Computer & Information Science - Computer Security (Group 7)
1/25
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
26 Terms
What is information security?
Information security is the numerous techniques and policies implemented to protect data from unauthorized access and modification.
What is cyber security?
Cybersecurity is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, theft of, or damage to hardware, software, or data.
What makes information security important?
Information security is important as it prevents access to and modification of data from unauthorized persons who could sometimes have malicious intentions.
True or False?
Cybersecurity deals with the protection of DIGITAL data and information whereas Information security deals with safeguarding your information assets that are both PHYSICAL and DIGITAL
True
Can the terms "computer security" and "cyber security" be used interchangeably?
Yes because most information is stored electronically and is accessible via the Internet, which therefore enforces the importance of protection from malicious users both digitally and physically.
What are the three qualities used to evaluate and address issues risen by information security?
Confidentiality, Availability & Integrity
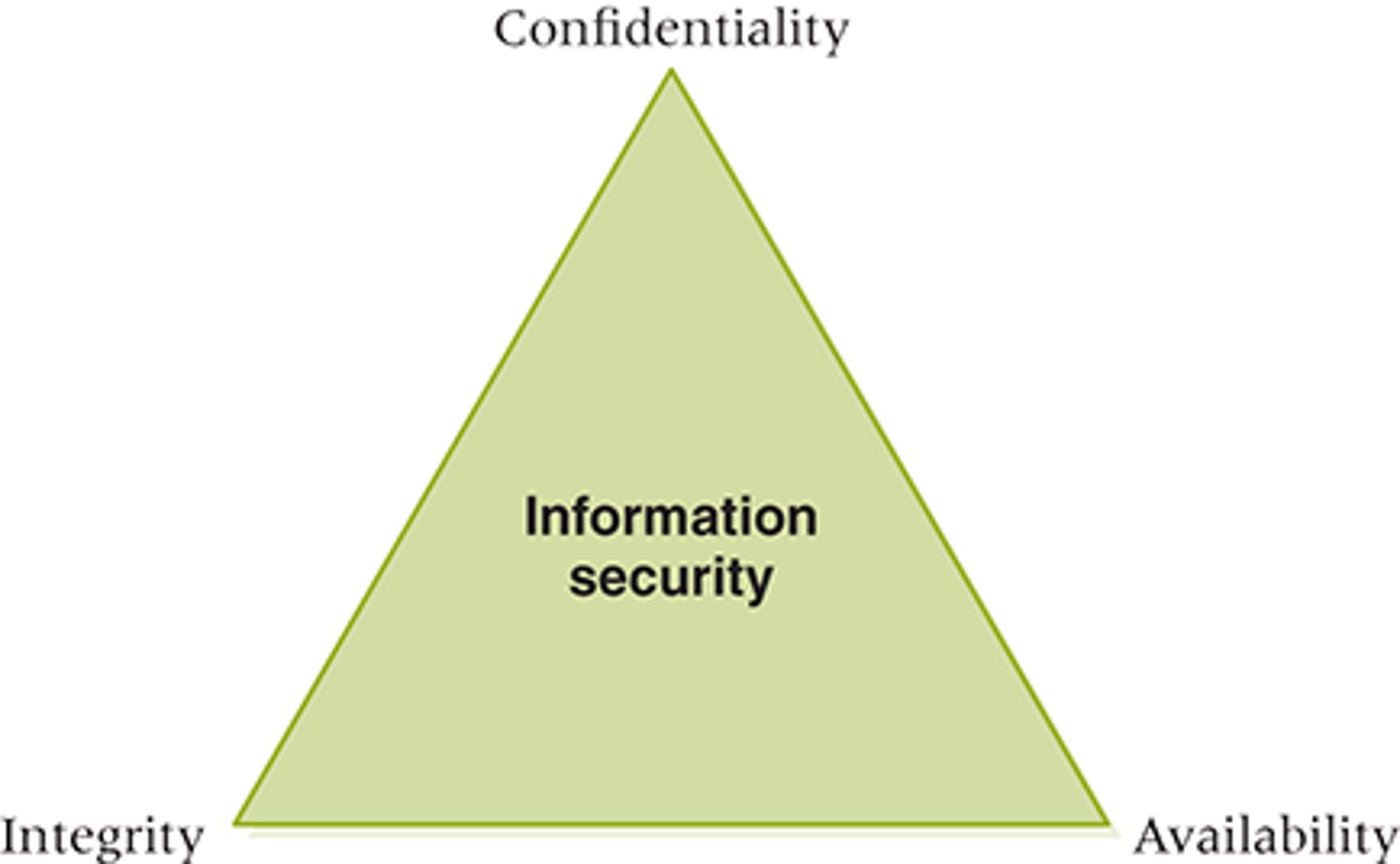
What is confidentiality?
