2.1 Hardware and Communication
1/115
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
116 Terms
Computer architecture
It describes how a computer is theoretically put together.
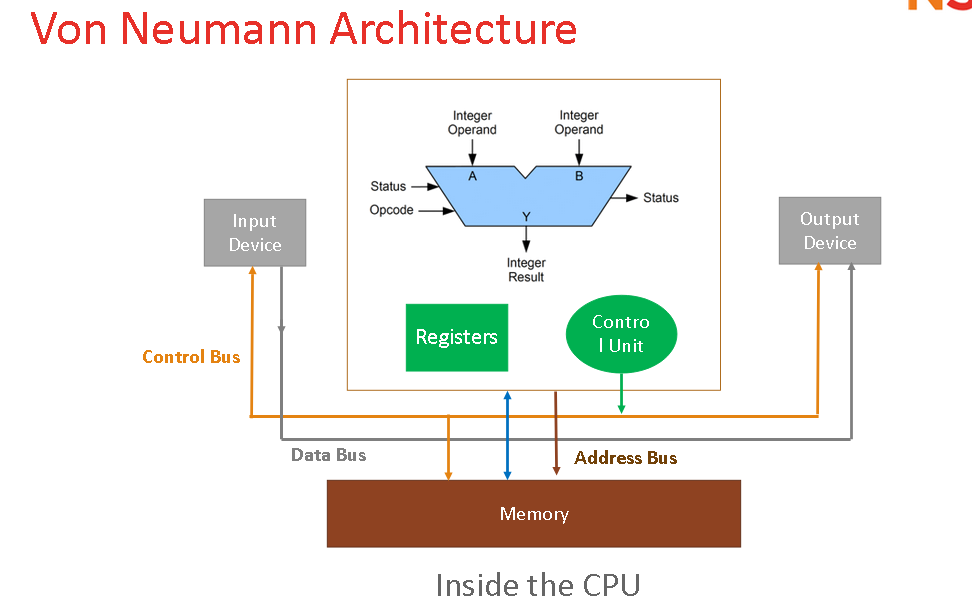
Describe the Von Neumann Machine.
The Von Neumann Machine is a computer architecture that stores both data and program instructions in the same memory. It uses a single processor to fetch, decode, and execute instructions in a linear sequence. (Input, Process, Output)
What are the advantages of Von Neumann architecture?
- It can process nearly all types of data
- cheaper than alternative methods.
What are the disadvantages of Von Neumann architecture?
Can be slower than alternative methods;
can be limited by the bus transfer rate;
doesn't always make maximum use of the CPU;
Poorly written programs can get their data mixed up as both programs and data share the same memory.
Components of the CPU
ALU, Control Unit, Registers, Memory, Input, Output
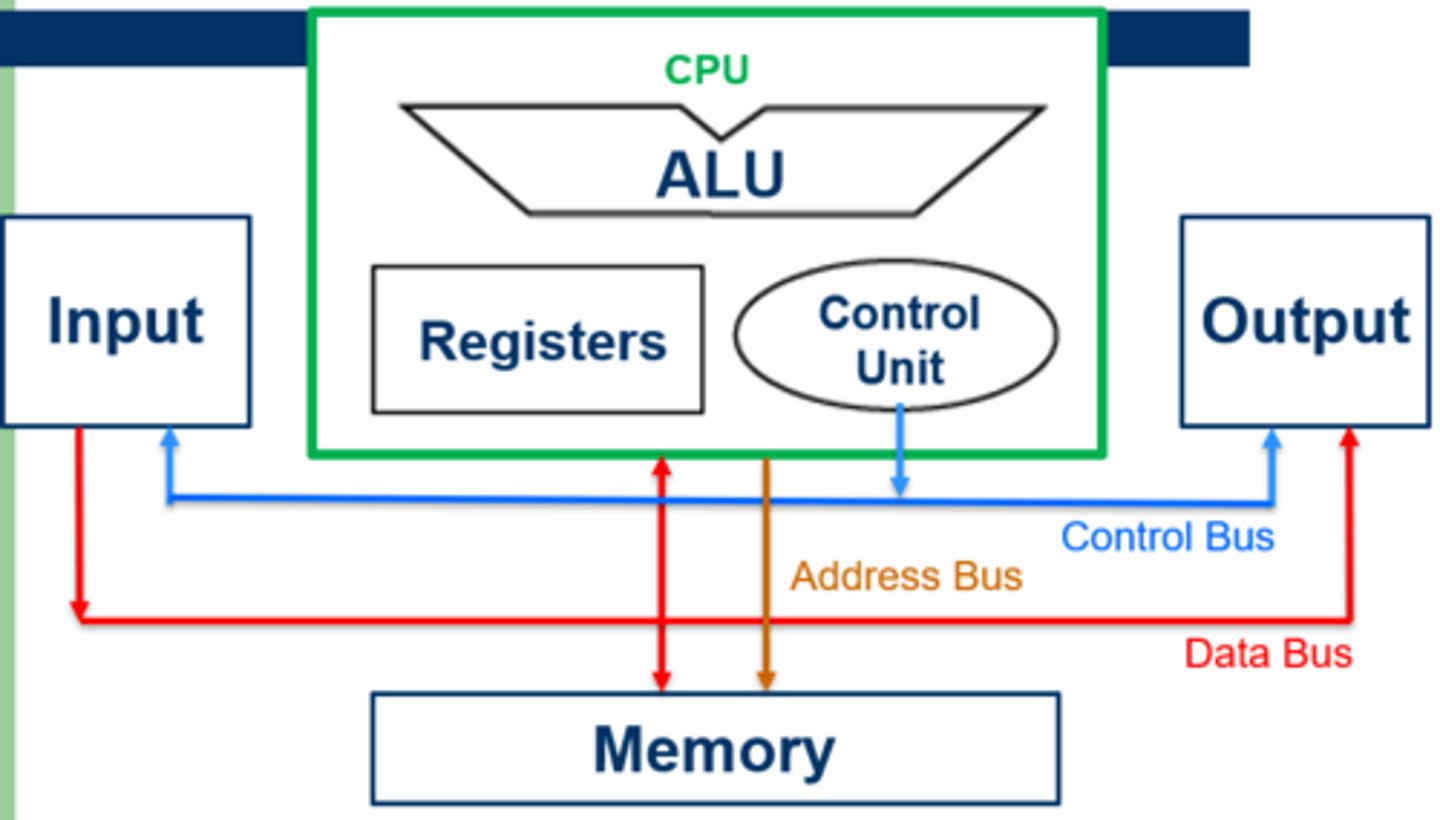
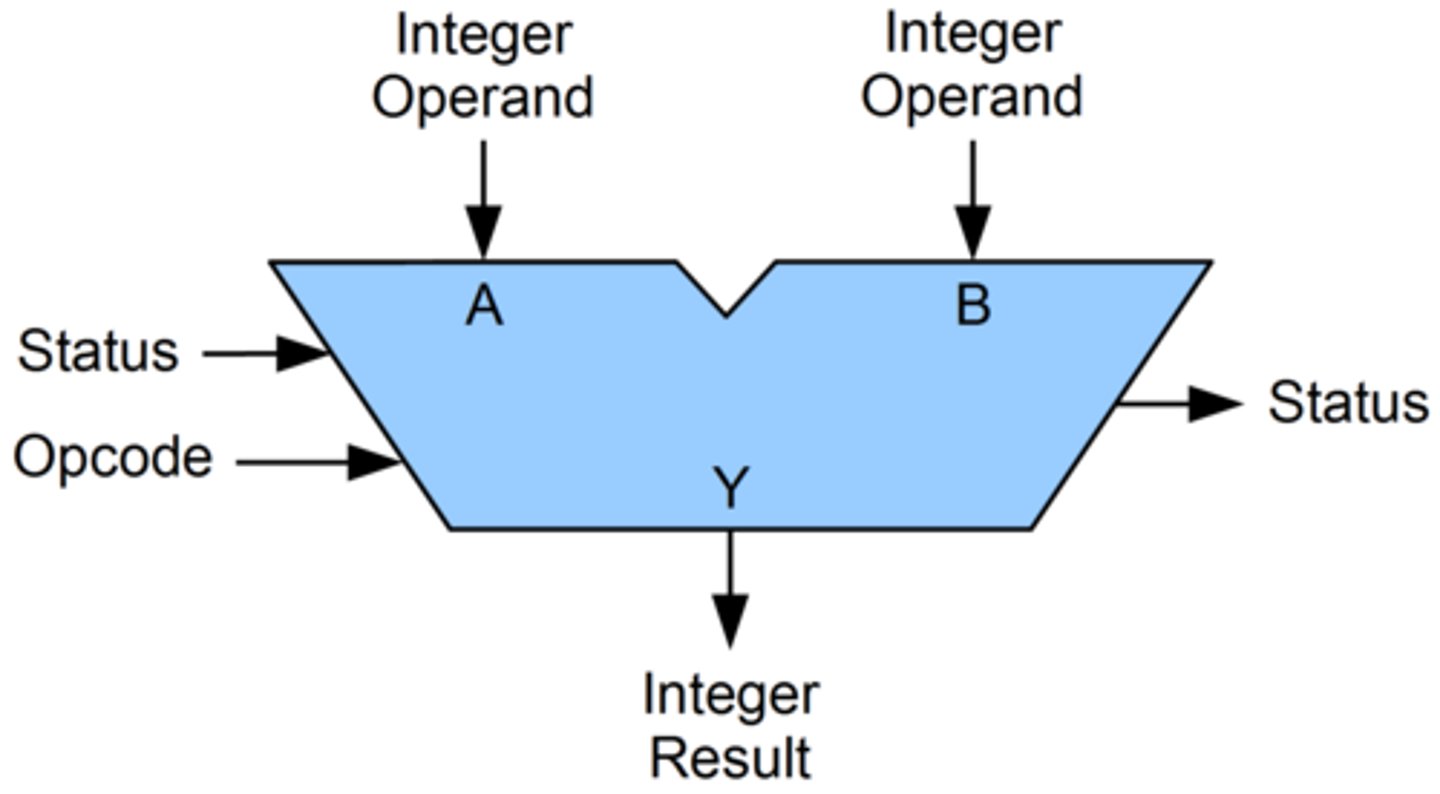
ALU
Arithmetic Logic Unit carries out calculations and logical operations in the CPU. This is the main point where inputs and outputs interact
Registers
Specialized storage locations in the CPU that hold data and instructions for quick retrieval and processing.
They provide high-speed access, as they run at the same speed as the processor, to frequently used data, improving overall processing efficiency.
They are the fastest memory and play a big role improving efficiency
Control Unit
Control unit is part of the CPU that executes instructions
Input
Input is devices used to give instructions to the computer
Output
