2.4 Replay Attacks & Malicious Code
1/10
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
11 Terms
Replay Attack
An attacker intercepts network traffic between a client and server, the attacker then replays this captured data to the server, impersonating the victim.
To carry out this attack, the attacker needs access to raw network data, which can be obtained through methods like a network tap, ARP poisoning, or malware on the victim's computer.
The replay attack itself is not an on-path attack, it is often preceded by one to gather the necessary data for replaying.
Address Resolution Protocol (ARP):
Find the MAC address of a computer with a known IP address
Pass The Hash
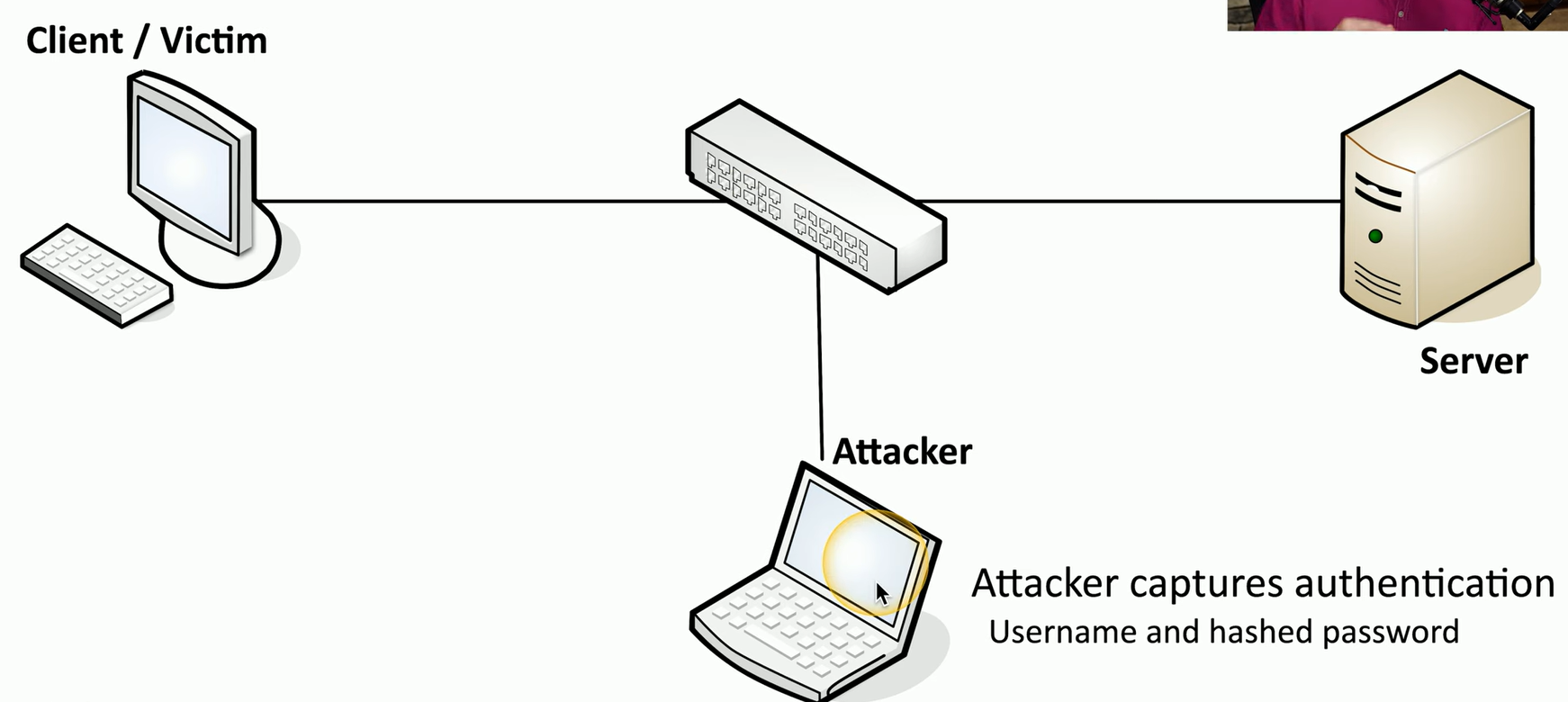
This starts with the client or the victim computer sending a normal authentication request to a server.
During that process, the attacker has put in place a way to redirect or get a copy of that traffic also sent to the attacker’s computer.
Once the attacker has this information, they can replay the username and hashed password back to the server posing as the original client.
The server receives a username and hashed password that properly authenticates, so the attacker now has access to the server posing as the victim computer.
