Dumpsbase Salesforce Identity Certification
1/75
Earn XP
Description and Tags
https://www.dumpsbase.com/freedumps/salesforce-certified-identity-and-access-management-architect-exam-materials-pass-on-the-first-attempt.html
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
76 Terms
1. Universal Containers (UC) is building a custom employee hut) application on Amazon Web Services (AWS) and would like to store their users' credentials there. Users will also need access to Salesforce for internal operations. UC has tasked an identity architect with evaluating Afferent solutions for authentication and authorization between AWS and Salesforce.
How should an identity architect configure AWS to authenticate and authorize Salesforce users?
Configure the custom employee app as a connected app
Configure AWS as an OpenID Connect Provider
Create a custom external authentication provider.
Develop a custom Auth server in AW
Correct: 2
To understand why "Configure AWS as an OpenID Connect Provider" is the correct answer, let's break down the scenario and the provided options:
Scenario:
Universal Containers (UC) is developing a custom employee application on AWS.
This application needs to store user credentials.
Users will also need access to Salesforce for internal operations.
An identity architect is tasked with evaluating solutions for authentication and authorization between AWS and Salesforce.
Options Analysis:
Configure the custom employee app as a connected app (Wrong):
A connected app in Salesforce allows an external application to integrate with Salesforce using APIs. However, this doesn't address the requirement of handling user credentials and authentication directly between AWS and Salesforce.
Configure AWS as an OpenID Connect Provider (Correct):
OpenID Connect (OIDC) is an identity layer built on top of OAuth 2.0. It allows clients to verify the identity of the end-user based on the authentication performed by an authorization server.
By configuring AWS as an OpenID Connect Provider, AWS can manage user authentication, and then issue tokens that Salesforce can validate to authorize access.
This setup allows seamless integration for Single Sign-On (SSO) where users can log in to AWS and automatically gain access to Salesforce using the same credentials.
Create a custom external authentication provider (Wrong):
While creating a custom external authentication provider is a possible solution, it requires significant effort to develop and maintain. Additionally, it might not be as secure and reliable as using established protocols like OpenID Connect.
Develop a custom Auth server in AWS (Wrong):
Developing a custom authentication server would involve building and maintaining a full-fledged authentication system, which is complex and unnecessary given the availability of standardized solutions like OpenID Connect. This option is overkill for the given requirements.
Conclusion:
Configuring AWS as an OpenID Connect Provider is the correct choice because it leverages an established protocol to handle authentication and authorization between AWS and Salesforce efficiently. This approach ensures security, scalability, and ease of integration, fulfilling UC's requirements without the complexity of custom solutions.
2. The executive sponsor for an organization has asked if Salesforce supports the ability to embed a login widget into its service providers in order to create a more seamless user experience.
What should be used and considered before recommending it as a solution on the Salesforce Platform?
OpenID Connect Web Server Flow. Determine if the service provider is secure enough to store the client secret on.
Embedded Login. Identify what level of UI customization will be required to make it match the service providers look and feel
Salesforce REST apis. Ensure that Secure Sockets Layer (SSL) connection for the integration is used
Embedded Login. Consider whether or not it relies on third party cookies which can cause browser compatibility issues
Correct: 4
3. Northern Trail Outfitters (NTO) utilizes a third-party cloud solution for an employee portal. NTO also owns Salesforce Service Cloud and would like employees to be able to login to Salesforce with their third-party portal credentials for a seamless expenence. The third-party employee portal only supports OAuth.
What should an identity architect recommend to enable single sign-on (SSO) between the portal and Salesforce?
Configure SSO to use the third party portal as an identity provider
Create a custom external authentication provider
Add the third-party portal as a connected app
Configure Salesforce for Delegated Authentication
Correct: 1
4. Universal Containers is budding a web application that will connect with the Salesforce API using JWT OAuth Flow.
Which two settings need to be configured in the connect app to support this requirement? Choose 2 answers
The Use Digital Signature option in the connected app
The "web" OAuth scope in the connected app
The "api" OAuth scope in the connected app
The "edair_api" OAuth scope m the connected app
Correct: 1 and 3
5. Universal containers (UC) has multiple salesforce orgs and would like to use a single identity provider to access all of their orgs.
How should UC'S architect enable this behavior?
Ensure that users have the same email value in their user records in all of UC's salesforce orgs.
Ensure the same username is allowed in multiple orgs by contacting salesforce support.
Ensure that users have the same Federation ID value in their user records in all of UC's salesforce orgs.correct
Ensure that users have the same alias value in their user records in all of UC's salesforce orgs.
