CCNA Flash Cards
1/23
Earn XP
Description and Tags
CCNA
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
24 Terms
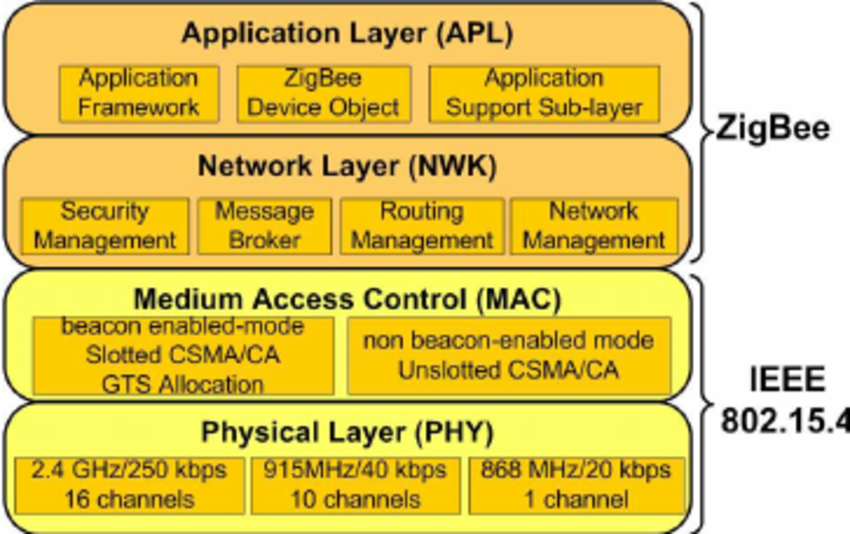
The IEEE 802.15.4 2.4GHz standard has how many channels to operate on?
IEEE 802.15.4 is a standard that defines the physical and MAC layers for low-rate wireless personal area networks (LR-WPANs). It is designed for low-power, low-data-rate, and short-range communication, making it ideal for IoT applications and sensor networks. The standard supports star and peer-to-peer topologies and operates in frequency bands such as 2.4 GHz, 868 MHz, and 915 MHz. It serves as the foundation for higher-level protocols like Zigbee, Thread, and 6LoWPAN.
Define CSMA/CD
Carrier sense multiple access with collision detection (CSMA/CD), is a network multiple access method in which carrier sensing is used, but nodes attempt to avoid collisions by transmitting only when the channel is sensed to be idle. When they do transmit, nodes transmit their packet data in its entirety.
Define CDMA
Code-division multiple access (CDMA) is a channel access method used by various radio communication technologies. CDMA is an example of multiple access, where several transmitters can send information simultaneously over a single communication channel. This allows several users to share a band of frequencies (see bandwidth). To permit this without undue interference between the users, CDMA employs spread spectrum technology and a special coding scheme (where each transmitter is assigned a code).[1][2]
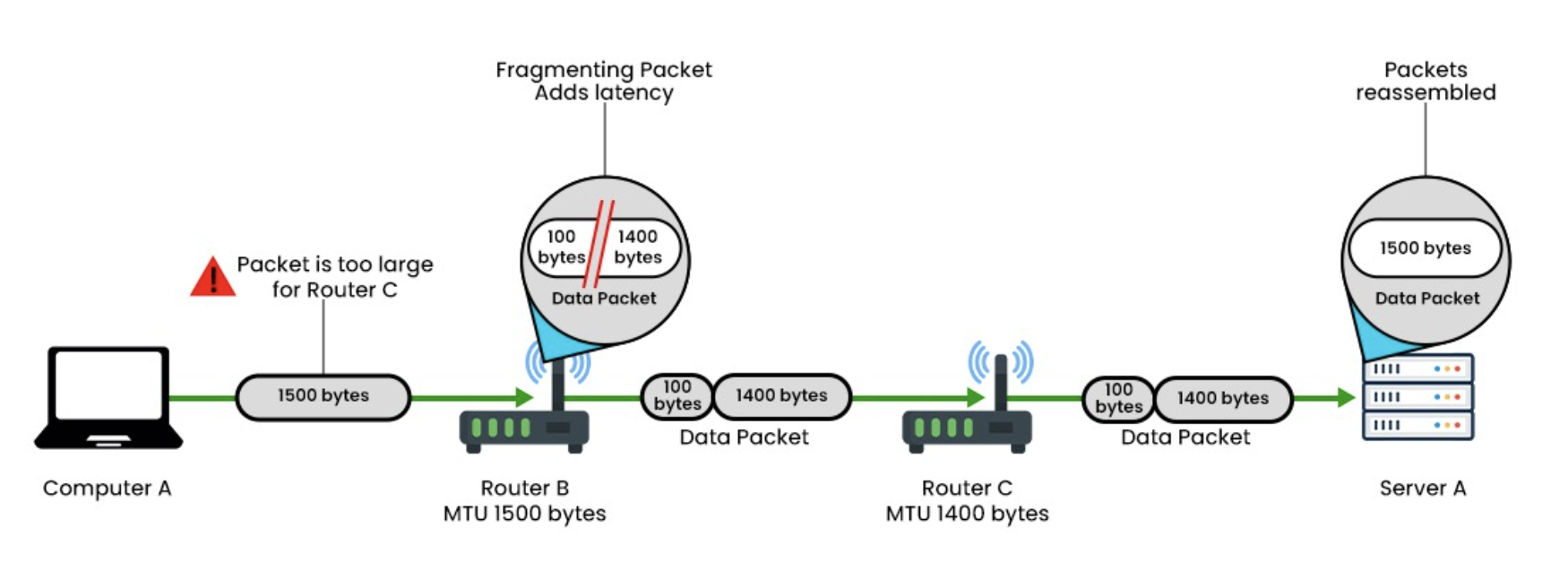
What is MTU?
Stands for Maximum Transfer Unit
MTU is a link layer parameter that is dependent on both the network layer protocol and the physical media. It contains both the TCP and IP headers.