Confidentiality is the assurance that information is not disclosed to unauthorized persons, processes, or devices at any given time.
What is integrity?
Integrity is assurance that any information provided is accurate and trustworthy.
What is availability?
Availability is a guarantee of reliable access to the information by AUTHORIZED people. This is ensuring that when information is required by such users, it is readily available to them.
True or False?
Protection of your account balance by the bank the protection of your health and personal information within hospitals are some scenarios where information confidentiality comes into play.
True
Is the following an example of integrity, confidentiality or availability?
Ensuring bank balance can only be modified by appropriate users via appropriate mechanisms.
Integrity
True or False?
Hardware problems and network attacks can cause an information availability problem.
True
True or False?
User authentication verifies the identity of a user attempting to gain access to a network or computing resource by authorizing a human-to-machine transfer of credentials during interactions on a network to confirm a user's authenticity.
True
What are the three general types of authentication credentials?
1. Something the user knows such as:
- Username and password
- A PIN (Personal Identification Number)
2. Something the user possesses such as:
- Identification card with a magnetic strip
- smart card with an embedded memory chip.
3. Biometrics (Physical Traits) such as:
- fingerprints, retina pattern, or voice pattern.
Which is the most expensive authentication method to implement?
Biometrics
1. "The password must be six characters or longer."
2. "It must contain at least one uppercase and one lowercase letter."
3." It must contain at least one digit."
4. "It must contain at least one special character, such as ! or %."
The guidelines above are known collectively as:
The Password Criteria
What is CAPTCHA?
CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) is a system used to:
1. Differentiate humans from computers in order to ensure that the information provided through a web form has been filled in by a person as opposed to a computer program.
2. Prevent spam or inappropriate material.
A program that grants unauthorized access to a software system to any person who knows it exists is known as:
A Back Door
The term "secret writing" is where the professional term _____________________ derived from.
Cryptography
Cryptography is a method of protecting information and communications through the use of codes, so that only those for whom the information is intended can read and process it.
How would you describe encryption and decryption?
1. Encryption is the process of converting ordinary text (known as plaintext) into cryptography terminology (a form that is unreadable). This form is known as ciphertext.
2. Decryption reverses this process, translating ciphertext into plaintext. A cipher is an algorithm used to perform a particular type of encryption and decryption.
Any program code that explicitly attempts to bypass appropriate authorization safeguards and/or perform unauthorized functions.
A Malicious Code, also known as Malware
What is a virus?
A program that embeds itself in another program. This "infected" file is referred to as the virus host. When the host is executed, the virus code runs as well.
What is a WORM?
WORM is a standalone program that self-replicates, but does not require a host program to infect the computer. A worm tends to cause problems on the networks it uses to send copies of itself to other systems, often by consuming bandwidth.

True or False?
A worm requires a host program whereas a virus does not
False
What problems does a worm cause on networks?
Consumes bandwidth.
True or False
The difference between a virus and a WORM is that a virus tends to cause problems on a particular computer by corrupting or deleting files whereas WORM tends to send copies of itself to other computers on the same network
True