Advanced Network Security
1/63
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
64 Terms
![<p><strong>RSS-based Key Exchange</strong></p><p><strong>SITUATION:</strong></p><ul><li><p><code>A</code> and <code>B</code> use <code>PT_A = [12, … , 21]</code> and <code>PT_B = [12, … 22]</code>, and have <code>-8 p.u.</code> of mutual attenuation</p></li><li><p>Single-antenna static eavesdropper <code>ε</code>, with <code>-3 p.u</code>. to <code>A</code> and <code>-7 p.u.</code> to <code>B</code> </p></li><li><p>Assume packets do not carry a Source ID (anonymous)</p></li><li><p><code>ε</code> can identify the source based on the received power </p><ul><li><p><code>[5-9]</code> is <code>B</code>, <code>[16-18]</code> is <code>A</code>… but when <code>[9-16]</code>, who is transmitting?</p></li><li><p><code>ε</code> can only place a threshold in the middle <code>(12.5)</code> and decide <code>A</code> if <code>[9-12.5]</code> and B if <code>[12.5-16]</code></p></li></ul></li></ul><p></p><p><strong>ALGORITHM:</strong></p><ul><li><p>Assume <code>A</code> has a secret <code>KA = [1, 0, 1]</code> and <code>B</code> has a secret <code>KB = [0, 1, 0]</code></p></li><li><p>When <code>B</code> is transmitting a bit, we take it as it is; when A is transmitting, we complement it (<code>0->1, 1->0</code>)</p><ul><li><p><code>ε</code> knows about this (the algorithm is always public)</p></li></ul></li><li><p>At each slot, <code>A</code> and <code>B</code> extract random delay and TX power, and wait for such delay. The first one whose delay expires, transmit</p></li></ul><p></p><p><strong>QUESTION:</strong></p><p><strong>1: Compute the key</strong></p><p><strong>2: Compute the adversary’s guessed key.</strong></p><p></p>](https://knowt-user-attachments.s3.amazonaws.com/61c74427-69a3-44ee-a5ff-24087c522f5c.png)
RSS-based Key Exchange
SITUATION:
AandBusePT_A = [12, … , 21]andPT_B = [12, … 22], and have-8 p.u.of mutual attenuationSingle-antenna static eavesdropper
ε, with-3 p.u. toAand-7 p.u.toBAssume packets do not carry a Source ID (anonymous)
εcan identify the source based on the received power[5-9]isB,[16-18]isA… but when[9-16], who is transmitting?εcan only place a threshold in the middle(12.5)and decideAif[9-12.5]and B if[12.5-16]
ALGORITHM:
Assume
Ahas a secretKA = [1, 0, 1]andBhas a secretKB = [0, 1, 0]When
Bis transmitting a bit, we take it as it is; when A is transmitting, we complement it (0->1, 1->0)εknows about this (the algorithm is always public)
At each slot,
AandBextract random delay and TX power, and wait for such delay. The first one whose delay expires, transmit
QUESTION:
1: Compute the key
2: Compute the adversary’s guessed key.
1: Compute the key
K_AB = [0, 1, 0, 1, 0, 0]
Slot-by-slot reasoning:
Slot 1 – B transmits → take
K_B[1] = 0→K_AB[1] = 0Slot 2 – B transmits → take
K_B[2] = 1→K_AB[2] = 1Slot 3 – A transmits → use
K_A[1] = 1→ complement →K_AB[3] = 0Slot 4 – A transmits → use
K_A[2] = 0→ complement →K_AB[4] = 1Slot 5 – B transmits → take
K_B[3] = 0→K_AB[5] = 0Slot 6 – A transmits → use
K_A[3] = 1→ complement →K_AB[6] = 0
2: Compute the adversary’s guessed key.
