ITS Certiport Cybersecurity Certification Exam Study Guide
1/470
Earn XP
Description and Tags
ape together strong
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
471 Terms
Describe Phishing
Sending an email message or displaying a web announcement that falsely claims to be from a legitimate enterprise. One of the most common forms of social engineering.
Describe Spear Phishing
regular phishing sends millions of generic messages, but spear phishing is customized for its recipients, including names and personal information to try and make it seem more legit.
Describe Whaling
going after the “big fish,” whaling is a type of spear phishing where you target wealthy or important individuals, like senior executives or CEOs
Describe Vishing
Voice phishing, attackers call victims who play a recorded message pretending to be someone else or an institution, like a bank, to try and trick the victim into giving up private information.
example: you get a call from your bank stating that your credit card has experienced fraudulent activity and are instructed to call a different number, which then asks you to enter your credit card number, bank number, SSN, and other information into the keypad.
Describe Smishing
A variation on vishing that uses SMS (text messages) and callback recorded phone messages.
Describe Spam
unsolicited email that is sent to a large number of recipients
Describe Spim
spam delivered through instant messaging (IM) instead of email.
Describe a watering hole attack
an attack directed towards a smaller group of specific individuals, like major executives at a manufacturing company.
These executives tend to visit a common website. An attacker can try and use this website to infect them with malware.
Your company's Accounts Payable department reports that an invoice was marked as paid, but the vendor has shown proof they never received any of the $783,296 payment. Accounts Payable confirms that the amount was deducted from the company's accounts, but the recipient account number does not match the vendor's. After an investigation, you discover that the invoice was paid by the Chief Financial Officer. He says he paid the invoice after receiving an after-hours, past-due invoice from the vendor claiming that they would be filing a civil action in court the next morning. Rather than wait for Accounts Payable to come in the next day and verify the invoice date, the CFO immediately paid the full amount.
What type of social engineering attack was your company most likely a part of?
a) Pharming
b) Credential Harvesting
c) Phishing
d) Whaling
Whaling
What does a $IEM do
help security teams manage and respond to security warnings and alarms
What does a $OAR do
gathers data and analytics to automate incident response.
ex: when ransomware hits, shut the power off to the servers
TIP: Soar does More!
What are the features of a SIEM
TIP: ACATEL
Aggregation, Correlation, Automated alerting and triggers, Time synchronization, Event duplication, Logs
ACATEL - All Cars Aren’t Truly E-Lectric
What is Aggregation in a SIEM?
combines data from multiple data sources—such as network security devices, servers, and software applications—to build a comprehensive picture of attacks.
What is Correlation in a SIEM?
searches the data acquired through SIEM aggregation and looks for common characteristics, such as multiple attacks coming from a specific source.
What is Automated alerting and triggers in a SIEM?
can inform security personnel of critical issues that need immediate attention.
A sample trigger may be Alert when a firewall, router, or switch indicates 40 or more drop/reject packet events from the same IP source address within 60 seconds.
What is Time synchronization in a SIEM?
Because alerts occur over a wide spectrum of time, SIEM time synchronization can show the order of the events.
What is Event duplication in a SIEM?
When the same event is detected by multiple devices, each generates an alert. The SIEM event duplication feature can help filter the multiple alerts into a single alarm.
What is the point of having logs in a SIEM?
SIEM logs or records of events can be retained for future analysis and to show that the enterprise has been in compliance with regulations.
Which feature of a SIEM tool can help filter multiple alerts detected by different devices for the same event into a single alarm?
Event Duplication
What is sentient analysis?
allows SIEMs to track postings threat actors make in discussion forums with other attackers to better determine their behavior and mindsets.
Remember: SOAR does NOT use sentient analysis
Seo-jun is a bug bounty hunter. He was hired by an industrial organization to damage the network's security defenses as much as possible. Seo-jun gained initial access to a system in the network by sending a spear-phishing email into the network that installed a virus. What sequence of actions should he perform to achieve repeated and long-term access to multiple systems in the network with a highly privileged account?
a) Perform backdoor installation, then lateral movement, and then perform privilege escalation
b) Perform privilege escalation, then lateral movement, and then perform backdoor installation
c) Perform backdoor installation, then privilege escalation, and then lateral movement
d) Perform lateral movement, then credential dumping, and then perform backdoor installation
Privilege escalation → lateral movement → backdoor installation
What is an attack on a NoSQL database compromised by data manipulation when the input is not sanitized by the application?
XML injection
Smith installed new meeting-scheduling software that automatically sends emails and reminders to the recipient's computer. Smith noticed that after installation, the software was also tracking other applications he accessed on his computer. What is this attack called?
a) Backdoor
b) Trojan
c) Spyware
d) PUP
Trojan
What is KRI?
