Security + Professor Messer & Cyber
1/489
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
490 Terms
Social engineering principles
- Authority - pretending (CEO or Police) or knowing the CEO so do it or else
- Intimidation (Bad things will happen like payroll will fail)
-Consensus/Social Proof - they try to convince based on what's normally expected, a coworker did it for them last week
- Scarcity/Urgency (quantity) - time will expire, needs to happen now (creates Panic) - "buy now before the deal is over"
- Familiarity - know common people
- Trust - Pretending the attacker is from IT please click perform these steps
- Urgency - Time sensitivity that demand immediate action
Reciprocity - doing something in hopes to get something in return
Liking - Being likable so someone will do something for you
Commitment/Consistency - manipulate someone by making their requests seem consistent with what the person has done in the past.
CIA Triad
Confidentiality, Integrity, Availability
Organization data
- Product Information
- Employee Records
- Financial records
- Company private data
- Customer Information
Personal data
- family pictures and videos
- Health Records
- Social Security Number
- email and mail address
Phishing
- An email tricking you to click on malicious links/attachments or asking to provide personal information
- sent in bulk, not targeting individuals
(click here to update your payment details)
(click here to claim a prize)
Phishing Prevention
- Security awareness training
- software to prevent users from receiving phishing emails
- Don't be fooled by typos (check the URL)
- Usually, there's something not quite right (incorrect spelling, fonts, graphics)
- Go to the website directly
- check email headers
- Use MFA for credentials
- only login to trusted sites
SMishing (SMS Phishing)
Phishing messages using text messages
Forwards links and asks for personal information
- check the random information
- check for incorrect spelling
- check for incorrect URLs
- go to the site directly
Vishing (voice phishing)
a phone scam that attempts to defraud people by asking them to call a bogus telephone number to confirm their account information
- Caller ID spoofing
- Fake security checks or bank updates
- requesting personal information or access to your PC
How to Prevent:
- Service providers/third party tools will automatically block spam calls
- join do not call lists
- ignore them let them go to VM
- hang up
Typosquatting/URL hijacking
Websites with names similar to real websites; users making typographical errors are sent to a site filled with malware.
www.facebok.com or www.ffacebook.com
- the attacker can sell the misspelt domain to the company
- the attacker can sell the misspelt domain to a competitor so they can redirect traffic to the competitor's site
- the attacker can make money by putting ads on the site
- Phishing site - downloads malicious software when you visit the site
Pharming
Reroutes requests for legitimate websites to false websites, a hacker poisons a DNS server to redirect requests to a false website
- Difficult to know that you are being phished
- Hard for anti-malware software to stop
Defend against pharming
- don't use the default DNS settings use (openDNS/Google)
- check the padlock icon in the browser URL (certificates) it will alert when the site is not secure
- don't enter sensitive info into sites that look odd.
- check default router credentials (hackers could login to change DNS settings)
- enable MFA on your credentials
- keep browsers up to date (Patched)
Spear phishing
- Phishing with inside information (makes the attack more believable. targeting a certain person or group
Whaling attack
- attacking the CEO, officials or high-level executives with a phishing attack
Pretexting
a form of social engineering in which one individual lies to obtain confidential data about another individual
"Hi we are calling from Visa regarding your account"
Prepending
Influencing the subject before an event occurs adding words to a malicious file like "SAFE" to gain interest in opening
Using social media mentions (hash tags) to increase visibility or a post
Eliciting Information
encouraging/extracting information using casual conversation
Bracketing - using both high and low estimates to get a specific number from someone (how much did you make last year 80,000? and person may correct you with the accurate amount)
Can you top this - play on the fact that some people like to show off, you can share an extreme story to see if they will better it
Confidential Bait - Pretend to share confidential information which makes the other person feel like they can also share something confidential
identity fraud
your personal information is used to make purchases, withdraw cash, or set up new accounts, receive government benefits without your approval.