Output is the devices used to display or produce results
Name the special registers used in the Von Neumann architecture.
PC (Program Counter)
CIR (Current Instruction Register)
MAR (Memory Address Register)
MDR (Memory Data Register)
ACC (Accumulator)
Program Counter (PC)
PC stores the location (address) of the next instruction in a program to be executed
When it is time to fetch the next instruction, the content of the program counter (PC) is loaded into the memory address register (MAR).
Current Instruction Register (CIR)
The Current Instruction Register (CIR) holds the current instruction ready for decoding and execution by the control unit.
What is opcode and operand?
Operand - the data or memory address an instruction operates on
Opcode - machine code that specifies the action performed in the instruction
Memory Address Register (MAR)
MAR temporarily stores the address of the next data or instruction in main memory. It is connected to the address bus.
This address is passed to RAM by means of the address bus.
Memory Data Register (MDR)
The Memory Data Register (MDR) holds the contents of the memory at the location stored in the Memory Address Register (MAR) temporarily after they are copied from main memory.
Data is passed in both directions through the MDR but program instructions go only one way from main memory to the CPU
The movements between CPU and MDR, MDR and main memory are made via the data bus
Accumulator (ACC)
ACC temporarily stores various pieces of data within the CPU.
All data to be processed or that has been processed, or results of calculations made by the Arithmetic Logic Unit (ALU), is temporarily stored within the accumulator.