Key Risk Indicator
Which of the following is true for KRI?
a. A KRI exceeding its normal bounds is always an indicator of compromise.
b. A KRI exceeding its normal bounds is not always an indicator of compromise.
c. A KRI exceeding its normal bounds is never an indicator of compromise.
d. A KRI never exceeds its normal bounds.
A KRI exceeding its normal bounds is not always an indicator of compromise.
What does AIS stand for?
Automated Indicator Sharing
Your organization is planning to be a part of the CISCP program as a partner. As an information security expert in your company, you are approached by your CEO, who wants to understand how the speed limit of public information centers like CISCP is handled.
How should you explain how this speed limit is handled to him?
a. CISCP implements PPTP, which takes care of the speed limit issue of public information centers.
b. CISCP currently implements threat maps to address the issue of public information center speed limits.
c. CISCP implements AIS, which resolves the speed limit issue of public information centers.
d. CISCP implements HTTP protocol in communications to address the speed limit issue of public information centers.
c) CISCP implements AIS, which resolves the speed limit issue of public information centers.
Remember: AIS stands for Automated Indicator Sharing. When you see CISCP, think AIS
John needs to identify public key systems that generate different, random public keys for each session and, even if a key gets stolen, should not reveal more than one message.
Which public key system should John suggest?
a) Diffie-Hellman
b) Diffie-Hellman Ephemeral
c) Elliptic Curve Diffie-Hellman
d) Perfect Forward Secrecy
d) Perfect Forward Secrecy
Diffie-Hellman (DH)
Generate a mutual key for 2-parties
EXAMPLE: Alice and Bob agree on a large prime number and related integer. Those two numbers can be made public, yet Alice and Bob, through mathematical computations and exchanges of intermediate values, can separately create the same key.
Diffie-Hellman Ephemeral (DHE)
Generate a TEMPORARY mutual key for 2 parties
In a DHE scenario, Alice and Bob would agree on a set of parameters, each generate a private number, and then exchange information derived from their private numbers with each other. This allows them to compute the same shared secret key without ever directly exchanging their private numbers.
What is Elliptic Curve Cryptography (ECC)?
ECC uses the mathematics of elliptic curves to encrypt key pairs for public key encryption. In the elliptic curve, certain points are plotted and, based on these points, keys are generated mathematically.
What two cryptography algorithms use ECC?
DSA (Digital Signature Algorithm) and Elliptic Curve Diffie-Hellman (ECDH)
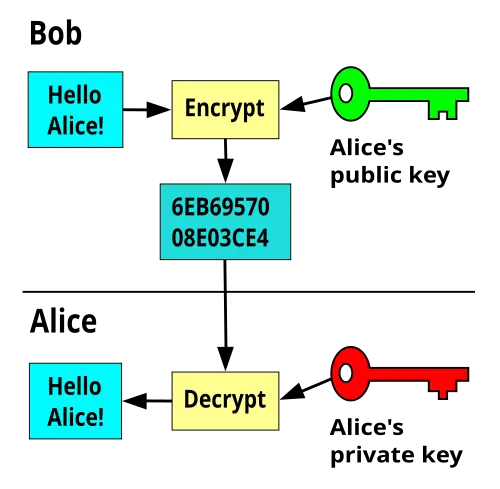
Elliptic Curve Diffie-Hellman (ECDH)
Stronger security w/ smaller key size
ECDH uses elliptic curve cryptography (ECC) instead of prime numbers in its computation
Do you exchange keys during a Diffie-Hellman key exchange?
No.
In the Diffie-Hellman key exchange, you don't directly exchange keys. Instead, you exchange public values (derived from private keys) that allow both parties to compute a shared secret key.
What is Perfect Forward Secrecy?
a cryptography method with NO FIXED ALGORITHM that randomly generates encryption keys and uses asymmetric encryption. It ensures that once keys are used, they can’t be reused.
If one message is sent, it’s encrypted with random keys. Every time a call is initiated, its encrypted with random keys.
What is an ACL
Access Control List - contains rules that administer the availability of digital assets by granting or denying access to them.
Networking ACLs filter access to a network and are often found on routers.
