TCP/IP
1/13
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
14 Terms
Describe how a packet would flow if computer A wants to visit a webpage. Dont worry about in depth just say the layers and protocol at each
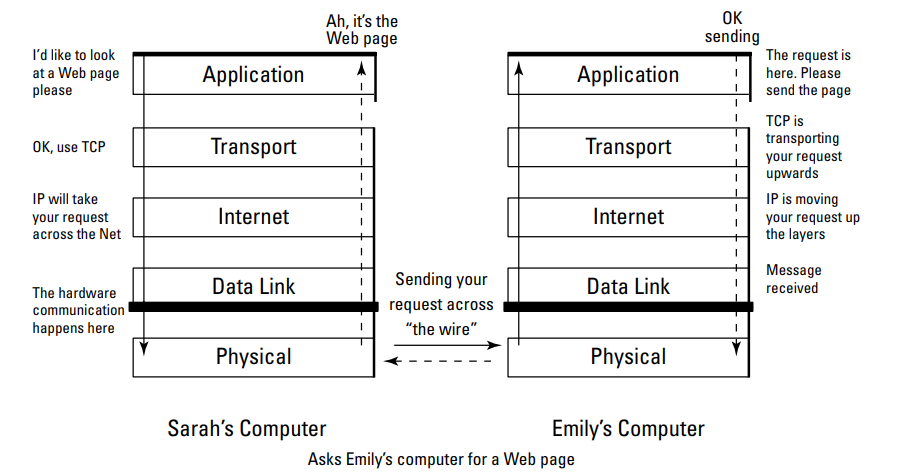
Explain the Application Layer (5)
The TCP/IP protocols that sit on Layer 5 receive packets from the lower protocols, de-packetize them back into their original form, and let the various TCP/IP applications and services manage the data according to the original user request, such as, “Please browse the Web.”
Layer 5 ✓ Establishes and coordinates a session, which is a connection between two computers: Before two computers can transmit data between themselves, they must establish a session. The session announces that a transmission is about to occur and, at the end of it, determines whether the transmission was successful. ✓ Works with operating systems to convert files from one format to another, if the server and client use different formats: Without file format conversion, file transfers could happen only between computers that have the same file format.
✓ Sets up the environment so that applications can communicate with each other and with users: Requests for service and data start at the application layer and move down through the remaining four layers before going out across a network. The application layer is also where secure protocols for specific applications, such as Web browsing and e-mail, reside.
Explain the Transport Layer (4)
Although the internet layer routes your information to its destination, it can’t guarantee that the packets holding your data will arrive in the correct order or won’t pick up any errors during transmission. That’s one of the transport layer’s jobs. TCP works at the transport layer to ensure that the packets have no errors and that all packets arrive and are reassembled in the correct order. Without this layer, you couldn’t trust your network. UDP also works at the transport layer and shares one function with TCP: to move your data up to the next layer. However, sometimes network services would rather be fast than correct, so UDP does no error checking on your packets, saving transport time.
Explain the Network / internet layer (3)
This layer receives packets from the data link layer (Layer 2) and sends them to the correct network address. If more than one possible route (or path) is available for the data to travel, the internet layer works out the best route. Without it, the data couldn’t reach the correct location. Internet Protocol is used.
Explain the Data Link layer (2)
- splits data into packets to be sent across the connection medium, and then wiring, such as Ethernet.
- The data link layer moves data up through the higher layers for transportation across networks and through tunnels to Virtual Private Networks (VPNs).
What are the layers of the TCP/IP stack. Give an example for each layer.
5. Application - HTTP, SSH, DNS, FTP, SMTP
4. Transport - TCP, UDP
3. Network - IP, ARP, ICMP
2. Link - Ethernet
1. Physical - wires, radio waves
What two possible types of IP address can you have (not v4 or v6)
Private and Public
Describe a private network
A private network is also known as a nonroutable network because it isn’t connected to the Internet — at least not directly. The TCP/IP For Dummies network is a private network hidden behind a firewall. None of our computers connects to the Internet. We can use any IP addresses on our private network we want because the Internet doesn’t know anything about them, and it doesn’t care. However, the Internet powers that be have reserved a set of addresses just for private networks. These addresses, which can be within the range of 192.168.0.0 to 192.168.255.255, appear often in the examples in this book.A private network is a closed network that is not directly accessible from the Internet, typically utilizing reserved IP address ranges such as 192.168.x.x. Devices within a private network can communicate freely, but require mechanisms like Network Address Translation (NAT) to connect to public networks.
