Week 4: Hijacking and poisoning
1/56
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
57 Terms
What is hijacking?
An active attack to take over something that belongs to someone else, particularly at runtime
What is spoofing?
Masquerading or impersonation - pretending to be somebody you are not
What is the difference between hijacking and spoofing?
Hijacking takes over an existing connection, whereas spoofing initiates a new connection
What are the motivations for hijacking
Disrupting or jamming communications
Inserting false or malicious data
What is an on path adversary?
The compromised router that is involved in the path of an ongoing connection
What is an off path adversary?
The compromised router that is not involved in the path of an ongoing connection
On path adversaries vs off path adversaries
On path adversaries are more powerful because they use the connection state to predict sequence numbers in TCP hijacking, but are more difficult to scale up due to extra analysis
Inserting false data is very difficult for off path adversaries
What is poisoning?
Contamination of a trusted source of information
What are TCP connections identified by?
Their source and destination IP and port number, which links to applications running on hosts
What is the TCP three-way handshake?
The process by which a TCP connection is established
What are the steps of the TCP three-way handshake?
For client = c suffix, server = s suffix
SYN: SeqNo_c = x
SYN+ACK: SeqNo_s = y, AckNo_c = x+1
ACK: AckNo_s = y+1, SeqNo_c = x+1
What are the key header fields in a TCP three-way handshake?
port numbers (16 bits each)
SYN flag (1 bit)
ACK flag (1 bit)
Sequence number (32 bits)
Acknowledgement number (32 bits)
What is TCP session hijacking?
When an attacker injects data into an end to end TCP connection between two hosts
What are the steps for on-path TCP session hijacking?
1. Sniff packets to observe the ongoing TCP communication
2. Predict the sequence numbers being used by the client and server
3. Inject data by constructing a valid TCP segment with the correct source and destination IP and port, and a predicted sequence number acceptable to the recipient
How does the attacker predict the TCP sequence number in an on path attack?
An on-path attacker can observe the TCP communication between the client and the server by sniffing network packets
Why must the injected packet match the receiver's expected sequence number?
Because TCP will only accept data that matches the next expected sequence number; otherwise, it is buffered or discarded.
What happens if a spoofed packet uses a sequence number of x + δ instead of the expected x + 1?
It is considered out-of-order, and the receiver buffers it at position x + δ, leaving a gap of δ bytes.
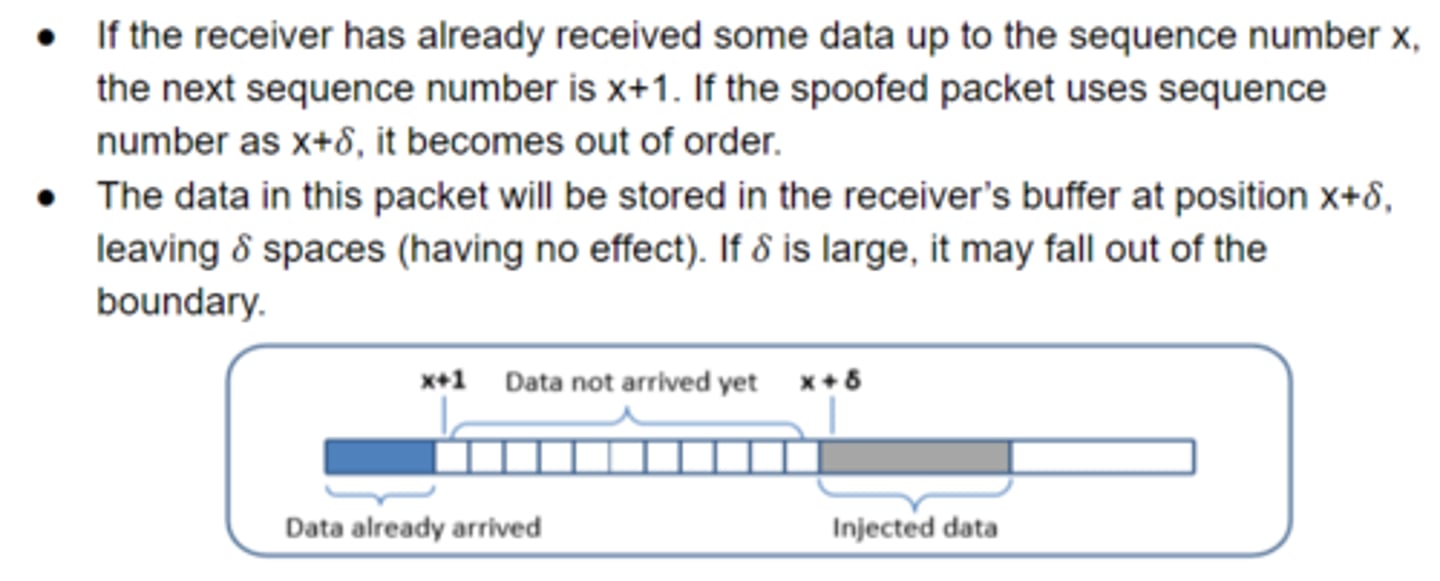
What is the consequence if δ is large when injecting data with an incorrect sequence number?
