Chapter 14: Virtual Machines
1/47
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
48 Terms
Virtualization technology allows a PC or server to simultaneously run more than one….
OS, or more than one session of the same OS
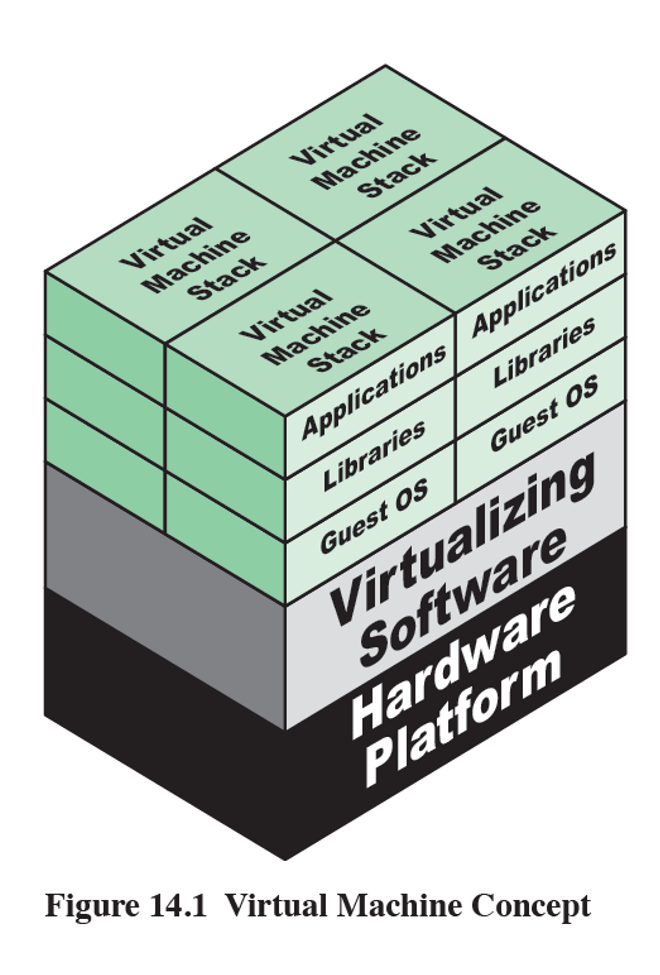
Virtualization
Virtualization is technology that you can use to create virtual representations of servers, storage, networks, and other physical machines
Why are VMs preferable than servers?
servers take a lot of space + money
VMs save more money
What is a hypervisor?
the software for virtualization
AKA virtual machine monitor or VMM
What does a hypervisor do?
it acts as a layer between the hardware and the VMs to act as a resource broker
- allows multiple VMs to safely coexist on a single physical host
Each VM has its own what?
OS, which may be the same or different from the host OS
What is the consolidation ratio?
number of VMs that can run on a host
Reasons for virtualization
Legacy hardware
run old application on modern hardware
Rapid deployment:
physical server may take weeks, VM may take minutes
Versatility:
run many kinds of applications on one server
Consolidation:
replace many physical servers with one
Aggregating:
combine multiple resources into one virtual resource, such as storage
Dynamics:
new VM can easily be allocated, such as for load-balancing
Ease of management:
easy to deploy new VM for testing software
Increased availability:
VMs on a failed host can quickly be restarted on a new host
What does virtualization abstract?
physical hardware from the VM it supports
How is a VM configured?
with some number of processors, some amount of RAM, storage resources, and network connectivity
How are hypervisors limited?
in only the resources it has been configured to see
What does the hypervisor do with I/O?
Privileged instructions?
facilitates I/O from the VM to the host and back again to the correct VM
privileged instructions must be caught and handled by the hypervisor, creating some performance lost
How is a VM instance defined?
as files
VM files
config files defines number of virtual processors, amount of memory, I/O device access, and network connectivity
- storage VM sees may be files in physical file system
Hypervisor Functions
Execution management of VMs:
scheduling, memory management, context switching, etc.
Devices emulation and access control:
emulating devices requested by VMs, mediating access to host devices.
Execution of privileged operations:
rather than run them on host hardware.