Impersonation
- pretending to be someone they are not
- attack the victim as someone higher in rank (CEO, IT)
- Throw tons of technical details around
- pretending to know someone familiar
- talk about common interests (Sports or News Trends)
How to protect against impersonation
- Never volunteer information
- Don't disclose personal detail
- Always verify before revealing info
- Verification should be encouraged
Dumpster diving
- Mobile garbage bin
- Important Information thrown out with the trash
- Gather details that can be used for a different
- Timing is important
- Dumpster diving can be legal if not locked up
- fence and lock trash cans
- shred/burn documents
- Examine trash for sensitive information
Shoulder surfing
- obtaining information by observing someone as they view or enter information
- webcam monitoring, Binoculars/ Telecopes, video surveillance
Preventing shoulder surfing
- control your input ( be aware of your surroundings)
- Use privacy filters
- Keep your monitor out of sight
- avoid public Wi-Fi and use MFA
De-hoaxing
- consider the source (don't believe anyone)
- cross reference - check hoax info websites to confirm hoax
- spam filters can help - filters can move to spam folder
- too good to be true it is
Computer hoaxes
Computer hoaxes are false or misleading messages, emails, or online content that are designed to deceive or trick computer users.
- Chain Emails to multiple people
- Social media hoaxes - fake news on social media
- Some hoaxes will take your money (Ask to buy gift cards and send code)
- Fake virus popups to get you to contact a number to click on a link
Watering hole attack
A malicious attack that is directed toward a small group of specific individuals who visit the same/popular website. (Coffee Shop, Financial Website)
hacking a popular website (using a vulnerability), when you go to the site and login or place an order you get infected with Malware
Watching the watering hole
- using VPN to encrypt traffic
- firewalls and IPS ( stop the network traffic before things get bad
- Anti-virus/ Anti- malware signature updates
Spam
unsolicited, unwanted commercial/Non-Commercial email messages or Phishing Attempts
- Security concerns
- Cause resource utilization
- Storage costs
- Software costs (Spam Filter)
SPIM (spam over internet messaging)
A form of spam using instant messaging that targets instant messaging users
Ways to Prevent Spam
- Spam Filter (email or on mail server/gateway)
- Allowed List - only emails from trusted senders are allowed through
- SMTP Standard Checks (RFC Standards) - block emails that don't follow RFC standards
- rDNS (Reverse DNS Lookup) block emails where the sender's domain doesn't match the IP address
- Tarpitting - Intentionally slow down the server conversation on your end or the hackers end so the hacker gives up and moves on
- Recipient Filtering - Block all emails not addressed to a valid recipient's email address
Influence campaigns
Using social engineering to sway attention and sympathy in a particular direction.
- Sway public opinion on political or social views
- the actor creates fake accounts on social media
- the fake users create a post fake content on social media
- real news outlets and real users pick it up because it is popular and they report on it
Influence Campaigns -Hybrid Warfare (Cyberwarfare)
Normally carried out by state actors (governments) to influence the balance of power in a country by using military, political, economic, or civil means, and conceivably running a campaign to spread disinformation.
Used to influence public opinion to start wars or change the opinion of a government
Credential Harvesting (Password Harvesting)
attackers trying to gain access to usernames, passwords, that might be stored on your computer
attackers harvest credentials by using:
- Phishing
- Mailware
- Brute Force
Prevent credential harvesting by:
- not clicking on links and attachments
- use MFA
- keep antivirus/ant-malware up to date
- use proper password management (avoid password re-use)
- dont send credentials over public wifi
Invoice Scams
using fraudulent invoices to steal from a company, typically the attacker knows who pays the bill for the company
The attacker pretends to be someone important in the company
Types of viruses
- Boot sector viruses - takes controls on bootup by infecting the boot sector of the HDD
-- Macro viruses - run in Macros (Common in Microsoft Office)
- Direct Action viruses - attach itself to files and spread when opening
- Resident viruses - embed itself into memory
- Polymorphic Virus - Can modify their code to evade detection
- Web Scripting virus - can exploit a browsers vulnerabilities
Malware
Malware is a type of software that is specifically designed to cause harm to a computer system, network, or device. The term "malware" is a combination of "malicious" and "software,
Defense against Malware:
- Keep anti-virus/anti-malware up to date
- Keep OS and software up to date
- Don't visit shady websites
Malware types
- Viruses - Infects executable files and spreads through a system by self-replicating to other devices. (it must be executed)
- Worm - a self-replicating program that spreads a cross the network, Worms do not need any human intervention to spread
- Trojans - disguises itself as legitimate software, but contains Malware (applications, videos) they are not viruses (only allow software from trusted sources and dont allow users to install software)
- Ransonware (Crypto-Malware) - encrypts files or locks a user out of a system, and demands payment in exchange for restoring access. (backup systems, store backups separately, file auto-versioning, patching, caution with websites & attachments)
Potentially Unwanted Programs (PUP)
- non malicious software
- installs toolbars, ad popups or redirects to other search engines
- Adware: A type of malware that displays unwanted advertisements or pop-ups on a user's screen. Developers get paid per click our view
- Malvertising - Malicious advertising, using ads to spread malware
Spyware - A type of malware that is designed to spy on a user's activity, such as recording keystrokes or taking screenshots.