Correct: 3
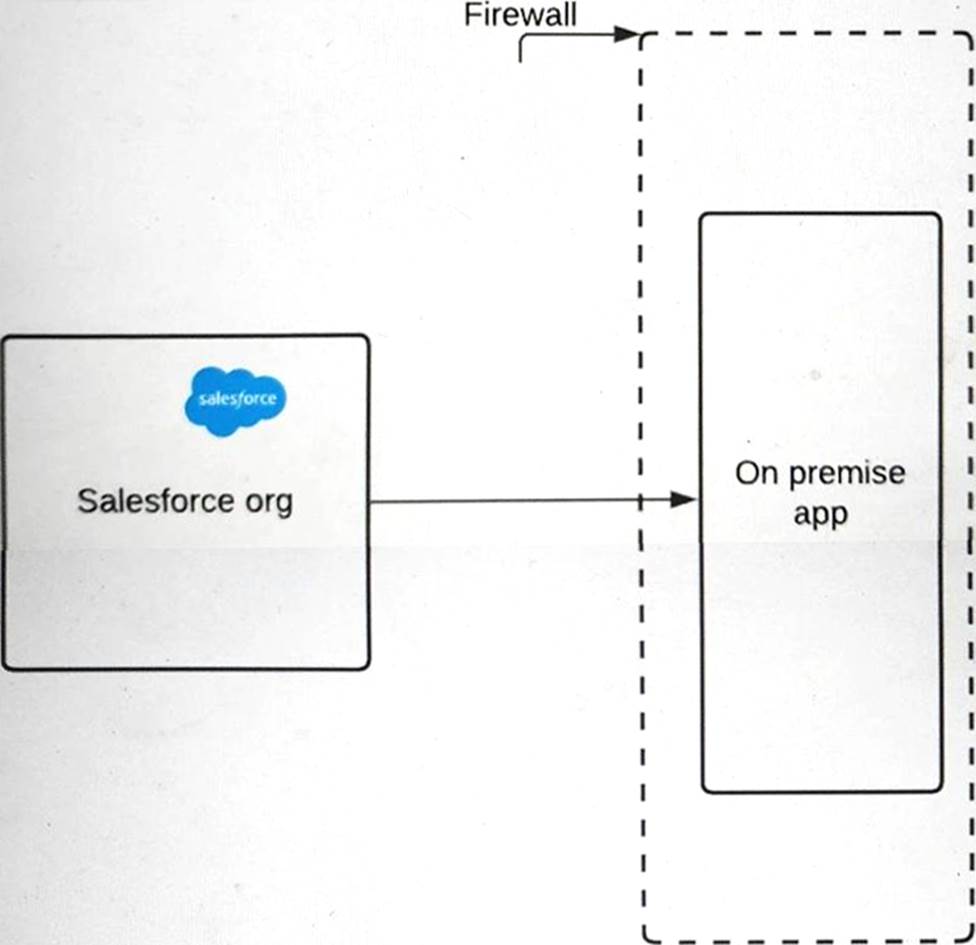
6. A pharmaceutical company has an on-premise application (see illustration) that it wants to integrate with Salesforce.
The IT director wants to ensure that requests must include a certificate with a trusted certificate chain to access the company's on-premise application endpoint.
What should an Identity architect do to meet this requirement?
Use open SSL to generate a Self-signed Certificate and upload it to the on-premise app.
Configure the company firewall to allow traffic from Salesforce IP ranges
Generate a certificate authority-signed certificate in Salesforce and uploading it to the on-premise application Truststore
Upload a third-party certificate from Salesforce into the on-premise server.
Correct: 2
7. The security team at Universal Containers (UC) has identified exporting reports as a high-risk action and would like to require users to be logged into Salesforce with their Active Directory (AD) credentials when doing so. For all other users of Salesforce, users should be allowed to use AD Credentials or Salesforce credentials.
What solution should be recommended to prevent exporting reports except when logged in using AD credentials while maintaining the ability to view reports when logged in with Salesforce credentials?
Use SAML Federated Authentication and block access to reports when accessed through a Standard Assurance session.
Use SAML Federated Authentication and Custom SAML JIT Provisioning to dynamically and or remove a permission set that grants the Export Reports Permission.
Use SAML federated Authentication, treat SAML Sessions as High Assurance, and raise the session level required for exporting reports
Use SAML federated Authentication with a Login Flow to dynamically add or remove a Permission Set that grants the Export Reports Permission.
Correct: 3
8. Universal Containers (UC) wants to build a custom mobile app for their field reps to create orders in salesforce. After the first time the users log in, they must be able to access salesforce upon opening the mobile app without being prompted to log in again.
What Oauth flows should be considered to support this requirement?
Web Server flow with a Refresh Token.
Mobile Agent flow with a Bearer Token.
User Agent flow with a Refresh Token.
SAML Assertion flow with a Bearer Token.
Correct: 3
9. A global fitness equipment manufacturer uses Salesforce to manage its sales cycle. The manufacturer has a custom order fulfillment app that needs to request order data from Salesforce. The order fulfillment app needs to integrate with the Salesforce API using OAuth 2.0 protocol.
What should an identity architect use to fulfill this requirement?
Canvas App Integration
OAuth Tokens
Authentication Providers
Connected App and OAuth scopes
Correct: 4
10. Universal Containers is creating a web application that will be secured by Salesforce Identity using the OAuth 2.0 Web Server Flow uses the OAuth 2.0 authorization code grant type).
Which three OAuth concepts apply to this flow? Choose 3 answers
Verification URL
Client Secret
Access Token
Scopes
Correct: 2, 3, 4
For the OAuth 2.0 Web Server Flow (also known as the authorization code grant type), the following three OAuth concepts are relevant:
Client Secret: This is a confidential string used by the client to authenticate to the authorization server. It is used along with the client ID to prove the identity of the application making the request.
Access Token: This token is issued by the authorization server after the client application has successfully authenticated and been authorized. It is used to access the protected resources on behalf of the user.
Scopes: These define the specific permissions or level of access that the client application is requesting. They determine what resources and operations the access token will allow the client to perform.
Therefore, the correct answers are:
Client Secret
Access Token
Scopes
The "Verification URL" is not directly related to the OAuth 2.0 Web Server Flow.
11. Universal containers (UC) employees have salesforce access from restricted ip ranges only, to protect against unauthorised access. UC wants to rollout the salesforce1 mobile app and make it accessible from any location.
Which two options should an architect recommend? Choose 2 answers
Relax the ip restriction in the connect app settings for the salesforce1 mobile app
Use login flow to bypass ip range restriction for the mobile app
Relax the ip restriction with a second factor in the connect app settings for salesforce1 mobile app
Remove existing restrictions on ip ranges for all types of user access.
