Cisco CCST Networking Practice Exam
1/12
Earn XP
Description and Tags
These flashcards cover key concepts from the Cisco CCST Networking Practice Exam, including protocols, troubleshooting commands, and networking principles.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
13 Terms
Which protocol does IPv6 use host use to resolve the MAC address associated with a destination host.
Neighbor Discovery Protocol (NDP)
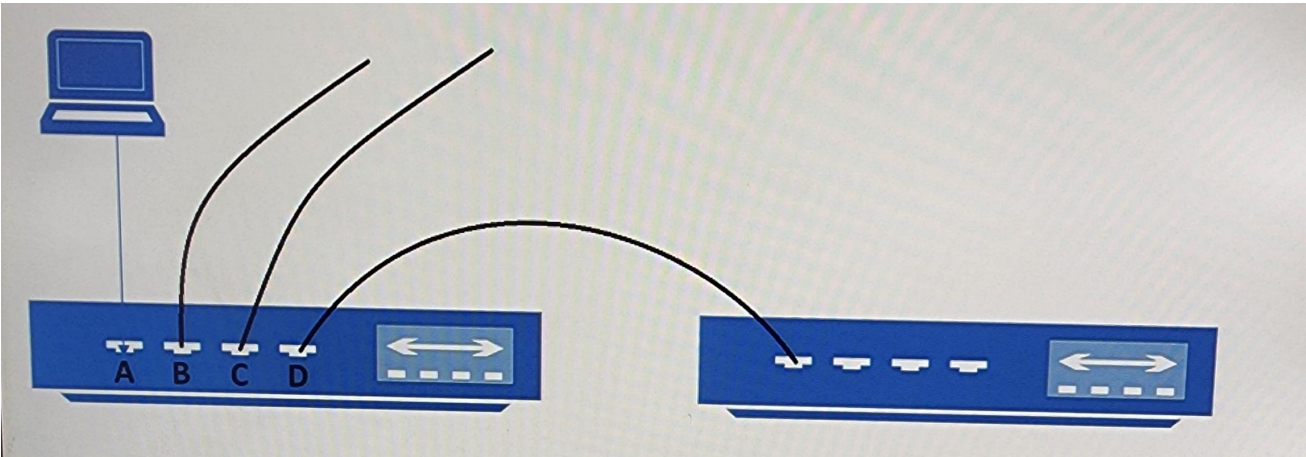
You have two switches that are connected as shown in the image.
The laptop is connected to port A on the 1st switch, The second switch is connected to port D on the first switch. The laptop sends a broadcast frame to the first switch.
• You need to identify the ports through which the broadcast frame are forwarded.
• Which ports should you identify?
B, C and D only
Match the OSI layer with the correct protocol.
OSI Layer - Application
SMTP, HTTP, FTP
Match the OSI layer with the correct protocol.
OSI Layer - Transport
TCP, UDP
Match the OSI layer with the correct protocol.
OSI Layer - Network
Router
Match the OSI layer with the correct protocol.
OSI Layer - Data Link
Layer 2 Switch
Match the OSI layer with the correct protocol.
OSI Layer - Physical
Cable, Hub, NIC
Identify the correct CIA security principle from the example.
You generate a digital signature and attach it to a message.
Integrity
Identify the correct CIA security principle from the example.
You configure 3 redundant web servers at your company
Availability
Identify the correct CIA security principle from the example.
You encrypt sensitive email message.
Confidentiality
Which network technology is not impacted by electromagnectic and radio wave interference.
Fiber
How does a firewall determine which traffic to block?
The firewall matches traffic based on source and destination IP addresses.