Rootkits - A type of malware that is designed to hide its presence on a system, often by modifying the operating system. core system files (part of the kernel) - hard to detect and remove
Botnets: A type of malware that infects multiple devices and creates a network of "zombie" computers that can be controlled remotely. used to spread misinformation, create high network traffic, mine crypto and DDos attacks.
Command & Control (C&C) - used to control bots remotely, the connection can be established by a vulnerability or a backdoor
Fileless malware: A type of malware that operates entirely in memory, leaving no traces on the victim's hard drive and making it more difficult to detect and remove.
Backdoors - allows attackers back into a system after they gain access, they are not always malicious developers create them.
Prevent viruses:
- keep anti-virus/anti-malware software up to date
- don't open files blindly
- be careful what you download from the internet
- watch out for social engineering techniques
- code review
- network monitoring
- firewalls
- user awarenes
Virus vs. Worm
Viruses require some sort of activation, Worms do not
Worms and viruses are designed to self-replicate
Viruses latch on to other software
Worms spread through vulnerabilities
drive-by download
Program which automatically downloads when a user visits a web page, usually without their knowledge or consent.
How you get malware
- a worm finds a vulnerability
- installs malware that includes a remote access backdoor (Bot may be installed later)
- Your computer must run a program (email link, pop-up, drive-by download, worm)
-Vulnerable computer (out of date OS)
Protecting against ransomware
- always have a backup (an offline backup, ideally
- Keep your operating system up to date (Patch those vulnerabilities)
- keep your applications up to date (security patches)
- Keep your anti-virus/anti-malware signatures up to date (new attacks every hour)
Remote Access Trojans (RATs)
a type of malware that allows an attacker to take control of a victim's computer or device from a remote location. The attacker can then use this access to steal data, install additional malware, or use the infected system as a platform for launching further attacks.
- remote Administration Tool (ultimate backdoor, administrative control of a device)
Stealing sensitive data such as login credentials, financial information, or personal files.
Monitoring user activity, including keystrokes, web browsing, and application usage.
Using the victim's computer to launch attacks on other systems, as part of a larger botnet.
as cryptocurrency mining or distributing spam.
Protecting againsts trojans and RATs
- Don't run unknown software or links
- Keep anti-virus/anti-malware signatures updated (there are always new attacks)
- Always have a backup
- Use strong passwords
- Be cautious when allowing remote access to others
Easter egg
Non-malicious code that when invoked, displays an insider joke, hidden message, or secret feature
Zeus/Zbot malware
botnet malware used to clean out bank accounts.
commonly combined with Necurs rootkit for hard detection and removal.
Finding and removing rootkits
- Anti-malware scans/up to date
- have backups to restore your system
- use a specific remover
- Secure boot with UEFI (security in the BIOS)
Keyloggers
a type of software or hardware device that records every keystroke made on a computer or other device
Keyloggers can be installed on a device in a number of ways, including as part of a malware infection, through physical access to the device, or via a remote connection. Once installed, a keylogger can silently record every keystroke made on the device, including passwords, emails, chat conversations, and other sensitive information.
