ISTN103 - Exam Questions
1/422
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
423 Terms
Which HTML element contains the actual content of a web page?
[A] <http></http>
[B] <head></head>
[C] <title></title>
[D] <body></body>
[E] <html></html>
D
The “Type” attribute of the <source> element for a video insert on a webpage describes the _________.
[A] media source type
[B] media compression type
[C] MIME type
[D] media extension of the video
[E] images within the video
C
For the <!doctype> declaration in HTML5, which statement is true?
[A] There must be only one <!doctype> declaration
[B] There must be only two <!doctype> declarations
[C] There can be any number of <!doctype> declarations
[D] The <!doctype> declaration is optional
[E] None of the above
A
The default encoding character type used in HTML5 coding is ________.
[A] UTF-16
[B] UTF-32
[C] ASCII
[D] EDCDIC
[E] None of the above
E
Which of the following is the most appropriate tag in HTML5 to divide the document into logical document sections?
[A] <div></div>
[B] <span></span>
[C] <frame></frame>
[D] <section></section>
[E] <group></group>
D
In HTML5, the <header>, <footer>, <article>, <section> elements are referred to as ________ elements because they provide structure and logical composition to a web page.
[A] control
[B] graphic
[C] semantic
[D] multimedia
[E] format
C
Which of the following tags, when used together with the h1-h6 elements, enables the page designer to structure the document display?
[A] section
[B] article
[C] aside
[D] header
[E] title
A
Which of the following is NOT a form control element in HTML5?
[A] url
[B] search
[C] money
[D] email
[E] time
C
Which attribute of the <audio> tag will enable the viewer to adjust the audio volume, playback and pause/resume playback?
[A] autoplay
[B] src
[C] adjust
[D] controls
[E] preload
D
Given the following line of HTML5 code:
<!-- link rel=”stylesheet” type=”text/css” href=”style.css”-->
Which of the following about the code line is true?
[A] The browser applies CSS to the webpage
[B] The type attribute is wrongly specified
[C] The browser will ignore the line of code
[D] An error message will be displayed
[E] None of the above
C
![<p><form></p><p>Username:</p><p><input type="text" name="stunum" value="[1]"></p><p><br></p><p>Password:</p><p><input type="[2]" name="pass" value="passw"></p><p><br> <br></p><p><input type="radio" name="UG" value="Undergrad"</p><p>[3]>Undergraduate<br></p><p><input type="radio" name="PG"</p><p>value="Postgrad">Postgraduate<br></p><p><br></p><p><input type="[4]" name="Save" value="Save">Save my</p><p>credentials<br></p><p><br></p><p><input type="Submit" value="[5]"></p><p><br></p><p></form></p><p></p><p>The missing keyword labelled [1] is ________.</p><p>[A] Enter your student number</p><p>[B] Text</p><p>[C] TextBox</p><p>[D] Checked</p><p>[E] None of the above</p><p></p>](https://knowt-user-attachments.s3.amazonaws.com/441b0816-c099-4d5f-988f-f10047dbe50b.jpeg)
<form>
Username:
<input type="text" name="stunum" value="[1]">
<br>
Password:
<input type="[2]" name="pass" value="passw">
<br> <br>
<input type="radio" name="UG" value="Undergrad"
[3]>Undergraduate<br>
<input type="radio" name="PG"
value="Postgrad">Postgraduate<br>
<br>
<input type="[4]" name="Save" value="Save">Save my
credentials<br>
<br>
<input type="Submit" value="[5]">
<br>
</form>
The missing keyword labelled [1] is ________.
[A] Enter your student number
[B] Text
[C] TextBox
[D] Checked
[E] None of the above
A
![<p><form></p><p>Username:</p><p><input type="text" name="stunum" value="[1]"></p><p><br></p><p>Password:</p><p><input type="[2]" name="pass" value="passw"></p><p><br> <br></p><p><input type="radio" name="UG" value="Undergrad"</p><p>[3]>Undergraduate<br></p><p><input type="radio" name="PG"</p><p>value="Postgrad">Postgraduate<br></p><p><br></p><p><input type="[4]" name="Save" value="Save">Save my</p><p>credentials<br></p><p><br></p><p><input type="Submit" value="[5]"></p><p><br></p><p></form> </p><p></p><p>The missing keyword labelled [2] is ________.</p><p>[A] value</p><p>[B] pass</p><p>[C] password</p><p>[D] text</p><p>[E] passwrd</p>](https://knowt-user-attachments.s3.amazonaws.com/1739abfa-daaa-49ce-aa24-e43b55a71a19.jpeg)
<form>
Username:
<input type="text" name="stunum" value="[1]">
<br>
Password:
<input type="[2]" name="pass" value="passw">
<br> <br>
<input type="radio" name="UG" value="Undergrad"
[3]>Undergraduate<br>
<input type="radio" name="PG"
value="Postgrad">Postgraduate<br>
<br>
<input type="[4]" name="Save" value="Save">Save my
credentials<br>
<br>
<input type="Submit" value="[5]">
<br>
</form>
The missing keyword labelled [2] is ________.
[A] value
[B] pass
[C] password
[D] text
[E] passwrd
C
![<p><form></p><p>Username:</p><p><input type="text" name="stunum" value="[1]"></p><p><br></p><p>Password:</p><p><input type="[2]" name="pass" value="passw"></p><p><br> <br></p><p><input type="radio" name="UG" value="Undergrad"</p><p>[3]>Undergraduate<br></p><p><input type="radio" name="PG"</p><p>value="Postgrad">Postgraduate<br></p><p><br></p><p><input type="[4]" name="Save" value="Save">Save my</p><p>credentials<br></p><p><br></p><p><input type="Submit" value="[5]"></p><p><br></p><p></form> </p><p></p><p>The missing keyword labelled [3] is ________.</p><p>[A] select</p><p>[B] checked</p><p>[C] selected</p><p>[D] radio</p><p>[E] default</p>](https://knowt-user-attachments.s3.amazonaws.com/baadb30e-0103-4116-8896-4c5c183eb0cb.jpeg)
<form>
Username:
<input type="text" name="stunum" value="[1]">
<br>
Password:
<input type="[2]" name="pass" value="passw">
<br> <br>
<input type="radio" name="UG" value="Undergrad"
[3]>Undergraduate<br>
<input type="radio" name="PG"
value="Postgrad">Postgraduate<br>
<br>
<input type="[4]" name="Save" value="Save">Save my
credentials<br>
<br>
<input type="Submit" value="[5]">
<br>
</form>
The missing keyword labelled [3] is ________.
[A] select
[B] checked
[C] selected
[D] radio
[E] default
B
![<p><form></p><p>Username:</p><p><input type="text" name="stunum" value="[1]"></p><p><br></p><p>Password:</p><p><input type="[2]" name="pass" value="passw"></p><p><br> <br></p><p><input type="radio" name="UG" value="Undergrad"</p><p>[3]>Undergraduate<br></p><p><input type="radio" name="PG"</p><p>value="Postgrad">Postgraduate<br></p><p><br></p><p><input type="[4]" name="Save" value="Save">Save my</p><p>credentials<br></p><p><br></p><p><input type="Submit" value="[5]"></p><p><br></p><p></form> </p><p></p><p>The missing keyword labelled [4] is ________.</p><p>[A] box</p><p>[B] check</p><p>[C] square</p><p>[D] checkbox</p><p>[E] deselected</p>](https://knowt-user-attachments.s3.amazonaws.com/aee59cfc-c269-4522-b7b4-4a8888e8c917.jpeg)
<form>
Username:
<input type="text" name="stunum" value="[1]">
<br>
Password:
<input type="[2]" name="pass" value="passw">
<br> <br>
<input type="radio" name="UG" value="Undergrad"
[3]>Undergraduate<br>
<input type="radio" name="PG"
value="Postgrad">Postgraduate<br>
<br>
<input type="[4]" name="Save" value="Save">Save my
credentials<br>
<br>
<input type="Submit" value="[5]">
<br>
</form>
The missing keyword labelled [4] is ________.