Fragmentation is allowed by MTU.
MTU = MSS + 40 (IP header + TCP header)
Typically 1500 Bytes
MTU size does not rely on the value of MSS
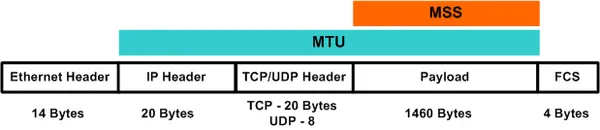
What is MSS?
Stands for Maximum Segment Size
A TCP option called MSS is negotiated as part of the handshake. The IP header and the TCP header are not included
MSS prohibits fragmentation.
MSS = MTU – 40 (IP header + TCP header)
1460 Bytes
MSS size totally depends on the value of the underlying MTU.
Why FHRP (First Hop Redundancy Protocols) routers need to send gratuitous ARP request
To change the MAC address tables of switches
Why DHCP snooping used to prevent rogue DHCP servers doesn’t prevent manually configured IP addresses.
Need IP snooping
Arp table only contains entries for devices in its own IP network. True or False
True
What do Vlans do?
VLANS are
Broadcast a domain that is partitioned and isolated at the data link layer (L2)
data link layer (L2) constructs, analogous to IP subnets (network layer, layer 3 constructs)
Provides L2 broadcast segmentation based on Layer 3 addresses
VLANS are configured on switch
End devices have no concept of vlans-Only IP network addresses
What is the Max number of Vlans? What is Vlans normal range?
4096 (12 bit)
Normal Range: (0 and 4095 reserved)
1-1005
Vlan 1 automatically created and cannot be deleted
1002 to 1005 reserved for legacy token Ring and FDDI
Extended-Range Ids (switch model dependent)
1006-4094
Service providers and larger enterprises
What’s the standard name that defines both:
How VLANs work at Layer 2
How VLAN tags are added to Ethernet frames for trunking
802.1Q is the IEEE standard
What traffic is usually associated with Vlan1?