Management of VMs (lifecycle management):
configuration of VMs and controlling VM states (e.g. Start, Pause, Stop).
Administration:
hypervisor platform and software administration activities.
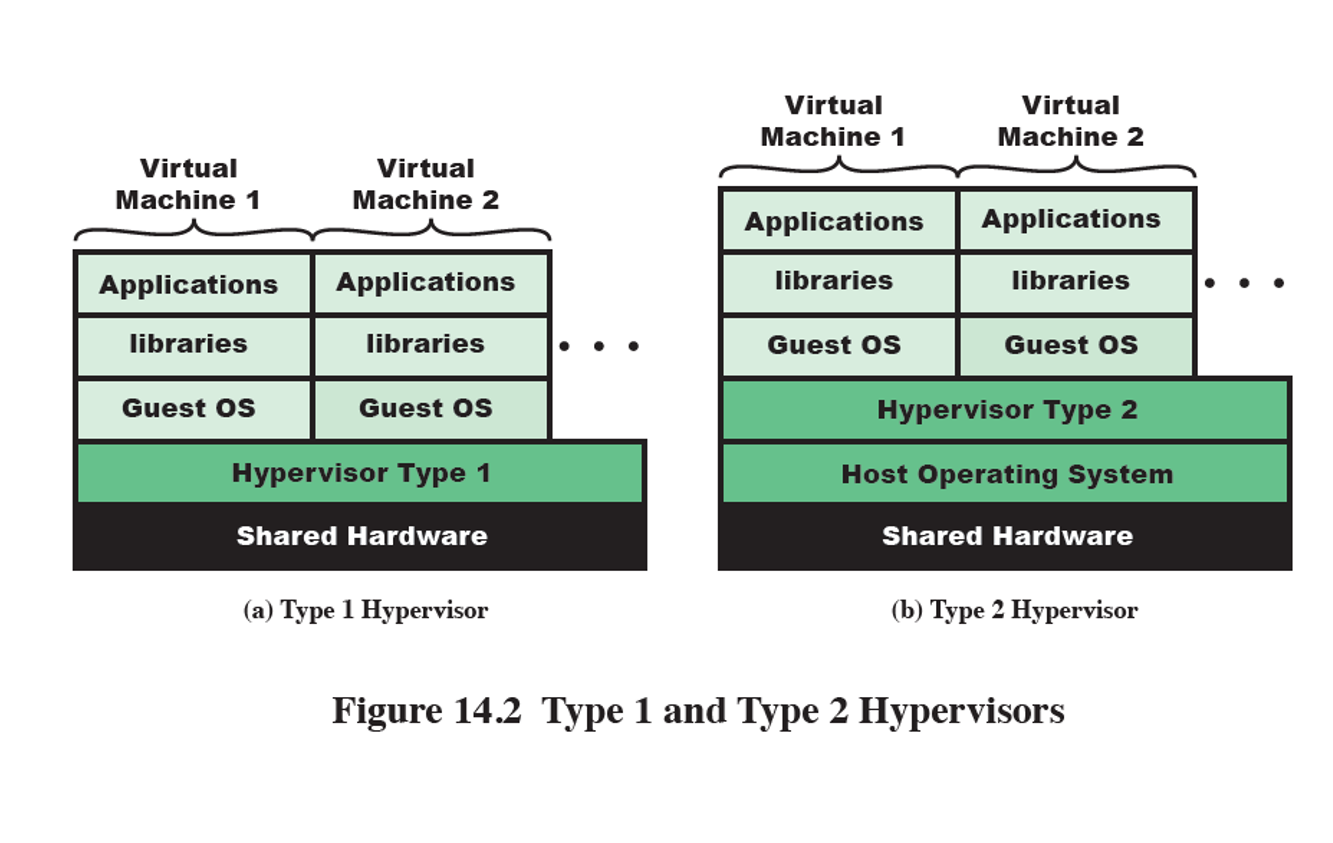
Types of Hypervisors
Type 1 (Baremetal)
Type 2 (Hosted)
Type 1
hypervisor runs directly on host hardware much like an OS would run
directly controls host resources
faster
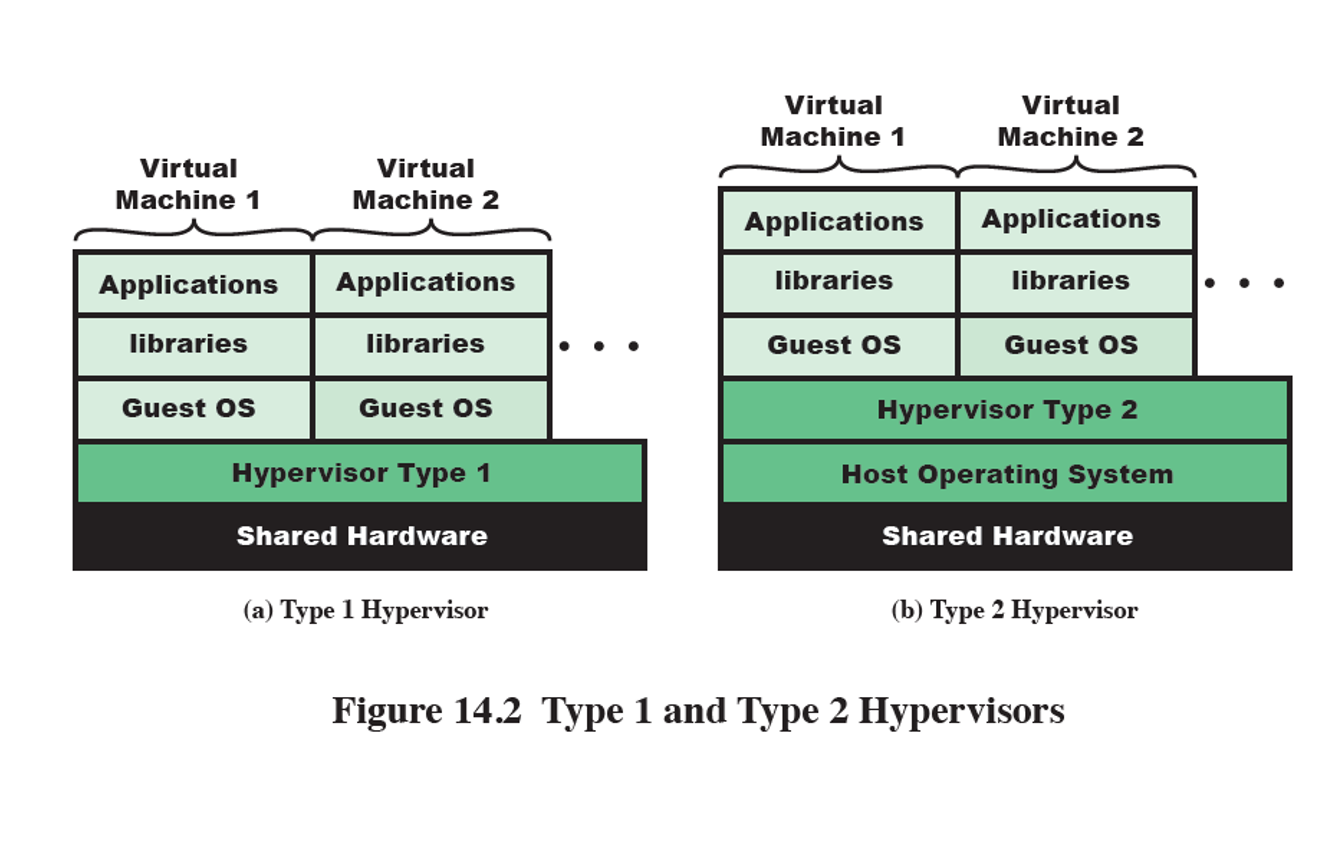
Type 2
Hypervisor runs on host’s OS