Preventing keyloggers
- Usually installed with malware (Use anti-virus/anti-malware & Keep your signatures updated)
- Block unauthorized communication ( block the exfiltration attempt & Firewall rules/ monitoring)
- Run a keylogging scanner (checks for keylogging activity)
Why is there so much adware and spyware
- Money
- your computer time and bandwidth is incredibly valuable
- Your bank account is incredibly valuable
Protecting against adware/spyware
- Maintain your anti-virus/ anti-malware (always have the latest signatures)
- Always know what you're installing (and watch your options during the installation)
- have a good backup
- Run some scans (Malwarebytes with latest signatures)
- Know what you are installing
Botnets
- Robot networks
- Once your machine is infected, it becomes a bot
- gets on your computer though trojan horse or OS/ application vulnerability
- Botnets are for sale
Stopping a Bonet
- Prevent initial infection (OS and application patches, Antivirus/anti-malware and updating signatures
- Identify an existing infection (On-demand scans and Network monitoring)
- IPS (Intrusion Prevention System) on a firewall from communicating to the C&C
- Security Groups NACL (Network Access Control List)
- Setup monitoring and logging
Bot Herder
An attacker who controls a botnet to launch attacks on other systems
Logic bomb
- Malware that is executed by a set of instructions when specific conditions are met (used by disgruntled employees)
- It can by executed at a certain time (time bomb)
- user event
- Logic bombs are difficult to identify and prevent as they may lie dormant for a longer period of time before being activated
Preventing a logic bomb
- implement strict access controls to a limited number of users
- Log monitoring (alert on changes, host-based intrusion detection, Tripwire, etc)
- constant auditing for changes
- strong password policies
Prevent Password Attacks
- Implement Password Policy (password lengths, deny lists, account lockouts, default password change)
- Use a password managers
- Enforce MFA
Forms of MFA/2FA
Something you are (biometric, face recognition, voice, veins, eyes)
Something you have (smart card, USB token, push SMS, PIN via SMS)
Something you know (password, pin, Security Question)
Somewhere you are (location, IP, geolocation area)
Something you can do (handwriting, typing technique, using patterns)
Something you exhibit - the way you talk, walk, or act
Someone you know - an employee vouching for you, comes down to meet you or your mother's maiden name
Weakest to Strongest:
- Something you know
- Something you have
- Something you are
plain text password
Passwords that are unencrypted and clear
- don't use software that does not support encrypted passwords or update to the latest version that does
Hashing Passwords
- Hashes represent data as a fixed-length string or text
- Will not have a collision
- different inputs will not have the same hash
- a hash is a one-way trip, it cannot be recovered (cannot remove the hash back to plain text)
- Use a hash to provide integrity
- Can be used to create digital signature
Hashes vs Encryption
Encryption - Secures confidential data (sending a password securely over HTTPS)
Hashing - protects the integrity of the information (storing the password in a database)
Hashing is a fixed length, all passwords will have the same hash length
Encryption uses variable lengths, passwords that are encrypted will be different lengths
Encryption a two-way function what is encrypted can be decrypted
Hashing - a one-way function that scrambles plain text, it cannot be reversed,
Spray Attack (Password Spraying)
- Type of Brute Force attack which tries common passwords
hackers will only try a few before stopping so they dont lock the account out
Prevent:
using MFA, Capcha, and force passwords to change at first login
Brute Force Attack - Online
the password cracker tries every possible combination of characters until the hash is matched
- Brute Force Attacks are ONLINE
- Keep trying the login process
- they are very slow and they lock out accounts
Brute Force Attack - Offline
- Takes the password database offline to crack the hashes
- It will not lockout accounts
- use powerful GPUs to crack the hashes quickly
Brute Force Attack - Dictionary Attack
Try common words from a dictionary as a password
- the cracker will try common numbers that replace letters (0 instead of O)
- use powerful GPUs to crack the hashes quickly
- use MFA
- limit number of login attempts
- reset password after a certain number of failed attempts
Credential Stuffing
Brute force attack in which stolen user account names and passwords are tested against multiple websites.
to defend against credential stuffing:
- Enforce MFA
- Add a pin, secondary password or security question
- Check user passwords against know leaked passwords
Rainbow Table
A table of hash values and their corresponding plaintext values that can be used to look up password values if an attacker is able to steal a system's encrypted password file.
- you need different rainbow table for each application/Operating System as they are not the same
Salt
Adding extra data to the beginning or the end of a hash so it is harder to crack
- Prevents Rainbow Tables as the hashes will always be different
Types of Physical Attacks
Malicious USB Cable - additional electronics inside the cable that will act as a HID (Human Interface Device) to allow the hacker to type or use the mouse, the hacker can open CMD and install malicious software
- dont use random cables
- keep systems up to date
- dont leave visitors alone
- use up to date anti virus
Malicious Flash Drive - additional electronics inside the drive that could run malicious software, hackers will leave them lying round to see if users will connect the drive and run the file
- dont use random flash drives
- keep systems up to date
- dont leave visitors alone
- use up to date anti virus
Skimming - stealing information from your card when you insert it into a pin pad or ATM, it will copy the stripe information.