K = [1, 0, 1, 1, 0, 1]
Correct guesses: 4 out of 6
Slot 1: RSS = 14 → inferred A → B sent 0 → guessed 1 ✅
Slot 2: RSS = 13 → inferred A → B sent 1 → guessed 0 ✅
Slot 3: RSS = 10 → inferred B → A sent 1 → guessed 1 ❌
Slot 4: RSS = 17 → inferred A → A sent 0 → guessed 1 ✅
Slot 5: RSS = 7 → inferred B → B sent 0 → guessed 0 ✅
Slot 6: RSS = 11 → inferred B → A sent 1 → guessed 1 ❌
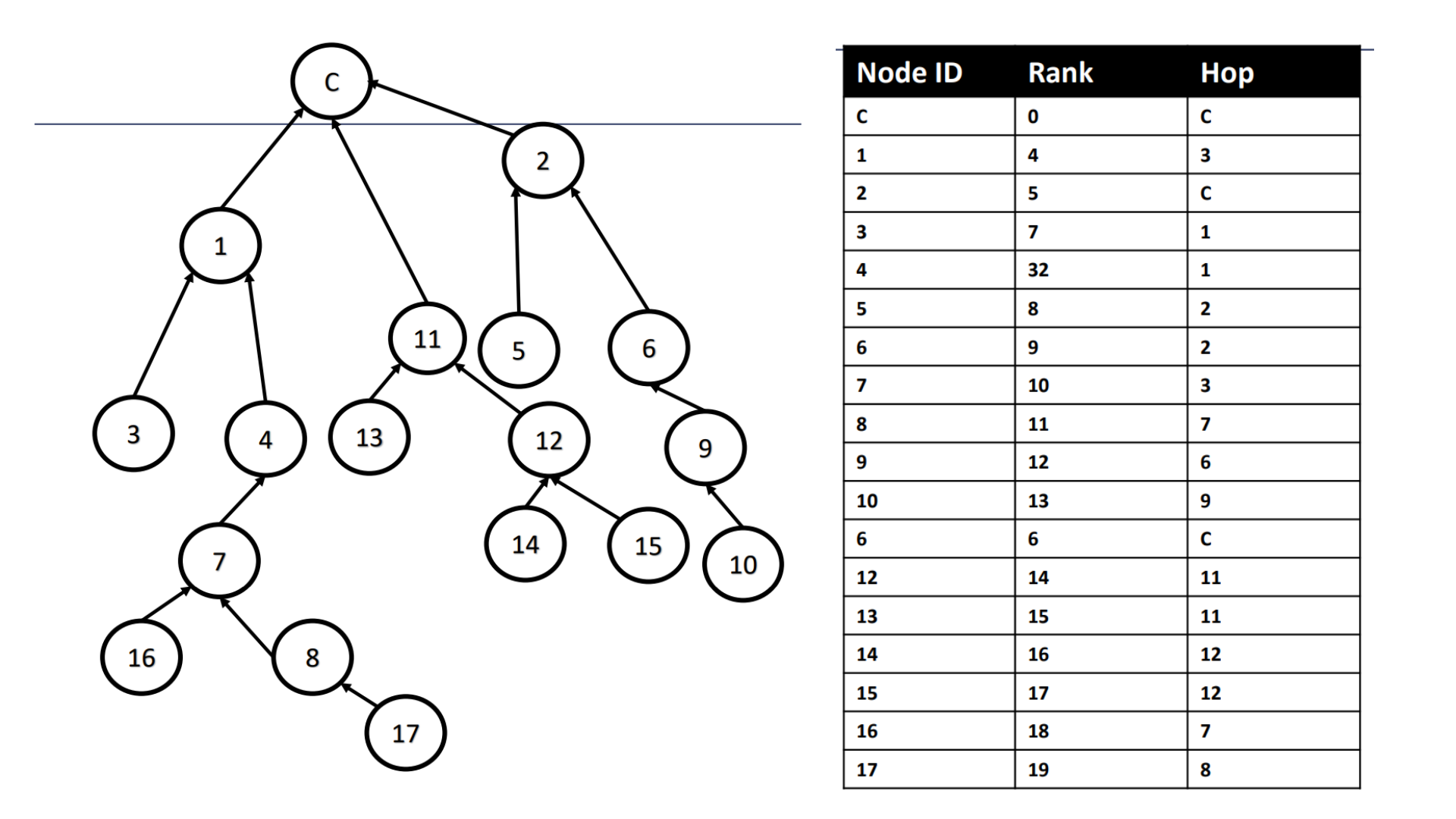
RPL
Identify the attacks and mention a mitigation for each attack
Sybil Attack
Issue: Node 11 isn't in the node list but appears in the topology. Node 6 appears twice.
