CISCO CCNA introductions FINAL exam
1/155
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No study sessions yet.
156 Terms
sort these QoS priorities from highest to lowest
web page
audio conference,
financial transactions,
audio conference; financial transactions; web page
Match the description to the IPv6 addressing component
subnet ID
global routing
interface ID
This network portion of the address is assigned by the provider. | |
This part of the address is used by an organization to identify subnets. | |
This part of the address is the equivalent to the host portion of an IPv4 address. |
This network portion of the address is assigned by the provider. | global routing |
This part of the address is used by an organization to identify subnets. | subnet ID |
This part of the address is the equivalent to the host portion of an IPv4 address. | interface ID |
Characteristics cut through and store and forward
cut-through: low latency; may forward runt frames; begins forwarding when destination address is received.
store-and-forward: always stores entire frame; checks CRC before forwarding; checks frame length before forwarding.
match het juiste netwerk bij de juiste ip adressen
192.168.0.0/26;
192.168.0.128/25;
192.168.0.80/30
192.168.0.96/27;
A: 192.168.0.128/25;
B: 192.168.0.0/26;
C: 192.168.0.96/27;
D: 192.168.0.80/30
Host sends something to a remote LAN with an empty ARP cache. How to obtain destination MAC?
Send an ARP request for the MAC address of the default gateway.
New LAN must support 25 devices. Smallest subnet mask?
255.255.255.224
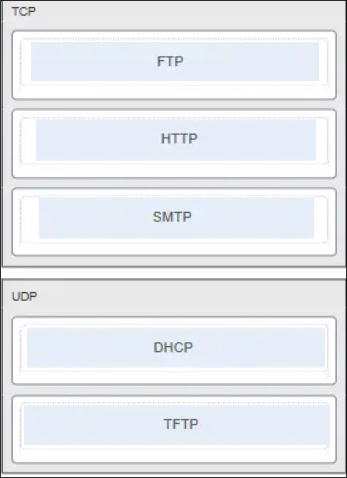
Match application protocols to transport protocols.(TCP en UDP
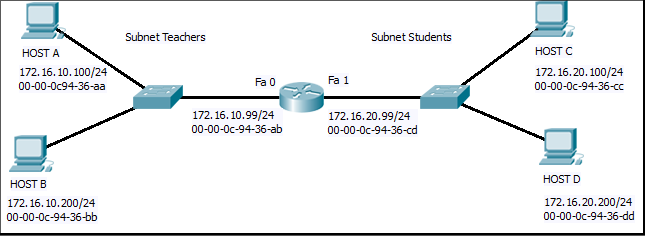
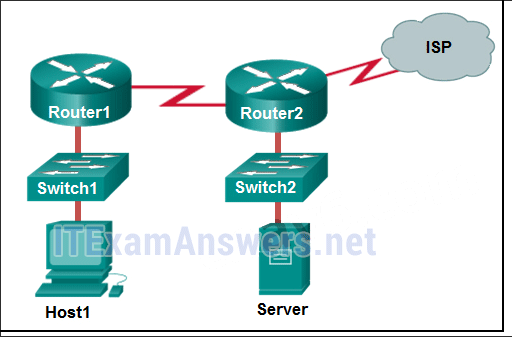
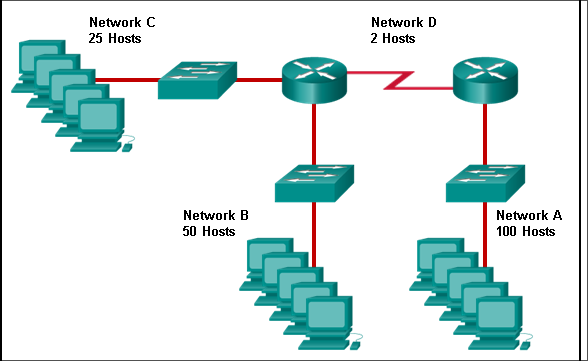
Refer to the exhibit. Host B on subnet Teachers transmits a packet to host D on subnet Students. Which Layer 2 and Layer 3 addresses are contained in the PDUs that are transmitted from host B to the router?
Layer 2 destination address = 00-00-0c-94-36-ab
Layer 2 source address = 00-00-0c-94-36-bb
Layer 3 destination address = 172.16.20.200
Layer 3 source address = 172.16.10.200
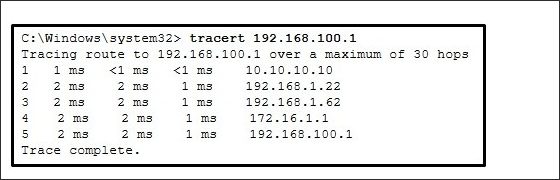
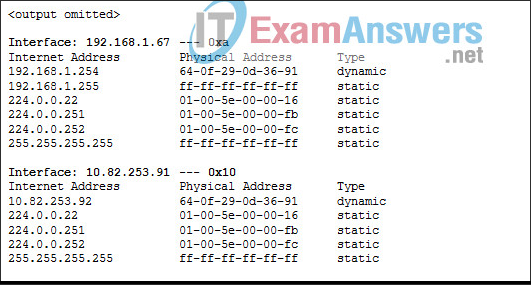
Ping output shows connectivity to 192.168.100.1. Which two are correct? (Choose two.)
This host does not have a default gateway configured.