The data may fall out of the receiving buffer boundary, making it ineffective and discarded.
What mechanism allows TCP to handle out-of-order packets like the one at x + δ?
TCP buffers out-of-order packets in its receive window and waits for the missing earlier segments to fill the gap.
What are the challenges of off path TCP hijacking?
Off-path attackers cannot directly observe the sequence numbers. If an off-path attacker blindly spoofs a SYN packet, the real client may send a RST (reset) packet, terminating the connection
What is a TCP initial sequence number attack?
An off-path attack where the attacker tries to spoof the client by guessing the initial sequence number
How were initial sequence numbers historically generated?
Some TCP/IP stacks (like BSD Unix) used predictable ISN generation, increasing by a fixed amount per second and per new connection, making guessing easier
What are the steps of the TCP initial sequence number attack?
1. ICMP flooding the real client to prevent responses
2. Creating a real connection to the target server to record the server's sequence number
3. Closing the connection with the server
4. Sending a spoofed SYN packet as the client to the server, guessing the initial sequence number
5. The server sends SYN+ACK to the flooded client (ignored)
6. Sending a spoofed ACK packet to the server with the acknowledgement number based on the previously recorded server sequence number
What is Border Gateway Protocol (BGP)?
An inter-Autonomous System (AS) routing protocol that connects thousands of ISPs in the Internet
What is an autonomous system (AS)?
A single network or a group of networks controlled by a common network administrator (or group of administrators) on behalf of a single administrative entity
What are all ASs assigned?
A globally unique Autonomous System Number (ASN)
What is the CIDR prefix?
A notation used in BGP to represent subnets or collections of subnets.
It indicates the number of '1' bits in the subnet mask
BGP routes traffic based on CIDR prefixes
What does intra-AS routing mean?
Routing within the same AS
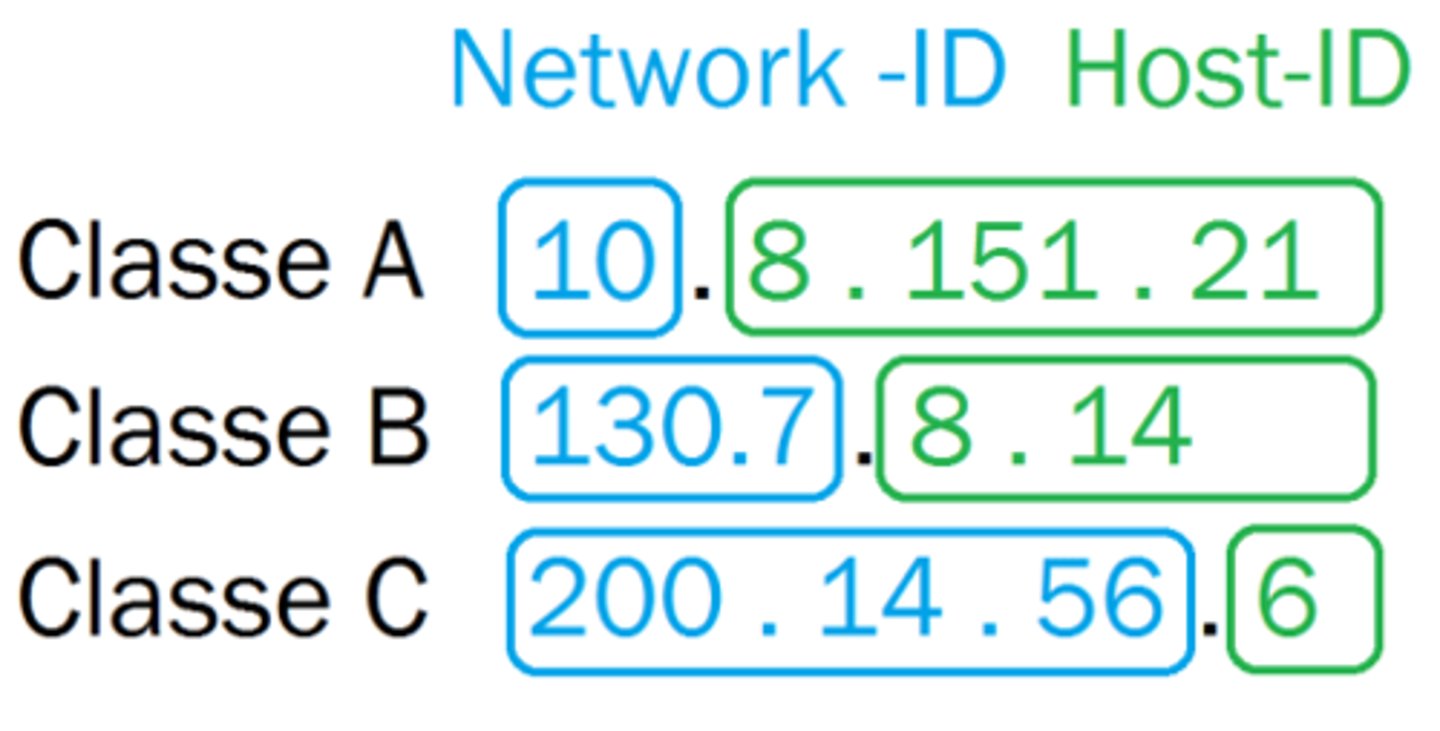
What is a classless IP address?
An address with any number of bits for its network portion
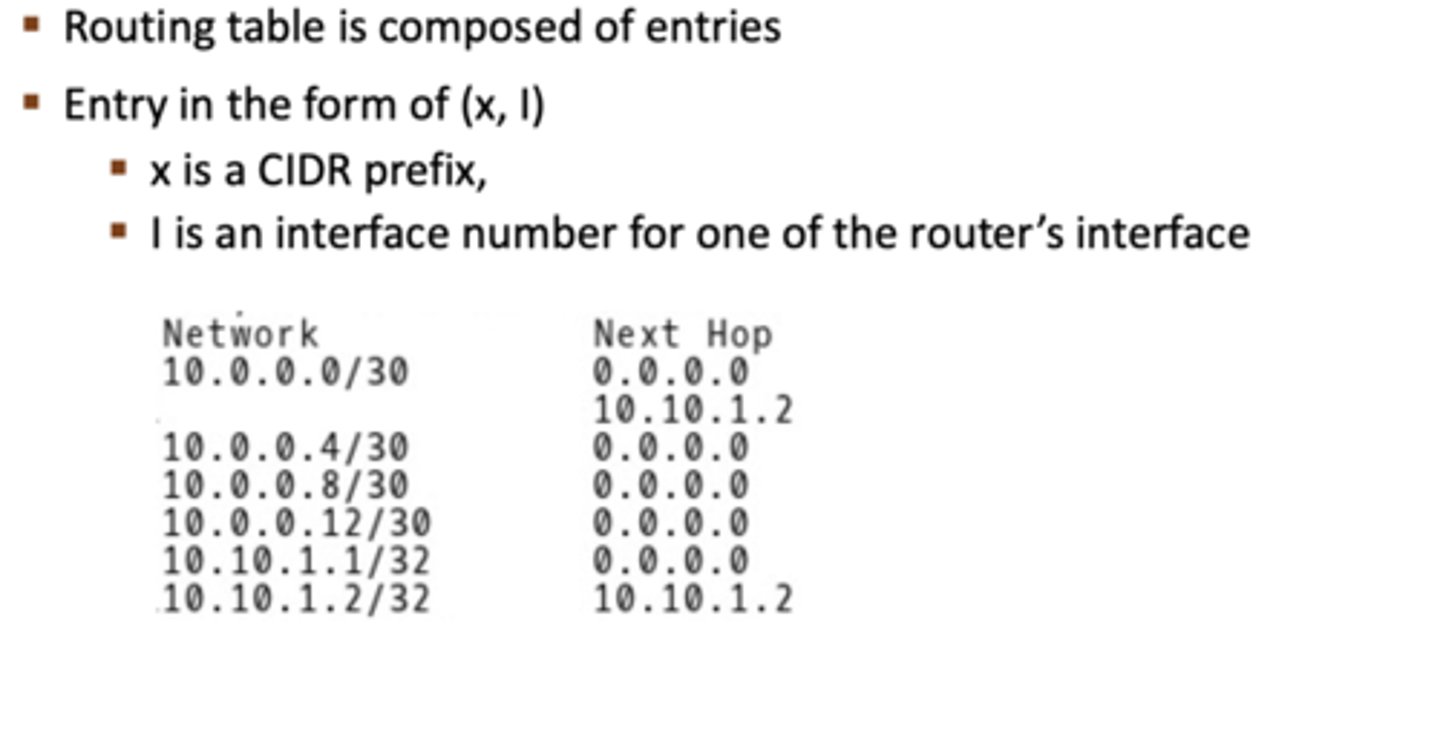
What is a BGP routing table?