relies on host OS for hardware interactions
less secure
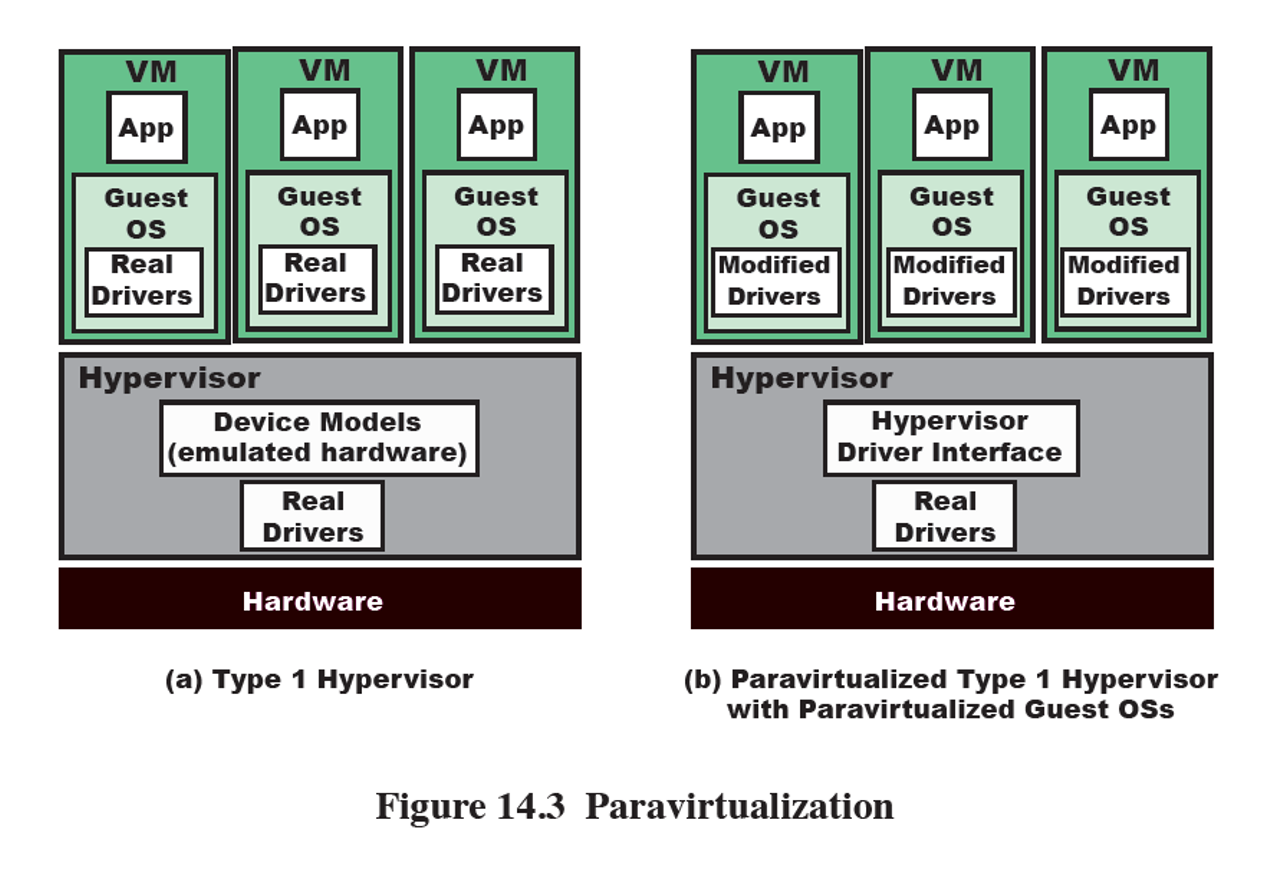
paravirtualization
software-assisted virtualization technique
OS is modified so that calls to the hardware are replaced with calls to the hypervisor
Faster with less overhead
Hardware assisted virtualization
through virtualization extensions taht the hypervisor to use
- even extra instructions for the hypervisor instead of performing these functions in code (Then OS doesn’t need to be modified)
What is a virtual appliance?
consists of applications and an operating system distributed as a virtual machine image
independent of hypervisor or processor architecture
can run on either type 1 or type 2 hypervisor
way easier than installing an OS
Security Virtual Appliance
monitors and protects other VMs
can monitor the state of the VM including registers, memory, and I/O devices as well as network traffic through API
Another approach to virtualization is….