Correct: 1, 3
It’s not possible to bypass ip range restriction with a login flow. The ip is verified way before the login flow is intended to start its execution
12. An Enterprise is using a Lightweight Directory Access Protocol (LDAP) server as the only point for user authentication with a username/password. Salesforce delegated authentication is configured to integrate Salesforce under single sign-on (SSO).
Mow can end users change their password?
Users once logged In, can go to the Change Password screen in Salesforce.
Users can click on the "Forgot your Password" link on the Salesforce.com login page.
Users can request the Salesforce Admin to reset their password.
Users can change it on the enterprise LDAP authentication portal.
Correct: 4
13. Which two are valid choices for digital certificates when setting up two-way SSL between Salesforce and an external system. Choose 2 answers
Use a trusted CA-signed certificate for salesforce and a trusted CA-signed cert for the external systemcorrect
Use a trusted CA-signed certificate for salesforce and a self-signed cert for the external systemwrong
Use a self-signed certificate for salesforce and a self-signed cert for the external systemcorrect
Use a self-signed certificate for salesforce and a trusted CA-signed cert for the external system
Correct: 3 and 4
14. Universal containers (UC) has a classified information system that it's call centre team uses only when they are working on a case with a record type of "classified". They are only allowed to access the system when they own an open "classified" case, and their access to the system is removed at all other times. They would like to implement SAML SSO with salesforce as the IDP, and automatically allow or deny the staff's access to the classified information system based on whether they currently own an open "classified" case record when they try to access the system using SSO.
What is the recommended solution for automatically allowing or denying access to the classified information system based on the open "classified" case record criteria?
Use a custom connected App handler using apex to dynamically allow access to the system based on whether the staff owns any open "classified" cases
Use apex trigger on case to dynamically assign permission sets that grant access when a user is assigned with an open "classified" case, and remove it when the case is closed
Use custom SAML jit provisioning to dynamically query the user's open "classified" cases when attempting to access the classified information system
Use salesforce reports to identify users that currently owns open "classified" cases and should be granted access to the classified information system
Correct: 1
Even thought the 2 is also appealing, with the 1 it’s real time and no need to create/manage any permission set
15. Universal Containers (UC) uses Global Shipping (GS) as one of their shipping vendors. Regional leads of GS need access to UC's Salesforce instance for reporting damage of goods using Cases. The regional leads also need access to dashboards to keep track of regional shipping KPIs. UC internally uses a third-party cloud analytics tool for capacity planning and UC decided to provide access to this tool to a subset of GS employees. In addition to regional leads, the GS capacity planning team would benefit from access to this tool. To access the analytics tool, UC IT has set up Salesforce as the Identity provider for Internal users and would like to follow the same approach for the GS users as well.
What are the most appropriate license types for GS Tregional Leads and the GS Capacity Planners? Choose 2 Answers
Customer Community Plus license for GS Regional Leads and External Identity for GS Capacity Planners
Customer Community Plus license for GS Regional Leads and Customer Community license for GS Capacity Planners
Identity Licence for GS Regional Leads and External Identity license for GS capacity Planners
Customer Community license for GS Regional Leads and Identity license for GS Capacity Planners
Correct: 1 and 2
16. Universal Containers (UC) wants its users to access Salesforce and other SSO-enabled applications from a custom web page that UC magnets. UC wants its users to use the same set of credentials to access each of the applications.
What SAML SSO flow should an Architect recommend for UC?
SP-Initiated with Deep Linking
SP-Initiated
IdP-Initiated
User-Agent
Correct: 3
17. Universal containers (UC) built a customer Community for customers to buy products, review orders, and manage their accounts. UC has provided three different options for customers to log in to the customer Community: salesforce, Google, and Facebook.
Which two role combinations are represented by the systems in the scenario? Choose 2 answers
Google is the service provider and Facebook is the identity provider
Salesforce is the service provider and Google is the identity provider
Facebook is the service provider and salesforce is the identity provider
Salesforce is the service provider and Facebook is the identity provider
Correct: 2 and 4
18. A group of users try to access one of Universal Containers' Connected Apps and receive the following error message: " Failed: Not approved for access."
What is the most likely cause of this issue?
The Connected App settings "All users may self-authorize" is enabled.
The Salesforce Administrators have revoked the OAuth authorization.
The Users do not have the correct permission set assigned to them.
The User of High Assurance sessions are required for the Connected App.
Correct: 3
19. Universal Containers has multiple Salesforce instances where users receive emails from different instances. Users should be logged into the correct Salesforce instance authenticated by their IdP when clicking on an email link to a Salesforce record.
What should be enabled in Salesforce as a prerequisite?
My Domain
External Identity
Identity Provider
Multi-Factor Authentication
Correct: 1
20. After a recent audit, universal containers was advised to implement Two-factor Authentication for all of their critical systems, including salesforce.
Which two actions should UC consider to meet this requirement? Choose 2 answers
Require users to provide their RSA token along with their credentials
Require users to supply their email and phone number, which gets validated
Require users to enter a second password after the first Authentication
Require users to use a biometric reader as well as their password
Correct: 1 and 4
21. Containers (UC) has an existing Customer Community. UC wants to expand the self-registration capabilities such that customers receive a different community experience based on the data they provide during the registration process.
What is the recommended approach an Architect Should recommend to UC?
Create an After Insert Apex trigger on the user object to assign specific custom permissions
Create separate login flows corresponding to the different community user personas
Modify the Community pages to utilize specific fields on the User and Contact records
Modify the existing Communities registration controller to assign different profiles
Correct: 4
22. Universal Containers (UC) wants to build a few applications that leverage the Salesforce REST API. UC has asked its Architect to describe how the API calls will be authenticated to a specific user.
Which two mechanisms can the Architect provide? Choose 2 Answers
Authentication Token
Session ID
Refresh Token
Access Token
Correct: 3 and 4
23. Northern Trail Outfitters (NTO) believes a specific user account may have been compromised. NTO inactivated the user account and needs U perform a forensic analysis and identify signals that could Indicate a breach has occurred.