[A] box
[B] check
[C] square
[D] checkbox
[E] deselected
D
![<p><form></p><p>Username:</p><p><input type="text" name="stunum" value="[1]"></p><p><br></p><p>Password:</p><p><input type="[2]" name="pass" value="passw"></p><p><br> <br></p><p><input type="radio" name="UG" value="Undergrad"</p><p>[3]>Undergraduate<br></p><p><input type="radio" name="PG"</p><p>value="Postgrad">Postgraduate<br></p><p><br></p><p><input type="[4]" name="Save" value="Save">Save my</p><p>credentials<br></p><p><br></p><p><input type="Submit" value="[5]"></p><p><br></p><p></form> </p><p></p><p>The missing keyword labelled [5] is ________.</p><p>[A] login</p><p>[B] submit</p><p>[C] reset</p><p>[D] button</p><p>[E] loginbutton</p>](https://knowt-user-attachments.s3.amazonaws.com/e4f21040-1281-4ea9-8392-3c359b60d9ed.jpeg)
<form>
Username:
<input type="text" name="stunum" value="[1]">
<br>
Password:
<input type="[2]" name="pass" value="passw">
<br> <br>
<input type="radio" name="UG" value="Undergrad"
[3]>Undergraduate<br>
<input type="radio" name="PG"
value="Postgrad">Postgraduate<br>
<br>
<input type="[4]" name="Save" value="Save">Save my
credentials<br>
<br>
<input type="Submit" value="[5]">
<br>
</form>
The missing keyword labelled [5] is ________.
[A] login
[B] submit
[C] reset
[D] button
[E] loginbutton
A
Which of the following is an advantage of prototyping?
[A] Each iteration builds on the previous one, so the final iteration might be
incrementally better than the initial solution
[B] Formal end-of-phase reviews might not occur
[C] The primary focus is on the development of the prototype, therefore system
documentation is often absent or incomplete
[D] Prototyping enables early detection of errors and omissions
[E] None of the above
D
A consulting firm is considering a new systems development project to keep track of
all the work allocated to sub-contractors. The systems development team estimate
that it will take 18 months to implement the system. However, the consulting firm
need the system to be available in 14 months, as they are undergoing a merger. The
type of feasibility that is being challenged here is ________.
[A] Technical
[B] Economic
[C] Legal
[D] Operational
[E] Schedule
E
What is/are the advantage(s) of using Computer-Aided Software Engineering (CASE)
tools?
i) Produce systems with longer effective operational life
ii) Produce systems that more closely meet user needs
iii) Produce systems with excellent documentation
iv) Can be easy to customise
v) Can be easily used with existing systems
[A] i), ii) and iii)
[B] i), ii) and iv)
[C] ii), iii) and iv)
[D] ii), iv) and v)
[E] iii), iv) and v)
A
During the Design phase of the SDLC, which of the following activities take place?
i) Ensure that the user interface of the new system will be consistent and provide
useful feedback
ii) Work out ways to keep the new system safe from harm
iii) Purchase hardware for the new system
iv) Devise a plan to ensure that the system will continue working in spite of a disaster
striking
[A] i) and ii)
[B] ii) and iii)
[C] iii) and iv)
[D] i), ii) and iv)
[E] ii), iii) and iv)
D
A government department has developed a new system. The developers have done
some testing. However, they still need to test whether the system will work when
many users all use the system at the same time. What sort of testing is needed?
[A] Unit testing
[B] Integration testing
[C] Beta testing
[D] Volume testing
[E] User acceptance testing
D
A system would need to be maintained if ________.
i) the system programmers were short of work
ii) errors were found in the system
iii) users wanted changes to a screen
iv) the database management system were no longer supported
[A] i) and ii)
[B] ii) and iii)
[C] iii) and iv)
[D] i), ii) and iii)
[E] ii), iii) and iv)
E
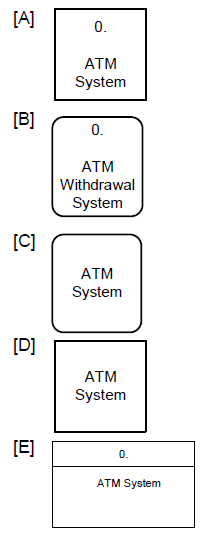
At the bank’s ATM, when account holders want to withdraw money, they enter their PIN;
they also enter the amount they want to withdraw and the account from which they want
to withdraw the money. The system responds with the desired amount of cash and a
receipt, which contains the details of the withdrawal transaction.
Based on this narrative, the best way to draw the system is ________.
B
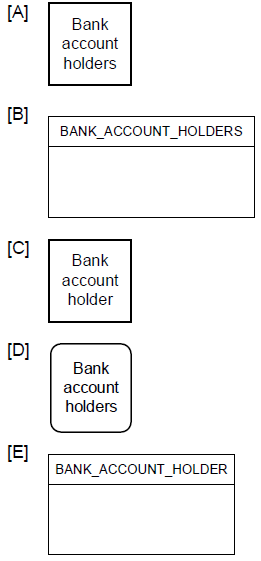
At the bank’s ATM, when account holders want to withdraw money, they enter their PIN;
they also enter the amount they want to withdraw and the account from which they want
to withdraw the money. The system responds with the desired amount of cash and a
receipt, which contains the details of the withdrawal transaction.
Based on this narrative, the best way to draw the external entity is ________.
C
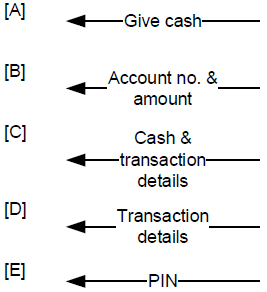
At the bank’s ATM, when account holders want to withdraw money, they enter their PIN;
they also enter the amount they want to withdraw and the account from which they want
to withdraw the money. The system responds with the desired amount of cash and a
receipt, which contains the details of the withdrawal transaction.
Based on this narrative, the best way to draw the OUTPUT of the system is _______.
D
![<p>At the university, when lecturers want the library to stock new books, they give the list of</p><p>new books to the library’s purchasing administrator, who enters the books’ details into</p><p>the purchasing system. The system sends the list to the library manager. The library</p><p>manager checks the budget and then enters the approved list of books to be purchased.</p><p>When the purchased books arrive, the lecturer is sent a message saying that the books</p><p>have arrived, and that they may be borrowed.</p><p>The diagram below, which depicts this narrative, has some errors </p><p></p><p>There are errors in the diagram components numbered ________.</p><p>[A] 1 and 2</p><p>[B] 2 and 3</p><p>[C] 3 and 4</p><p>[D] 1 and 3</p><p>[E] 2 and 4</p>](https://knowt-user-attachments.s3.amazonaws.com/c170aade-5ac7-4f73-b2e0-12b83523e507.jpeg)
At the university, when lecturers want the library to stock new books, they give the list of
new books to the library’s purchasing administrator, who enters the books’ details into
the purchasing system. The system sends the list to the library manager. The library
manager checks the budget and then enters the approved list of books to be purchased.
When the purchased books arrive, the lecturer is sent a message saying that the books
have arrived, and that they may be borrowed.
The diagram below, which depicts this narrative, has some errors
There are errors in the diagram components numbered ________.
