ASA Checkpoint Exam
1/20
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
21 Terms
1. A network analyst wants to monitor the activity of all new interns. Which type of security testing would track when the interns sign on and sign off the network?
vulnerability scanning
password cracking
network scanning
integrity checker
integrity checker
2. What are three characteristics of SIEM? (Choose three.)
can be implemented as software or as a service
Microsoft port scanning tool designed for Windows
examines logs and events from systems and applications to detect security threats
consolidates duplicate event data to minimize the volume of gathered data
uses penetration testing to determine most network vulnerabilities
provides real-time reporting for short-term security event analysis
can be implemented as software or as a service
examines logs and events from systems and applications to detect security threats
consolidates duplicate event data to minimize the volume of gathered data
3. What testing tool is available for network administrators who need a GUI version of Nmap?
SuperScan
SIEM
Nessus
Zenmap
Zenmap
4. What is the goal of network penetration testing?
determining the feasibility and the potential consequences of a successful attack
detecting potential weaknesses in systems
detecting configuration changes on network systems
detecting weak passwords
determining the feasibility and the potential consequences of a successful attack
5. How does network scanning help assess operations security?
It can detect open TCP ports on network systems.
It can detect weak or blank passwords.
It can simulate attacks from malicious sources.
It can log abnormal activity.
It can detect open TCP ports on network systems.
6. What are three characteristics of the ASA routed mode? (Choose three.)
This mode is referred to as a “bump in the wire.”
In this mode, the ASA is invisible to an attacker.
The interfaces of the ASA separate Layer 3 networks and require different IP addresses in different subnets.
It is the traditional firewall deployment mode.
This mode does not support VPNs, QoS, or DHCP Relay.
NAT can be implemented between connected networks.
The interfaces of the ASA separate Layer 3 networks and require different IP addresses in different subnets.
It is the traditional firewall deployment mode.
NAT can be implemented between connected networks.
7. In which two instances will traffic be denied as it crosses the ASA 5505 device? (Choose two.)
traffic originating from the inside network going to the DMZ network
traffic originating from the inside network going to the outside network
traffic originating from the outside network going to the DMZ network
traffic originating from the DMZ network going to the inside network
traffic originating from the outside network going to the inside network
traffic originating from the DMZ network going to the inside network
traffic originating from the outside network going to the inside network
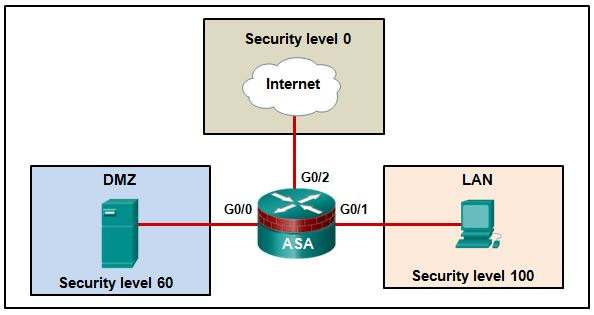
8. Refer to the exhibit. Based on the security levels of the interfaces on the ASA, what statement correctly describes the flow of traffic allowed on the interfaces?
Traffic that is sent from the LAN and the Internet to the DMZ is considered inbound.
Traffic that is sent from the DMZ and the Internet to the LAN is considered outbound.
Traffic that is sent from the LAN to the DMZ is considered inbound.
Traffic that is sent from the LAN to the DMZ is considered is considered inbound.
Traffic that is sent from the DMZ and the LAN to the Internet is considered outbound.
Traffic that is sent from the DMZ and the LAN to the Internet is considered outbound.
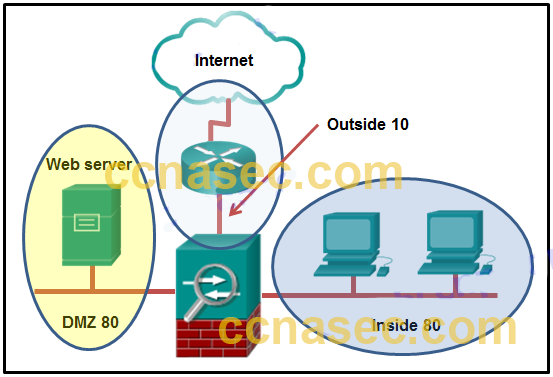
9. Refer to the exhibit. A network administrator is configuring the security level for the ASA. Which statement describes the default result if the administrator tries to assign the Inside interface with the same security level as the DMZ interface?