What should NTO's first step be in gathering signals that could indicate account compromise?
Review the User record and evaluate the login and transaction history.
Download the Setup Audit Trail and review all recent activities performed by the user.
Download the Identity Provider Event Log and evaluate the details of activities performed by the user.
Download the Login History and evaluate the details of logins performed by the user.
Correct: 4
24. An Architect needs to advise the team that manages the Identity Provider how to differentiate Salesforce from other Service Providers.
What SAML SSO setting in Salesforce provides this capability?
Identity Provider Login UR
Issuer
Entity Id
SAML Identity Location.
Correct: 3
25. Universal containers (UC) is building a mobile application that will make calls to the salesforce REST API. Additionally UC would like to provide the optimal experience for its mobile users.
Which two OAuth scopes should UC configure in the connected App? Choose 2 answers
Refresh token
API
full
Web
Correct: 1 and 2
26. When designing a multi-branded Customer Identity and Access Management solution on the Salesforce Platform, how should an identity architect ensure a specific brand experience in Salesforce is presented?
The Experience ID, which can be included in OAuth/Open ID flows and Security Assertion Markup Language (SAML) flows as a URL parameter.
Provide a brand picker that the end user can use to select its sub-brand when they arrive on salesforce.
Add a custom parameter to the service provider's OAuth/SAML call and implement logic on its login page to apply branding based on the parameters value.
The Audience ID, which can be set in a shared cookie.
Correct: 1
27. Universal Containers (UC) has a strict requirement to authenticate users to Salesforce using their mainframe credentials. The mainframe user store cannot be accessed from a SAML provider. UC would also like to have users in Salesforce created on the fly if they provide accurate mainframe credentials.
How can the Architect meet these requirements?
Use a Salesforce Login Flow to call out to a web service and create the user on the fly.
Use the SOAP API to create the user when created on the mainframe; implement Delegated Authentication.
Implement Just-In-Time Provisioning on the mainframe to create the user on the fly.
Implement OAuth User-Agent Flow on the mainframe; use a Registration Handler to create the user on the fly.
Correct: 2
28. Universal Containers wants to implement Single Sign-on for a Salesforce org using an external Identity Provider and corporate identity store.
What type of authentication flow is required to support deep linking'
Web Server OAuth SSO flow
Service-Provider-Initiated SSO
Identity-Provider-initiated SSO
StartURL on Identity Provider
Correct: 2
29. Universal Containers (UC) would like to enable self-registration for their Salesforce Partner Community Users. UC wants to capture some custom data elements from the partner user, and based on these data elements, wants to assign the appropriate Profile and Account values.
Which two actions should the Architect recommend to UC1 Choose 2 answers
Configure Registration for Communities to use a custom Visualforce Page
Modify the SelfRegistration trigger to assign Profile and Account.
Modify the CommunitiesSelfRegController to assign the Profile and Account.
Configure Registration for Communities to use a custom Apex Controller.
Correct: 1 and 3
30. Containers (UC) has implemented SAML-based single Sign-on for their Salesforce application and is planning to provide access to Salesforce on mobile devices using the Salesforce1 mobile app. UC wants to ensure that Single Sign-on is used for accessing the Salesforce1 mobile App.
Which two recommendations should the Architect make? Choose 2 Answers
Configure the Embedded Web Browser to use My Domain URcorrect
Configure the Salesforce1 App to use the MY Domain URcorrect
Use the existing SAML-SSO flow along with User Agent Flow.wrong
Use the existing SAML SSO flow along with Web Server Flow.
Correct: 1 and 2
31. Universal Containers (UC) is using its production org as the identity provider for a new Experience Cloud site and the identity architect is deciding which login experience to use for the site.
Which two page types are valid login page types for the site? Choose 2 answers
Experience Builder Page
lightning Experience Page
Login Discovery Page
Embedded Login Page
Correct: 1 and 3
32. Universal containers (UC) wants to integrate a Web application with salesforce. The UC team has implemented the Oauth web-server Authentication flow for authentication process.
Which two considerations should an architect point out to UC? Choose 2 answers
The web application should be hosted on a secure server.
The web server must be able to protect consumer privacy
The flow involves passing the user credentials back and forth
The flow will not provide an Oauth refresh token back to the server
Correct: 1 and 2
33. Universal Containers (UC) is building a custom Innovation platform on their Salesforce instance. The Innovation platform will be written completely in Apex and Visualforce and will use custom objects to store the Data. UC would like all users to be able to access the system without having to log in with Salesforce credentials. UC will utilize a third-party idp using SAML SSO.
What is the optimal Salesforce licence type for all of the UC employees?
Identity Licence.
Salesforce Licence.
External Identity Licence.
Salesforce Platform Licence.
Correct: 3
34. Universal Containers (UC) is planning to deploy a custom mobile app that will allow users to get e-signatures from its customers on their mobile devices. The mobile app connects to Salesforce to upload the e-signature as a file attachment and uses OAuth protocol for both authentication and authorization.
What is the most recommended and secure OAuth scope setting that an Architect should recommend?
Id
Web
Api
Custom_permissions
Correct: 3
35. Northern Trail Outfitters (NTO) is launching a new sportswear brand on its existing consumer portal built on Salesforce Experience Cloud. As part of the launch, emails with promotional links will be sent to existing customers to log in and claim a discount. The marketing manager would like the portal dynamically branded so that users will be directed to the brand link they clicked on; otherwise, users will view a recognizable NTO-branded page.
The campaign is launching quickly, so there is no time to procure any additional licenses.
However, the development team is available to apply any required changes to the portal.