[A] 1 and 2
[B] 2 and 3
[C] 3 and 4
[D] 1 and 3
[E] 2 and 4
B
![<p>At the university, when lecturers want the library to stock new books, they give the list of</p><p>new books to the library’s purchasing administrator, who enters the books’ details into</p><p>the purchasing system. The system sends the list to the library manager. The library</p><p>manager checks the budget and then enters the approved list of books to be purchased.</p><p>When the purchased books arrive, the lecturer is sent a message saying that the books</p><p>have arrived, and that they may be borrowed.</p><p>The diagram below, which depicts this narrative, has some errors </p><p></p><p>There are errors in the diagram components numbered ________.</p><p>[A] 5 and 6</p><p>[B] 6 and 7</p><p>[C] 7 and 8</p><p>[D] 5 and 8</p><p>[E] 6 and 8</p>](https://knowt-user-attachments.s3.amazonaws.com/677a78a0-f937-4173-8d5e-af06594f839f.jpeg)
At the university, when lecturers want the library to stock new books, they give the list of
new books to the library’s purchasing administrator, who enters the books’ details into
the purchasing system. The system sends the list to the library manager. The library
manager checks the budget and then enters the approved list of books to be purchased.
When the purchased books arrive, the lecturer is sent a message saying that the books
have arrived, and that they may be borrowed.
The diagram below, which depicts this narrative, has some errors
There are errors in the diagram components numbered ________.
[A] 5 and 6
[B] 6 and 7
[C] 7 and 8
[D] 5 and 8
[E] 6 and 8
D
![<p>At the university, when lecturers want the library to stock new books, they give the list of</p><p>new books to the library’s purchasing administrator, who enters the books’ details into</p><p>the purchasing system. The system sends the list to the library manager. The library</p><p>manager checks the budget and then enters the approved list of books to be purchased.</p><p>When the purchased books arrive, the lecturer is sent a message saying that the books</p><p>have arrived, and that they may be borrowed.</p><p>The diagram below, which depicts this narrative, has some errors </p><p></p><p>The error with component 9 is that ________.</p><p>[A] it is labelled as a verb/action/command</p><p>[B] it is a physical flow</p><p>[C] it should be singular</p><p>[D] it should flow to the purchasing librarian</p><p>[E] There is nothing wrong with this component</p>](https://knowt-user-attachments.s3.amazonaws.com/5e686ea1-5eb1-4d5f-a758-ccc946f5edf6.jpeg)
At the university, when lecturers want the library to stock new books, they give the list of
new books to the library’s purchasing administrator, who enters the books’ details into
the purchasing system. The system sends the list to the library manager. The library
manager checks the budget and then enters the approved list of books to be purchased.
When the purchased books arrive, the lecturer is sent a message saying that the books
have arrived, and that they may be borrowed.
The diagram below, which depicts this narrative, has some errors
The error with component 9 is that ________.
[A] it is labelled as a verb/action/command
[B] it is a physical flow
[C] it should be singular
[D] it should flow to the purchasing librarian
[E] There is nothing wrong with this component
B
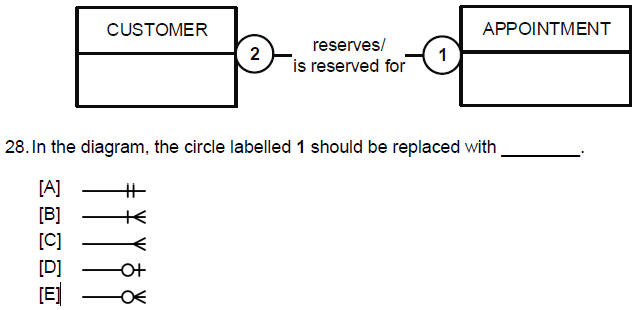
Kathy’s Beauty Salon provides a number of services, like haircuts, manicures and pedicures. When customers enquire about Kathy’s services, they provide their details, which are stored. They do not have to make an appointment at the same time as making their enquiry. Over time, customers could make many appointments. Customers do not share appointments.
E
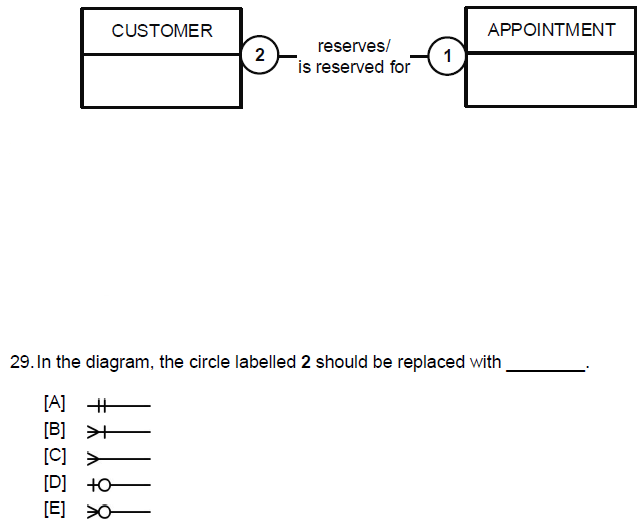
Kathy’s Beauty Salon provides a number of services, like haircuts, manicures and
pedicures. When customers enquire about Kathy’s services, they provide their details,
which are stored. They do not have to make an appointment at the same time as making
their enquiry. Over time, customers could make many appointments. Customers do not
share appointments.
A
![<p>According to this diagram, it is optional for ________.</p><p>i) a doctor to treat a patient</p><p>ii) a patient to be prescribed a medicine</p><p>iii) a patient to be assigned a ward</p><p>iv) a ward to be assigned to a patient</p><p>v) a patient to be treated by a doctor</p><p>[A] i) and iii)</p><p>[B] i) and iv)</p><p>[C] ii) and iii)</p><p>[D] ii) and v)</p><p>[E] iv) and v)</p>](https://knowt-user-attachments.s3.amazonaws.com/6f6da8f3-874d-48a8-856d-265304b7ce10.jpeg)
According to this diagram, it is optional for ________.
i) a doctor to treat a patient
ii) a patient to be prescribed a medicine
iii) a patient to be assigned a ward
iv) a ward to be assigned to a patient
v) a patient to be treated by a doctor
[A] i) and iii)
[B] i) and iv)
[C] ii) and iii)
[D] ii) and v)
[E] iv) and v)
B
![<p>According to this diagram, ________.</p><p>i) a doctor must treat at least one patient</p><p>ii) a ward does not need to be assigned to a patient</p><p>iii) a medicine can be prescribed to more than one patient</p><p>iv) a patient is treated by only one doctor</p><p>v) a patient does not need to be prescribed any medication</p><p>[A] i) and iii)</p><p>[B] i) and v)</p><p>[C] ii) and iii)</p><p>[D] ii) and iv)</p><p>[E] iv) and v)</p>](https://knowt-user-attachments.s3.amazonaws.com/7bf965c6-dced-4bea-ac80-22d6c38b7841.jpeg)
According to this diagram, ________.
i) a doctor must treat at least one patient
ii) a ward does not need to be assigned to a patient
iii) a medicine can be prescribed to more than one patient
iv) a patient is treated by only one doctor
v) a patient does not need to be prescribed any medication
[A] i) and iii)
[B] i) and v)
[C] ii) and iii)
[D] ii) and iv)
[E] iv) and v)
D
![<p>Based on the diagram, labels 1 and 2 refer to ________ and ________, respectively.</p><p>[A] 1) Attribute 2) Instance</p><p>[B] 1) Entity 2) Instance</p><p>[C] 1) Cardinality 2) Relationship</p><p>[D] 1) Relationship 2) Cardinality</p><p>[E] 1) Relationship 2) Entity</p>](https://knowt-user-attachments.s3.amazonaws.com/3a358fe0-cc5e-470b-a1bb-a0545f40bdd7.jpeg)
Based on the diagram, labels 1 and 2 refer to ________ and ________, respectively.