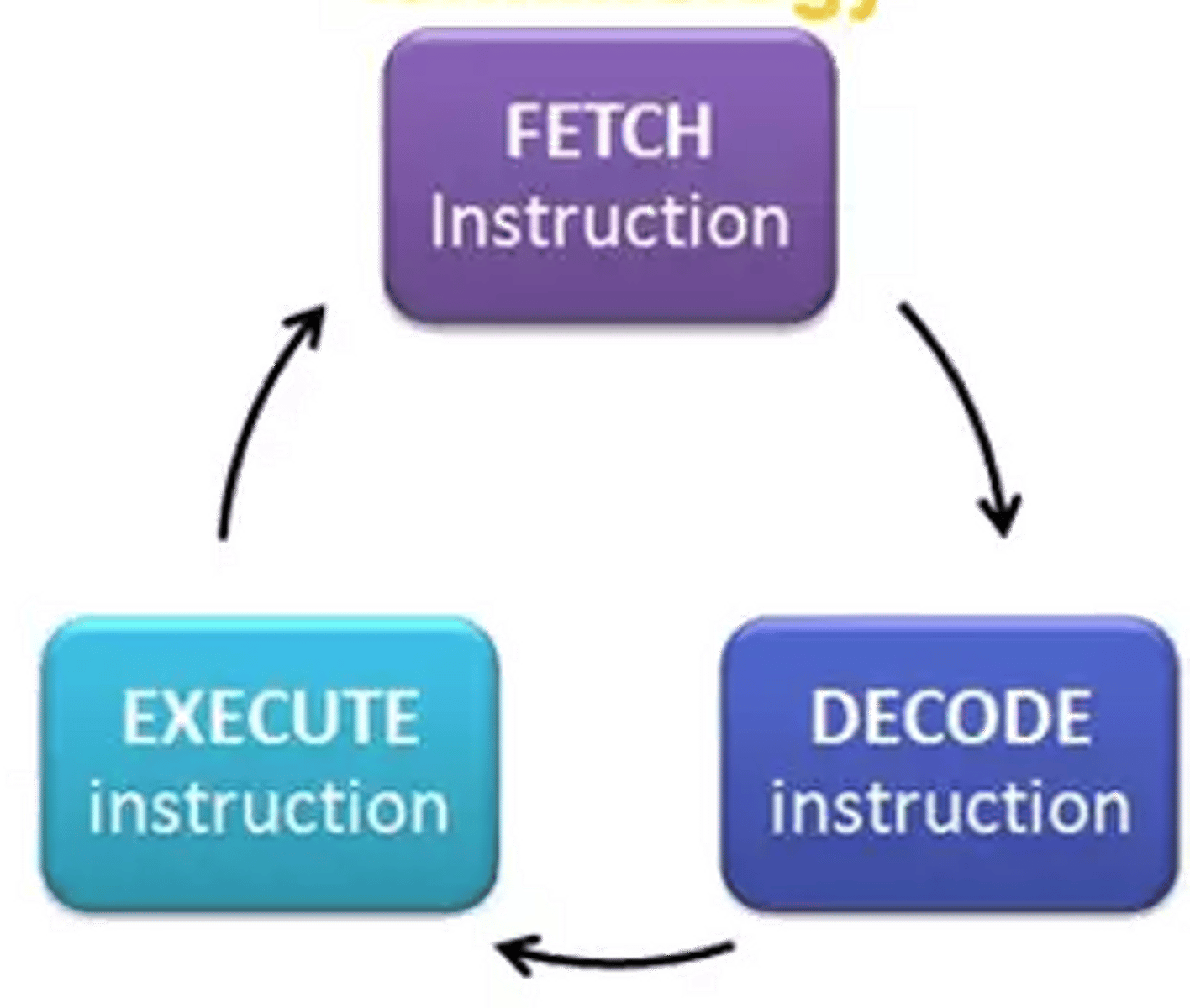
What is the role of the fetch-decode-execute cycle?
The fetch-decode-execute cycle is used to process instructions in the Von Neumann architecture. It involves fetching the next instruction from memory, decoding it, and executing it.
What is pipelining
Pipelining allows for mulitple parts of the processor to operate in parrallel, meaning the accumulator can operate while new instructions are fetched. So one instruction can be fetched while the previous one is being decoded and registered (This is the point of separate registers, advantage of FDE). This improves efficiency
Steps in the Fetch process
1. The PC stores the address of the next instruction. The instructions are held sequentially in the memory, so the value in the PC is incremented so that it will always point to the next instruction to be carried out.
2. The address of the next instruction is copied from the PC to the MAR and the address is looked up in memory
3. The data that is stored at the memory (RAM) address in the MAR is then copied to the MDR. (Could Take a number of clock cycles depending on if the instruction is in cache memory)
4. Once it is ready to be executed, the executable part of the instruction is copied into the CIR.
Steps in the Decode process
The opcode (Operation Code/Machine code) is decoded so execution can take place
The contents of the MDR is copied over to the CIR
Instructions are then decoded and executed from the CIR
While this happens new instructions are being fetched which allows for efficient use of memory and clock cycles
Fetch-Decode-Execute Cycle
1. Load the address that is in the program counter (PC) into the memory address register (MAR).
2. Increment the PC by 1 to point to the next instruction to be executed.
3. Load the instructions that are in the memory address given by the MAR into the MDR.
4. Load the instruction that is now in the MDR into the current instruction register (CIR).
5. Decode the instruction that is in the CIR.
6. Execute the instruction.
7. Reset by going to step 1.
What is a jump (JMP) command?
A jump breaks the FDE cycle and forces it to start from scratch
This happens because the next instruction fetched is not the next one in the sequence
A jump will slow down the processor due to the break in the cycle and lose the benefits of pipelining
What is the purpose of incrementing the PC?
To point to the next instruction in sequence
What is the difference between the fetch and execute processes?
Fetch: retrieves instructions
Execute: carries out instructions
What is the role of the control unit (CU)?
The control unit manages the flow of data and instructions between the CPU and memory. By:
Retrieving an instruction from memory
Decodes he instruction
It then generates control signals to send to other components of the CPU (like the ALU, and memory) or to other components through the connected Control Bus
What are the different types of memory used in computers?
Registers, RAM (Random Access Memory), Cache, and secondary storage (such as hard disks, optical disks, and solid-state storage devices)
Random Access Memory (RAM)
• RAM (Random Access Memory) holds programs and associated data when an application is running.
• RAM holds the operating system.
• RAM is composed of cheap semiconductor devices.
• A large amount of RAM allows more data and larger sections of programs to be held in electronic memory, reducing the number of slow disk operations or virtual memory
Why do we need chaching?
When a program is run it loads instructions from main memory
Memory is slower than the processor and therefore the processor will have to wait for main memory to fetch data (wastes clock cycles, reduces efficiency)
This is the von neuman bottle neck so we need cache to be a middle main as it is much faste
Cache
• Cache is small, extremely fast memory.