Which approach should the identity architect recommend?
Create a full sandbox to replicate the portal site and update the branding accordingly.
Implement Experience ID in the code and extend the URLs and endpomts, as required.
Use Heroku to build the new brand site and embedded login to reuse identities.
Configure an additional community site on the same org that is dedicated for the new brand.
Correct: 2
36. Northern Trail Outfitters (NTO) leverages Microsoft Active Directory (AD) for management of employee usernames, passwords, permissions, and asset access. NTO also owns a third-party single sign-on (SSO) solution. The third-party party SSO solution is used for all corporate applications, including Salesforce.
NTO has asked an architect to explore Salesforce Identity Connect for automatic provisioning and deprovisiorung of users in Salesforce.
What role does identity Connect play in the outlined requirements?
Service Provider
Single Sign-On
Identity Provider
User Management
Correct: 4
37. The CIO of universal containers(UC) wants to start taking advantage of the refresh token capability for the UC applications that utilize Oauth 2.0. UC has listed an architect to analyze all of the applications that use Oauth flows to. See where refresh Tokens can be applied.
Which two OAuth flows should the architect consider in their evaluation? Choose 2 answers
Web server
Jwt bearer token
User-Agent
Username-password
Correct: 1 and 3
38. How should an Architect automatically redirect users to the login page of the external Identity provider when using an SP-Initiated SAML flow with Salesforce as a Service Provider?
Use visualforce as the landing page for My Domain to redirect users to the Identity Provider login Page.
Enable the Redirect to the Identity Provider setting under Authentication Services on the My domain Configuration.
Remove the Login page from the list of Authentication Services on the My Domain configuration.
Set the Identity Provider as default and enable the Redirect to the Identity Provider setting on the SAML Configuration.
Correct: 3
39. Universal Containers (UC) is building an authenticated Customer Community for its customers. UC does not want customer credentials stored in Salesforce and is confident its customers would be willing to use their social media credentials to authenticate to the community.
Which two actions should an Architect recommend UC to take? Choose 2 answers.
Use Delegated Authentication to call the Twitter login API to authenticate users.
Configure an Authentication Provider for LinkedIn Social Media Accounts.
Create a Custom Apex Registration Handler to handle new and existing users.
Configure SSO Settings For Facebook to serve as a SAML Identity Provider.
Correct: 2 and 3
40. A company wants to provide its employees with a custom mobile app that accesses Salesforce. Users are required to download the internal native IOS mobile app from corporate intranet on their mobile device. The app allows flexibility to access other Non Salesforce internal applications once users authenticate with Salesforce. The apps self-authorize, and users are permitted to use the apps once they have logged into Salesforce.
How should an identity architect meet the above requirements with the privately distributed mobile app?
Use connected app with OAuth and Security Assertion Markup Language (SAML) to access other Non Salesforce internal apps.
Configure Mobile App settings in connected app and Salesforce as identity provider for non-Salesforce internal apps.
Use Salesforce as an identity provider (IdP) to access the mobile app and use the external IdP for other non-Salesforce internal apps.
Create a new hybrid mobile app and use the connected app with OAuth to authenticate users for Salesforce and non-Salesforce internal apps.
Correct: 2
41. A real estate company wants to provide its customers a digital space to design their interior decoration options. To simplify the registration to gain access to the community site (built in Experience Cloud), the CTO has requested that the IT/Development team provide the option for customers to use their existing social-media credentials to register and access.
The IT lead has approached the Salesforce Identity and Access Management (IAM) architect for technical direction on implementing the social sign-on (for Facebook, Twitter, and a new provider that supports standard OpenID Connect (OIDC)).
Which two recommendations should the Salesforce IAM architect make to the IT Lead? Choose 2 answers
Use declarative registration handler process builder/flow to create, update users and contacts.
Authentication provider configuration is required each social sign-on providers; and enable Authentication providers in community.
For supporting OIDC it is necessary to enable Security Assertion Markup Language (SAML) with Just-in-Time provisioning (JIT) and OAuth 2.0.
Apex coding skills are needed for registration handler to create and update users.
Correct: 2 and 4
42. Universal containers(UC) has implemented SAML-BASED single Sign-on for their salesforce application and is planning to provide access to salesforce on mobile devices using the salesforce1 mobile app. UC wants to ensure that single Sign-on is used for accessing the salesforce1 mobile app.
Which two recommendations should the architect make? Choose 2 answers
Use the existing SAML SSO flow along with user agent flow.
Configure the embedded Web browser to use my domain URL
Use the existing SAML SSO flow along with Web server flow
Configure the salesforce1 app to use the my domain URL
Correct: 1 and 4
43. Universal containers(UC) has a customer Community that uses Facebook for authentication. UC would like to ensure that changes in the Facebook profile are reflected on the appropriate customer Community user.
How can this requirement be met?
Use the updateuser() method on the registration handler class.
Use SAML just-in-time provisioning between Facebook and Salesforce
Use information in the signed request that is received from Facebook.
Develop a schedule job that calls out to Facebook on a nightly basis.
Correct: 1 (3 is also really feasible here)
44. Northern Trail Outfitters (NTO) has a number of employees who do NOT need access Salesforce objects. Trie employees should sign in to a custom Benefits web app using their Salesforce credentials.
Which license should the identity architect recommend to fulfill this requirement?
Identity Only License
External Identity License
Identity Verification Credits Add-on License
Identity Connect License
Correct: 1
45. What is one of the roles of an Identity Provider in a Single Sign-on setup using SAML?
Validate token
Create token
Consume token
Revoke token
Correct: 2
46. Containers (UC) uses a legacy Employee portal for their employees to collaborate. Employees access the portal from their company’s internal website via SSO. It is set up to work with SiteMinder and Active Directory. The Employee portal has features to support posing ideas. UC decides to use Salesforce Ideas for voting and better tracking purposes. To avoid provisioning users on Salesforce, UC decides to integrate Employee portal ideas with Salesforce idea through the API.