The ASA allows inbound traffic initiated on the Internet to the DMZ, but not to the Inside interface.
The ASA console will display an error message.
The ASA will not allow traffic in either direction between the Inside interface and the DMZ.
The ASA allows traffic from the Inside to the DMZ, but blocks traffic initiated on the DMZ to the Inside interface.
10. What can be configured as part of a network object?
interface type
IP address and mask
upper layer protocol
source and destination MAC address
IP address and mask
11. What is the function of a policy map configuration when an ASA firewall is being configured?
binding a service policy to an interface
binding class maps with actions
identifying interesting traffic
using ACLs to match traffic
binding class maps with actions
12. What is the purpose of configuring an IP address on an ASA device in transparent mode?
management
routing
NAT
VPN connectivity
management
13. Which license provides up to 50 IPsec VPN users on an ASA 5506-X device?
the most commonly pre-installed Base license
a purchased Security Plus upgrade license
a purchased Base license
a purchased AnyConnect Premium license
a purchased Security Plus upgrade license
14. What mechanism is used by an ASA device to allow inspected outbound traffic to return to the originating sender who is on an inside network?
access control lists
Network Address Translation
security zones
stateful packet inspection
stateful packet inspection
15. When configuring interfaces on an ASA, which two pieces of information must be included? (Choose two.)
group association
service level
FirePower version
security level
access list
name
security level
name
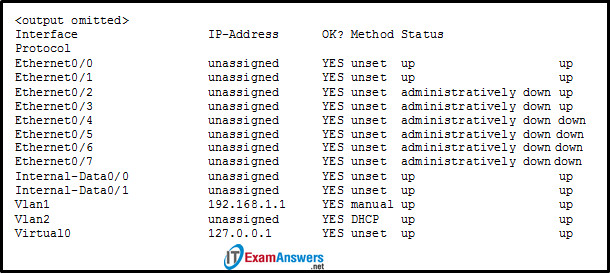
16. Refer to the exhibit. A network administrator is verifying the security configuration of an ASA. Which command produces the exhibited output?
show vlan
show ip interface brief
show interface ip brief
show switch vlan
show interface ip brief
17. What interface configuration command is used on an ASA to request an IP address from an upstream DSL device?
ip address ip-address netmask
ip address dhcp setroute
dhcpd address IP_address1 [ -IP_address2 ] if_name
ip address pppoe
ip address pppoe
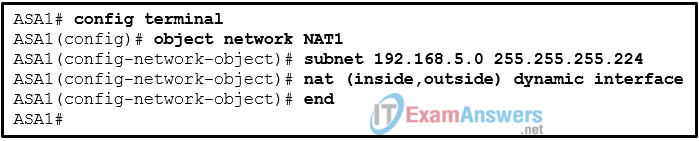
18. Refer to the exhibit. What kind of NAT is configured on the ASA device?
dynamic NAT
Twice NAT
dynamic PAT
static NAT
dynamic PAT
19. What is the purpose of the Tripwire network testing tool?
to perform vulnerability scanning
to provide information about vulnerabilities and aid in penetration testing and IDS signature development
to assess configuration against established policies, recommended best practices, and compliance standards
to detect unauthorized wired network access
to provide password auditing and recovery
to assess configuration against established policies, recommended best practices, and compliance standards
20. A network analyst is testing the security of the systems and networks of a corporation. What tool could be used to audit and recover passwords?
L0phtCrack
SuperScan
Nessus
Metasploit
L0phtCrack
21. In which two instances will traffic be denied as it crosses the ASA 5506-X device? (Choose two.)
traffic originating from the inside network going to the outside network
traffic originating from the inside network going to the DMZ network
traffic originating from the outside network going to the inside network
traffic originating from the outside network going to the DMZ network
traffic originating from the DMZ network going to the inside network
traffic originating from the outside network going to the inside network
traffic originating from the DMZ network going to the inside network