• Cache holds intermediate data while processing is carried out.
• Cache can be located on or very near the processor.
• Cache much faster to access than RAM main memory.
• Cache is made from logic devices, so it is more expensive than main memory.
• A large cache size reduces the need for slower access to RAM main memory.
• Cache memory attempts to solve the "Von Neumann Bottleneck" where the processor runs much faster than the memory by acting as a middleman between the main memory and the registers.
• Data and instructions that are used regularly are stored in cache and retrieved by the processor when necessary.
• When the cache is full, the least recently used data is discarded.
• Algorithms try to avoid a cache miss (when data has to be fetched from main memory rather than cache).
What are cache levels used for?
Due to high cost of cache memory, multiple levels of cache (L1, L2, L3) are used to optimize performance. Each level with varying speeds and sizes,.
What are the cache levels?
Level 1: Small and Fast embedded in the CPU
Level 2: Higher capacity but slower, on the CPU dedicated to a single or pair of cores, could be located on a separate chip to avoid being slowed down by traffic on the main bus
Level 3: Improves performance of the L1 and L2 cache and normally shared by all cores, largest and slowest cache but much faster than RAM
What is the difference between RAM and cache?
RAM is the main memory of the computer, while cache is a small, fast memory located near the processor that stores frequently used data and instructions.
What is the clock speed and how does it affect performance?
Clock speeed is the speed of the processor. It is measured in cycles per second and determines how many instructions the CPU can execute in a given time, as each instruction requires a fixed number of clock cycles. Higher clock speeds typically lead to better performance.
How many Clock Cycles are in a GHz?
One billion clock cycles. e.g. 1.8GHz is 1,800,000,000 Cycles
What other factors affect CPU performance?
Clock Speed
Threading Type (Hyper Or MultiThreading)
Number of Cores
UnderVolting - Reducing Power
(Over/Under)clocking
Cache Size
Difference between Underclocking and Undervolting
Underclocking decreases the CPU's clock speed to reduce power consumption and heat, but affecting performance
Undervolting lowers the voltage supplied to the CPU, often improving efficiency without affecting performance drastically. (Saving on Energy and Power)
What is Overclocking?
Overclocking increases the performance of the CPU by setting the clock rate above the manufacturers specified rate, which allows faster data processing and improved performance
What are some dangers of overclocking?
An Overclocked component operates outside the recomnded conditions which creates unpredicatble errors that may lead to system instability and data loss
Overclocking can void warranty and reduce life span of the CPU
It can also lead to excessive heat generation, requiring improved cooling solutions to avoid thermal damage and using more energy. (If the temperature is not regulated the component can shut down)
What is the von Neumann bottleneck
The CPU can process instructions faster than memory can supply data, which results in idle times where the CPU waits for data to be retrieved from memory
The bottleneck occurs because the same channel is being used to fetch data and instructions (It can only do 1 at a time)
This leads to the CPU waiting for memory to process instructions
What are strategies to fix the bottleneck?
Cache (Smaller, faster memory)
Parallel processing (Multi Core Processors)
The use of multiple cores means that instructions can be processed in parallel
While one core is executing instructions another can access memory
What happens in parallel processing?
Two or more processors work together to perform a single task
These are split into sub tasks called threads and then the tasks can be executed simultaneously by all processors
This reduces time taken to execute a program but it needs to be specially writen to take avantage of this
How do processors act in a multi core system?
All cores act in the same way as a single-core syste
Each processor in a multi-core system needs to communicate with each other continously, as other processors need to be aware of key tasks
When each processor has completed its task they combine results to complete the solution
What is Amdahls Law?
A technique used to find out the potential speed up of the task and allows for estimating the impact of parallel processing based on how much of a task can be parallelized versus how much must be performed sequentially.
What is the formula for Amdahls law
S=speed up P=portion that can be parallelised N=number of processors
S = 1 / ((1 - P) + (P / N))
New time = single core time/speed time
How can amdahls law assess feasibility of an investment?
High parallelisation > 70%
Moderate 50-70%
Low < 50%
High paralleisation will make it more feasable and worth it to invest in more processors
What is the purpose of parallel processing?
Parallel processing allows multiple tasks to be executed simultaneously, reducing the runtime of programs and improving performance.
In parallel processing, two or more processors work together to perform a single task, which is done by making use of cores on a processor
The task is split into smaller sub-tasks (threads).
These tasks are executed simultaneously by all available processors (any task can be processed by any processor).
This hugely decreases the time taken to execute a program, but software has to be specially written to take advantage of these multi-core systems.
What is a benefit of parallel processing?
More instructions can be processed
It decreases the time taken to execute a program
Tasks can be shared to reduce the load on individual processors and avoid bottlenecks
Disadvantages of Parallel Processing
- It is difficult to write programs for multi-core systems.
- Results from different processors need to be combined at the end of processing, which can be complex and adds to the time taken to execute a program.
- Not all tasks can be split across multiple processors.
- Concurrency introduces new classes of software bugs.
- Cannot split sequential tasks.
- Data must be up-to-date, and processing units will need to change their calculations based on the actions of other processing units.
Runtime Calculations
Determining the limiting factors of parallelization
Limitation factors of parllelisation of parallel processing in terms of runtime
Programs written specifically for parallel processing may have a certain portion of code that cannot be parallelised (serial).
What is the formula for Amdahl's law (Runtime Calculations)?
Tp = Ts(L + P/N)
Tp is parallel processing time
Ts is time using a single processor system
L is fraction of the processing which must be linear
P is fraction which can be run in parallel
N is the number of processors.
What's Voice Input?
Voice input is used to give specific instructions to the computer system and is commonly used on smartphones. The system is only listening out for certain words, meaning it uses less processing power than dictation.
(Can have difficulty with accents and background noise and cannot perform all instruction)
What's Vocabulary Dictation?
Vocabulary Dictation allows users to input data that will be processed by the computer output as a text in a document.
This is of particular benefit in mobile computing and for visually or motor impaired users.
More processing required due to analysis of the sound wave to look for all words.
What's Voice Recognition Print?