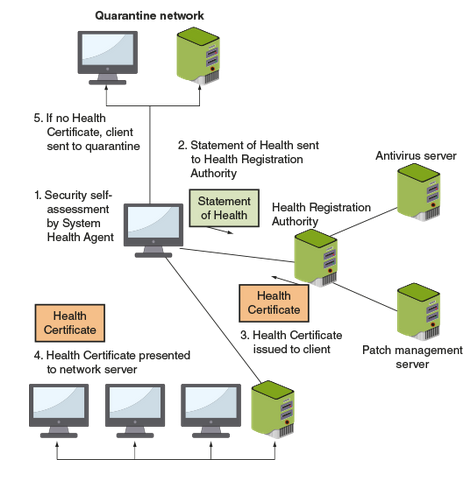
What is an NAC? What does it do?
Network Access Control - designed to prevent computers with sub optimal security from potentially infecting other computers through the network.
Describe a VPN (Virtual Private Network)
Virtual Private Tunnel - a tunnel created to encrypt data going from the main office to remote office and provides a dedicated secure tunnel between two points over the internet
Describe the difference between a remote access VPN and a site-to-site VPN
remote access VPNs are a user-to-LAN connection for remote users.
site-to-site VPN is a connection in which multiple sites can connect to other sites over the Internet.
What is an Always-On VPN?
A VPN that allows the user to stay connected at all times instead of connecting and disconnecting from it.
Full Tunnel VPN vs. Split Tunnel VPN
A Full Tunnel VPN has all traffic sent to the VPN concentrator and protects it.
A Split Tunnel VPN only sends SOME traffic to the VPN concentrator and is protected, while the rest of the traffic directly accesses the Internet.
What are the benefits of using Split Tunnel VPN
it can help preserve bandwidth and reduce the load on the VPN concentrator.
What is the greatest flaw in Layer 2 Tunneling Protocol (L2TP)
does not offer encryption or protection, unlike TLS, but it can be paired with IPsec to be safer.
In an interview, you were asked to analyze the following statements regarding secure network designs and choose the correct one. Which of the following should you choose?
a. An ACL is a security technology that enables authorized users to use an unsecured public network.
b. A VPN contains rules that administer the availability of digital assets by granting or denying access to them.
c. A SMTP is a VPN protocol that does not offer any encryption or protection, so it is usually paired with IPsec.
d. A NAC examines an endpoint before it can connect to the network, denying access to any device that does not meet specific criteria
d. A NAC examines an endpoint before it can connect to the network, denying access to any device that doesn’t meet specific criteria.
What is the size range for bits in RSA keys?
1024 - 15360
(1024, 2048, 3072, 7680, 15360)
What is the size range for bits in ECC keys?
160 - 521
(160, 224, 256, 384, 521)
Describe the Public classification level
the least sensitive data that would only cause a small amount of harm if disclosed
example: # of employees
Describe the Proprietary classification level
data disclosed outside the company on a limited basis to trusted third parties. an unexpected disclosure could reduce a company’s competitive advantage.
example: nontechnical specifications for a new product
-
proprietary = company losing advantage
Describe the Private classification level
data might not harm the company itself, but could hurt others
example: human resources data of employees (ssn, addresses, numbers, etc)
Describe the Confidential classification level
data used internally within the company. public disclosure would cause significant harm to the organization.
example: news of an impending merger or acquisition
Describe the Sensitive classification level
data that could cause catastrophic
harm to the company if disclosed
example: technical specifications for a new product that a rival company could steal
What is a data governance policy?
defines who is responsible for the data, how it can be accessed, how it should be used, and how its integrity is maintained
What is a data retention policy?
specifies how long data should be retained after its served its purpose
Describe the managerial control category
controls that use administrative methods like creating new policies and procedures
example: acceptable use policy that specifies users should not visit malicious websites
Describe the technical control category
controls implemented and executed using some type of technical system, like operating system controls, firewalls, and anti-virus.
example: Unified Threat Management (UTM) device that performs packet filtering, antiphishing, and web filtering.
Describe the operational control category
Controls implemented and executed by people, like security guards or monthly lunch-and-learns/other awareness programs.
example: conducting workshops to help train users to identify and delete phishing messages
You conducted workshops to help train users to identify different risks. What control category does this fall within?
a) operational
b) managerial
c) technical
d) deterrent
operational
You work in an enterprise that provides various services to other enterprises. After successfully negotiating terms with a new client, you were asked to issue an agreement that specifies the responsibilities of each party and guarantee of services. Which of the following agreements should you issue?
a. Nondisclosure agreement
b. Business partnership agreement
c. Service-level agreement
d. Memorandum of understanding
Service-level agreement
Describe deterrent controls
attempts to discourage security violations before they occur but does not directly prevent access
example: a splash screen that displays a warning about unauthorized access and consequences (technical), threat of demotion(managerial), front reception desk (operational), posted warning signs (physical)
Describe preventative controls
works to prevent the thread from coming in contact with the vulnerability
example: a firewall rule (technical), on-boarding policy (managerial), a guard shack checking for identification (operational), door lock (physical)
Describe physical controls
implements security in a defined structure or location
Describe Detective controls
designed to identify and log any threat that has reached the system
example: collect and review system logs (technical), review login reports (managerial), regularly patrol the property to find infiltration signs (operational), enable motion detectors (physical).