[A] 1) Attribute 2) Instance
[B] 1) Entity 2) Instance
[C] 1) Cardinality 2) Relationship
[D] 1) Relationship 2) Cardinality
[E] 1) Relationship 2) Entity
E
![<p>Which of the following is NOT a possible attribute of the ‘rectangle’ DOCTOR?</p><p>[A] Firstname</p><p>[B] DoctorID</p><p>[C] Address</p><p>[D] PhoneNo</p><p>[E] MedicineID</p>](https://knowt-user-attachments.s3.amazonaws.com/16434ee3-4117-426c-9492-8c2c877119b2.jpeg)
Which of the following is NOT a possible attribute of the ‘rectangle’ DOCTOR?
[A] Firstname
[B] DoctorID
[C] Address
[D] PhoneNo
[E] MedicineID
E
![<p>The output of the flowchart is ________.</p><p>[A] 3</p><p>[B] 5</p><p>[C] 7</p><p>[D] 9</p><p>[E] 11</p>](https://knowt-user-attachments.s3.amazonaws.com/8cf83779-256c-451b-bb32-692219e30dfb.jpeg)
The output of the flowchart is ________.
[A] 3
[B] 5
[C] 7
[D] 9
[E] 11
D
![<p>The flowchart has ________ variables.</p><p>[A] 1</p><p>[B] 2</p><p>[C] 3</p><p>[D] 4</p><p>[E] 5</p>](https://knowt-user-attachments.s3.amazonaws.com/00e44707-daff-47e8-b2af-629a74251912.jpeg)
The flowchart has ________ variables.
[A] 1
[B] 2
[C] 3
[D] 4
[E] 5
B
![<p>How many times will X = X + 1 execute if the Input Total value changes from 0 to 2?</p><p>[A] 2</p><p>[B] 3</p><p>[C] 4</p><p>[D] 5</p><p>[E] 6</p>](https://knowt-user-attachments.s3.amazonaws.com/229f3348-4fac-4aa9-8dac-41f791265597.jpeg)
How many times will X = X + 1 execute if the Input Total value changes from 0 to 2?
[A] 2
[B] 3
[C] 4
[D] 5
[E] 6
B
![<p>What will be the output of the flowchart be when the Input Total value changes from</p><p>0 to 2?</p><p>[A] 10</p><p>[B] 11</p><p>[C] 12</p><p>[D] 13</p><p>[E] 14</p>](https://knowt-user-attachments.s3.amazonaws.com/0ac5c98a-5b0c-4c8f-b6e8-7c08170ee791.jpeg)
What will be the output of the flowchart be when the Input Total value changes from
0 to 2?
[A] 10
[B] 11
[C] 12
[D] 13
[E] 14
B
![<p>How many decision structures are there?</p><p>[A] 0</p><p>[B] 1</p><p>[C] 2</p><p>[D] 3</p><p>[E] 4</p>](https://knowt-user-attachments.s3.amazonaws.com/25da8763-9a08-4b28-9675-51431bab7969.jpeg)
How many decision structures are there?
[A] 0
[B] 1
[C] 2
[D] 3
[E] 4
B
![<p>How many constant values are there?</p><p>[A] 1</p><p>[B] 2</p><p>[C] 3</p><p>[D] 4</p><p>[E] None</p>](https://knowt-user-attachments.s3.amazonaws.com/6e9099d0-0b8e-45e8-9ebf-a6916b20835b.jpeg)
How many constant values are there?
[A] 1
[B] 2
[C] 3
[D] 4
[E] None
E
![<p>What will be the outcome of the flowchat when X is assigned an initial value of 4?</p><p>[A] The loop in the flow chart ends after 2 repetitions</p><p>[B] The loop in the flow chart ends after 1 repetition</p><p>[C] The loop in the flow chart never ends</p><p>[D] The loop in the flow chart ends immediately</p><p>[E] The loop in the flow chart ends after 3 repetitions</p>](https://knowt-user-attachments.s3.amazonaws.com/9972e21d-92d3-44e1-99b1-4b103e8daae6.jpeg)
What will be the outcome of the flowchat when X is assigned an initial value of 4?
[A] The loop in the flow chart ends after 2 repetitions
[B] The loop in the flow chart ends after 1 repetition
[C] The loop in the flow chart never ends
[D] The loop in the flow chart ends immediately
[E] The loop in the flow chart ends after 3 repetitions
C
The correct sequence of the programming process is ________.
i) Define the problem
ii) Outline into an algorithm or flowchart
iii) Test the algorithm or flowchart
iv) Code the algorithm/flowchart and run the program
v) Document and maintain the program
vi) Outline the solution
[A] i), ii), iv), v), iii) and vi)
[B] i), vi), ii), iii), iv and v)
[C] ii), iv), vi), iii), v) and i)
[D] iv), i), vi), v), iii) and ii)
[E] iii), i), v), iv), ii) and vi)
B
![<p>DEPARTMENT_NAME and REG_YEAR refer to ________.</p><p>[A] Variables</p><p>[B] Values</p><p>[C] Identifiers</p><p>[D] Declarations</p><p>[E] Constants</p>](https://knowt-user-attachments.s3.amazonaws.com/57ec333d-8559-453e-bca9-345c7b25a01d.jpeg)
DEPARTMENT_NAME and REG_YEAR refer to ________.
[A] Variables
[B] Values
[C] Identifiers
[D] Declarations
[E] Constants
E
![<p>The data type best to represent X is ________.</p><p>[A] Integer</p><p>[B] String</p><p>[C] boolean</p><p>[D] Decimal</p><p>[E] Char</p>](https://knowt-user-attachments.s3.amazonaws.com/f6b8b270-4baa-42e0-8129-4a2a215c5c9d.jpeg)
The data type best to represent X is ________.
[A] Integer
[B] String
[C] boolean
[D] Decimal
[E] Char
B
![<p>The data type best suited to represent Y is ________.</p><p>[A] Integer</p><p>[B] String</p><p>[C] Boolean</p><p>[D] Decimal</p><p>[E] Char</p>](https://knowt-user-attachments.s3.amazonaws.com/535d7de6-c694-4089-9ffe-95bf246a0d02.jpeg)
The data type best suited to represent Y is ________.
[A] Integer
[B] String
[C] Boolean
[D] Decimal
[E] Char
D
![<p>Which method is adopted to facilitate calculations on text input by a user?</p><p>[A] Convert</p><p>[B] Calc</p><p>[C] Calculate</p><p>[D] Parse</p><p>[E] None of the above</p>](https://knowt-user-attachments.s3.amazonaws.com/36801f93-b8e5-4285-897c-7d6a8b7ee5fc.jpeg)
Which method is adopted to facilitate calculations on text input by a user?
[A] Convert
[B] Calc
[C] Calculate
[D] Parse
[E] None of the above
D
![<p>Runners Shoe Warehouse uses the following screen to calculate sales details. A</p><p>customer is offered the following discount structure, depending on the total value of the</p><p>sale:</p><p>Gross Sale < 1500: 15% discount</p><p>Gross Sale 1500 to 3000: 20% discount</p><p>Gross Sale > 3000: 25% discount</p><p></p><p>Assume the following variables are being used in the program:</p><p>Quantity</p><p>Price</p><p>GrossSale</p><p>Discount</p><p>NetSale </p><p></p><p>Which of the variable(s) should be declared as Integer?</p><p>[A] Quantity</p><p>[B] Price</p><p>[C] Discount</p><p>[D] [A] and [B]</p><p>[E] [B] and [C]</p>](https://knowt-user-attachments.s3.amazonaws.com/06d4ba51-e5bd-4846-99dc-325039c73618.jpeg)
Runners Shoe Warehouse uses the following screen to calculate sales details. A
customer is offered the following discount structure, depending on the total value of the
sale:
Gross Sale < 1500: 15% discount
Gross Sale 1500 to 3000: 20% discount
Gross Sale > 3000: 25% discount
Assume the following variables are being used in the program:
Quantity
Price
GrossSale
Discount
NetSale
Which of the variable(s) should be declared as Integer?