(dont use tampered machines, use reputable stores, use credit instead of credit, check your bank statements)
Card Cloning - cloning a credit card including the CVC number or Gift Cards, when the GC is activated the hacker will use their card to take the funds from the legitimate GC
Tailgating - following an authorized person into a secure area
Shoulder surfing - looking over a user's shoulder while they are entering sensitive information
Power surge attacks: Attackers can damage or destroy electronic devices by sending a high voltage surge of electricity to the device.
Jamming: This involves disrupting wireless signals or electronic communications by broadcasting high-powered signals on the same frequency.
Machine Learning
A type of artificial intelligence that leverages massive amounts of data so that computers can improve the accuracy of actions and predictions on their own without additional programming.
Poisoning Machine Learning
Confuse the AI (Data Poisoning)- attackers send modified training data that causes the AI to behave incorrectly
AI Evasion attacks
Used to evade detection or mislead AI models, such as machine learning algorithms, by manipulating or changing the input data
Changing inputs to mess with AI machine learning.
Protect AI Evasion Attacks
- Secure the learning algorithms
- implement adversarial training
- Regular testing and auditing
Artificial Intelligence vs Machine Learning vs Deep Learning
Artificial Intelligence - focuses on accomplishing "smart" tasks combining machine learning and deep learning to emulate human intelligence
Machine Learning - a subset of AI, that uses algorithms to learn from data
Deep Learning - a subset of machine learning concerned with algorithms inspired by structure and function of the brain called Artificial Neural Networks
Supply-chain attack (Island Hoping)
A cyber-attack that seeks to damage an organization by targeting less-secure elements in the supply chain. (third party vendors/suppliers) IE Solarwinds Attack
How to Defend:
- Maintain a secure and up-to-date infrastructure
- Build a secure software update process
- restrict access to systems
- only allow authorized applications to run
- develop incident response processes
- use end-point detection (EDR)
Cloud-based attacks vs On-premises Attacks
Cloud-based attacks - Data center is often more secure and less vulnerable to disruptive attacks (like DDoS) On the downside, you will not have facility-level or physical system-level audit access.
On-premises Attacks - You do not benefit from the cloud's shared responsibility model. You have more control but are responsible for security of the full stack.
Org has to defend a wider range of attacks and greater expense and effort to defend against them.
Cloud-based vs. on-premises Deployments
Cloud based Pros:
- centralized
- costs less
- no data center
- automated signature and security updates
- Limited down times
- no hardware purchases
- provider provides physical security
- build systems quickly (one click)
Cloud based Cons:
- users must be trained on best security practices using the cloud
- more vulnerable to disruptive attacks
- Must have a internet connection
- Relying on a third party
- uncontrolled down time
- third parties could gain access
- cloud share responsibility (who is responsible if breached)
On-premises Pros:
- You have full control of your data
- on-site IT can manage security better
- you can maintain uptime and availability.
- more secure and less vulnerable
On-premises Cons:
- It puts the security burden on the client
- incurring the cost of having a fully staffed security team and renting a data center
- changes take a while, planning, ordering hardware
- you are responsible for the infrastructure
Cryptographic Attacks
- Birthday: - the probability of multiple of finding 2 inputs that have the same Hash value (prevent by using long hashes)
- Collision: - used with MD5 hash receiving the same hash even though the plaintext passwords are different (use collision-resistant hashes)
- Downgrade: - Force the system to downgrade the encryption so they can downgrade the security (TLS 1.2 to TLS 1.0) or downgrade from HTTPS to HTTP
- Brute Force - attacker tries every possible password
- Dictionary - use common words or phrases on a dictionary to guess a password
- Replay - attacker captures or eavesdrop network packets and replays them to gain access (credentials or sessions) (prevent by using date and time stamps)
Known plaintext attack: This type of attack involves analyzing the encrypted ciphertext and the corresponding plaintext to figure out the secret key.
- Side-Channel - using exploits in a cryptographic system, such as the power consumption or electromagnetic radiation, to gain access to the encryption key.