container virtualization
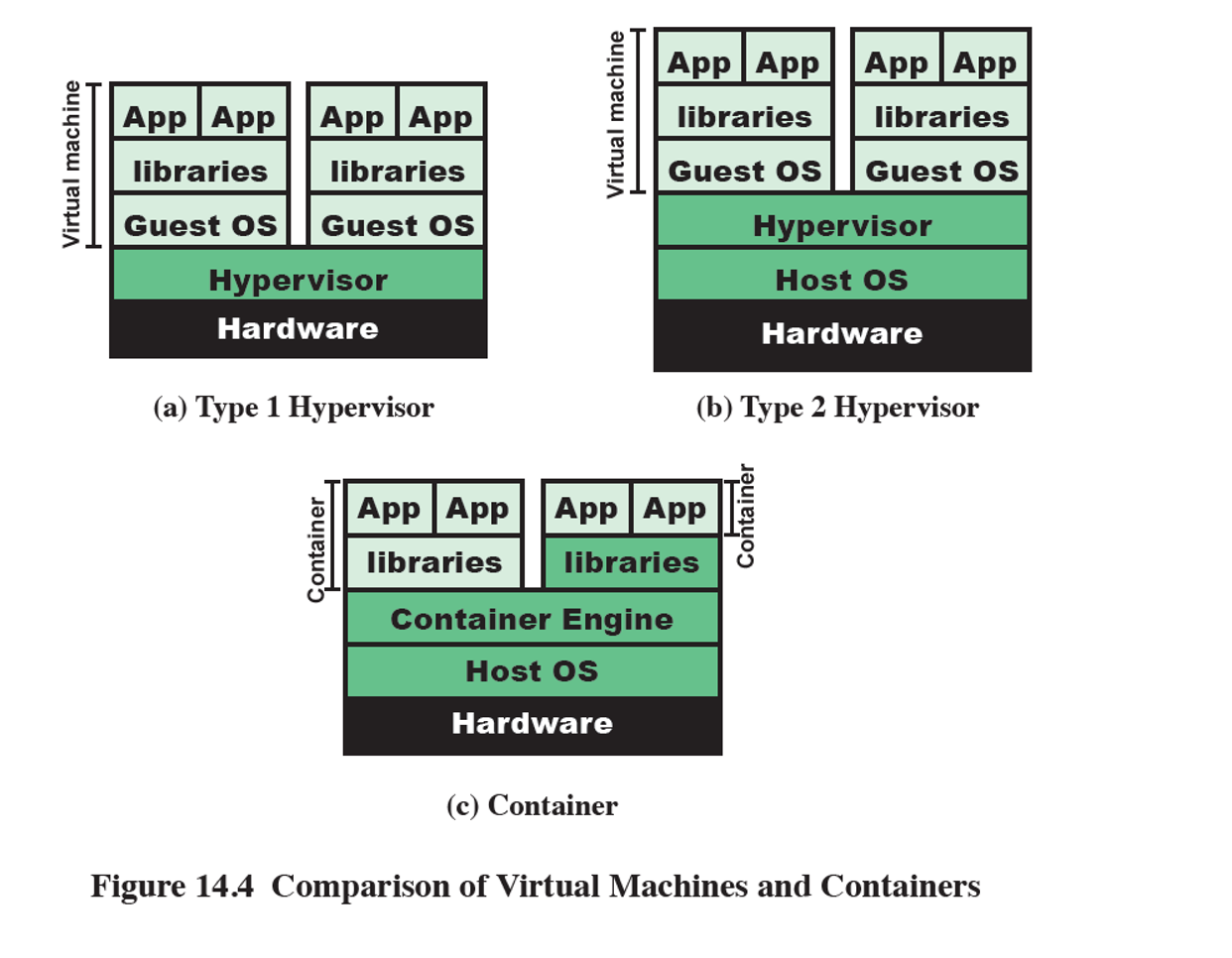
Container virtualization
Software running on top of the host OS kernel provides an isolated execution environment.
Unlike hypervisor VMs, containers do not aim to emulate physical servers.
Instead, all containerized applications on a host share a common OS kernel. (container does not have OS of its own)
This eliminates the need for each VM to run its own OS and greatly reduces overhead.
process containers
AKA control groups
- allow for multiple process hierarchies in a single OS
containerization of the user environment
normally all processes descendants of init process forming a single process hierarchy
hierarchies is associated wit hsystem resources at config time
What do control groups provide?