Composed of entries in the form of (x, I), where x is a CIDR prefix and I is an interface number for one of the router's interfaces
What is BGP longest prefix matching?
When a router needs to forward a packet, it selects the route with the longest matching CIDR prefix, as this is considered the most specific route. This is why sub-prefix hijacking can be effective
How does BGP route advertisement work?
ASs advertise network prefix reachability information, including the advertised prefix and the AS path (sequence of ASs) that lead to that prefix, to neighboring ASs.
This information is exchanged over TCP connections using port 179
How are route advertisements expressed as for an AS?
A sequence of ASNs (descending order of most recently visited) and the subnet prefix
eBGP (external BGP)
BGP connections that span two different ASs and use TCP
iBGP (internal BGP)
BGP connections between routers within the same AS and use TCP
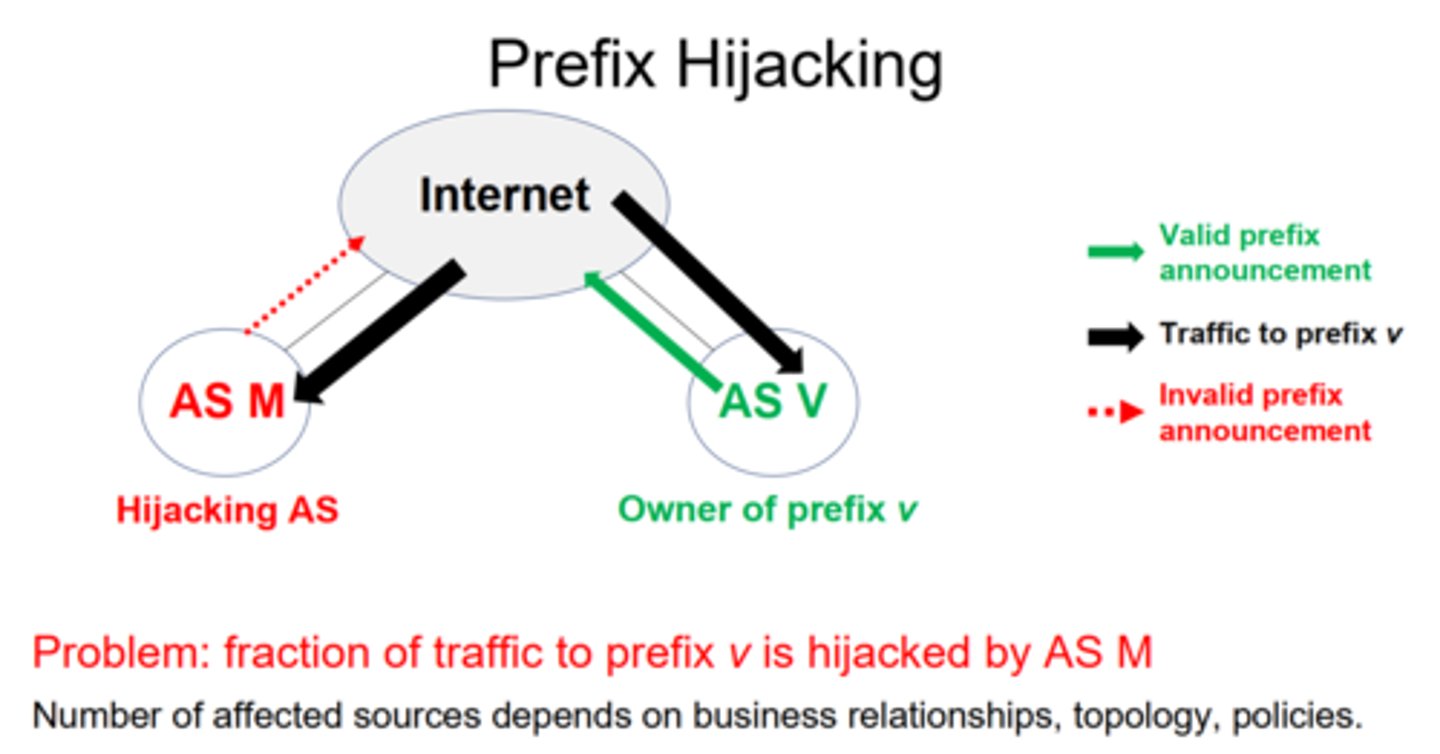
What is BGP prefix hijacking?