[A] Quantity
[B] Price
[C] Discount
[D] [A] and [B]
[E] [B] and [C]
A
![<p>Runners Shoe Warehouse uses the following screen to calculate sales details. A</p><p>customer is offered the following discount structure, depending on the total value of the</p><p>sale:</p><p>Gross Sale < 1500: 15% discount</p><p>Gross Sale 1500 to 3000: 20% discount</p><p>Gross Sale > 3000: 25% discount</p><p></p><p>Assume the following variables are being used in the program:</p><p>Quantity</p><p>Price</p><p>GrossSale</p><p>Discount</p><p>NetSale </p><p></p><p>Which of the variable(s) should be declared as Decimal?</p><p>[A] Quantity</p><p>[B] Price</p><p>[C] Discount</p><p>[D] [A] and [B]</p><p>[E] [B] and [C]</p>](https://knowt-user-attachments.s3.amazonaws.com/27284e68-9764-496f-a2c7-44376009d4cf.jpeg)
Runners Shoe Warehouse uses the following screen to calculate sales details. A
customer is offered the following discount structure, depending on the total value of the
sale:
Gross Sale < 1500: 15% discount
Gross Sale 1500 to 3000: 20% discount
Gross Sale > 3000: 25% discount
Assume the following variables are being used in the program:
Quantity
Price
GrossSale
Discount
NetSale
Which of the variable(s) should be declared as Decimal?
[A] Quantity
[B] Price
[C] Discount
[D] [A] and [B]
[E] [B] and [C]
B
![<p>Runners Shoe Warehouse uses the following screen to calculate sales details. A</p><p>customer is offered the following discount structure, depending on the total value of the</p><p>sale:</p><p>Gross Sale < 1500: 15% discount</p><p>Gross Sale 1500 to 3000: 20% discount</p><p>Gross Sale > 3000: 25% discount</p><p></p><p>Assume the following variables are being used in the program:</p><p>Quantity</p><p>Price</p><p>GrossSale</p><p>Discount</p><p>NetSale</p><p></p><p>What should be the scope of these variables? </p><p>[A] Module-level</p><p>[B] Local</p><p>[C] Global</p><p>[D] Procedural</p><p>[E] Functional</p>](https://knowt-user-attachments.s3.amazonaws.com/0a730f5d-320f-4e49-9c7e-77811799218b.jpeg)
Runners Shoe Warehouse uses the following screen to calculate sales details. A
customer is offered the following discount structure, depending on the total value of the
sale:
Gross Sale < 1500: 15% discount
Gross Sale 1500 to 3000: 20% discount
Gross Sale > 3000: 25% discount
Assume the following variables are being used in the program:
Quantity
Price
GrossSale
Discount
NetSale
What should be the scope of these variables?
[A] Module-level
[B] Local
[C] Global
[D] Procedural
[E] Functional
B
![<p>Runners Shoe Warehouse uses the following screen to calculate sales details. A</p><p>customer is offered the following discount structure, depending on the total value of the</p><p>sale:</p><p>Gross Sale < 1500: 15% discount</p><p>Gross Sale 1500 to 3000: 20% discount</p><p>Gross Sale > 3000: 25% discount</p><p></p><p>Assume the following variables are being used in the program:</p><p>Quantity</p><p>Price</p><p>GrossSale</p><p>Discount</p><p>NetSale</p><p></p><p>To facilitate the calculation of the Gross Sale value in TextBox4, what code is required</p><p>to convert the ‘text’ input value to a ‘numeric’ value?</p><p>[A] Quantity = Integer.Convert(TextBox3.Text)</p><p>Price = Decimal.Conver(TextBox2.Text)</p><p>[B] Quantity = Integer.Parse(TextBox3.Text)</p><p>Price = Decimal.Parse(TextBox2.Text)</p><p>[C] Quantity = Integer.Parse(TextBox2.Value)</p><p>Price = Decimal.Parse(TextBox3.Value)</p><p>[D] Quantity = Integer.Parse(TextBox2.Text)</p><p>Price = Decimal.Parse(TextBox3.Text)</p><p>[E] None of the above</p>](https://knowt-user-attachments.s3.amazonaws.com/f9bf3394-eb25-4d0c-bf1e-2e0b7f79a57c.jpeg)
Runners Shoe Warehouse uses the following screen to calculate sales details. A
customer is offered the following discount structure, depending on the total value of the
sale:
Gross Sale < 1500: 15% discount
Gross Sale 1500 to 3000: 20% discount
Gross Sale > 3000: 25% discount
Assume the following variables are being used in the program:
Quantity
Price
GrossSale
Discount
NetSale
To facilitate the calculation of the Gross Sale value in TextBox4, what code is required
to convert the ‘text’ input value to a ‘numeric’ value?
[A] Quantity = Integer.Convert(TextBox3.Text)
Price = Decimal.Conver(TextBox2.Text)
[B] Quantity = Integer.Parse(TextBox3.Text)
Price = Decimal.Parse(TextBox2.Text)
[C] Quantity = Integer.Parse(TextBox2.Value)
Price = Decimal.Parse(TextBox3.Value)
[D] Quantity = Integer.Parse(TextBox2.Text)
Price = Decimal.Parse(TextBox3.Text)
[E] None of the above
D
![<p>Runners Shoe Warehouse uses the following screen to calculate sales details. A</p><p>customer is offered the following discount structure, depending on the total value of the</p><p>sale:</p><p>Gross Sale < 1500: 15% discount</p><p>Gross Sale 1500 to 3000: 20% discount</p><p>Gross Sale > 3000: 25% discount</p><p></p><p>Assume the following variables are being used in the program:</p><p>Quantity</p><p>Price</p><p>GrossSale</p><p>Discount</p><p>NetSale</p><p></p><p>To display the value of the Discount calculated in TextBox5, which of the following</p><p>code is required?</p><p>[A] <a target="_blank" rel="noopener noreferrer nofollow" href="http://TextBox5.Name">TextBox5.Name</a> = Discount.ToString("N")</p><p>[B] TextBox5.Text = Discount.ToString("C")</p><p>[C] TextBox5.Text = Discount.ToString("N")</p><p>[D] TextBox5.Value = Discount.ToString("N")</p><p>[E] None of the above</p>](https://knowt-user-attachments.s3.amazonaws.com/d9941789-43a1-49c5-a535-25f295dcefed.jpeg)
Runners Shoe Warehouse uses the following screen to calculate sales details. A
customer is offered the following discount structure, depending on the total value of the
sale:
Gross Sale < 1500: 15% discount
Gross Sale 1500 to 3000: 20% discount
Gross Sale > 3000: 25% discount
Assume the following variables are being used in the program:
Quantity
Price
GrossSale
Discount
NetSale
To display the value of the Discount calculated in TextBox5, which of the following
code is required?