Describe compensating controls
provides an alternative to normal controls that for some reason cannot be used
example: firewall blocks a specific application instead of patching the app (technical), implementing a separation of duties (managerial), requiring simultaneous guard duties (operational), generator used after power outage (physical)
Describe corrective controls
intended to mitigate or lessen the damage caused by an incident and continue operating with minimal downtime.
example: restoring from backups can mitigate ransomware infection (technical), create policies for reporting security issues (managerial), contact law enforcement to manage criminal activity (operational), use a fire extinguisher (physical)
Describe directive control types
a relatively weak security control, you are directing to do something more secure instead of less secure
example: store all sensitive files in a protected folder, create compliance policies and procedures, training users on proper security policy, post a sign for “authorized personnel only”
Service-Level Agreement (SLA)
minimum terms of services provided (uptime, response time agreement, etc.) that is commonly used between customers and service providers.
-
example: a contract with an ISP that says no more than four hours of unscheduled downtime, technicians will be dispatched if needed, and might require customers to keep spare equipment on site.
Memorandum of Understanding (MOU)
Usually states common goals, but not much more. No signed contract, not legally enforceable. Both sides agree to the contents of a memorandum and is usually in the form of a letter of intent.
Business Partnership Agreement (BPA)
A formal agreement between two or more parties outlining the terms of their business relationship, including roles, responsibilities, and profit sharing.
Nondisclosure Agreement (NDA)
a legal contract between parties that specifies how confidential material will be shared between the parties but restricted to others.
An NDA creates a confidential relationship between the parties to protect any type of confidential and proprietary information.
What business agreement protects any type of confidential or proprietary information?
Nondisclosure Agreement (NDA)
Measurement System Analysis (MSA)
uses scientific tools to determine the amount of variation that is added to a process by a measurement system,
example: a third party who manufactures a product for an organization would need to demonstrate that how it measures the size, weight, dimensions, and other properties of the product is both valid and does not contribute to any variation of the product.
A threat actor employed by the victimized organization who purchases and deploys their own devices in the enterprise network is referred to as which of the following?
a. Cyberterrorist
b. Competitor
c. Broker
d. Shadow IT
d. Shadow IT
Describe BYOD
Bring Your Own Device - employees use their personal devices for business purposed and have full responsibility for choosing and supporting said device
Describe COPE
Corporate Owned, Personally Enabled - employees choose from a selection of company approved devices
Describe CYOD
Choose Your Own Device - employees choose from a limited selection of approved devices, but pay the upfront cost of the device while the business owns the contract.
Describe VDI
Virtual Desktop Infrastructure - stores sensitive applications and data on a remote server accessed through a smartphone
Describe Corporate Owned
device is purchased and owned by the enterprise. Employees use the phone only for company-related business.
In which of the following mobile device deployment models are employees supplied a chosen device paid for by their company for both professional and personal use?
a. BYOD
b. COPE
c. CYOD
d. VDI
b. COPE (Company Owned, Personally Enabled)
Ramesh is very active on social media. He visits a lot of pages and views a lot of photos. He also uploads most of his photos to social media sites such as Facebook and Instagram. By doing this, he increases the risk of becoming a victim of which of the following?
a. Firmware over-the-air
b. GPS tagging
c. Unauthorized recording
d. Tethering
b. GPS tagging
Metadata stored on images can reveal locations, as well as geographical indicators that can be found within images.
Which of the following processes can conceal a file, message, image, or a video within another file, message, image, or a video?
a. Cryptography
b. Steganography
c. Encryption
d. Decryption
b. Steganography
Steganography involves audio, video, or images, unlike cryptography (which is text based)
John needs to identify public key systems that generate different, random public keys for each session and, even if a key gets stolen, should not reveal more than one message.
Which public key system should John suggest?
a. Diffie-Hellman
b. Diffie-Hellman Ephemeral
c. Elliptic Curve Duffie-Hellman
d. Perfect forward secrecy
d. Perfect Forward Secrecy
Using perfect forward secrecy, you can’t reveal the contents of more than one message. This system ensures that session keys are not compromised by the theft of a private key, maintaining the confidentiality of multiple messages.
