they use the sender’s public key to verify it.
If the public key can’t verify the digital signature, it means the message was changed or wasn’t signed by the real sender.
Creating a Digital Signature – Part 1
Alice wants to send Bob a message: “You’re hired, Bob.” This message is called the plaintext. Alice checks a box in her email program to include a digital signature.
Behind the scenes, her email software takes that message and runs it through a hashing algorithm, creating a short fingerprint of the text.
Then, the program encrypts that hash using Alice’s private key. This encrypted hash becomes the digital signature, and only Alice could have made it, because only she has her private key.
The actual message, “You’re hired, Bob,” is still sent as plain text—it’s not encrypted in this case. The digital signature is added to the message, either as an attachment or at the end

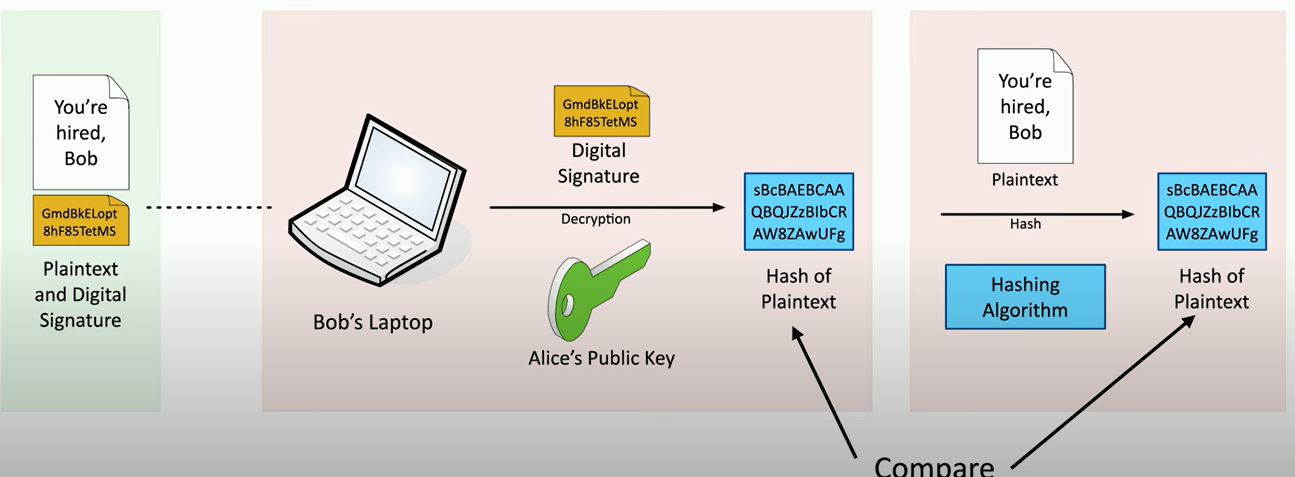
Creating A Digital Signature – Part 2
Now Bob wants to make sure the message he got is exactly what Alice sent—and that it really came from her.
His email program looks at the digital signature and decrypts it using Alice’s public key. Since Alice’s private key was used to create the signature, her public key is the only thing that can decrypt it. The result is the hash of the original message.
Next, Bob’s email program runs the same hashing algorithm on the message itself. If the hash it creates matches the one from the digital signature, then Bob knows two things: The message wasn’t changed (integrity), and It really came from Alice (authentication), since only she could’ve created that signature.