Stop Passing The Hash
Use encryption so that none of the traffic sent across the network can be seen.
Include some additional salting of the password so that, each time an authentication occurs, it’s using a different salt and, therefore, a different hash.
Server is configured to not accept the same hash twice in a row.
Browser Cookies
Are files that store information about the websites you visit, helping manage sessions and tracking on those sites.
Themselves aren’t executable or malicious, but they contain valuable information, such as usernames and session details, which can pose privacy risks.
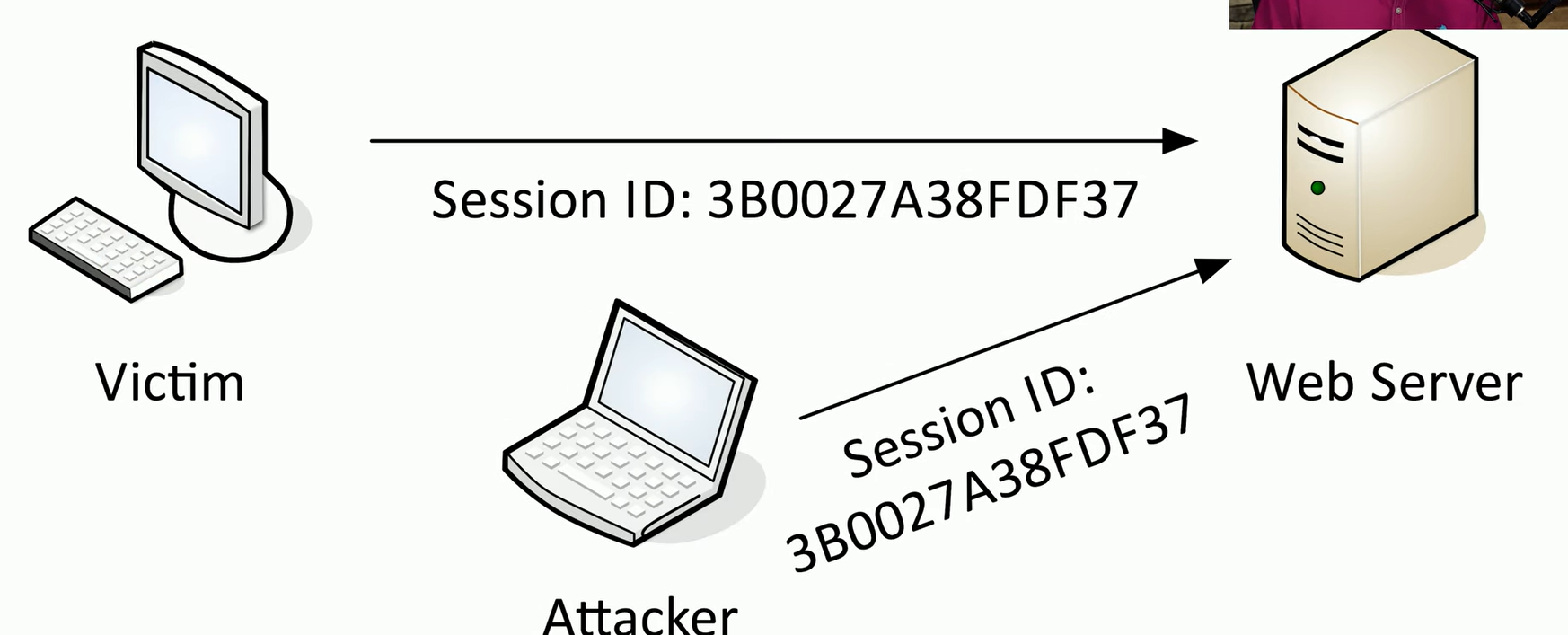
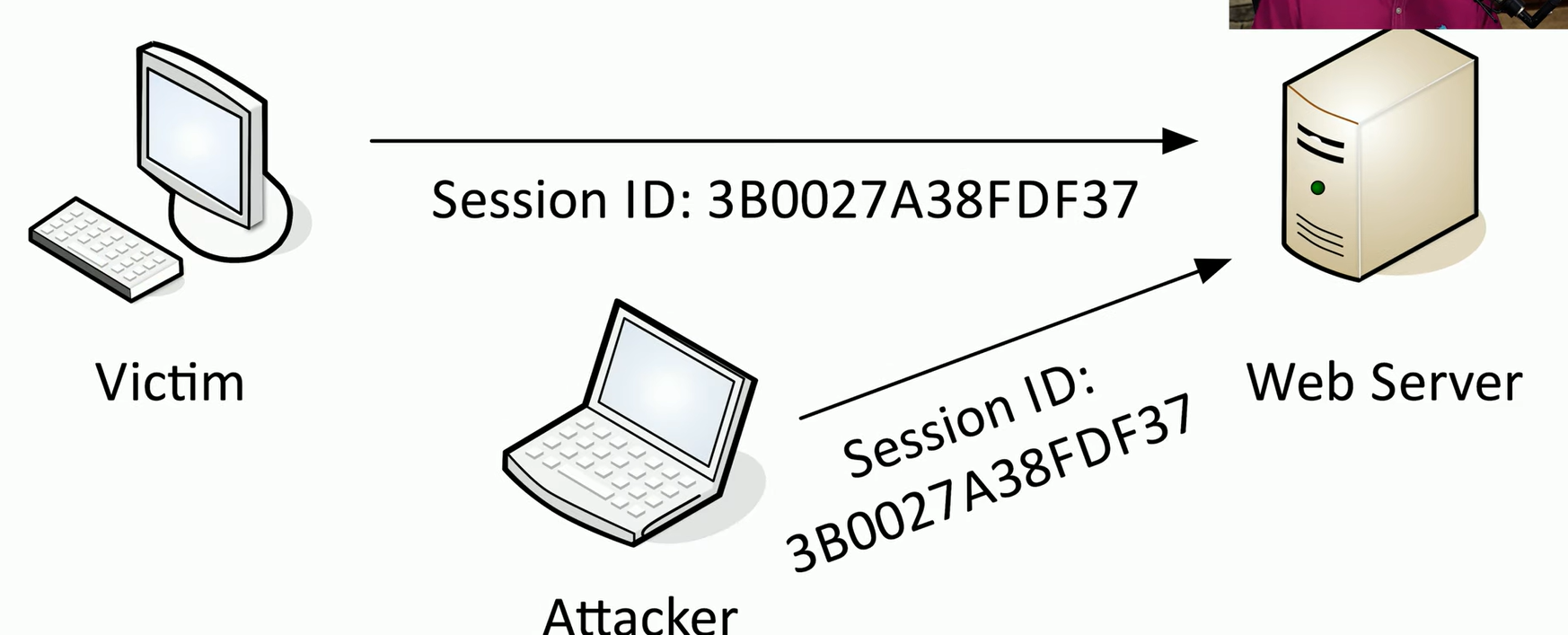
Session Hijacking (Sidejacking)
When a user authenticates initially with a web server. So they provide a username and password, and a session ID is sent back to the victim’s computer.
If the attacker does gain access to the session ID, they can use it for subsequent sessions to the web server.
And every time they use this session ID, the web server thinks it’s coming from the original victim’s computer, which is now logged in.
And the attacker would now have access to everything the victim machine would have on that web server.
Header Manipulation
Involves intercepting and modifying the headers sent between systems, which may contain sensitive details like session IDs.
Tools like Wireshark or Kismet can capture these headers
Exploits such as cross-site scripting can steal these details from a client machine
Can then use tools like Firesheep or Scapy to modify headers
Cookies Manager+ Firefox add-on can be used to tamper with cookies
Prevent Session Hijacking
Encrypting all communications; attackers can't see the session ID, they can't capture it.