Resource limiting
limit how much memory is usable
Prioritization
some groups can get a larger share of CPU or disk I/O
Accounting
can be used for billings purposes
Control
groups of processes can be frozen or stopped and restarted
How are containers set up?
Container engine sets up each container as an isolated instance by requesting resoruces from the OS
Each container application then directly uses the resources of the host OS
Container Lifecycle
Setup
enabling the Linux kernel containers
installation of tools and utilities to create the container environment
Configuration
specify IP addresses
root file system
allowed devices
Management
startup
shutdown
migration
•In a VM environment, a process executes inside a guest virtual machine.
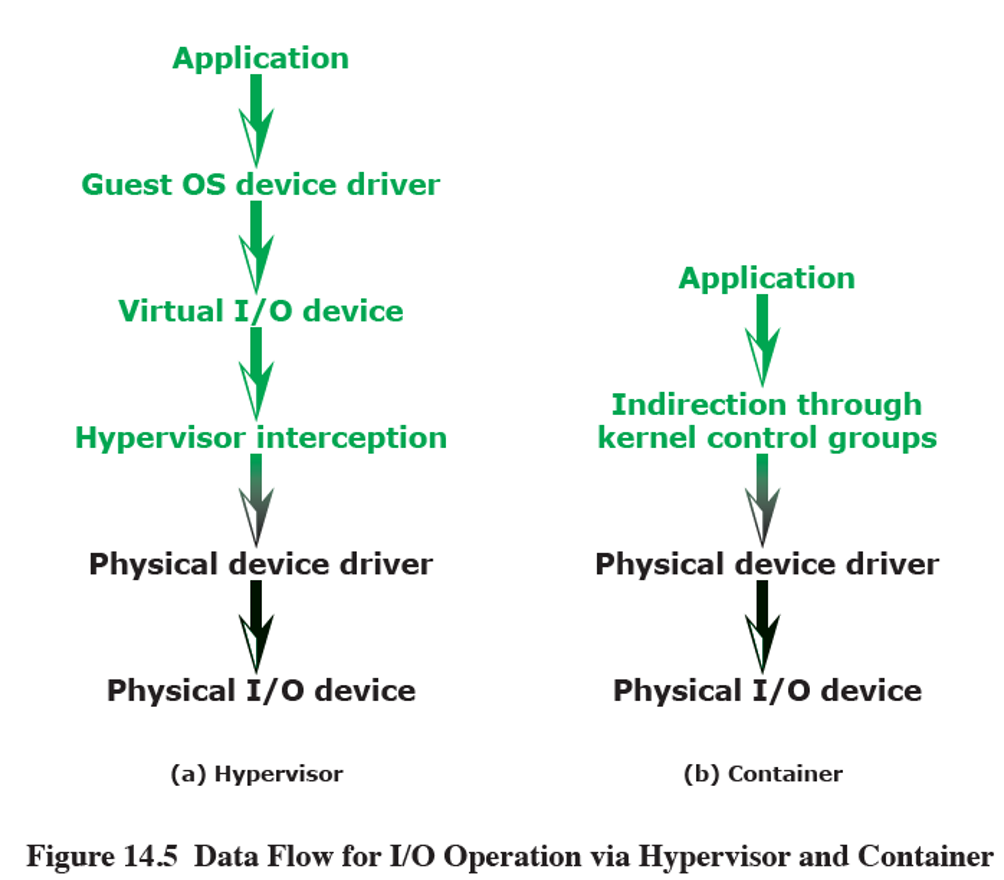
How are I/O requests handled in containers?
