Software Engineering Exam Review
1/99
Earn XP
Description and Tags
Flashcards based on Software Engineering lecture notes.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
100 Terms
What are the characteristics of good software?
Reliable, Efficient, Ergonomic, Easy to maintain, Meet user Requirements
List probable causes of the software crisis.
Immature development and verification techniques, Low reproducibility of projects, Long and costly development process, Rapid introduction of new tools and technologies, Interoperability issues, Rapidly changing requirements, Complexity of systems
What is software engineering?
Technical knowledge of life cycle phases; Treats software as a product designed to meet a specific need; Empirical knowledge; An engineering discipline that deals with all aspects of software development
What is the software lifecycle?
The events and activities during the life of software, from the creation of an idea to its decommissioning
Describe the Big Bang software lifecycle.
"We sit down, we code; Maybe it will be a big boom and we’ll earn money"
Describe the Code and Fix software lifecycle
"We create a specification; Code-fix loop; The loop ends when the developer or the client has had enough"
Describe the waterfall model of the software lifecycle.
Idea, Specification, Design, Coding, Testing, Implementation
Describe the spiral model of the software lifecycle.
Iterative: Idea, Specification, Design, Coding, Testing, Implementation, Repeat
Describe incremental manufacturing in the software lifecycle.
Idea; We plan and design (sometimes everything, sometimes a small part); We produce in short cycles; We test; Implement; Repeat
Describe the Agile model.
A project management and software development approach that emphasizes iterative and incremental development, flexibility, and collaboration.
What is a 'defect' in software development?
A bug in the code that may (or may not) lead to incorrect execution
What is a 'Faulty execution'?
A situation in which the system produces a bad result, potentially due to a defect
What are static tests?
Analysis of design documents and other non-executable artifacts; Source code analysis
Select methods of code overview.
Over-the-shoulder, Email pass-around, Pair Programming, Tool-assisted
What is IEEE 1028?
A standard that defines five types of software reviews and audits: management reviews, technical reviews, inspections, walk-throughs, and audits, along with the procedures for each.
Who was Michael Fagan?
Inventor of the formal software inspection called “Fagan Inspection.” The process focuses on finding defects in documents like source code.
How many stages are there in inspection?
Six stages
Planning - the facilitator plans the inspection
Preparatory meeting - the author presents the product assumptions
Preparation - inspectors examine the product looking for defects
Inspection meeting - the presenter reads the product, inspectors point out defects
Corrections - the author implements the recommended corrections
Follow-up - inspectors verify the introduced corrections
What is static testing?
Analysis of design documents and other non-executable artifacts; Source code analysis; Code reviews, Transitions, Inspections
What is Dynamic Testing?
Examine the system's response to input and other variables; The system must be running.
What are Unit Tests?
Testing minimal components (e.g., methods); Each unit is tested separately.
What are Integration Tests?
Checking the integration of increasingly large modules; Finding defects in the interactions between them
What are System Tests?
Testing the system as a whole; This includes integration with external systems
What are Acceptance Tests?
Testing as part of software acceptance
What are Regression Tests?
Automated, Runs after software modification, to ensure that changes do not break working functionality
Describe Black Box Testing.
Treating software as a black box, not considering implementation; Unknown internal code structure.
Describe White Box Testing.
Known internal code structure; Testers have full knowledge of the internal workings of the application.
Describe Grey Box Testing.
Partially known internal code structure; Combination of Black box + White box
What is Equivalence Partitioning?
Test cases built based on equivalence intervals, typically derived from the specification
What are Fuzz Tests?
Input random data (fuzz) and check if the program crashes
What are Model-Based Tests?
Test cases are derived in whole or in part from a model that describes some aspects of the system under test
What are Specification-Based Tests?
Testing compliance with the requirements, preparing test cases based on the requirements
What is Verification in software testing?
"Have we built the software right?" Formal, Functional, and Dynamic checking of algorithms
What is Validation in software testing?
Whether we built the right software; Confirms that the product will perform in the intended application through Acceptance testing and Use in production
Select differences between dynamic and static verification.
First one includes Unit, Integration, System, Acceptance, Functional, and Non-functional tests.
Second includes Coding conventions, Detection of bad practices, Metrics, and Formal verification.
What does a test case description usually include?
Identifier, Identifier of the use case/requirement under test, Initial conditions, Steps, Expected result; must be reproducible.
What is a Smoke Test?
A subset of test cases; Tests useful for verifying proper installation and other changes; Can be run faster than the entire test suite.
What is Test Automation?
Using software to reduce or eliminate repetitive tasks, creating scripts or recording macros.
Select recommendations for testing.