Enabling HTTPS ensures that the connection is secure
Many websites are now HTTPS-only
Browser extensions can enforce HTTPS connections, preventing any unencrypted traffic.
If end-to-end encryption isn't possible, encrypting the connection from your device to a VPN concentrator can provide security for the initial part of the journey, leaving only the final segment unencrypted.
Exploiting A Vulnerability
Can be done through various methods,
Social engineering
Using default credentials
Exploiting misconfigurations
These attacks often don't require advanced technical skills, as they target mistakes made by users.
Exploiting misconfigurations is like walking through an unlocked door, using malicious code requires more technical expertise.
Malicious Code
Encompasses various methods used to gain unauthorized access to systems
Executables, scripts, macro viruses, worms, and Trojan horses.
To defend against these threats, a comprehensive protection strategy is required.
Using anti-malware software to block executables and potentially harmful scripts, employing firewalls to filter malicious traffic, regularly updating and patching systems to close vulnerabilities, and promoting secure computing habits to prevent social engineering attacks like phishing.
Malicious Code Examples
WannaCry ransomware exploited a vulnerability in Windows SMBv1, allowing attackers to execute arbitrary code and run any software on a victim's machine.
The British Airways cross-site scripting attack involved injecting malicious JavaScript into checkout pages, stealing credit card information from around 380,000 victims.
The Estonian Central Health Database breach occurred through SQL injection, allowing attackers to access sensitive health data for all citizens of Estonia, compromising the entire database.