Cause: Node 11 is likely impersonating Node 6 (multiple fake identities).
Mitigation: Enforce unique Node IDs and track identities using authentication.
Black Hole Attack
Issue: Node 1 accepts messages (e.g., from Node 3) but doesn't forward them to the root.
Cause: Node 1 is silently dropping traffic.
Mitigation: Use IDS or acknowledgment-based checks to detect non-forwarding nodes.
Increased Rank Attack
Issue: Node 4 has an unusually high rank (32) compared to its parent (1).
Cause: Node 4 advertises a fake high rank to disrupt routing.
Mitigation: Verify ranks using ACKs and limit drastic rank changes.
Security Planning
You are working with a constrained IoT device that needs to transmit a 655-byte message over a wireless IEEE 802.15.4 network. Your objective is to determine how many MAC-layer frames are needed to send the complete message while ensuring confidentiality and authenticity at the MAC layer.
Tasks:
Select the appropriate Auxiliary Security Header configuration
Choose the settings that provide the required security (authenticity + confidentiality) with minimal overhead.
Calculate the header sizes
Include all relevant fields from the MAC and security headers.
Use the parameters and addressing schemes listed below.
Determine the number of MAC-layer frames required
Account for maximum payload per frame after subtracting header overhead.
Divide the total message size accordingly.
COAP
UDP
RPL
IEEE 802.15.4 MAC
IEEE 802.15.4 PHY
Identify header sizes for each layer
COAP: 7 bytes
UDP: 8 bytes
RPL: 4 bytes
IEEE 802.15.4 (with security): 43 bytes
PHY: 1 byte
Break down the IEEE 802.15.4 MAC header
Base: 25 bytes
Auxiliary Security Header (
auxhd):Security Control: 1 byte
Frame Counter: 4 bytes
Key ID field: 4 bytes
MIC (authentication tag): 9 bytes
Total MAC layer header: 25 + 18 = 43 bytes
Calculate remaining payload space per frame (
K)MTU = 127 bytes
K = 127 – (7 + 8 + 4 + 43 + 1) = 65 bytesavailable for the message
Compute the number of frames (
M)Message size
N = 655 bytesM = ceil(655 / 65) = 11 frames
Which of these is not a security service defined by the ITU-T X.800 recommendation?
Authentication
Key Agreement
Authorization
Confidentiality
Key Agreement
Which of these is a security algorithm?
DTLS
SHA
IKE
SKKE
SHA
Which of these is not an attacker model?
Dolev-Yao
Man in the Middle
Canetti-Krawczyk
Honest-but-Curios
Man in the Middle
Which of these modes of operation of AES is inherently prone to cryptanalysis?
AES-OFB
AES-CTR
AES-ECB
AES-CBC
AES-ECB
Which one of these features is unique to the Industrial IoT application?
Data in Industrial IoT applications are typically more private than other IoT domains
IoT devices in Industrial IoT domains communicate with other IoT devices, not managed by the same system administrator
Constrained devices were already deployed in industrial domains, but not directly connected to the Internet
Wireless connectivity is prevalent, making it the prevalent vector to launch attacks
Constrained devices were already deployed in industrial domains, but not directly connected to the Internet
Which of these tiers of the IoT layered architecture is responsible for connecting the IoT devices to the Internet?
Device Tier
Gateway Tier
Cloud Tier
User Tier
Gateway Tier
Which of these attacks is NOT a Physical-Layer (PHY) attack?
Jamming
Energy Depletion
Side-Channel
Denial of Sleep
Denial of Sleep
Which of these statements about the adaption of IT security solutions to the IoT domain is true?
The security of IT-security approaches is not generally not that high, so they are feasible for IoT scenarios
All the cryptographic security testing done previously for IT networks should be verified again when including security solutions in the IoT domain
The Transport Layer Security protocol (TLS) is an example of a protocol that can be applied in a straightforward way from the IT to the IoT domain
When applied in the IoT domain, IT security approaches might lead to high energy consumption
When applied in the IoT domain, IT security approaches might lead to high energy consumption
Which of these conditions are likely to indicate that the communication channel is under jamming?
