14 Cryptography
1/8
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
9 Terms
What is the CIA triad?
Confidentiality - no unauthorised access to data
Integrity - no unauthorised change of data
Availability - service is always available to authorised users
What is symmetric key encryption?
Symmetric key encryption or private key cryptography is when sender and receiver share same private key used to encrypt and decrypt messages.
How is the cryptographic system characterised?
Type of encryption operations - substitution, transposition, product
Number of keys - single or multiple key
How plaintext is processed - block or stream
What is substitution cipher?
Sequence of bits or letters in plaintext replaced by other bits or letters. One example is Caesar cipher (replace each letter by third one after)
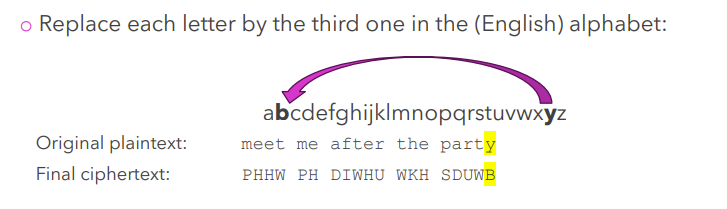
What is transposition cipher?
Transposition/Permutation cipher rearranges bits in ciphertext wihout changing letters used

What are the key ideas of modern block ciphers?
Confusion - make relationship between ciphertext and key complex
Diffusion - make statistical relationship between plaintext and ciphertext complex
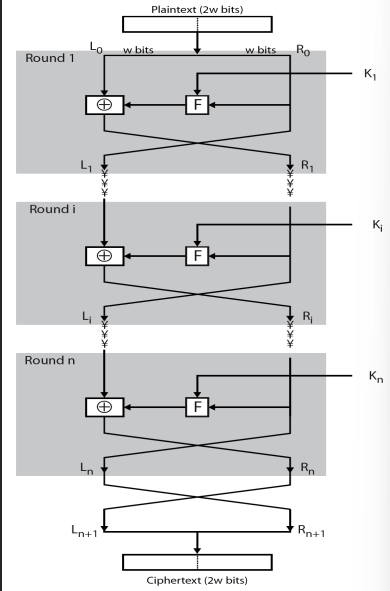
What is the feistel Cipher Structure?
Divide input into 2 halves
Perform substitution on left half of data
Perform permutation to swap 2 halves
What are some examples of product cipher?
Product cipher uses both substitution and transposition.
Data Encryption Standards (DES) in 1970 by IBM, uses 64 bits in block and key size
Advanced Encryption Standards (AES) in 1998, uses 128 bits in block and 128, 256 bits in key size
What are some examples of stream ciphers?
One time pad