Occurs when an AS announces routes to network prefixes that it does not actually control. This false information can be added to BGP routing tables across the Internet
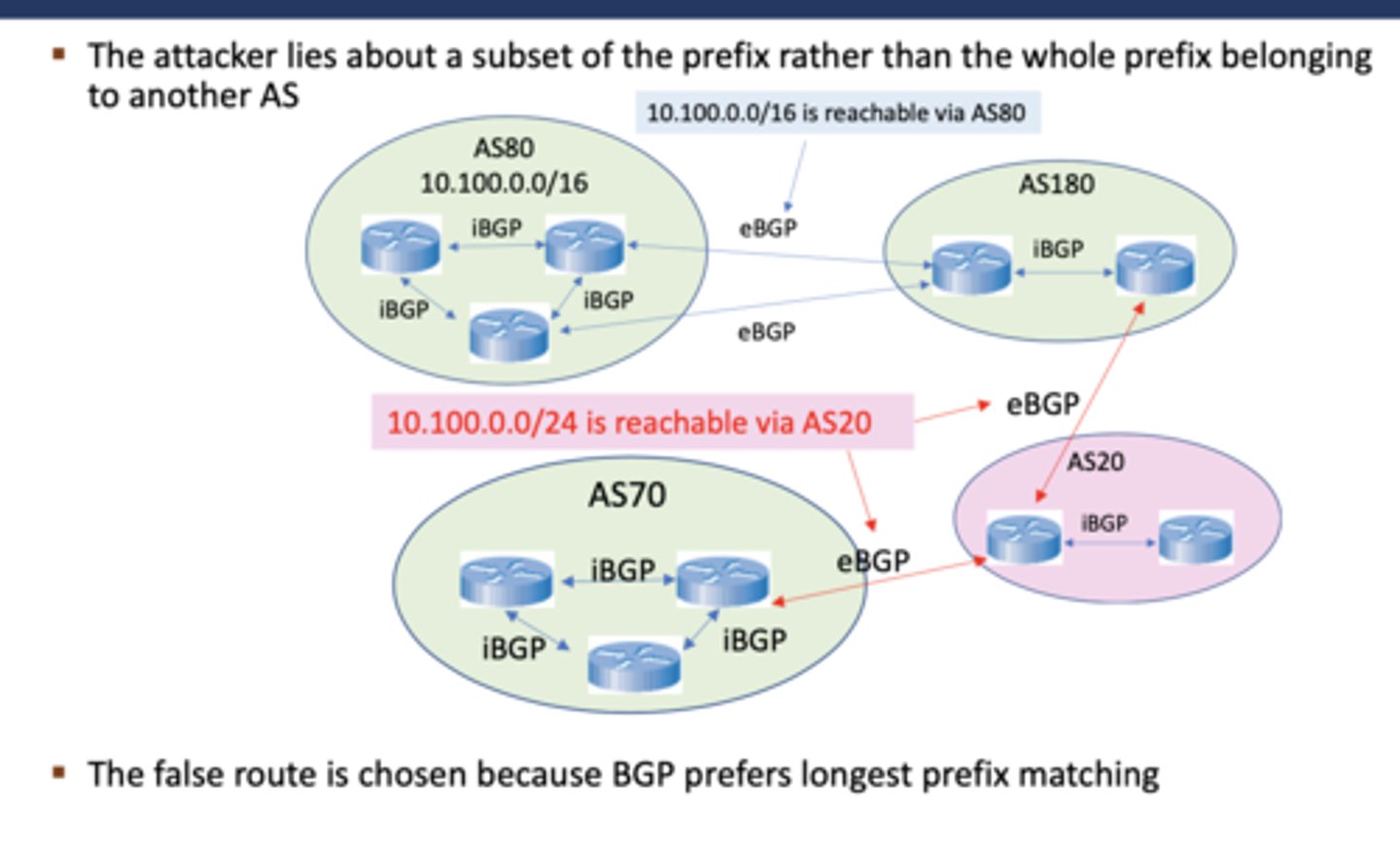
What is BGP sub-prefix hijacking?