How to stop tailgating
- Policy for visitors (you should be identify anyone or have an escort)
- one scan, one person ( A matter of policy or mechanically required
-Mantrap/ Airlock
- don't be afraid to ask (Who are you and why are you here)
Privilege Escalation
- Gain higher-level access to a system
- Higher-level access means more capabilities
- These are high-priority vulnerability patches
- Horizontal privilege escalation - user A can access user B
Vertical privilege escalation - user moving from low level privileges to high level privileges
Mitigating privilege escalation
• Patch quickly - fix the vulnerability
• Updated anti-virus/anti-malware software - Block known vulnerabilities
• Data Execution Prevention - Only data in executable areas can run
- regularly check system configurations
- implement strong access controls/password policies
- provide "Least Privilege" access
Improper Error Handling
Software errors that provide too much information that an attacker can use to gain access.
Proper error handling to avoid errors from displaying:
- Stack traces
- Database dumps
- Memory dumps
- Network information
Cross-Site Scripting (XSS)
- an attacker injects malicious script into a web page viewed by other users.
- The injected code is typically in the form of a script that executes when a user visits the infected web page, allowing the attacker to steal sensitive information or perform other malicious actions.
Prevent:
- input validation and filtering
- validate data length and data types
Non-persistent (reflected) XSS attack
an attacker injects malicious code into a URL or form field (Search Box) that is then reflected back to the user in the page response.
Bad guy may email a link
- Email link runs a script that sends credentials/session IDs/cookies to the bad guy
- Script embedded in URL executes in the victim's browser, as if it came from the server
- Bad guys use credentials/session IDs/cookies to steal victim's information without their knowledge
Persistent (stored) XSS attack
an attacker injects malicious code into a web page that is then permanently stored on the web server and served to all users who access that page.
- Bad guy posts a message to a social network that includes a malicious payload (it's now "persistent")
- Everyone gets the payload
- No specific target
- For social networking, this can spread quickly
- Everyone who views the message can have it posted to their page, where someone else can view it and propagate it further.
Protecting against XSS
Be careful when clicking untrusted links • Never blindly click in your email inbox. Never.
• Consider disabling JavaScript • Or control with an extension This offers limited protection