[A] TextBox5.Name = Discount.ToString("N")
[B] TextBox5.Text = Discount.ToString("C")
[C] TextBox5.Text = Discount.ToString("N")
[D] TextBox5.Value = Discount.ToString("N")
[E] None of the above
C
![<p>Runners Shoe Warehouse uses the following screen to calculate sales details. A</p><p>customer is offered the following discount structure, depending on the total value of the</p><p>sale:</p><p>Gross Sale < 1500: 15% discount</p><p>Gross Sale 1500 to 3000: 20% discount</p><p>Gross Sale > 3000: 25% discount</p><p></p><p>Assume the following variables are being used in the program:</p><p>Quantity</p><p>Price</p><p>GrossSale</p><p>Discount</p><p>NetSale</p><p></p><p>Which code is required to display an error message named “Data Entry Error” with the message “Quantity must be numeric“, if invalid data is input into TextBox2? </p><p>[A] <a target="_blank" rel="noopener noreferrer nofollow" href="http://MessageBox.Show">MessageBox.Show</a>("Quantity must be numeric", "Data Entry</p><p>Error", MessageBoxButtons.OK, MessageBoxIcon.Exclamation)</p><p>[B] With TextBox2</p><p>End With</p><p>[C] <a target="_blank" rel="noopener noreferrer nofollow" href="http://MessageBox.Show">MessageBox.Show</a>("Data Entry Error ", " Quantity must be</p><p>numeric ", MessageBoxButtons.OK, MessageBoxIcon.Exclamation)</p><p>[D] [A] and [B]</p><p>[E] [B] and [C]</p>](https://knowt-user-attachments.s3.amazonaws.com/b5e82b04-61a7-47cd-9567-9e697aa09041.jpeg)
Runners Shoe Warehouse uses the following screen to calculate sales details. A
customer is offered the following discount structure, depending on the total value of the
sale:
Gross Sale < 1500: 15% discount
Gross Sale 1500 to 3000: 20% discount
Gross Sale > 3000: 25% discount
Assume the following variables are being used in the program:
Quantity
Price
GrossSale
Discount
NetSale
Which code is required to display an error message named “Data Entry Error” with the message “Quantity must be numeric“, if invalid data is input into TextBox2?
[A] MessageBox.Show("Quantity must be numeric", "Data Entry
Error", MessageBoxButtons.OK, MessageBoxIcon.Exclamation)
[B] With TextBox2
End With
[C] MessageBox.Show("Data Entry Error ", " Quantity must be
numeric ", MessageBoxButtons.OK, MessageBoxIcon.Exclamation)
[D] [A] and [B]
[E] [B] and [C]
D
![<p>The employee hourly rates of pay are stored in one table, and a list of hours worked</p><p>during the previous week, are stored in a second table. The hourly rate is calculated</p><p>using a lookup function, and the Payment Due is a product of the number of hours that</p><p>each employee works and the rate per hour. </p><p></p><p>Which lookup and reference function was used to find the Hourly Rate in cell C12,</p><p>and then autofilled down to cell C17?</p><p>[A] =HLOOKUP(A12,A3:B8,2,TRUE)</p><p>[B] =HLOOKUP(A12,$A$3:$B$8,2,FALSE)</p><p>[C] =VLOOKUP(A12,2,$A$3:$B$8,FALSE)</p><p>[D] =VLOOKUP(A12,$A$3:$B$8,2,FALSE)</p><p>[E] =VLOOKUP(A12,$A$3:$B$8,2,TRUE)</p>](https://knowt-user-attachments.s3.amazonaws.com/fb855b6b-2a32-4eb1-989a-7051d5bcd717.jpeg)
The employee hourly rates of pay are stored in one table, and a list of hours worked
during the previous week, are stored in a second table. The hourly rate is calculated
using a lookup function, and the Payment Due is a product of the number of hours that
each employee works and the rate per hour.
Which lookup and reference function was used to find the Hourly Rate in cell C12,
and then autofilled down to cell C17?
[A] =HLOOKUP(A12,A3:B8,2,TRUE)
[B] =HLOOKUP(A12,$A$3:$B$8,2,FALSE)
[C] =VLOOKUP(A12,2,$A$3:$B$8,FALSE)
[D] =VLOOKUP(A12,$A$3:$B$8,2,FALSE)
[E] =VLOOKUP(A12,$A$3:$B$8,2,TRUE)
D
![<p>The employee hourly rates of pay are stored in one table, and a list of hours worked</p><p>during the previous week, are stored in a second table. The hourly rate is calculated</p><p>using a lookup function, and the Payment Due is a product of the number of hours that</p><p>each employee works and the rate per hour. </p><p></p><p>Which formula was used to calculate the Payment Due in cell D12, and then autofilled</p><p>down to cell D17?</p><p>[A] =B3*B12</p><p>[B] =B12*C12</p><p>[C] =$B$12*$C$12</p><p>[D] =IF(A3=A12, B12*C12,0)</p><p>[E] =HLOOKUP(A12,A3:B8,2,TRUE)</p>](https://knowt-user-attachments.s3.amazonaws.com/f99d5d75-d77d-45f3-a8c8-d44d810bbfb8.jpeg)
The employee hourly rates of pay are stored in one table, and a list of hours worked
during the previous week, are stored in a second table. The hourly rate is calculated
using a lookup function, and the Payment Due is a product of the number of hours that
each employee works and the rate per hour.
Which formula was used to calculate the Payment Due in cell D12, and then autofilled
down to cell D17?
[A] =B3*B12
[B] =B12*C12
[C] =$B$12*$C$12
[D] =IF(A3=A12, B12*C12,0)
[E] =HLOOKUP(A12,A3:B8,2,TRUE)
B
![<p>The employee hourly rates of pay are stored in one table, and a list of hours worked</p><p>during the previous week, are stored in a second table. The hourly rate is calculated</p><p>using a lookup function, and the Payment Due is a product of the number of hours that</p><p>each employee works and the rate per hour. </p><p></p><p>Which error will be displayed in cell C12 if the first column in the lookup table was not</p><p>sorted in ascending order and an exact match of the lookup value could not be found?</p><p>[A] #/N/A</p><p>[B] #REF!</p><p>[C] #NAME</p><p>[D] #NUM!</p><p>[E] #VALUE</p>](https://knowt-user-attachments.s3.amazonaws.com/14b5cc63-b560-49b6-aa1b-2ebb3cad198f.jpeg)
The employee hourly rates of pay are stored in one table, and a list of hours worked
during the previous week, are stored in a second table. The hourly rate is calculated
using a lookup function, and the Payment Due is a product of the number of hours that
each employee works and the rate per hour.
Which error will be displayed in cell C12 if the first column in the lookup table was not
sorted in ascending order and an exact match of the lookup value could not be found?
[A] #/N/A
[B] #REF!
[C] #NAME
[D] #NUM!
[E] #VALUE
A
![<p>Which of the following fields were used to produce the pivot table below?</p><p>Report Filter - Column Labels - Row Labels - Values</p><p>[A] Platform - Sales - Month - Count of Software</p><p>[B] Month - Platform - Software - Sum of Software</p><p>[C] Software - Month - Platform - Sum of Sales</p><p>[D] Platform - Month - Software - Sum of Sales</p><p>[E] Software - Platform - Month - Count of Sales</p>](https://knowt-user-attachments.s3.amazonaws.com/3fab25df-9a84-42c2-be70-6e41a0709dad.jpeg)
Which of the following fields were used to produce the pivot table below?
Report Filter - Column Labels - Row Labels - Values
[A] Platform - Sales - Month - Count of Software
[B] Month - Platform - Software - Sum of Software
[C] Software - Month - Platform - Sum of Sales
[D] Platform - Month - Software - Sum of Sales
[E] Software - Platform - Month - Count of Sales
D
![<p>In the following screenshot, after cell D12 was selected, which feature was used to</p><p>display the arrow from cell D12 to E12?</p><p>[A] Data Validation</p><p>[B] Trace Dependents</p><p>[C] Trace Precedents</p><p>[D] Evaluate Formula</p><p>[E] Error Checking</p>](https://knowt-user-attachments.s3.amazonaws.com/2a1ecbdd-f541-4759-9ccc-a12528d23566.jpeg)
In the following screenshot, after cell D12 was selected, which feature was used to
display the arrow from cell D12 to E12?
[A] Data Validation
[B] Trace Dependents
[C] Trace Precedents
[D] Evaluate Formula
[E] Error Checking
B
Nicki wants to print handouts for her audience, which will contain blank lines to the
right of each slide, for them to take down notes. When printing her slides, how many
slides per page should she choose in order to achieve this?