What is the role of Salesforce in the context of SSO, based on this scenario?
Service Provider, because Salesforce is the application for managing ideas.
Connected App, because Salesforce is connected with Employee portal via AP.
Identity Provider, because the API calls are authenticated by Salesforce.
An independent system, because Salesforce is not part of the SSO setup.
Correct: 1
47. Northern Trail Outfitters (NTO) uses the Customer 360 Platform implemented on Salesforce Experience Cloud. The development team in charge has learned of a contactless user feature, which can reduce the overhead of managing customers and partners by creating users without contact information.
What is the potential impact to the architecture if NTO decides to implement this feature?
Custom registration handler is needed to correctly assign External Identity or Community license for the newly registered contactless user.
If contactless user is upgraded to Community license, the contact record is automatically created and linked to the user record, but not associated with an Account.
Contactless user feature is available only with the External Identity license, which can restrict the Experience Cloud functionality available to the user.
Passwordless authentication can not be supported because the mobile phone receiving one-time password (OTP) needs to match the number on the contact record.
Correct: 3
49. An insurance company has a connected app in its Salesforce environment that is used to integrate with a Google Workspace (formerly known as G Suite).
An identity and access management (IAM) architect has been asked to implement automation to enable users, freeze/suspend users, disable users, and reactivate existing users in Google Workspace upon similar actions in Salesforce.
Which solution is recommended to meet this requirement?
Configure user Provisioning for Connected Apps.
Update the Security Assertion Markup Language Just-in-Time (SAML JIt; handler in Salesforce for user provisioning and de-provisioning.
Build a custom REST endpoint in Salesforce that Google Workspace can poll against.
Build an Apex trigger on the useriogin object to make asynchronous callouts to Google
APIs.
Correct: 1
50. Which three are capabilities of SAML-based Federated authentication? Choose 3 answers
Trust relationships between Identity Provider and Service Provider are required.
SAML tokens can be in XML or JSON format and can be used interchangeably.
Web applications with no passwords are more secure and stronger against attacks.
Access tokens are used to access resources on the server once the user is authenticated.
Centralized federation provides single point of access, control and auditing.
Correct: 1, 4, 5
51. Northern Trail Outfitters (NTO) uses a Security Assertion Markup Language (SAML)-based Identity Provider (idP) to authenticate employees to all systems. The IdP authenticates users against a Lightweight Directory Access Protocol (LDAP) directory and has access to user information. NTO wants to minimize Salesforce license usage since only a small percentage of users need Salesforce.
What is recommended to ensure new employees have immediate access to Salesforce using their current IdP?
Install Salesforce Identity Connect to automatically provision new users in Salesforce the first time they attempt to login.
Build an integration that queries LDAP periodically and creates new active users in Salesforce.
Configure Just-in-Time provisioning using SAML attributes to create new Salesforce users as necessary when a new user attempts to login to Salesforce.
Build an integration that queries LDAP and creates new inactive users in Salesforce and use a login flow to activate the user at first login.
Correct: 3
53. What information does the 'Relaystate' parameter contain in sp-Initiated Single Sign-on?
Reference to a URL redirect parameter at the identity provider.
Reference to a URL redirect parameter at the service provider.
Reference to the login address URL of the service provider.
Reference to the login address URL of the identity Provider.
Correct: 2
54. A client is planning to rollout multi-factor authentication (MFA) to its internal employees and wants to understand which authentication and verification methods meet the Salesforce criteria for secure authentication.
Which three functions meet the Salesforce criteria for secure MFA? Choose 3 answers
Username and password + SMS passcode
Username and password + security key
Third-party single sign-on with Mobile Authenticator app
Certificate-based Authentication
Lightning Login
Correct: 2, 3, 4
55. Universal Containers (UC) wants its closed Won opportunities to be synced to a Data Warehouse in near real time. UC has implemented Outbound Message to enable near real-time data sync. UC wants to ensure that communication between Salesforce and Target System is Secure.
What Certificate is sent along with the Outbound Message?
The CA-Signed Certificate from the Certificate and Key Management menu.
The default Client Certificate from the Develop--> API Menu.
The default Client Certificate or a Certificate from Certificate and Key Management menu.
The Self-Signed Certificates from the Certificate & Key Management menu.
Correct: 3
56. Universal containers(UC) wants to integrate a third-party reward calculation system with salesforce to calculate rewards. Rewards will be calculated on a schedule basis and update back into salesforce. The integration between Salesforce and the reward calculation system needs to be secure.
Which are the recommended best practices for using Oauth flows in this scenario? Choose 2 answers
Oauth refresh token flow
Oauth SAML bearer assertion flow
Oauthjwt bearer token flow
Oauth Username-password flow
Correct: 1, 3
about 2: The “Oauth SAML Bearer Assertion Flow” is typically used for Single Sign-On (SSO) scenarios where users authenticate once and gain access to multiple applications.
57. An identity architect has been asked to recommend a solution that allows administrators to configure personalized alert messages to users before they land on the Experience Cloud site (formerly known as Community) homepage.
What is recommended to fulfill this requirement with the least amount of customization?
Customize the registration handler Apex class to create a routing logic navigating to different home pages based on the user profile.
Use Login Flows to add a screen that shows personalized alerts.
Build a Lightning web Component (LWC) for a homepage that shows custom alerts.
Create custom metadata that stores user alerts and use a LWC to display alerts.
Correct: 2
58. Universal Containers (UC) uses Salesforce as a CRM and identity provider (IdP) for their Sales Team to seamlessly login to intemaJ portals. The IT team at UC is now evaluating Salesforce to act as an IdP for its remaining employees.