Keep your browser and applications updated • Avoid the nasty browser vulnerabilities
Validate input • Don't allow users to add their own scripts to an input field
Use HTTPS encryption
Implement Consent Security Policy (CSP)
Use browser extensions that block XSS attacks
SQL Injection
SQL injection involves exploiting vulnerabilities in a web application's code to execute unauthorized access to a SQL database
Prevent:
Input validation, user prepared statements and limit account privileges
Code Injection
A method used by hackers to insert malicious code into legitimate files or data transmissions and applications.
XML injection
Is a type of security vulnerability that occurs when an attacker is able to manipulate or inject malicious content into an XML document or XML application to gain unauthorized access
The best defense is to filter the user's input and sanitize it to make certain that it does not cause XPath to return more data than it should.
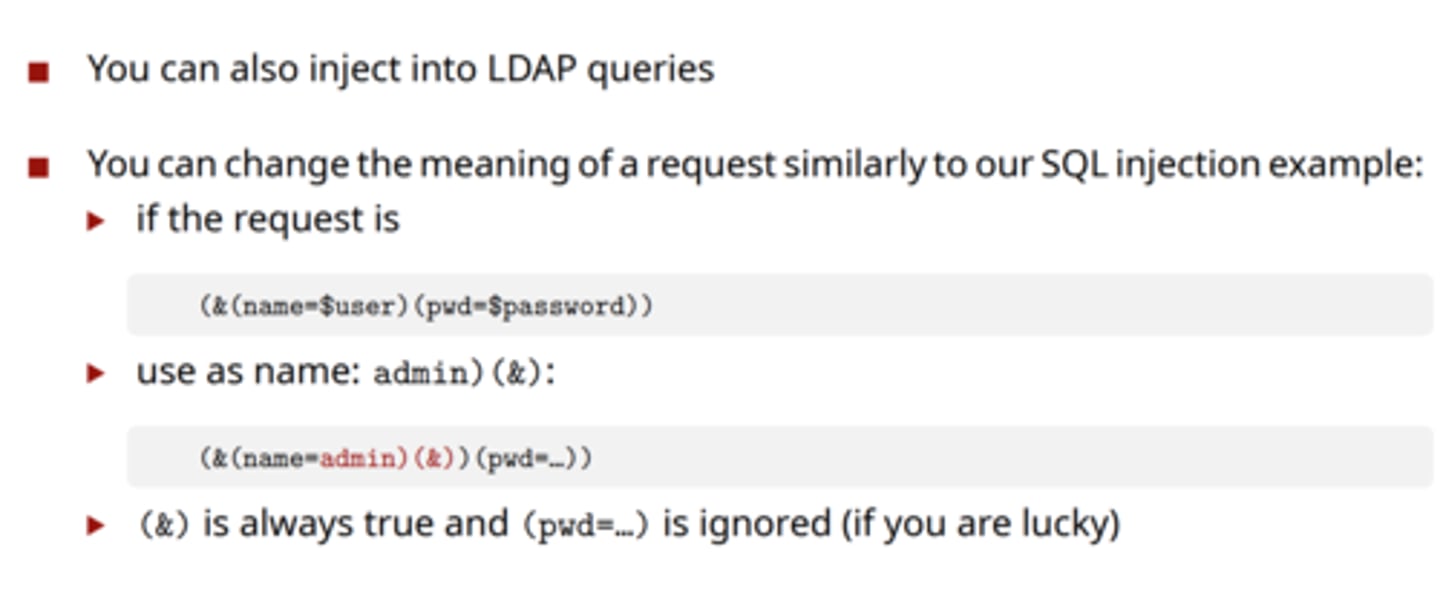
LDAP injection
Lightweight directory access protocol (LDAP) injection is a type of security vulnerability that occurs when an attacker is able to manipulate or inject malicious input into an LDAP query or command.
Modify LDAP requests to manipulate application results
https://example.com/searchusers?user=*
DLL injection
An attack that injects a malicious Dynamic Link Library (DLL) into memory and runs it. Attackers rewrite DLL, inserting malicious code
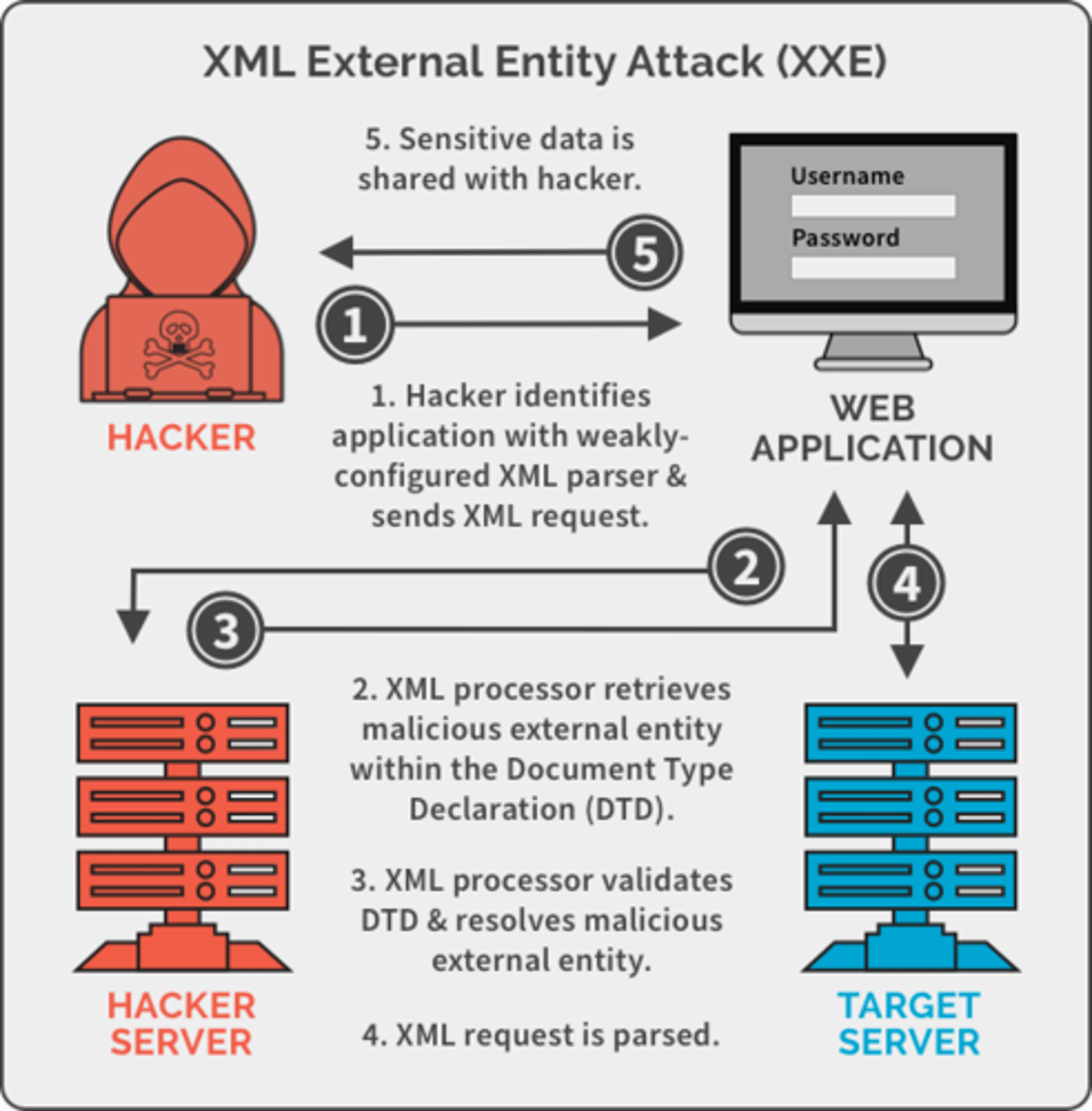
XML External Entities (XXE)
exploit: a vulnerability that occurs when an web application processes XML input from an untrusted source without proper validation or mitigation measures.
- Attackers could gain access to files on a application server
- Perform DOS attacks
- Gain backdoor access to systems
- used to perform server-side request forgery (SSRF)
prevent:
- Replace XML with JSON or YAML
- patch and update
- perform security testing
Buffer Overflow
A technique for crashing a system by sending too much data to the buffer in a computer's memory, and exceeds the size of the buffer. This can cause the data to spill over into adjacent memory locations, corrupting or overwriting data that may be used by the program or the operating system.
- Developers need to perform bounds checking so sections of memory cannot be overwritten (input validation)
Replay Attack
A type of network attack where an attacker captures network traffic and stores it for retransmission at a later time to gain
unauthorized access to a network.
Defend against Replay Attacks:
- Use time limits (Kerberos)
- use one-time passwords
- Nonce - Code that can only be used once and/or expires after a period of time
Session Replay