There are 4 hops between this device and the device at 192.168.100.1.
There is connectivity between this device and the device at 192.168.100.1.
The connectivity between these two hosts allows for videoconferencing calls.
The average transmission time between the two hosts is 2 milliseconds.
There are 4 hops between this device and the device at 192.168.100.1.
There is connectivity between this device and the device at 192.168.100.1.
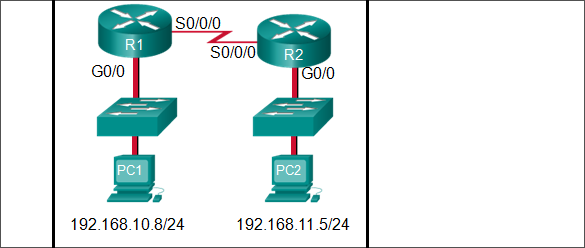
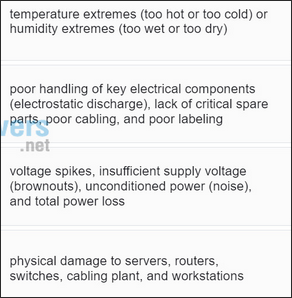
Match threat type to cause: electrical, hardware, environmental, maintenance.
electrical: spikes/brownouts/noise/power loss;
hardware: physical damage;
environmental: temp/humidity extremes;
maintenance: poor handling/ESD, lack of spares, poor cabling/labeling
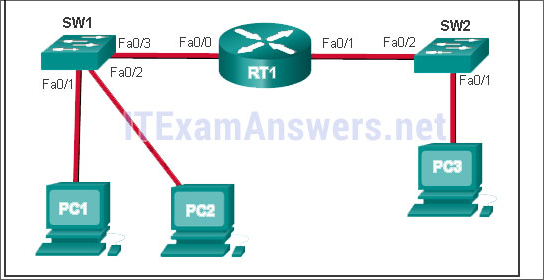
PC1 issues an ARP request because it needs to send a packet to PC2. In this scenario, what will happen next?
PC2 will send an ARP reply with the PC2 MAC address
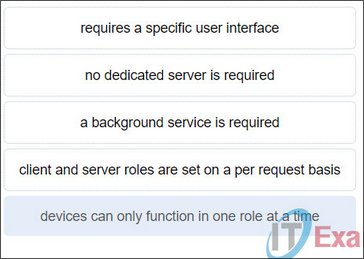
Match a statement to the related network model. P2P network vs P2P application . (Not all options are used.)
Network: no dedicated server; client and server roles are set on a per request basis.
Application: requires a specific user interface + background service required.
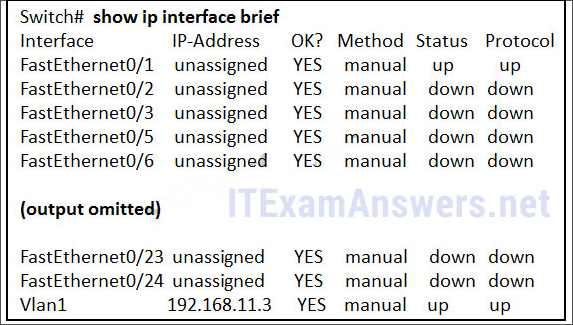
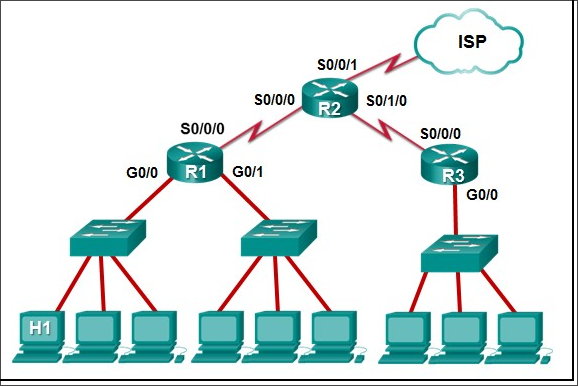
Refer to the exhibit. What three facts can be determined from the viewable output of the show ip interface brief command? (Choose three.)
Two physical interfaces have been configured.
The switch can be remotely managed.
One device is attached to a physical interface.
Passwords have been configured on the switch.
Two devices are attached to the switch.
The default SVI has been configured.
The switch can be remotely managed.
One device is attached to a physical interface.
The default SVI has been configured.
Match frame fields: to the correct functions
This field checks if the frame has been damaged during the transfer. |
This field helps to direct the frame toward its destination. |
This field is used by the LLC to identify the Layer 3 protocol. |
This field identifies the beginning of a frame. |
addressing | |
error detection | |
type | |
frame start |
addressing | This field helps to direct the frame toward its destination. |
error detection | This field checks if the frame has been damaged during the transfer. |
type | This field is used by the LLC to identify the Layer 3 protocol. |
frame start | This field identifies the beginning of a frame. |
Match the firewall function to the type of threat protection
packet filtering, URL filtering, application filtering, stateful packet inspection,
prevents access by port number | |
prevents access based on IP or MAC address | |
prevents unsolicited incoming sessions | |
prevents access to websites |
prevents access by port number | application filtering |
prevents access based on IP or MAC address | packet filtering |
prevents unsolicited incoming sessions | stateful packet inspection |
prevents access to websites | URL filtering |