[A] 2
[B] 3
[C] 4
[D] 6
[E] 9
B
In a PowerPoint presentation it is possible to combine multiple shapes to make a
more complex shape. To constrain the dimensions of the selected shapes that make
up the complex shape, the required procedure is to hold down the ________.
[A] SHIFT key on the keyboard while pressing the down arrow key
[B] SHIFT key on the keyboard while dragging the mouse
[C] CTRL key on the keyboard while dragging the mouse
[D] CTRL key on the keyboard while pressing the ENTER key
[E] CTRL and ALT keys on the keyboard while dragging the mouse
B
![<p>How will the slides advance in a PowerPoint presentation if both options, as shown</p><p>in the image below, are selected?</p><p>[A] Only when the presenter presses the arrow keys</p><p>[B] Only when the presenter presses the Enter key</p><p>[C] Only when the presenter clicks the left mouse button</p><p>[D] Automatically with manual override</p><p>[E] Automatically after the specified time interval without manual override</p>](https://knowt-user-attachments.s3.amazonaws.com/39d257c0-968b-4468-8182-70260d20619d.jpeg)
How will the slides advance in a PowerPoint presentation if both options, as shown
in the image below, are selected?
[A] Only when the presenter presses the arrow keys
[B] Only when the presenter presses the Enter key
[C] Only when the presenter clicks the left mouse button
[D] Automatically with manual override
[E] Automatically after the specified time interval without manual override
D
John wants to paste an Excel spreadsheet onto a slide and enable the chart to be
automatically updated every time the data is updated in Excel. Which method should
he use in order to accomplish this?
[A] Paste
[B] Paste | Paste Link
[C] Paste Special | Paste Link
[D] Paste Special | Paste
[E] All of the above
C
Organisations need to have controls whose aim is to achieve organisational
objectives. Furthermore, existing controls within organisations need to be appraised
according to standardized frameworks. Who are best at providing advice towards
achieving effective results of an organisation through appraising and providing a basis
to improve existing organisational controls?
[A] Technical experts
[B] Operational experts of the various activities
[C] Information system auditors
[D] [A] and [B]
[E] All of the above
C
In the context of available pacesetters for information governance within the
technology control community, your uncle who is a manager of a company is aware
that effective management of information and related Information Technology has
become critical to the survival and long-term success of the company.
From which of the following has the above status resulted?
[A] Cost of use of Information Technology
[B] Cost of use of Information Systems
[C] Increasing dependence on information and systems that deliver information
[D] [A] and [B]
[E] [A] and [C]
E
Increasing a user’s confidence about information, or an event that a user intends to
rely on is ________.
[A] giving assurance to information users
[B] promoting credibility of information
[C] improving accessibility of information to users
[D] [A] and [B]
[E] [B] and [C]
D
Which among the following are served by implementing the auditing procedures?
i) Evaluating products and services
ii) Being a force of improvement to offered products or services
iii) Determining the degree of correspondence between statements about
services and established criteria
iv) Making practical recommendations for promoting a better quality of products
or services
v) Communicating the results of an evaluation to interested users of products or
services
[A] i) and iv)
[B] iv) and v)
[C] iii) and v)
[D] ii) and iv)
[E] All of the above
E
In the context of information systems and financial auditing, a risk is composed of
three factors. Choose the three factors from the list below.
i) threat
ii) impact
iii) control
iv) measure
v) consistency
vi) vulnerability
[A] i), ii), v)
[B] ii), iii), iv)
[C] ii), iv), v)
[D] i), ii), vi)
[E] iii), iv), v)
D
Mr Harvey is an auditor who is performing a review of a company. However, Mr
Harvey is unable to establish confidence in the reliability of the client’s electronic
evidence. Therefore, the use of electronic data as audit evidence should be
________.
[A] eliminated as inappropriate
[B] qualified to become adequate
[C] referred to management for approval
[D] referred to the chief auditor for validation
[E] None of the above
B
The documentation of user activity from a system that displays the chronological
sequence of activities, which is used as a security record to provide documentary
evidence, is called the ________.
[A] audit log
[B] audit trail
[C] analysis guide
[D] analysis manual
[E] [A] or [B]
E
Mr Jacob has been hired as an auditor in a banking institution. He has been assigned
with two tasks. The first task is to evaluate if the information provided by the systems
will always be satisfactory and reliable. The second task is to evaluate if the
information in the bank systems will be accessible for the business when required.
Mr Jacob’s task involves evaluating ________.
[A] security
[B] integrity
[C] availability
[D] [B] and [C]
[E] All of the above
D
Businesses require the detection, or the correction, or cost-effectively preventing
risks. In the context of business control strategies dictating the handling of risks, who
decides on activities to be ensured and risks to be managed or transferred on
completion of risk analysis?
i) auditors
ii) chief auditor
iii) members of the management
iv) executive personnel of the organisation
[A] i) and iii)
[B] i) and iv)
[C] ii) and iii)
[D] iii) and iv)
[E] All of the above
D
The process of identifying and assessing business risk, including taking steps
towards reducing the risk to an acceptable level, is called risk ________.
[A] elimination
[B] reduction
[C] indemnifying
[D] management
[E] avoidance
D
Auditors have a standard method to select items for testing. The general
understanding is that auditors’ standard method to select items for testing is an
unchanging limitation. Which of the following is the auditor’s limited method to
determine appropriate items for testing?
[A] Auditing all items or events of a population
[B] Scrutinising all minutes of shareholders’ meetings
[C] Meeting the objectives of the audit procedures through testing
[D] The unlikelihood that an auditor examines every item in a population
[E] [A] and [B]
D
The Internal Control infrastructure assists management to achieve business
objectives. Which component of Internal Control is described by the characteristics
listed below?
i) Establishing the conditions under which all Internal Controls will operate
ii) A function of management’s philosophy and operating style
iii) Training human resources according to the required standard to promote
competence in exercising control
iv) Quality of employees who implement the Internal Controls, such as possession
of ethical values and integrity
[A] Effective monitoring
[B] Sound control environment
[C] Sound risk assessment process
[D] Sound operational control activities
[E] Practice providing the opportunity to report shortfalls
B
The common practice of businesses is to categorise risks, based purely on the
________.
[A] organisation’s response to them
[B] specialisation of organisational middle management
[C] availability of resources to handle them
[D] [B] and [C]
[E] [A] and [C]
E
In business operations, the main reason for requiring auditors’ confirmation of the
adequacy and effectiveness of the internal control system is because ________.
i) risks can be controlled
ii) risks can be influenced
iii) risks can be characterised
iv) risks cannot be eliminated
v) risks can only be managed
[A] i) and ii)
[B] ii) and iii)
[C] iii) and iv)
[D] iv) and v)
[E] All of the above
D
How many high-level control objectives in the IT governance framework that is based
on a set of best practices for information management, and intended for use by IT
audit professionals to enable good practice for policy development of IT control?
[A] 12
[B] 24
[C] 35
[D] 40
[E] None of the above
E
The City Bank is undergoing a process of evaluation to the transaction life cycle of its
Application Controls. The process of evaluation aims to provide management with
reasonable assurance about the accuracy and completeness of transactions
producing system information. What are the elements of evaluation?
i) data origination
ii) preparation
iii) input
iv) transmission
v) processing
vi) output
[A] i), ii), and iv)
[B] iii), v), and vi)
[C] i) and iv),
[D] i), iii), iv), v) and vi)
[E] All of the above
E
If risks that exist in the business can be mitigated entirely within the business, they
are categorised as ________.
[A] unpleasant
[B] impossible
[C] undefeatable
[D] controllable
[E] unbearable
D
In the context of performing Information Systems Auditing, what are CAATs?