An attack in which an attacker attempts to impersonate a user by stealing a valid session and reuses it
Defend against session replays - disallow session ID reuse in web apps
Pass the Hash Attack
a method used by attackers to gain unauthorized access to a system by using the hashed password of a user without knowing the actual plaintext password.
This is possible because the hash is a representation of the password that can be used for authentication purposes.
Defend against pass the hash:
- use least privileges
Cookies
• Information stored on your computer by the browser
• Used for tracking, personalization, session management
- Could be considered be a privacy risk
-Session IDs are often stored in the cookie
Session Hijacking (Sidejacking)
When an attacker gains access to a active session ID and uses the ID to pose as the victim without needing a username or password/ fix by encrypting connection
Prevent session hijacking
- Encrypt end-to-end (HTTPS) - so they cannot capture your session ID
- Encrypt end-to-somewhere - use a VPN
- Use session ID monitors
Header Manipulation
Altering the headers of a packet to bypass security controls or deceive a system into accepting or processing a packet in an unintended way.
an attacker can modify the header fields to include false or misleading information, such as changing the source IP address to make it look like the packet is coming from a trusted network, or altering the protocol field to trick the system into processing the packet in an unintended way.
Cross-Site Request Forgery (CSRF or XSRF)
an attacker tricks a user's web browser into performing unintended actions on a trusted website
IE: you login to your bank which creates a session cookie, you visit a malicious site that will take that session to access your banking site without your knowledge
Prevent CSRF:
- use CSRF tokens and check the referring URL to ensure it came from the local site
Server-Side Request Forgery (SSRF)
When an attacker exploits a vulnerable web application to have a web server perform a request on behalf of the attacker
In an SSRF attack, the attacker sends a request to a vulnerable web application, which then executes the request on the server-side without properly validating the input parameters.
The attacker can exploit this vulnerability to perform various malicious activities, such as scanning internal networks, accessing sensitive files, or attacking other vulnerable applications that are not accessible directly from the internet.
Prevent SSRF:
- never trust user inputs
Driver Manipulation
A software attack where the attacker rewrites or replaces the legitimate device driver or application programming interface (API) to enable malicious activity to be performed