Which Salesforce license is required to fulfill this requirement?
External Identity
Identity Verification
Identity Connect
Identity Only
Correct: 4
59. Universal Containers (UC) wants to build a mobile application that twill be making calls to the Salesforce REST API. UC's Salesforce implementation relies heavily on custom objects and custom Apex code. UC does not want its users to have to enter credentials every time they use the app.
Which two scope values should an Architect recommend to UC? Choose 2 answers.
Custom_permissions
Api
Refresh_token
Full
Correct: 2, 3
60. Northern Trail Outfitters (NTO) employees use a custom on-premise helpdesk application to request, approve, notify, and track access granted to various on-premises and cloud applications, including Salesforce. Salesforce is currently used to authenticate users.
How should NTO provision Salesforce users as soon as they are approved in the helpdesk application with the approved profiles and permission sets?
Build an integration that performs a remote call-in to the Salesforce SOAP or REST AP
Use a login flow to query the helpdesk to validate user status.
Have the helpdesk initiate an IdP-initiated Just-m-Time provisioning Security Assertion Markup Language flow.
Use Salesforce Connect to integrate with the helpdesk application.
Correct: 1
61. A web service is developed that allows secure access to customer order status on the Salesforce Platform. The Service connects to Salesforce through a connected app with the web server flow. The following are the required Actions for the authorization flow:
User Authenticates and Authorizes Access
Request an Access Token
Salesforce Grants an Access Token
Request an Authorization Code
Salesforce Grants Authorization Code
What is the correct sequence for the authorization flow?
1, 4, 5, 2, 3
4, 1, 5, 2, 3
2, 1, 3, 4, 5
4, 5, 2, 3, 1
Correct: 1
62. An administrator created a connected app for a custom web application in Salesforce which needs to be visible as a tile in App Launcher The tile for the custom web application is missing in the app launcher for all users in Salesforce. The administrator requested assistance from an identity architect to resolve the issue.
Which two reasons are the source of the issue? Choose 2 answers
StartURL for the connected app is not set in Connected App settings.
OAuth scope does not include "openid*.
Session Policy is set as 'High Assurance Session required' for this connected app.
The connected app is not set in the App menu as 'Visible in App Launcher".
Correct: 1 and 4
64. A third-party app provider would like to have users provisioned via a service endpoint before users access their app from Salesforce.
What should an identity architect recommend to configure the requirement with limited changes to the third-party app?
Use a connected app with user provisioning flow.
Create Canvas app in Salesforce for third-party app to provision users.
Redirect users to the third-party app for registration.
Use Salesforce identity with Security Assertion Markup Language (SAML) for provisioning users.
Correct: 1
key-word: User Provisioning for Connected Apps
65. Universal containers (UC) wants users to authenticate into their salesforce org using credentials stored in a custom identity store. UC does not want to purchase or use a third-party Identity provider. Additionally, UC is extremely wary of social media and does not consider it to be trust worthy.
Which two options should an architect recommend to UC? Choose 2 answers
Use a professional social media such as LinkedIn as an Authentication provider
Build a custom web page that uses the identity store and calls frontdoor.jsp
Build a custom Web service that is supported by Delegated Authentication.
Implement the Openid protocol and configure an Authentication provider
Correct: 2, 3
66. Universal containers (UC) would like to enable SAML-BASED SSO for a salesforce partner community. UC has an existing ldap identity store and a third-party portal. They would like to use the existing portal as the primary site these users access, but also want to allow seamless access to the partner community.
What SSO flow should an architect recommend?
User-Agent
IDP-Initiated
Sp-Initiated
Web server
Correct: 2
Why not 3? Because that would imply on users accessing salesforce first while UC wants to use the existing portal as the primary site their users access.
67. Universal Containers (UC) has five Salesforce orgs (UC1, UC2, UC3, UC4, UC5) Of Every user that is in UC2, UC3, UC4, and UC5 is also in UC1, however not all users on UC5 have access to every org. Universal Containers would like to simplify the authentication process such that all Salesforce users need to remember one set of credentials. UC would like to achieve this with the least impact to cost and maintenance.
What approach should an Architect recommend to UC?
Purchase a third-party Identity Provider for all five Salesforce orgs to use and set up JIT user provisioning on all other orgs.
Purchase a third-party Identity Provider for all five Salesforce orgs to use, but don't set up JIT user provisioning for other orgs.
Configure UC1 as the Identity Provider to the other four Salesforce orgs and set up JIT user provisioning on all other orgs.
Configure UC1 as the Identity Provider to the other four Salesforce orgs, but don't set up JIT user provisioning for other orgs.
Correct: 4
dont set up JIT, because they want the least amount of effort
68. Universal containers (UC) would like to enable self - registration for their salesforce partner community users. UC wants to capture some custom data elements from the partner user, and based on these data elements, wants to assign the appropriate profile and account values.
Which two actions should the architect recommend to UC? Choose 2 answers
Modify the
communitiesselfregcontrollerto assign the profile and account.Modify the
selfregistrationtrigger to assign profile and account.Configure registration for communities to use a custom visualforce page.
Configure registration for communities to use a custom apex controller.
Correct: 1, 3
69. Which two considerations should be made when implementing Delegated Authentication? Choose 2 answers
The authentication web service can include custom attributes.
It can be used to authenticate API clients and mobile apps.
It requires trusted IP ranges at the User Profile level.
Salesforce servers receive but do not validate a user’s credentials.
Just-in-time Provisioning can be configured for new users.