Low BER, low SNR
High BER, low SNR
Low BER, High SNR
High BER, High SNR
High BER, low SNR
Which of the following jamming techniques is more suitable to be selected by an attacker that does not want to be detected?
Deceptive Jamming
Constant Jamming
Noise Jamming
Sweep Jamming
Deceptive Jamming
Which of these jamming-related solutions would likely require the change of the hardware of a device?
Use of Time Synchronized Channel Hopping
Use of alternated transmission and silence
Use of Direct Sequence Spread Spectrum
Use of Received Signal Strength Indicator (RSSI)
Use of Direct Sequence Spread Spectrum
Which of these jamming techniques is more energy efficient for an attacker?
Proactive Jamming
Deceptive Jamming
Reactive Jamming
Barrage Jamming
Reactive Jamming
Which of these security functions is not provided by the IEEE 802.15.4 standard?
Protection against replay attacks
Data Confidentiality
Key Management
Data Authenticity
Key Management
Which of the following statements about link-layer security in IEEE 802.15.4 is true?
The IEEE 802.15.4 MAC payload can be authenticated, but the IEEE 802.15.4 MAC header cannot
The IEEE 802.15.4 MAC header can be encrypted but not authenticated
The IEEE 802.15.4 MAC Header cannot be encrypted
The IEEE 802.15.4 MAC payload cannot be authenticated
The IEEE 802.15.4 MAC Header cannot be encrypted
Which of these features is not provided by a Cryptographic Acceleration and Assurance Module (CAAM)?
Reduced memory size of the security solution
Increased code reuse for the security solution
Reduced Execution time for the security solution
Increased hardware independence of the security solution
Increased hardware independence of the security solution
Which of these keys is used in Zigbee IP to make the key establishment protocol confidential?
Master Key
Network Key
Link key
Pairwise Temporal Key
Master Key
Which of the following statements regarding Bluetooth keys is true?
The Application Key is used to securely broadcast packets in the network.
The Device Key is used to communicate securely with another device at the link layer.
The Link Key is used to derive the Device Key.
The Session Key, derived from the Network Key, is used to communicate securely with any other device in the network.
The Device Key is used to communicate securely with another device at the link layer
Which of these statements regarding the “Exchanging Public Keys” phase of the Bluetooth Secure Join is true?
Elliptic Curve Diffie Hellman (ECDH) is always used to generate the link key
It is based on the use of the FIPS P-160 elliptic curve
The new device always delivers its public key via the Bluetooth connection, even if an Out-Of-Band (OOB) channel is available
The availability of an Out-Of-Band channel is discovered through a bogus packet sent by the Provisioner to the new joining device.
Elliptic Curve Diffie Hellman (ECDH) is always used to generate the link key
Which of these security services is provided by the CCMP protocol in IEEE 802.11i?
Access Control
Peer Entity Authentication
Key Generation
Data Integrity
Data Integrity
Which protocol is used to carry authentication messages between the supplicant and the Access Point in IEEE 802.11 networks?
IEEE 802.11i
IEEE 802.11X
EAP over LAN (EAPoL)
RADIUS
EAP over LAN (EAPoL)
Which of these protocols is used by WPA2 for data confidentiality?
CCMP
AES-CCM*
AES-CCM
TKIP
CCMP
Which protocol is replaced by the Simultaneous Authentication of Equals (SAE) in WP3?
TKIP
CCMP
4-ways handshake
EAP exchange
4-ways handshake
Which of these registers in the GSM standard allows verifying the status of a Mobile Terminal?
Authentication Center
Home Location Register
Equipment Identity Register
Visitor Location Register
Equipment Identity Register
Which cryptographic algorithm is used by GSM to protect against eavesdropping on the communication channel?
A3
A5
A8
A9
A5
Which of these features enables authentication of the NodeB toward the 3G-USIM in 3G?
Delivery of AUTHN vector from the MT to the VLR
Delivery of AV from the AuC to the VLR
Delivery of RES from the MT to the VLR
Delivery of AUTHN vector from the VLR to the MT
Delivery of AUTHN vector from the VLR to the MT
Why is 3G preferred over GSM/2G in IoT today?