Select inputs that force the system to generate all error messages, cause buffer overflows, repeat inputs multiple times, cause calculation results to be too small/large/incorrect, ensure repeatability of tests
Select proper description of “CAN” in CAN PIG RIDE mnemonic.
Clear, concise reports; Information should accurately identify the type of error; Neutral reporting of facts
Select proper description of “PIG” in CAN PIG RIDE mnemonic.
Precise description of the problem, Isolate what was done to isolate the problem, Generalize what we have done to determine how general the problem is
Select proper description of “RIDE” in CAN PIG RIDE mnemonic.
Re-create steps to reproduce the bug, Impact of the bug in a production environment, Debug information needed by developers, Evidence to prove that the bug exists
What is Estimating?
Cautious pricing or rough calculation; Preliminary calculation of project costs; Determination of the project's time consumption;
Manipulability: Time, Scope, Budget
What is FPA (Function Point Analysis)?
A method for measuring the functional size of a software system, focusing on the user's external view of the system's functionality.
What is UCP (Use Case Points)?
Software estimation technique used to forecast the software size; Counts use cases instead of data sets and transactional functions.
What is the Refactoring Process?
Change of the code structure (but no change in code behavior); Cleans code with minimal risk of errors; Steps include Problem identification, Writing unit test, Refactoring, and Testing
Select “Bad smells” in code.
Code problem resulting from poor design; Examples include Code duplication, Long methods, Large classes, Long parameter list
What is “Shotgun surgery” in coding?
Used when responsibility/code has been scattered between many classes; Single change is made to multiple classes
What is a bidirectional association?
Both objects are aware of each other and can interact.
What is a unidirectional association?
Only one object knows about and interacts with the other.
What is Encapsulation?
Limiting direct access to some data by building the data with methods that are put in capsules with restricted access exposing just what is necessary
What is Layered Architecture?
Application divided into logical layers; Each provides specific layer of abstractions; Each layer responsible for different functions
What is Component-Based Architecture?
Application is divided into components; Each is responsible for a group of functionalities; Components can be substituted.
What is a Pipeline?
A process divided into stages, each implemented by a component connected into a pipe; Solution used in operating systems
What is “Sprint” in SCRUM?
Period of time, usually from 1 to 4 weeks, in which tasks are performed in SCRUM
What is Event-Driven Architecture?
Instead of direct calls between systems components, an event is issued; communication through events where Components create or consume events.
Who is Scrum Master?
Facilitates meetings, Removes blockers, ensures adherence to process, and oversees time constraints; DOES NOT MANAGE
What is ITIL?
Information Technology Infrastructure Library; Guidelines for delivering IT services in an enterprise; Set of rules based on best practices consisting of 5 publications
What roles are in ITIL?
Process Owner(Checks if service fits the purpose),
Process Manager(Monitors the process and reports),
Service Owner(Responsible for delivery),
Service Manager(Manages life cycle),
Business relationship manager,
Configuration and resource management
What is SCRUM?
Framework focused on managing software development process used for other projects; abstracts from technical issues.
What is the Product owner responsible for in SCRUM?
Responsible for project vision and profit, and manages priority of tasks in the backlog.
What is Code Refactoring?
The process of restructuring code to improve clarity, design, or performance without changing its external behavior or functionality.
What is the goal of code refactoring?
To improve visibility of the code, to make it clean, more readable, and more optimized
What are "code smells"?
Code smells are patterns that suggest potential problems in code structure or design
What is the difference between code duplication and feature envy?
First one - similar code appears in many places(cut-and-paste).
Second one - is when a class has methods that operate on other classes and/or methods are placed in the wrong class.
What is 'primitive obsession' in refactoring?
Not using classes for small tasks
What is the purpose of the 'Extract Method' refactoring technique?
Extracting a part of code and putting it into a method, then referring to the method where the code was, used for improving visibility and deleting code duplication
What is the difference between 'Inline Method' and 'Replace Temp with Query'?
Inline method eplace references to the method with its body and remove the method; Replace Temp with Query - Extract expression into the method - then call the method
What is a 'Lazy class' and when should it be removed?
When a created class doesn't do much; its content can probably be moved to another class
What is 'Shotgun Surgery' and how can it be fixed?
A change that requires modifying multiple classes; Fixed by centralizing responsibilities to reduce scattered changes.
What does "Replace Conditional with Polymorphism" mean?
We move the behaviors to obscure methods in subclasses, declare the original method as abstract
What is the “Introduce Parameter Object” technique?
If some class has a lot of same repeatable parameters - you store those parameters in the object and then just call the object
What is the 'Replace Constructor with Factory Method' pattern?
When a constructor does more than just setting the parameters; You create a method that takes care of constructor calls
What is meant by 'Replace Magic Number with Symbolic Constant'?