The attacker lies about a subset of a prefix rather than the whole prefix belonging to another AS. This works because BGP prefers longest prefix matching
What is a BGP routing blackhole?
Created when an AS advertises routes it cannot actually offer, causing packets to be sent into a network blackhole and will be dropped after the TTL expires. The AS7007 incident in 1997 is an example.
What is the Domain Name System (DNS)?
A distributed database system that translates human-readable hostnames to IP addresses
What is the structure of DNS servers?
It is tree-like, with nodes containing the information associated with it
The root server is the root node, followed by the level top level domain and then authoritative servers
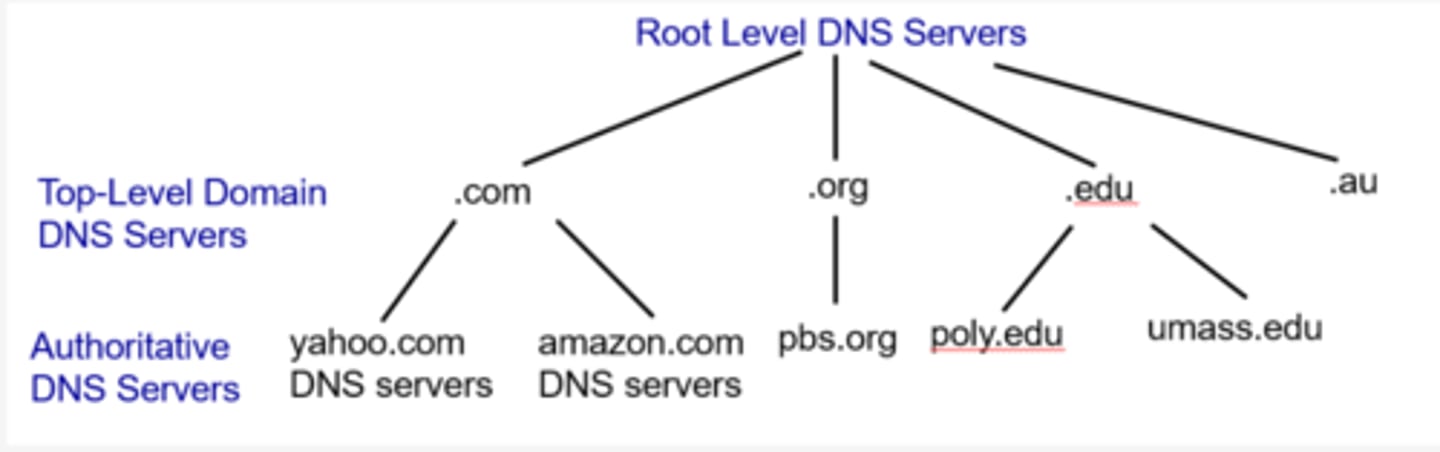
How is a domain name read in DNS?
As a path from the leaf to the root
What is DNS name resolution?
The process used to map names to IP addresses and IP addresses to names.
What is a DNS resolver?
A DNS client that requests information from DNS name servers.
How does an iterative DNS query work?