Support for data
Data Confidentiality
Mutual Trust
Use of standardized security algorithms
Support for data
Which of these attacks at the network layer of the IoT requires at least two nodes to cooperate?
Sinkhole
Blackhole
Wormhole
Hello Flood
Wormhole
Which of these cryptography algorithms is used in RPL for protecting against eavesdropping at the network layer?
RSA-SHA384
AES-CTR
AES-CBC
RSA-SHA256
AES-CTR
Neighbor attacks of RPL manipulate a single parameter of the RPL messages. Which one?
Rank
RPLInstanceID
DODAG-ID
Objective Function
Rank
When an IoT network uses RPL in Storing Mode, which element of the routing protocol can be abused to generate an attack?
DIO messages
Routing Table
Rank
DODAG-ID
Routing Table
Which of these security algorithms is recommended for use by CoAP?
RSA
RC4
AES
ECDH
ECDH
How DTLS allows for message reordering?
Counter in DTLS Record Header
Sequence Numbers in DTLS Record Header
Frame Counter in DTLS Record Header
It relies on message reordering features provided by TCP
Sequence Numbers in DTLS Record Header
Why DTLS is more exposed to Denial of Service (DoS) attacks than TLS?
DTLS adds acknowledgement messages that allow for better loss recovery, while TLS acks messages with other messages
TLS allows for reordering of messages, while DTLS requires correct order
DTLS allows for reception of messages out of sequence, and it does not immediately close the connection at the first error
DTLS adds HelloRetryRequest messages, which pave the way to DoS attacks
DTLS allows for reception of messages out of sequence, and it does not immediately close the connection at the first error
Which security protocol is referred to by MQTT regarding data integrity?
IPSec
TLS
DTLS
OSCOAP
TLS
Which of these information can be always extracted from communication packets through network traffic analysis?
Routing-layer headers
Packets Interarrival Times
Used encryption algorithms at the Application-layer
Transport-layer protocol used
Packets Interarrival Times
Which of these countermeasures can be used to mitigate the amount of information leaked through network traffic analysis?
Encrypt all traffic through an encryption algorithm
Enclose your transmitter into a Faraday cage
Always consume the same amount of energy per task
Transmit packets at regular intervals
Transmit packets at regular intervals
In event-triggered communications, which of the following countermeasures is not applicable to protect against side-channels?
Anticipate the transmission of a packet reporting an event by a small time
Encrypt all packets
Make packets all of the same size
Delay the transmission of a packet reporting an event by a small time
Anticipate the transmission of a packet reporting an event by a small time
Which of the following “features” is not applicable as a side channel to identify a drone?
Keystroke emanations
Unintentional Electro-Magnetic (EM) emissions
Energy consumption
Acoustic emanations
Keystroke emanations
Which of the following is a motivation for the ease of jamming GNSS signals?
Use of Binary-Phase Shift Keying (BPSK) modulation
Low Received Signal Strength (RSS) at the receiver
Low bit-rate
Use of globally available time and position information
Low Received Signal Strength (RSS) at the receiver
Why cryptographic solutions are not applicable for civil GNSS applications?
Hardware modification of satellites is largely impractical
The hardware of GNSS satellites cannot support cryptography operations
Cryptography solutions cannot be applied when the distance between the transmitter and the receiver is too large
Hardware modification of all civil GNSS receivers is impractical
Hardware modification of all civil GNSS receivers is impractical
Which of the following information cannot be useful to cross-check the authenticity of GNSS frames?
Messages broadcasted by Cellular Base Stations
Time to receive the signal
Readings from local Magnetometers
Received Power Level from the Satellites
Readings from local Magnetometers
Which of the following is not an element making the addition of security to ADS-B challenging?
Specific frequency used for wireless communication
Reliability of the communication link
Cost considerations
Broadcast scenario
Specific frequency used for wireless communication
Which of the following is not a reason why Public Key Cryptography (PKI) solutions cannot be adopted to secure ADS-B messages?
Not enough space in the payload for secure signatures
Need to elect/select a Trusted Third Party (TTP)
Time to execute cryptography operations
Message fragmentation would be required, that hardly couples with network reliability issues
Time to execute cryptography operations