Voice print recognition analyses the pattern of a sound, digitises it, and compares it to a stored voiceprint of the user to authenticate a user as part of a security system. It is looking for an almost exact match in the sound wave. Telephone banking will often use thisf or authentication
+Incredibly hard to replicate voice so very secure
-Voice deepfakes
-Ethical issues of biometrics
pros and cons of voice input
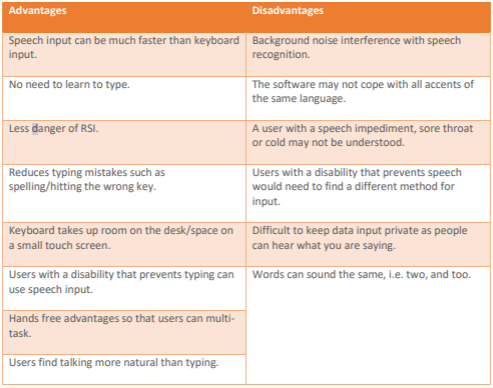
What are the different types of input devices commonly used?
Microphone, Camera, On-screen Keyboard
What's Microphone used for?
Microphones can be used as part of voice input systems in one of 3 ways
• Voice command systems allow the user to specify commands, such as opening a file
• Voice Dictation systems convert speech to text as an alternative to typing
• Security systems recognise frequency and amplitude of a particular voice, controlling access to a file or physical room.
Limitations of Microphones?
• Noisy environments
• Different accents or dialects
• Delineation (was "therefore" said, or "their four" ?
• Homophones (e.g. buy/by/bye, too/to/two)
Uses of Camera
• Facial recognition software can recognise a face in an image or video, perhaps even identifying it.
• Barcode and QR scanning software allow an alternative to entering numbers or web addresses
• Motion tracking software could activate image or video capture when something in the room moves
Limitations of camera
Cameras have finite resolution (the number of pixels)
Shutter speed ( the number of frames per second)
storage ( how much video and how many pictures can be stored)
What is an on-screen keyboard?
A virtual keyboard displayed on a screen.
It provides input functionality on the screen, reducing the need for physical input devices
It saves space and reduces the number of components that can break down
Limitations of on-screen keyboard
• When space is limited, keys can be too small, so words are mistyped
• Predictive text, auto-correct and similar technologies will not always be right.
• Often backup devices, such as voice input, needs to be included too.
Whats a touch screen?
Combine display (output) with touch-sensitive surface (input). Allow direct interaction with graphical elements. Work by sending X and Y coordiantes of the registered touch
Pros and cons of touch screen?
+Good for saving space (mobile phone)
+User friendly
-Bad for large text input
-Bad for people with visual impairments
Types of touch screen and differences
Resistive - Uses two transparetn sheets that register input when both touch (slower but more durable used for public screens used alot like fast food ordering)
Capacitive - allows for multiple touches to be recorded and uses the fact that humans can conduct electricity so each touch changes the electric field charge. (More expensive and less durable used for phones and other things)
Wha are biometric devices?
Like FaceID and Fingerprint scanners use biometric data that is unique to each person to authenticate a user. (Used on smartphones and banking)
Pros and Cons of biometrics?
+Secure due to features being unique
+Cannot forget fingerprint
-Expensive
-Could fail (Lose hand)
What are the different types of output devices commonly used?
Visual display unit (VDU), Speaker, Light-emitting diode (LED), Printer
Light-emitting diode (LED)
A single, usually very small, light on an electronic device.
A VDU`s LED can flash to indicate that its plugged in, or a phone can signal that a message has been received, without using lots of power or attracting lots of attention.
Visual Display Unit
VDU is a screen for displaying information, can be found in desktops, laptops, tablets, mobile phones, sat navs, smart TVs, digital cameras
Speaker
Outputs sound, which increasingly incorporate speech synthesis.
Many people speak search terms into their phones to have their phones "speak" results back to them, e.g. SIRI.
+Shared listening
-Connectivity issues (May need wire or bluetooth)
Printer
Printers are divided into:
• Inkjet (which uses ink)
• Laser (which burns toner onto the paper using a laser) and
• Plotter (which holds a pen in a mechanical hand, drawing accurately for technical documents such as architectural plans)
How does input and output work?
Data is captured by an input device, it is then processed by software before it is given back to the user in the form of an output.
Input → Processing → Output
Why are I/O devices improtant?
Communication with computers - Input devices allow us to interact with computers
Data collection - devices like sensors and cameras can collect physical data, which is important for things like monitoring systems and research
User experience - Designing a UI that makes efficient use of input and output devices is improtant for a good user experience
Automation and control - sensors and touch screens are used to control machines and processes, which is important for automation
Data processing - I/O devices are used to collect and present data that has been processed
Specilised fields - such as robotics, VR, and aerospace
Security - knowledge of these devices helps design a more secure system
Efficiency and optimisation - efficicent use of I/O devices is important for performance optimisation
Accessibility - certain devices can make a program more accessible (eye controls)
Innovation - new I/O development gives new ways to interact and use applications
Examples of I/O devices
MRI scanner, HUD(planes), Automated harvesting machines (farms), Biometric scanners (Banks security), Self checkout (shops)_
What are the different types of secondary storage devices?