The DNS resolver directly queries each name server in the hierarchy, starting from the root server, and each server refers the resolver to the next level
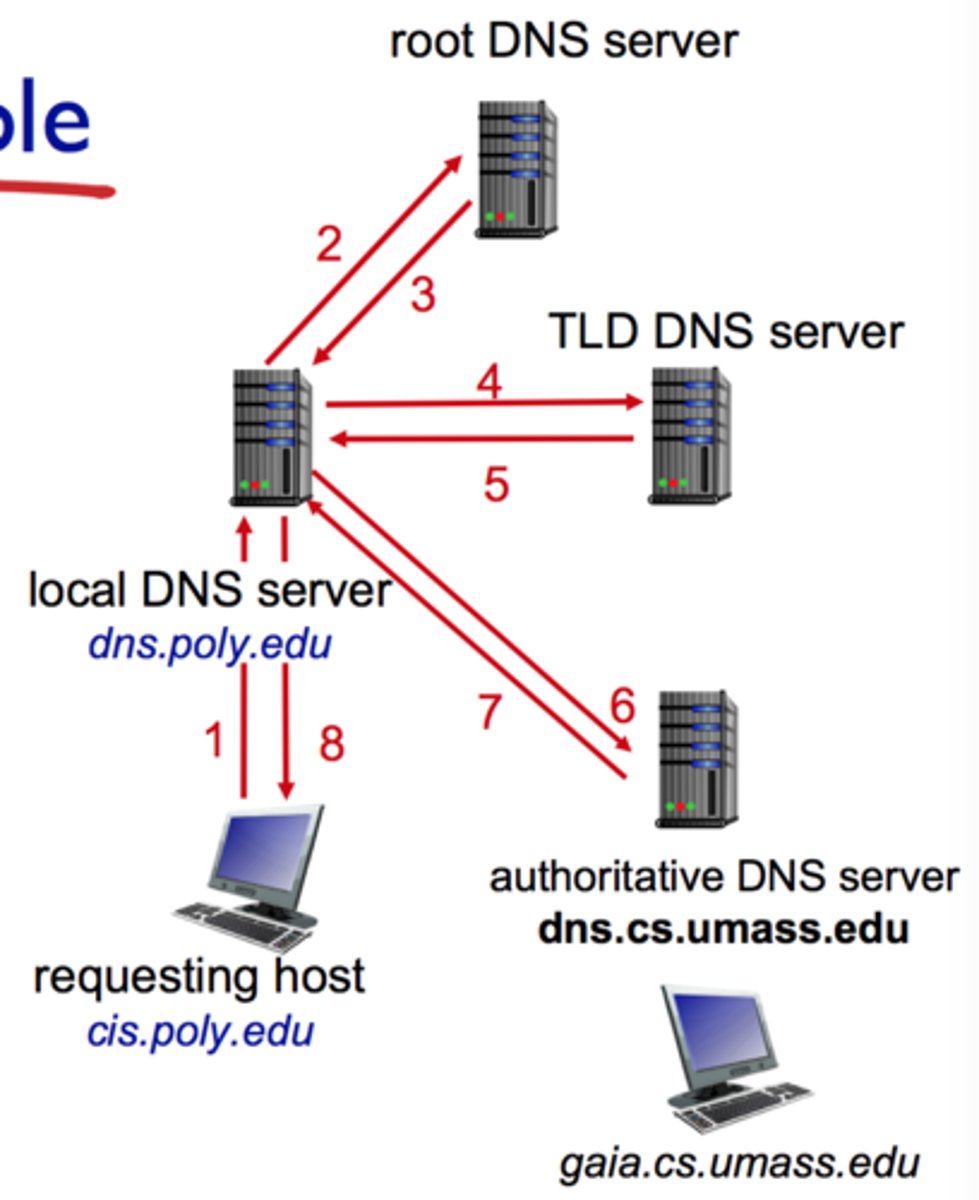
How does a recursive DNS query work?
The DNS resolver asks a name server to fully resolve the query. If the contacted server doesn't know the answer, it recursively queries other servers on behalf of the resolver.
Iterative vs recursive DNS queries
Recursive DNS queries are conceptually simpler, but does not scale and is not used in practice
What is a DNS cache?
DNS servers store resolved IP addresses for a certain TTL to answer subsequent queries faster, improving performance
Why do we need a DNS cache?
DNS queries require many repeated steps across lookups, which is not efficient
How do DNS queries work with caching?
