4.6 - CompTIA A+ Core 2
1/18
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
19 Terms
Incident response
The process of managing the aftermath of a security breach or cyberattack, with the goal of minimizing damage, reducing recovery time, and preventing future incidents.
Chain of custody
The process of maintaining and documenting the handling of evidence related to an incident to ensure its integrity and admissibility in legal proceedings.
First response (incident response)
Identify the issue (logs, monitoring data), and report to proper channels, including internal management and law enforcement.
Copy of drive (incident response)
Involves copying the contents of a drive via imaging software, and preserving the drive using hashes to maintain data integrity.
Documentation (incident response)
Involves creating a log of all findings during the incident response process, including an event summary, detailed information on data acquisition, findings, and conclusion.
Order of volatility
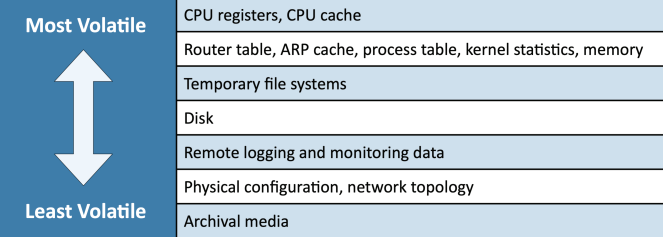
Refers to how stored data can last without changing; data should be gathered in the order of most volatile to least volatile to preserve data integrity.
Perpetual license agreements
Licenses that operate via ongoing subscriptions or payments, allowing users to maintain access to the software indefinitely.
Personal-use license
Software license agreement designed for the home user, usually associated with a single device or small group of devices.
Corporate-use license
Software license agreement intended for businesses, allowing installation and use on multiple devices or users within an organization.
Open-source license
Software licensing model that allows users to freely modify the source code of an executable and create their own software.
Non-disclosure agreement (NDA)
A legally binding contract that establishes a confidential relationship between parties, ensuring sensitive information remains protected.
Mutual non-disclosure agreement (MNDA)
A legally binding contract that ensures both parties protect each other's confidential information, allowing for the exchange of valuable insights.
Credit card payment information
Information related to digital credit/debit card payments, regulated via PCI DSS standards.
Personal government-issued information
Information like Social Security numbers, passport numbers, or driver's license details that must be protected under privacy regulations.
Personally Identifiable Information (PII)
Any data that can identify an individual; privacy policies can dictate how this is handled.
Protected Health Information/Healthcare data
Health information associated with an individual, protected under HIPAA regulations.
Data retention requirements
Regulations and policies that dictate the duration for which data must be stored and the conditions for its access.
Acceptable use policies (AUP)
Policies that dictate the acceptable use of company assets like workstations and company-issued phones.
Splash screens
A message, logo, or graphic shown during startup or login, used for branding, information, or compliance.