All layer 2 control traffic between two switches (e.g. DTP, VTP, STP BPDUs, PAgP, LACP, CDP, etc)
List the types of Vlans usually in an enterprise network?
Default VLAN
VLAN 1 (by default on Cisco devices)
All ports are in this VLAN out-of-the-box
User/Data VLAN
Assigned to end-user devices like PCs and printers
Often grouped by department (e.g., HR, Finance)
Native VLAN
Used for untagged traffic on trunk ports
Should not carry user data for security reasons
Management VLAN
Used to access network devices (e.g., switches, APs)
Isolated from user/data traffic
Guest VLAN
Provides Internet-only access for guests
Segmented from the main internal network
Parking Lot or Garbage VLAN
Used for unused or unauthorized switch ports
Helps prevent rogue device connections
How many Bytes is the Vlan Tag? Is this Vlan ID in the Tag? Is it part of a packet or frame?
4Bytes
Yes
Frame
what’s an egress port?
The output port on a switch or router where a frame or packet exits the device.
List what to do when using Trunks:
Configure interfaces on both ends as a “trunk”
Interfaces on both ends end must agree on the “native vlan”
Disable DTP negotiation
For security: Limit only the VLANs you want to transmit to other switches
If egress port is a trunk port and a vlan frame 10 is coming, List the 3 steps that trunk port would :
Frame tagged with VLAN 10 before being forwarded
Vlan 10 Tagged removed by adjacent switch
Adjacent switch only consuls only consults MAC address table for ports on VLAN 10
What is DTP(Dynamic Trunking Protocol)?
It’s a Cisco proprietary protocol used between switch ports to automatically negotiate whether a link should be a trunk or access port.
What is the Native VLAN?
For devices that don’t support or need tagging: VERY RARE
All trunks must have a native VLAN
Native VLAN must be the same on both ends (both switches)
By default: VLAN 1 is untagged and is the native VLAN
Vlan 1 carries control traffic: STP, CDP, VTP, DTP, PAgP/LACP
Vlan 1 cannot be deleted
Choose:
Keep VLAN 1 as the Native VLAN but should only carry control traffic and not user or management traffic OR configure Native VLAN on its own LAN
What is Cisco VLAN Trunking Protocol?
Cisco VTP is a network protocol used to manage all configured VLANs across a switched network, enabling switches to advertise VLAN information to other switches in the same VTP domain via trunk links
Includes:
VLAN configuration consistency by managing the additions, deletions, and name changes of VLANs across networks from a VTP server
VTP pruning, which optimizes network bandwidth by preventing VLAN traffic without local recipients from being sent over trunks links
Describe Voice over IP (VoIP) phones
designed to replaced PBX office phones that had a separate network
Know there might not be a second Ethernet LAN port where the old phone used to be and that phones usually sit next to the computer, Cisco IP phones, were designed to Share a single Ethernet connection with the existing PC
Most Ip phones have 3 port switch inside of the IP phone:
One port connects to the switch
One port connects to the computer
One (internal port connects to the Phone
Note: Doesn’t send STP BPDU’s
STP should treat this as a “host” port (later -PortFast, BPDU Guard)
-Typically want our PC and IP phone to be on separate VLANs for Qos options:
PC: User VLAN(access port) on associated with its IP network address
IP Phone: on a special voice VLAN associated with its network address
Voice VLAN will give priority to this voice traffic in times of congestion, QOS
What is a sliding window protocol? Give 1-2 examples
The sliding window protocol allows the sender to transmit multiple packets while waiting for the acknowledge- ment for the first packet. The goal here is to keep the link occupied with transmitting packets while the sender waits on acknowledgements (ACKs) for the first packet.
We can summarize the sliding window protocol in 2 sentences. The sender sends out a set of W packets (called a window of packets) at the beginning, i.e., packets with sequence numbers 1 through W. It then releases a new packet in response to an ACK. This idea of releasing a new packet every time a packet is acked is called the packet conservation principle.4
Examples: Selective Repeat, Go-N-Back