L19 - T19A - S4 - Secure Shell
1/7
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
8 Terms
Secure Shell (SSH)
Remote access protocol that connects to a command interpreter
Uses TCP port 22 by default
Uses encryption to protect each session
Has many commercial + open-source versions for all major OSs
Pair
Fingerprint
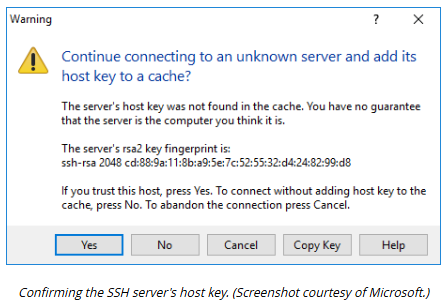
Each SSH server is configured with a public/private encryption key ___1___ identified by a host key __2___
Clients use the host key ____2____ to verify that they are attempting to connect to a trusted server
This mitigates risk of on-path attacks
True
Alternatively there are various enterprise software products designed for SSH key management
True or False: A mapping of host names to SSH server keys can be kept manually by each SSH client
Key
Securely
The server’s host ___ pair is used to set up an encrypted channel so that the client can submit authentication credentials _____
2 common methods SSH allows for client authentication to the server
Password authentication
Public key authentication
Extra
These methods can be enabled or disabled as required on the server
Password Authentication — SSH Client-Server Authentication
The client submits a username and password that are verified by the SSH server either
Against a local user database
Using an authentication server
e.g. a RADIUS Server or TACACS+
Public Key Authentication — SSH Client-Server Authentication
The server is configured with a list of the public keys of authorized user account
The client requests authentication using one of these keys,
The server generates a challenge with the user’s public key
The client must use the matching private key it holds to decrypt the challenge
This completes the authentication process
Critical
SSH
Monitoring for and removing compromised client public keys is a ____ security task
Many recent attacks on web servers have exploited poor _____ key management