Before performing the lookup, the local DNS server checks whether the lookup was done before - if it wasn't, then the lookup is performed and the server remembers the lookup in its cache
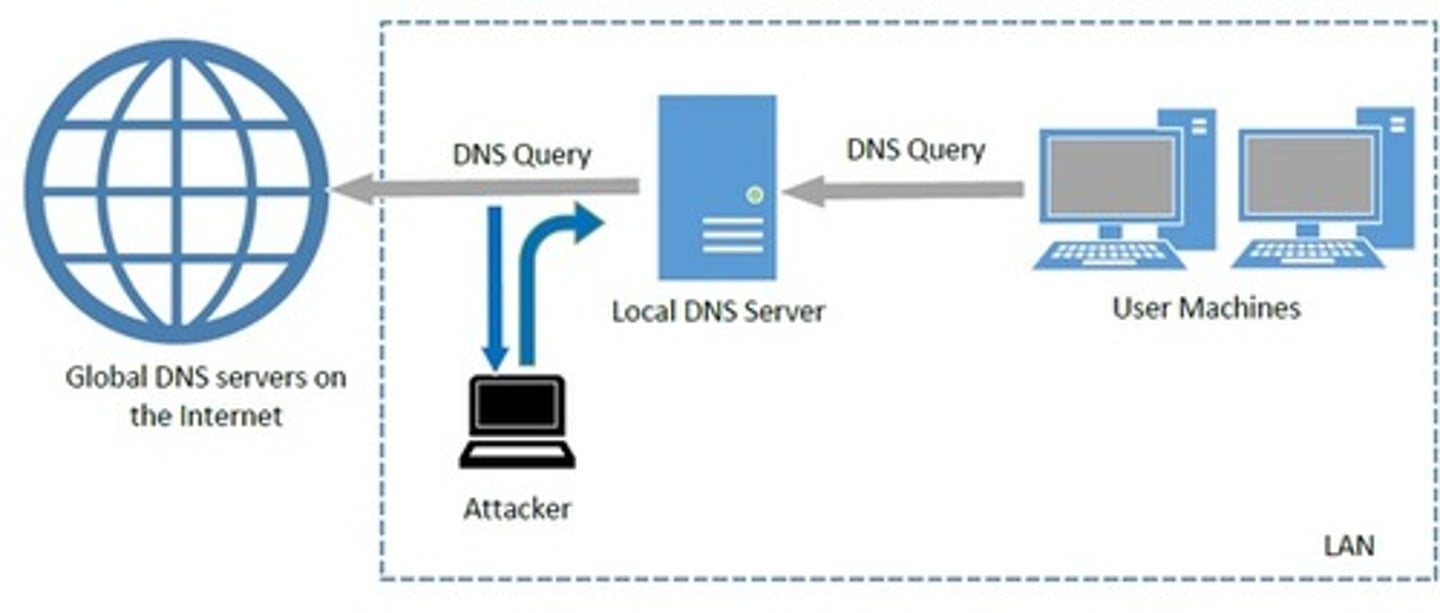
How does a DNS cache poisoning attack work?
attacker passively observes the client server activity
before the local DNS server expects a reply from the authoritative DNS server, the attacker sends a spoofed IP address to insert in its cache
If successful, clients querying the resolver for the poisoned domain will receive the incorrect IP address
What is the query ID (QID) of a DNS query?
A unique identifier in the query packet which is left intact by the server sending the reply, a way for the server to associate the answer of a lookup with its question
How can the QID be used in a DNS cache poisoning attack?
Attackers try to guess the QID of a legitimate query and send a forged response with the correct QID before the legitimate server, hoping their poisoned record will be cached
This works because DNS uses UDP which is connectionless, so the attacker does not need to establish a connection with the server
What is a Resource Record Set (RRSet)?
A group of DNS records with the same name and type
What is an RRSet attack?
Attackers can include a forged record for a different domain in the "additional" section of their malicious DNS response. If not properly checked, this can poison the cache with incorrect information for unrelated domains
What is a way to prevent RRSet attacks?
Bailiwick checking
What is Bailiwick checking?
A security mechanism to prevent RRSet attacks.
It involves checking if the names in the Authority and Additional sections of a DNS response are within the same domain (or a subdomain) as the query. Responses violating the Bailiwick rule should be rejected
How is a spoofed DNS response accepted by a local DNS server?
needs to have a matching source UDP port, the correct Question section, and the correct Query ID (TXID)