SRCS-PT-Virtualization and Microkernel hypervisors
1/3
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
4 Terms
In the context of virtualization, how does dynamic resource allocation contribute to optimizing performance, and what challenges might arise in managing dynamically allocated resources?
Dynamic resource allocation in virtualization serves as a pivotal strategy for real-time optimization, ensuring resources align with varying workload demands. This dynamic adaptability enhances overall system efficiency. However, challenges emerge, such as the delicate balance required to manage resource contention effectively and prevent overcommitment. Addressing these challenges necessitates the implementation of intelligent algorithms and robust monitoring tools to ensure the seamless orchestration of dynamically allocated resources.
How can virtualization technologies enhance fault tolerance in critical systems, and what strategies should be employed to ensure seamless operation in the event of a failure?
Virtualization contributes to fault tolerance through features like VM snapshots, clustering, and high-availability configurations. VM snapshots enable quick recovery by capturing virtual machine states, while clustering provides redundancy and load balancing. High-availability configurations ensure continuous operation. Proactive monitoring, automated failover, and fault-tolerant hypervisors further enhance resilience. Implementing these strategies minimizes downtime and data loss in critical systems.
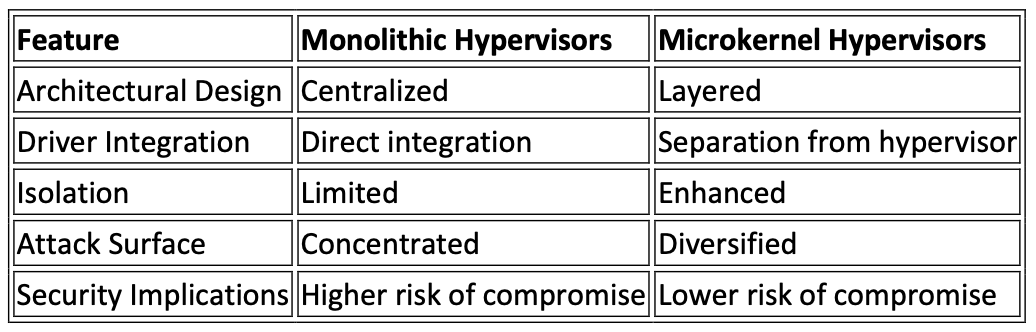
Explain the fundamental differences between microkernel hypervisors, exemplified by L4, and traditional monolithic hypervisors, highlighting the implications for security architecture.
Microkernel hypervisors, such as L4, and traditional monolithic hypervisors differ
fundamentally in their design principles, which significantly impact their security architecture.
(1) Architecture:
• Microkernel Hypervisors: Microkernels adopt a modular design where the
hypervisor's core functionality is kept minimal, with essential services implemented as
separate, user-space components. This design choice promotes simplicity and
isolation.
• Monolithic Hypervisors: Monolithic hypervisors, in contrast, incorporate most
functionalities within a single, large codebase running in privileged mode. This
approach may result in a more complex and interconnected system.
(2) Isolation and Attack Surface:
• Microkernel Hypervisors: The microkernel design minimizes the trusted computing
base, reducing the attack surface. Each service runs in a separate address space,
enhancing isolation and making it harder for an attacker to compromise the entire
system.
• Monolithic Hypervisors: Monolithic hypervisors have a larger attack surface because
all components share the same address space. A vulnerability in one part of the system
can potentially affect the entire hypervisor.
(3) Flexibility and Extensibility:
• Microkernel Hypervisors: Microkernels offer greater flexibility and extensibility due
to their modular nature. Additional functionalities can be added or removed without
affecting the core hypervisor, allowing for easier customization.
• Monolithic Hypervisors: Monolithic hypervisors may require more effort to add or
remove functionalities since changes can impact the entire system. This may result in
a less adaptable architecture.
(4) Formal Verification:
• Microkernel Hypervisors: Microkernels often lend themselves well to formal
verification methods due to their small codebase and modular structure. This can
enhance the confidence in the correctness of the hypervisor's security-critical
components.
• Monolithic Hypervisors: Formal verification is typically more challenging in monolithic
hypervisors because of their larger and more intricate codebase.
(5) Performance:
• Microkernel Hypervisors: Microkernels, by minimizing the core functionalities, aim for
better performance in terms of response time and resource utilization, making them
suitable for resource-constraint systems.
• Monolithic Hypervisors: Monolithic hypervisors may sacrifice some performance
optimizations for the sake of simplicity and integration.
Illustrate real-world scenarios where trap and emulate virtualization or binary translation are preferred over other virtualization techniques.
Legacy System Emulation → Binary Translation
Cross-Architecture Compatibility → Binary Translation
Virtualization on Embedded Systems → Trap and Emulate
Hardware-Assisted Virtualization Limitations → Trap and Emulate
Dynamic Code Translation for JIT Compilation → Binary Translation