Replacing a number (like 3.14 - Pi.Math) with a symbolic constant (public class) so its more understandable.
What are signs that you should extract a class from existing code?
When one class does the work of 2 classes
What is the difference between 'Push Down Method' and 'Pull Up Method'?
First Method moves a superclass method to subclasses where it makes sense (just one actor uses method);
Second Method extracts the same methods from subclasses to the superclass because both are in use by similar actors
What is 'Speculative Generality' in refactoring?
Code that is not needed at the moment, but 'may come in handy someday;' Its presence is confusing and makes it difficult to work with code that is actually needed
What is a 'Data Clump' and how can it be addressed?
The same few data elements appear in many places together, and it is often a good idea to consider creating a new class out of them
What are “Parallel Inheritance Hierarchies” in refactoring?
2+ class hierarchies related to each other (special case of shotgun surgery)
What is the difference between delegation and inheritance?
Delegation uses another object to do work; inheritance creates a subtype relationship
What is Event-Driven Architecture?
Loosely coupled components where Components create or consume events through Asynchronous exchange of event information. Specific consumers listen for events created by specific senders
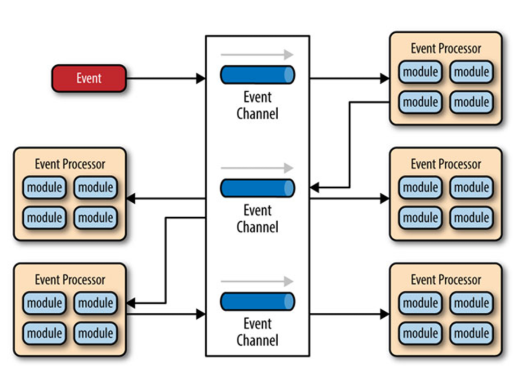
What is a message queue and how is it used?
Similar to event-driven, even looser connections. Messages are divided into classes, specific queues or topics. Clients listen for messages from a specific class/queue/topic.
What is the role of a broker in software architecture?
Mediator-type service that manages communication between customers and services; Often assists the customer in locating and identifying required services
What is Service-Oriented Architecture (SOA)?
Large-scale component architecture where Business logic is divided into many small, independent services and Applications are built by assembling selected services
What is REST and how does it relate to web services?
Representational State Transfer; An architectural style for designing web services that facilitates communication between systems, especially over the Internet. Use of web standards; No encapsulation
What is the purpose of the Abstract Factory pattern?
Provide an interface for creating families of related objects, without specifying concrete classes
When would you use the Strategy design pattern?
Defining a family of algorithms, encapsulating and treating them as interchangeable. The strategy allows the algorithm used to change independently of the client using it.
What is the Chain of Responsibility pattern?
Avoid binding the sender of a request to a single receiver by allowing more than one object to handle the request. Allow the order (and the use itself) of the objects handling the request to change dynamically
What is the difference between a class and an object in UML?
In UML, a class represents an object or a set of objects that share a common structure and behavior. Objects are model elements that represent instances of a class or of classes
What is the purpose of a package in UML?
To group elements, and to provide a namespace for the grouped elements
What are enumerations used for in UML?
In UML models, enumerations are model elements in class diagrams that represent user-defined data types
What is the difference between aggregation and composition?
Aggregation: A weak relationship where one object contains another but the contained object can exist independently.
Composition: A strong relationship where one object contains another, and the contained object cannot exist without the container.
What is Parkinson’s Law and how does it affect estimation?
"Work expands to fill the time available for its completion”; it can cause overestimation and inefficiency
What is the Delphi Method?
An estimation technique involving anonymous expert feedback through multiple rounds to reach consensus
What are the key components of Function Point Analysis (FPA)?
ILF- internal application datasets,
ELF - external data sets,
EI - data arriving from outside the application boundary,
EO - data sent outside the application boundary,
EQ - queries incoming from outside the application boundary
What are Use Case Points (UCP) and how are they calculated?
Software estimation technique used to forecast the software size by calculating the number and complexity of use cases and actors and including technical and environmental factors
What are user stories and how are they written?
A small functional requirement that has a business value. Acceptance criteria should be clearly defined using the INVEST method
What is the INVEST mnemonic in Scrum?
Independent, Negotiable, Valuable, Estimable, Small, Testable
What are spikes in Scrum?
Experiment with a technology, an algorithm, or an idea, to Improve estimates or Reduce technological risk; Implemented in a 'fast and dirty' approach
What is Technical Debt?
Untested, unrefined, refactored elements of the solution; The cost of additional rework caused by choosing an easy solution now instead of a better one
What is the purpose of a Sprint Retrospective?
Team discusses what went well, what could be better, and defines action items.