computing
1/44
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
45 Terms
How does cache memory improve performance
Faster access time than main memory
Slows frequently used instructions/data
How does increasing mantissa bits affect representation
Increases accuracy
What is breakpoint
Stops execution at specific line to inspect variables
What is watchpoint
Stops execution when a variable changes to inspect variables
Random number between 1-10
Number = [random.ranint(1,10
How does increasing exponent bits affect representation
Increases range
Benefit of comprehensive test plan
All functional requirements are tested

Rewrite the following
if N % divisor== 0 :
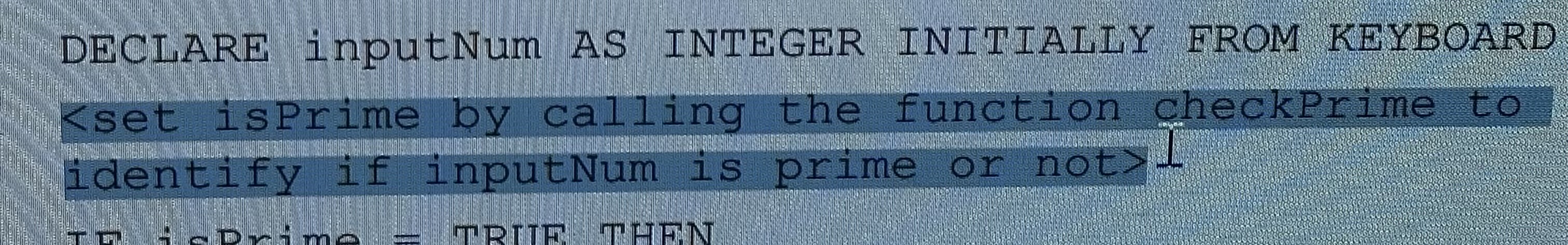
Rewrite highlighted
isPrime = checkPrime(inputNum)
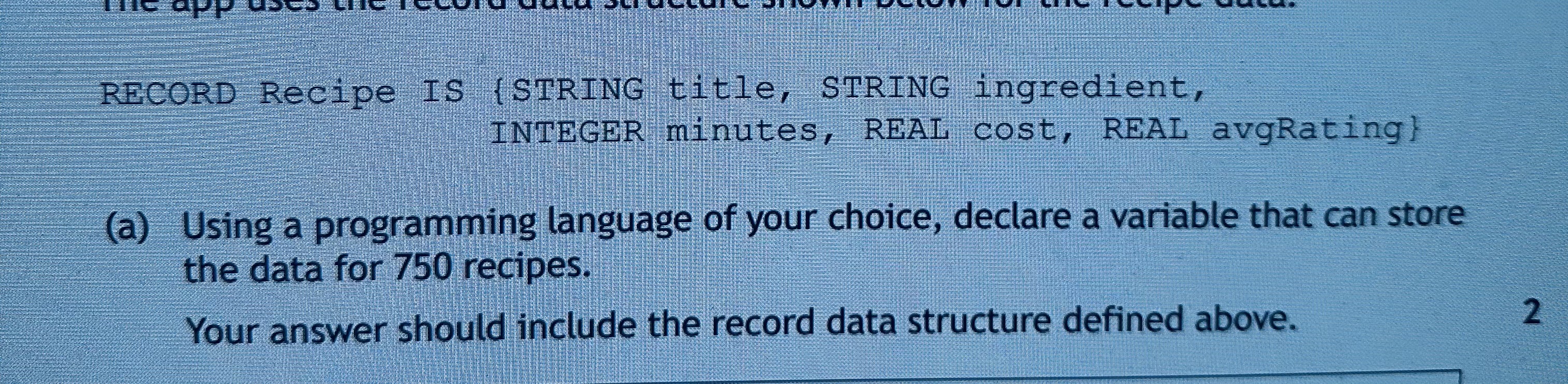
Answer the following
All recipe =[recipe() for x in range(750)]
Why is condition loop efficient
Exits array when value is found
What is an actual parameter
A parameter which is in the main program
What is a formal parameter
A parameter in the subprogram
Steps of fetch execute cycle
Address bus is set up with address
The processor activates the read line on the control bus
Data buss brings instruction from memory to register
It is then decoded and executed
How does identifying data flow assist programmer
Identifies parameters
Ways computer misuse can be breached
Unauthorised access
Intent to commit further offence
Unauthorised modification
Code for array of records
Class name
Def__init__(self):
Self.variable=“”
Design for array of records
RECORD array {
Variable AS TYPE STRING
variable AS TYPE REAL
variable AS TYPE BOOLEAN
Bandwidth consumption denial of service attack
Using all of websites available bandwidth
Resource starvation denial of service attack
An attempt to use enough server resources that the system becomes unresponsive
DNS denial of service attack
Modification of DNS record settings to point to a rogue DNS server
What is a Denial of service attack?
When someone tries to prevent legitimate users from accessing an online service via excessive network messages.
Types of test data
Normal, extreme and exceptional
Difference between extreme and exceptional
Exceptional is not within the range
What does increasing the cores on a processor do
Increases the number of instructions the processor can process at the same time
Why is a single processor running at twice the speed faster than a dual core processor
Not always able to share tasks equally between cores
What is a multi core processor
A processor that has multiple CPU’s on one chip
What does increasing the data bus width do
Increases the amount of data/info the bus can transfer at one time
What is cache memory
Small fast accessible memory usually on same chip as processor
What is clock rate
The frequency the clock generates pulses
How do intelligent transport systems improve traffic
Navigation systems avoid traffic
Use of cameras and sensors to move more
Car environmental impact
Start stop systems shut down cars engine when it’s not moving
Heating systems
Using sensors turn of heating when no one is home
Sensors can adjust heating if there is unusual activity
Compatibility testing is
Testing that website works on different browsers and devices
Symptoms of denial is service attacks
Slow performance
Inability to access data
Costs of Denial of service attacks
Lost revenue
Labour in fixing fault
Digital signature
created When message is sent with private key
Verifies sender and verifies message hasn’t been altered
Digital certificate
Authenticates a person, allowing the to exchange data over the internet over the internet using a public key
How is modular programming efficient and maintainable
Efficient: functions can be reused
Maintainable: Modules can be tested individually
Syntax error
Missing/wrong character or letter
Logic error
Error in logic of code, program can still execute but produces Unexpected results
execution error
Program is asked to do something it cannot do
Dry run
Programmer reads code and follows variable to check it is used/updated as expected
Bit mapped vs vector
Bitmapped resolution is set at creation and cannot be changed
Vector is resolution independent and can make use of highest resolution
Bitmapped is suited for photorealism and vector is not
vector more suitable
Object can be edited independently and can be layered