Hard disks, optical disks, and solid-state storage devices
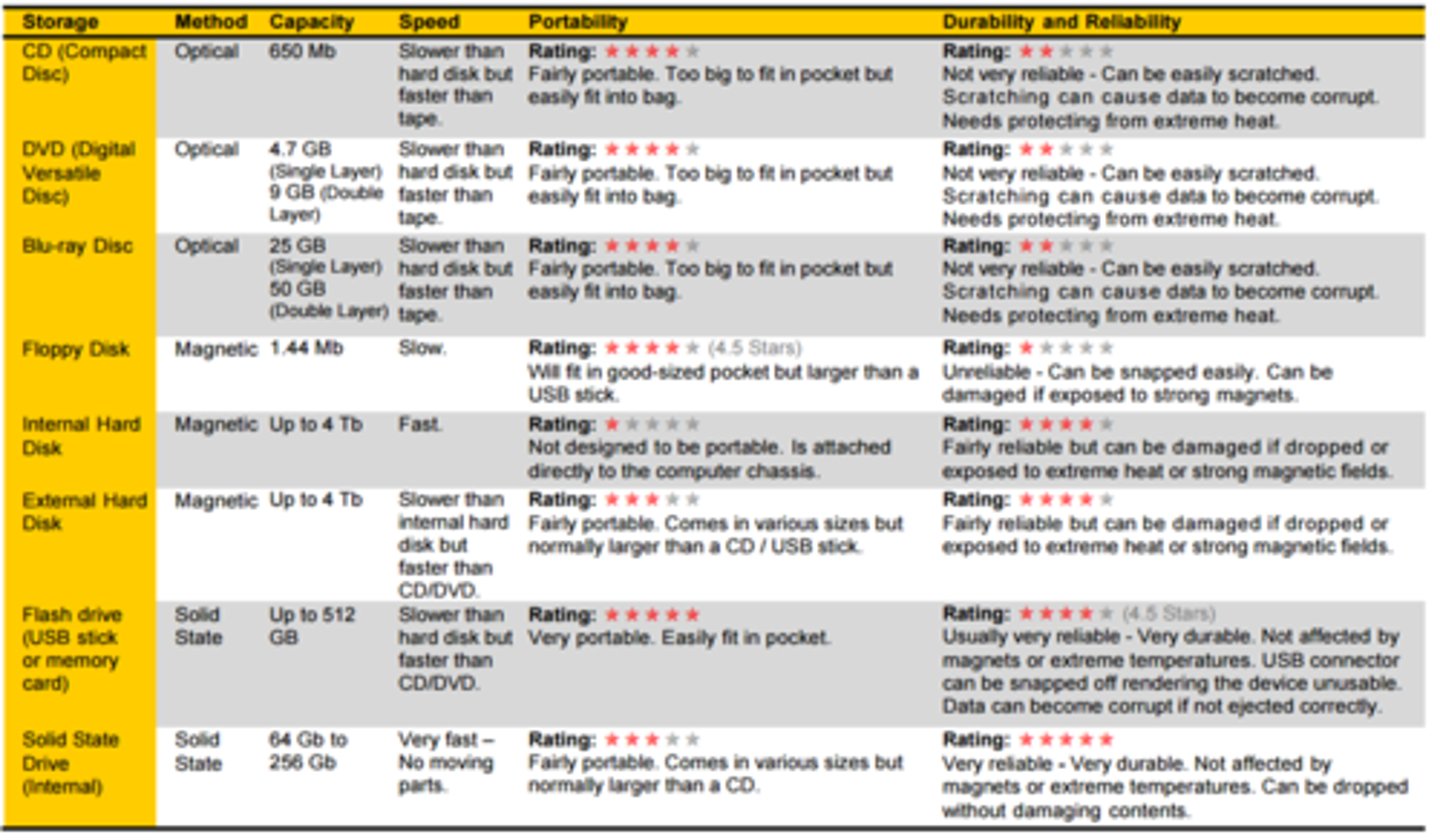
Storage Media Comparison
Optical
Optical storage media, including CDs DVDs and Blu-Ray disks, are written to and read from using lasers.
Just like magnetic disks, optical disks spin to allow the laser to read the data from the correct location.
The surface of the disk will have billions of locations in which pits can be physically burned by a laser, or not burned, to represent either a `0` or a `1`

Magnetic
Magnetic storage devices include the internal hard disk as well as floppy disks.
These disks are round and are divided into tracks and sectors:
Tracks
Clusters
Sectors
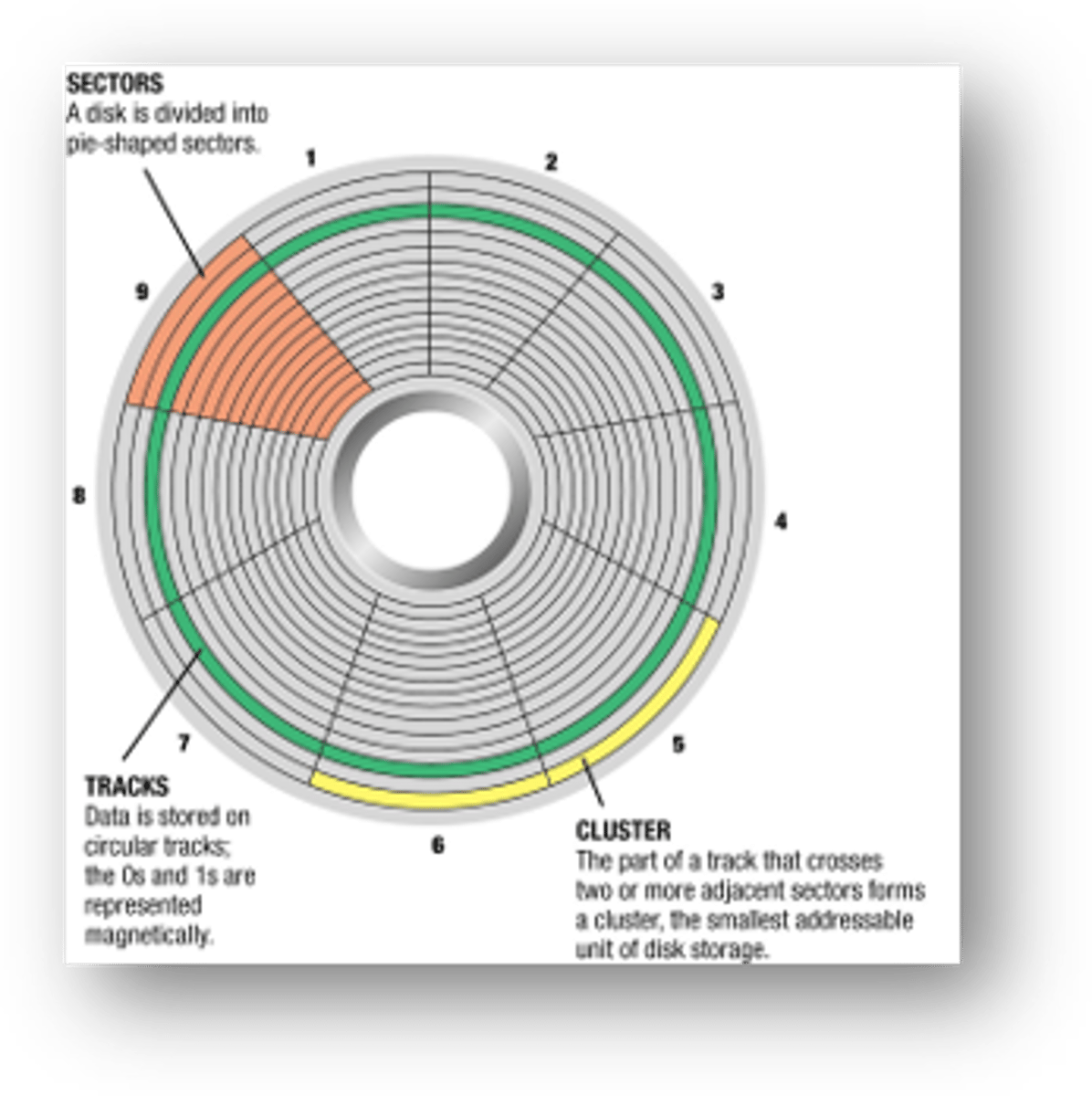
Hard Disk Drive (HDD)
A magnetic hard disk drive (HDD) is the most common form of secondary storage within desktop computers. A read/write head moves nanometres above the disk platter and uses the magnetic field of the platter to read or edit data.