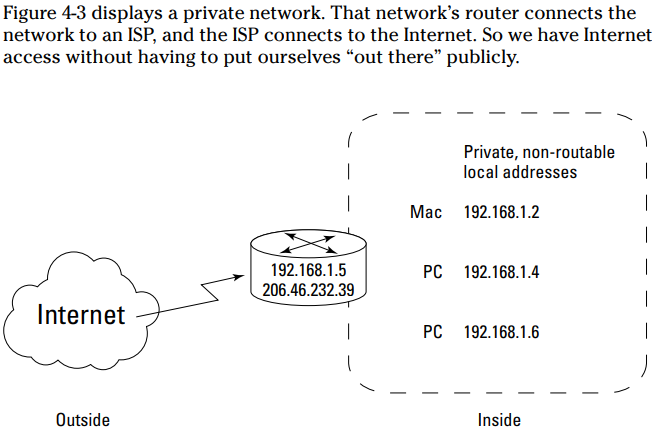
What does the DHCP do?
If your organization uses the Dynamic Host Configuration Protocol (DHCP), the DHCP server software automatically assigns an IP address to your host and other relevant network configuration parameters, allowing devices to communicate on a TCP/IP network without manual configuration.
How to find ip address in windows or linux?
Use the command line to execute commands like "ipconfig" in Windows or "ifconfig" or "ip addr" in Linux to display the current IP address and network configuration.
What is a router
A router is a computer that runs software that figures how a packet should be forwarded on the route to its destination. A router works at the internet layer of the TCP/IP layer cake, and connects to at least two networks. Most routers are in homes and offices and send Web, e-mail, and other Internet messages from the local area network (LAN) through your broadband connection (such as cable or DSL modem) to your ISP. Your ISP sends your routed messages out to the Internet. A combination cable modem/ router connects the home LAN to the ISP. Some of the fancier routers combine routing functions with a DHCP server and a firewall. Chapters 4 and 5 contain information about DH
What is subnet masks
When the network administrator borrows bits from the main network address’s host section, TCP/IP needs to know which bits of the host section are borrowed to be used as the network address. The administrator uses a subnet mask to borrow those host bits. A subnet mask is 32 bits that overlay an IP address. The mask sets all the bits for the network address to 1, and all the bits for the host address to 0. The mask tells the router, “Look only at the bits that lie under the 1s. Forget about any bits that lie under the 0s.” Because the router can skip the masked-out bits (that is, the zeroed-out bits), it can send packets on their way faster than if it had to look at the entire address. Before defining a subnet mask, the network administrator needs to figure out how many subnets to create and how many hosts will be in each subnet. This determines how many bits should be set to 1. The more bits used for the subnet mask, the fewer hosts can be on each subnet created. A subnet mask is a 32-bit number used to differentiate the network and host portions of an IP address. It helps routers in routing packets efficiently by indicating which bits correspond to the network and which correspond to the host.
How does subnet masks effect the ip address
The subnet mask is applied to the IP address in every message in order to separate the network number and the host number. For example, when your computer examines the address 192.9.200.15 and applies the default subnet mask of 255.255.255.0, it sees the network number 192.9.200 and the host number 15.
What is NAT
NAT (also called IP NAT) consists of two parts:
✓ A pass-through between your private intranet and the outside world (public Internet)
✓ A translator to and from private IP addresses to global IP addresses NAT allows multiple computers on one intranet to share one officially registered IP address.
Only one computer on the intranet must have a registered IP address to get to the Internet; the device that has the official IP address is called a NAT router. Requests from the hosts on your intranet go through the NAT router on their way to and from the Internet. Network Address Translation (NAT) is a technique that allows multiple devices on a local network to share a single public IP address. It translates the private IP addresses of devices on the local network to the public IP address for communication over the Internet.