I/O request is sent to guest OS to an emulated device the guest OS sees
hypervisor sends it through to the host OS which sends it to the physical device
I/O request in a container environment is routed through kernel control group indirection to the physical device
Advantages and disadvantages of containers
Pros:
by sharing OS kernel, a system may run many containers compared to the limited number of VMs and guest OSs of a hypervisor environment
Application performance is close to native system performance
Cons:
container applications only portable acorss systems with the same OS kernel and virtualization support features
an app for a different OS than the host is not supported
may be less secure if there are vulnerabilities in the host OS
Container + files?
each container sees its own isolated file system with symbolically links into each container from OS files and common applications (saves space with only locally created files actually existing in container’s file system)
Microservices
architectural style in which an application is decomposed into loosely coupled self-contained services.
smaller deployable unit than the whole application, making it easier and quicker to push out updates or add features. This helps to support a continuous delivery practice.
each service is broken out as an individual part
containers are a natural fit for microservices
Can there be multiple instances of a microservice?
yes b/c it is part of a much larger application
- to share load for each part versus doing so for the entire application
Docker
popularized containers
- docker containers stored in cloud as images which can be pulled whe nneeded
Two ways to provide processor resources
Emulation
emulated chip and software
Advg: runs differently on platforms
Cons: not efficient
Schedule time on physical CPUs
most common
Virtual Processors (vCPUs)
best if number of vCPUs is no more than the number of pCPUs b/c chances are server was underutilized in teh first place and VM server may be mroe powerful
instead use software tools to monitor resource needs on the physical server in order to proeprly size the VM
or start with one vCPU and monitor performance, adding more vCPUs as necessary
Protection rings
describe level of privilege granted to the software
most trusted ring is 0 where kernel runs
1 and 2 used by device drivers
3 user applications run here
When running in a hypervisor, which protection ring should it be run in?
ring 0
but guest OS in VM wants to run in ring 0 too, so hypervisor must intercept and manage guest OS activities in ring 0
How does the hypervisor manage memory?
maps memory requests of guest OS to physical memory on the server
- if same file as OS, to save memory, hypervisor maps VM requests to copy of block in physical memory
What is a memory overcommit?
the hypervisor temporarily borrows memory from one VM to satisfy the needs of another using a balloon driver
these pages are pages the guest OS no longer needs
The VM directly communicates with…..
the emulated device that is mapped to a physical device
I/O virtualization advantages
enables hardware independence since teh VM sees a more general device
helps with VM migration since the enw host may not have teh exact same device
VMware ESXi Features
Storage VMotion:
migrates a virtual machine while it is in use.
Fault Tolerance:
creates a lockstep copy on another host, if the host fails users are switched to the copy without interruption.
Site Recovery Manager:
copies virtual machines to another site in case of data center disaster, allowing the new site to be up in minutes.
Storage and Network I/O Control:
lets an administrator set policies so that when there is contention on the network specific VMs or groups of VMs get priority.
Distributed Resource Scheduler (DRS):
can migrate VMs for workload balancing across hosts.
Token Bucket Filter
adjusting R and T determines fraction capacity a VM can claim
R/T fraction of processor allocation
Sum of R/T ratios for the various VMs must add to one or less
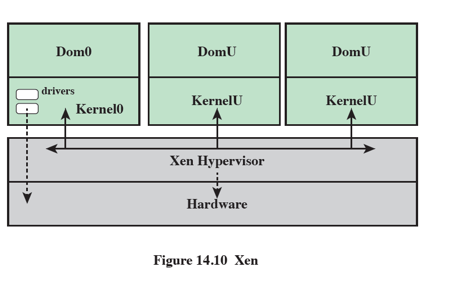
Microsoft Hyper-V Describe
Domain 0 (initial VM) has direct access to the hardware
Guest VMs are unprivileged called DomU
Dom0 provides access to network and storage resources to the DomU domains
Parent partition is like Dom0, child partitions are like DomU
Java VM
runs in a VM
JVM provides runtime space for Java program to run on any OS on any hardware without code changes
has own instruction set, PC, stack, heap
Linux VServer
File system isolation
changes root directory to something other than real root so server can only affect its own view of the file system
Process isolation
provides the server a new security context, so taht its processes cannot see or interact with processes from another context
Network isolation
provides server a specific IP address
Root isolation
changes teh capabilities of the server to not do everything the root user can do and set resource limits
Vserver Scheduling
token bucket filter overlays teh standard Linux Scheduler
controls how much processor time each VM gets
Tokens add to teh bucket at a rate of R tokens every interval T
Execution consumes tokens and when bucket empties, VM is put on hold until it refils to M tokens
R/T = fraction of processor allocation