Solid State Drive (SSD)
Solid state storage devices use electronic circuits, specifically transistors, to store data electronically.
They have no moving parts and they are sturdier and quieter than magnetic or optical devices.
Each 0 or 1 requires two transistors for storage.
Transistors become smaller, so they allow more storage.
A USB flash drive (USB stick) is another type of solid state storage that is used to transport files easily because of its small size.
Memory cards, like the SD card in a digital camera or a Micro SD card in a smartphone, are another example of solid state storage.

Solid State Drives (SSDs) VS Hard Disk Drives (HDDs)?
SSDs feature a non-mechanical design of NAND flash mounted on circuit boards, making them shock-resistant, while HDDs consist of various moving parts, making them open to shock and damage.
SSDs have faster data access, quicker bootup times on computers, and the ability to access all parts of the drive equally. While HDDs, whose data access speed depends on the distance of data from the read and write heads,.
SSD performance is unaffected by fragmentation, but HDDs may need to be defragmented.
SSDs use significantly less power at peak load than hard drives
SSDs energy efficiency can deliver longer battery life in laptops.
Flash-based SSDs weigh considerably less than hard drives, which makes SSDs lighter.
SSDs require very little power to operate, which translates into less heat output by the system.
Hard Disk Drives are cheaper than SSDs, which generally have a more cost-effective storage capacity.
What is the process of fragmentation?
Fragmentation occurs when the file system fills up, and file changes result in blocks no longer being contiguous as they won't fit back into the space vacated. Files are then split and physically stored on different parts of the disk.
What is the process of defragmentation?
Defragmentation is the process of consolidating data on a disk by moving all parts of files to an empty contiguous area.
What is the difference between magnetic, optical, and solid-state storage media?
Magnetic storage uses magnetic disks to store data, optical storage uses lasers to read and write data on optical disks, and solid-state storage uses electronic circuits to store data electronically.
What is a network?
A network is a collection of connected devices that can communicate and share resources with each other.
Networks consist of two or more computers, a shared network medium, which may be wired or wireless, and a communication agreement or protocol.
What are the benefits of using a network?
Networks allow devices to share resources, communicate, and exchange information.
Example: Sharing files across network, printers
Local Area Network(LAN)
LAN is a small network, usually within one building and owned by one organisation.
Wide Area Network (WAN)
WAN is a large network, that can cover a whole country or even the entire globe, and may be owned by many organisations.
What is the difference between a LAN and a WAN?
A LAN (Local Area Network) is a small network within a single building, while a WAN (Wide Area Network) is a larger network that can cover a whole country or even the entire globe.
What are the two network structures?
- Client Server
- Peer-to-peer
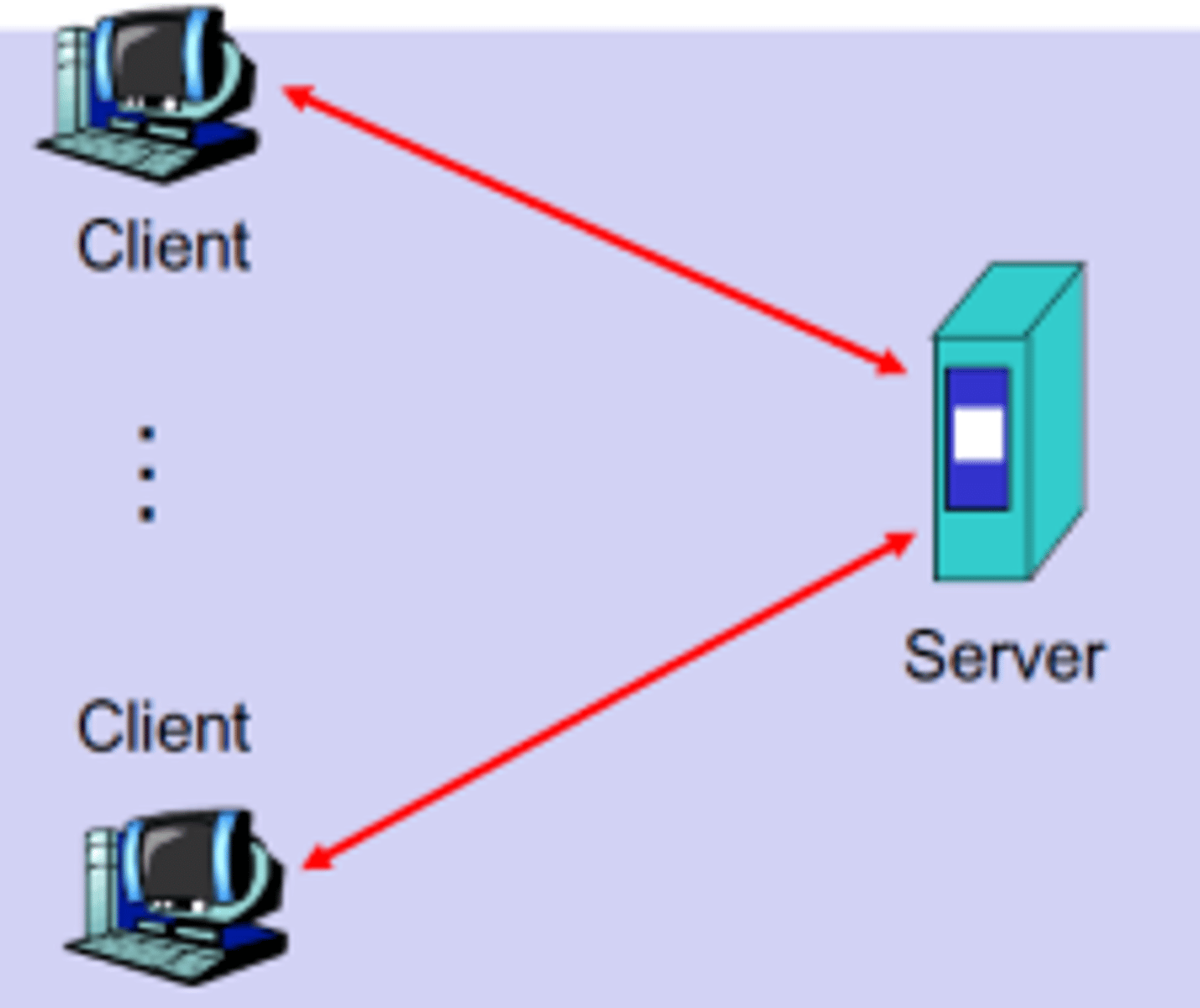
Client-Server Structure
A client-server structure provides services to anyone connecting to it.