Which of the following contains the set of rules that govern the operation of a PKI?
a. Electronic code book (ECB)
b. Certificate policy (CP)
c. Signature resource guide (SRG)
d. Certificate practice statement (CPS)
b. Certificate policy (CP)
CP is a set of published rules that govern the operation of a PKI, providing recommended baseline security requirements for the use and operation of CA
ABC Manufacturing Company is located in Hiroshima, Japan. Being prone to earthquakes, the company decided to implement a backup of their data on a Singapore server. The IT administrator contacted you to identify the optimal command-line interface protocol for this backup. Which protocol should you advise?
a. Secure sockets layer
b. Transport layer security
c. Secure shell
d. Hypertext transport protocol secure
c. Secure Shell
SSH is a protocol for secure remote login and other secure network services over an insecure network. It enables secure data transfer and management of servers.
Describe DNS Poisoning / Spoofing
manipulates DNS settings, redirecting users to malicious sites instead of the intended domain by modifying the local lookup table on a device to point to a different domain.
This misdirects users to malicious sites without their knowledge. For instance, an attacker may replace a legitimate website’s IP address with that of a phishing site.
Describe DNS Hijacking
a higher level attack that infects an external DNS server with IP addresses pointing to malicious sites.
often involves altering the configuration of a DNS server itself to redirect users to malicious sites. This can mean changing the server’s settings to point certain user requests to harmful or misleading destinations, such as sites designed to steal personal information.
What is the difference between DNS poisoning and DNS hijacking
DNS poisoning compromises the integrity of the DNS data where DNS hijacking alters the control of the DNS service itself
You are assigned to hunt for traces of a dangerous DNS attack in a network. You need to capture DNS attacks that can compromise DNS replies to all the devices in the network. What type of DNS attack should you look for?
a. DNS amplification attack
b. DNS poisoning
c. DNS hijacking
d. DNS botnet attack
c. DNS hijacking
What is a firewall?
a. A firewall is an ultimate security device that blocks everything malicious from entering a network.
b. A firewall is a network security system that monitors and controls all incoming and outgoing traffic.
c. A firewall is a network security system that monitors only incoming network traffic.
d. A firewall provides physical security for all enterprise devices connected to a network.
b. A firewall is a network security system that monitors and controls all incoming and outgoing traffic.
What are the four types of clouds?
Public, Private, Community, and Hybrid
Describe a Public Cloud
Available to everyone over the Internet
Describe a Private Cloud
Your own virtualized local data center
Describe a Hybrid Cloud
More than one public or private cloud, adding to complexity.
What is SaaS
Software as a Service
Example: Zoom, Dropbox, Adobe
Designed for End Users
What is PaaS
Platform as a Service
Example: Heroku, Openshift, Google App Engine
Designed for Software Developers
What is IaaS
Infrastructure as a Service
Example: AWS, VMware, Azure
Designed for network architects and IT administrators
Your enterprise ran out of computing resources due to the increasingly high rate of stored data. You are asked to choose a cloud model in which your enterprise can have the most control over the hardware. Which model should you choose?
a. Infrastructure as a service
b. Platform as a service
c. Software as a service
d. Security as a service
a. Infrastructure as a Service (IaaS)
is the best choice because it provides complete control over virtualized hardware resources.
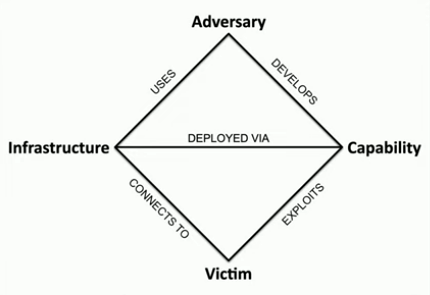
What are the four corners of the Diamond Model of Intrusion Analysis
TIP: CAIV (like “cave”)
Capability, Adversary, Infrastructure, Victim
TIP: Think of CAIV (like “cave”) and picture your adversary hiding in a cave - their capability is hidden, infrastructure is built, and the victim is outside.
Which controls are looked at as technical controls? (You can select multiple)
A) IDs
B) Training manual
C) Firewall
D) AUP
a) IDs and c) Firewall
Controls that enforce security are seen as technical controls. The other options are policy documents, which are more administrative controls
Which type of injection attack uses keywords such as select and update to manipulate data through a web form?
A) LDAP injection
B) SQL injection
C) XML injection
D) HTML injection
B) SQL injection
An SQL injection is an injection attack that uses keywords such as select and update to manipulate data through a web form
What is a DLL Injection?
DLL injection is a technique used to run external code within the address space of another process by manipulating the target process to load a dynamic link library (DLL).