[A] Computer Appropriate Actions To Systems
[B] Computer Actions Appropriate for Teams
[C] Computer Actualizing Audit Tools
[D] Computer Aided Audit Techniques
[E] Computer Acoustic Applications Tools
D
During risk assessment activities within a business environment, the impact analysis
stage is characterised by ________.
[A] criticality of data
[B] sensitivity of data
[C] assessment of asset criticality
[D] analysis of the mission impact
[E] All of the above
E
The IT governance framework that is based on a set of best practices for information
management, and intended for use by business and IT management as well as IT
audit and assurance professionals, is called (the) ________.
[A] ITGI
[B] COBIT
[C] ISACA
[D] IT guide
[E] IT transcript
B
Which fundamental principle of auditing is associated with the passage below?
Auditors act in the interests of primary stakeholders, while having regard to the wider
public interest. The identity of primary stakeholders is determined by reference to the
agreement requiring an audit.
[A] Accountability
[B] Materiality
[C] Judgement
[D] Objectivity
[E] Rigour
A
Which fundamental principle of auditing is associated with the passage below?
Auditors may allow their reports to be included in documents containing other
information only if they consider the additional information not to be in conflict with
the matters covered by their report. Another reason for auditors to allow their reports
to be included with other information is if they do not believe that other information is
misleading, such as wrongfully gaining confidence.
[A] Judgement
[B] Association
[C] Competence
[D] Providing value
[E] Clear communication
B
Which of the following is one of the key elements in the definition of Information
Systems Management (ISM)?
[A] businesses
[B] strategies
[C] capital
[D] investments
[E] None of the above
B
Why do organizations develop and maintain Information Systems?
[A] To exploit latest technologies
[B] To achieve organisational strategies
[C] To create a social networking presence on the Web
[D] To be modern
[E] All of the above
B
In which way(s) can a computerized Information System (IS) implemented in an
organization benefit business processes in an organization?
[A] By automatically creating procedures to be followed by employees
[B] By automatically documenting process policies to be obeyed by employees
[C] By moving work from the computer side to the human side
[D] By automating processes, thus reducing labor costs
[E] All of the above
D
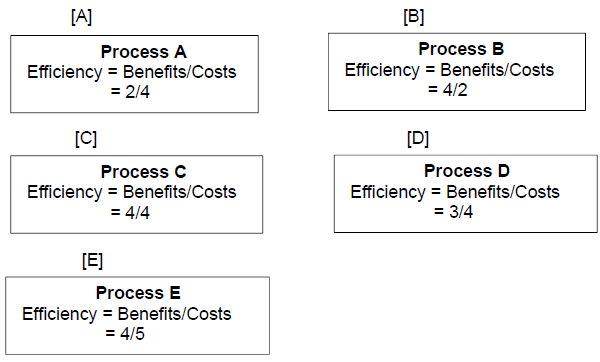
The five processes A, B, C, D, and E below accomplish the same function. From
among the five processes below, select one process that is more efficient than the
rest of the processes.
B
Which of the following is the correct sequence of a planning process used by
organizations to determine the requirements and functions of an Information System
to be developed?
i) Determining Value Chains
ii) Developing a Competitive Strategy
iii) Determining Information System requirements and functions
iv) Determining Business Processes
v) Analysis of Industry Structure
[A] v) –> ii) –> i) –> iv) –> iii)
[B] i) –> ii) –> iii) –> iv) –> v)
[C] ii) –> iv) –> v) –> i) –> iii)
[D] iv) –> i) –> v) –> iii) –> ii)
[E] ii) –> v) –> iii) –> i) –> iv)
A
What is the end result of an Information System that uses the following functions?
i) Sales forecasts to plan production;
ii) Production plan to determine raw material needs; and
iii) Material needs to schedule purchases
[A] Lean-in-time inventory
[B] Enterprise Recourse Production (ERP)
[C] Just-in-time inventory
[D] Smart Production
[E] Agile-in-time inventory
C
Information Systems vary by Scope. All of the following are Information Systems Scope
EXCEPT _________.
[A] Enterprise Information System
[B] Workgroup Information System
[C] Integrated Information System
[D] Personal Information System
[E] Inter-enterprise Information System
C
When an organisation’s strategy changes, what should the IS function do in response?
[A] Consider changing the information system management structure
[B] Consider restructuring the IS organisation
[C] Review the new strategy of the organisation
[D] Review the adequacy of its current IS capacity and plan appropriate action
[E] Review the capability of the CIO
D
IS procedures are ________.
[A] designed to ensure confidentiality, integrity and availability of IS
[B] tried and tested ways of implementing IS services in various aspects of ISM
[C] guidelines for how IS operations and management must be carried out on
daily basis
[D] mainly written step-by-step instructions for processes that need to be
followed in IS operations management
[E] mainly mandated rules from top management regarding IS management
D
IS Best Practices are ________.
[A] revised and documented issues on IS confidentiality, integrity and
availability
[B] tried and tested ways of implementing IS services in various aspects of ISM
[C] guidelines for how IS operations and management must be carried out on
daily basis
[D] mainly written step by step instructions for processes that need to be
followed in IS operations management
[E] mainly mandated rules from top management regarding IS management
B
The emergence of high speed networks, high capacity and resilient hardware, and
distributed architecture support systems have made which of the following information
system management structure possible?
[A] Centralised
[B] Decentralised
[C] Hybrid
[D] Traditional
[E] Matrix
C
Why is it important for the management structure of information systems management
within an organisation to be aligned to the various functions within the organisation?
[A] To create independence between management and information systems
[B] To achieve autonomy in decision making
[C] To conform to the organisation’s management structure
[D] To achieve responsibility and accountability
[E] To develop an IS specialisation
D
Which would be the most appropriate IS management organisational structure for an
organisation that wishes to achieve standardised hardware, software and efficient
utilisation of its IS personnel?
[A] Centralised
[B] Decentralised
[C] Hybrid
[D] Traditional
[E] Matrix
A
Which of the following is a description of a Managed Service within a business
environment?
[A] It is a collection of Service Level Agreements (SLAs) wherein the client
reviews SLAs and the conversation between parties focuses on how SLAs
can be improved
[B] When the client and vendor equally participate in sourcing their respective
pieces of work and create a project team
[C] When a third party provides services to an organisation, but the organisation
maintains management control over the complete service and the individual
services are provided as a series of separate provisions
[D] When project reviews are centred around project delivery, team skills,
experience and personnel attitude.
[E] A service that manages the quality of project resources where the project
quality and timelines are unknown.
C
Who is responsible for coordinating the people and resources needed to successfully complete a systems development project?
[A] System stakeholder
[B] Systems analyst
[C] Project manager
[D] Steering team member
[E] Project sponsor
C
A develoment team is investigating the feasibility of a systems development project. Their client has given them a budget of R500,000 for the system to be designed, developed and implemented. Their project estimate has been calculated at R525,000. This project could face problems with ________ feasibility.
[A] technical
[B] legal
[C] economic
[D] operational
[E] schedule
C
Benefits of buying software, rather than developing it, are that ________.
i) the quality of the software can be assessed before purchasing
ii) it requires many in-house resources
iii) the software will meet the requirements more closely
iv) the software can be obtained immediately
[A] i) and ii)
[B] ii) and iii)
[C] iii) and iv)
[D] ii) and iii)
[E] i) and iv)
E
Which of the following regarding the Pareto principle are true?
i) This principle means that implementing 80 percent of the system will achieve most of the desired benefits
ii) When applied to systems development, the system will have a low cost and quick completion time
iii) When applied to systems development, the system will have a high cost, but a speedy completion time
iv) When applied to systems development, it will deliver an ideal solution
v) This principle is also known as the 80-20 rule
[A] i) and iv)
[B] ii) and v)
[C] i), ii) and iv)
[D] i), iii) and v)
[E] ii), iv) and v)
B