Services, such as file storage, are made available on servers to which clients connect in order to access the services. Web servers, which host websites over the internet, are among the most common. Clients use web browsers to access the webpages held on the server.
Peer-to-Peer (P2P) Strcuture
A P2P (Peer to Peer) network is where every client has the same status as one another. Each client is referred to as a 'peer'. This structure is used in torrents, where files are shared across various computers.
Peer-to-peer networking allows very large files to be downloaded efficiently without the need for a powerful server.
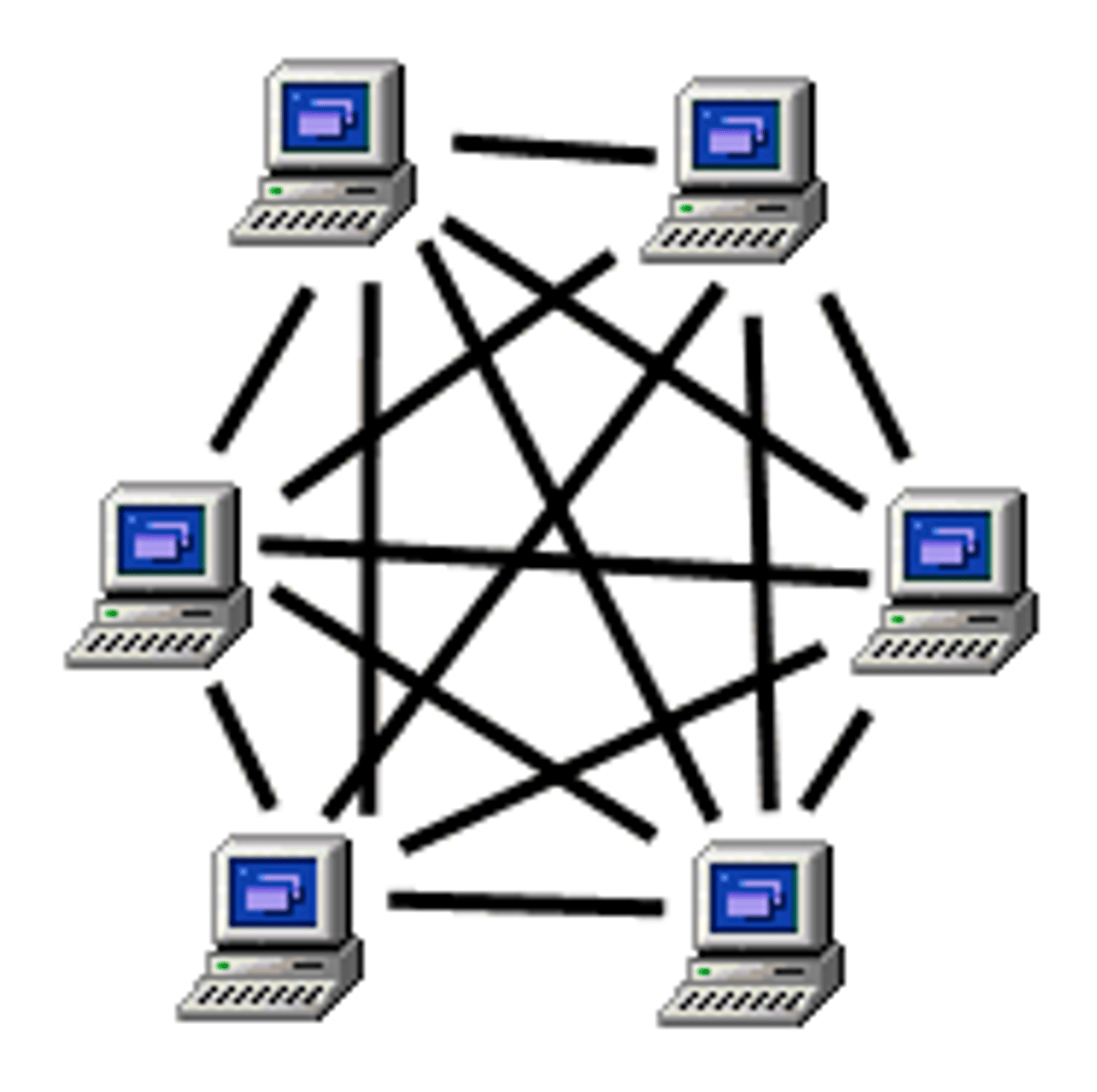
What is the difference between a client-server and a peer-to-peer network?
In a client-server network, a server provides services to clients, while in a peer-to-peer network, all computers are equal.
Networking standards
Networking standards are to make sure that the hardware and software that are made by different vendors can work together seamlessly. If there were no networking standards, it would be difficult to create networks that could share information reliably.
importance of networking standards
• Networking standards such as Wi-Fi protocols and Ethernet ensure the interoperability of networking technologies.
• The standards define the rules of communication among networked devices.
• Standards exist to help ensure products from different vendors are able to work together in a network without risk of incompatibility.
• Examples include Wi-Fi protocols and Ethernet.
What is a protocol?
A protocol is a set of rules for how devices communicate and how data is transmitted across a network.
What is the purpose of a protocol in networking?
It ensures that both the sender and receiver understand one another's transmissions.
Common Protocols
HTTP, FTP, SMTP, TCP/IP, IMAP, DHCP, UDP, RTSP