Correct: 2, 4
70. Universal Containers (UC) built an integration for their employees to post, view, and vote for ideas in Salesforce from an internal Company portal. When ideas are posted in Salesforce, links to the ideas are created in the company portal pages as part of the integration process. The Company portal connects to Salesforce using OAuth. Everything is working fine, except when users click on links to existing ideas, they are always taken to the Ideas home page rather than the specific idea, after authorization.
Which OAuth URL parameter can be used to retain the original requested page so that a user can be redirected correctly after OAuth authorization?
Redirect_uri
State
Scope
Callback_uri
Correct: 2
It’s NOT Redirect_uri:
This parameter specifies the URL to which the user is redirected after authorization. It is used to direct the user back to the application, but it does not retain information about the original requested page.
71. Northern Trail Outfitters (NTO) is planning to implement a community for its customers using Salesforce Experience Cloud. Customers are not able to self-register. NTO would like to have customers set their own passwords when provided access to the community.
Which two recommendations should an identity architect make to fulfill this requirement? Choose 2 answers
Add customers as contacts and add them to Experience Cloud site.
Enable Welcome emails while configuring the Experience Cloud site.
Allow Password reset using the API to update Experience Cloud site membership.
Use Login Flows to allow users to reset password in Experience Cloud site.
Correct: 3, 4
73. A university is planning to set up an identity solution for its alumni. A third-party identity provider will be used for single sign-on Salesforce will be the system of records. Users are getting error messages when logging in.
Which Salesforce feature should be used to debug the issue?
Apex Exception Email
View Setup Audit Trail
Debug Logs
Login History
Correct: 4
74. An architect has successfully configured SAML-BASED SSO for universal containers. SSO has been working for 3 months when Universal containers manually adds a batch of new users to salesforce. The new users receive an error from salesforce when trying to use SSO. Existing users are still able to successfully use SSO to access salesforce.
What is the probable cause of this behaviour?
The administrator forgot to reset the new user's salesforce password.
The Federation ID field on the new user records is not correctly set.
The my domain capability is not enabled on the new user's profile.
The new users do not have the SSO permission enabled on their profiles.
Correct: 2
75. Universal Containers (UC) is rolling out its new Customer Identity and Access Management Solution built on top of its existing Salesforce instance. UC wants to allow customers to login using Facebook, Google, and other social sign-on providers.
How should this functionality be enabled for UC, assuming ail social sign-on providers support OpenID Connect?
Configure an authentication provider and a registration handler for each social sign-on provider.
Configure a single sign-on setting and a registration handler for each social sign-on provider.
Configure an authentication provider and a Just-In-Time (JIT) handler for each social sign-on provider.
Configure a single sign-on setting and a JIT handler for each social sign-on provider.
Correct: 1
76. Which two statements are capable of Identity Connect? Choose 2 answers
Synchronization of Salesforce Permission Set Licence Assignments.
Supports both Identity-Provider-Initiated and Service-Provider-Initiated SSO.
Support multiple orgs connecting to multiple Active Directory servers.
Automated user synchronization and de-activation.
Correct: 2, 4
77. A security architect is rolling out a new multi-factor authentication (MFA) mandate, where all employees must go through a secure authentication process before accessing Salesforce. There are multiple Identity Providers (IdP) in place and the architect is considering how the "Authentication Method Reference" field (AMR) in the Login History can help.
Which two considerations should the architect keep in mind? Choose 2 answers
AMR field shows the authentication methods used at Id.
Both OIDC and Security Assertion Markup Language (SAML) are supported but AMR must be implemented at Id.
High-assurance sessions must be configured under Session Security Level Policies.
Dependency on what is supported by OpenID Connect (OIDC) implementation at IdP
Correct: 1, 4
78. Universal Containers (UC) has a classified information system that its call center team uses only when they are working on a case with a record type "Classified". They are only allowed to access the system when they own an open "Classified" case, and their access to the system is removed at all other times. They would like to implement SAML SSO with Salesforce as the IdP, and automatically allow or deny the staff's access to the classified information system based on whether they currently own an open "Classified" case record when they try to access the system using SSO.
What is the recommended solution for automatically allowing or denying the access to the classified information system based on the open "classified" case record criteria?
Use Salesforce reports to identify users that currently owns open "Classified" cases and should be granted access to the Classified information system.
Use Apex trigger on case to dynamically assign permission Sets that Grant access when an user is assigned with an open "Classified" case, and remove it when the case is closed.
Use Custom SAML JIT Provisioning to dynamically query the user's open "Classified" cases when attempting to access the classified information system.
Use a Custom Connected App Handler using Apex to dynamically allow access to the system based on whether the staff owns any open "Classified" Cases.
Correct: 4
79. How should an identity architect automate provisioning and deprovisioning of users into
Salesforce from an external system?
Call SOAP API upsertQ on user object.
Use Security Assertion Markup Language Just-in-Time (SAML JIT) on incoming SAML assertions.
Run registration handler on incoming OAuth responses.
Call OpenID Connect (OIDC)-userinfo endpoint with a valid access token.
Correct: 2 (na real eh o SOAP devido o deprovisioning)
80. Universal Containers (UC) operates in Asia, Europe and North America regions. There is one Salesforce org for each region. UC is implementing Customer 360 in Salesforce and has procured External Identity and Customer Community licenses in all orgs.
Customers of UC use Community to track orders and create inquiries. Customers also tend to move across regions frequently.
What should an identity architect recommend to optimize license usage and reduce maintenance overhead?
Merge three orgs into one instance of Salesforce. This will no longer require maintaining three separate copies of the same customer.
Delete contact/ account records and deactivate user if user moves from a specific region; Sync will no longer be required.
Contacts are required since Community access needs to be enabled. Maintenance is a necessary overhead that must be handled via data integration.
Enable Contactless User in all orgs and downgrade users from Experience Cloud license to External Identity license once users have moved out of that region.
Correct: 3