Network Security: Authentication and Access Control
1/111
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
112 Terms
What is the process of verifying an identity claimed by or for a system entity called?
Authentication.
What are the two steps involved in an authentication process?
Identification step and Verification step.
What does the identification step in user authentication involve?
Presenting an identifier to the security system.
What does the verification step in user authentication involve?
Presenting or generating authentication information that verifies the binding between the entity and the identifier.
What are the four means of user authentication?
1. Something the individual knows (e.g., password, PIN). 2. Something the individual possesses (e.g., cryptographic keys, smart cards). 3. Something the individual is (e.g., static biometrics like fingerprint). 4. Something the individual does (e.g., dynamic biometrics like voice pattern).
What is mutual authentication?
Protocols that enable communicating parties to verify each other's identity and exchange session keys.
What is a replay attack?
An attack where an opponent copies a message and replays it later.
What are the three types of replay attacks?
1. Simple replay of a message. 2. Replay of a timestamped message within a valid time window. 3. Backward replay without modification.
What is one approach to cope with replay attacks?
Attach a sequence number to each message used in an authentication exchange.
What is one-way authentication?
A process where the recipient wants assurance that a message is from the alleged sender.
What is the purpose of a key distribution center (KDC) in symmetric encryption?
To generate and distribute keys for secure communication between parties.
What is a suppress-replay attack?
An attack where a message is intercepted and replayed later when the timestamp becomes current.
What is Kerberos?
An authentication service developed as part of Project Athena at MIT.
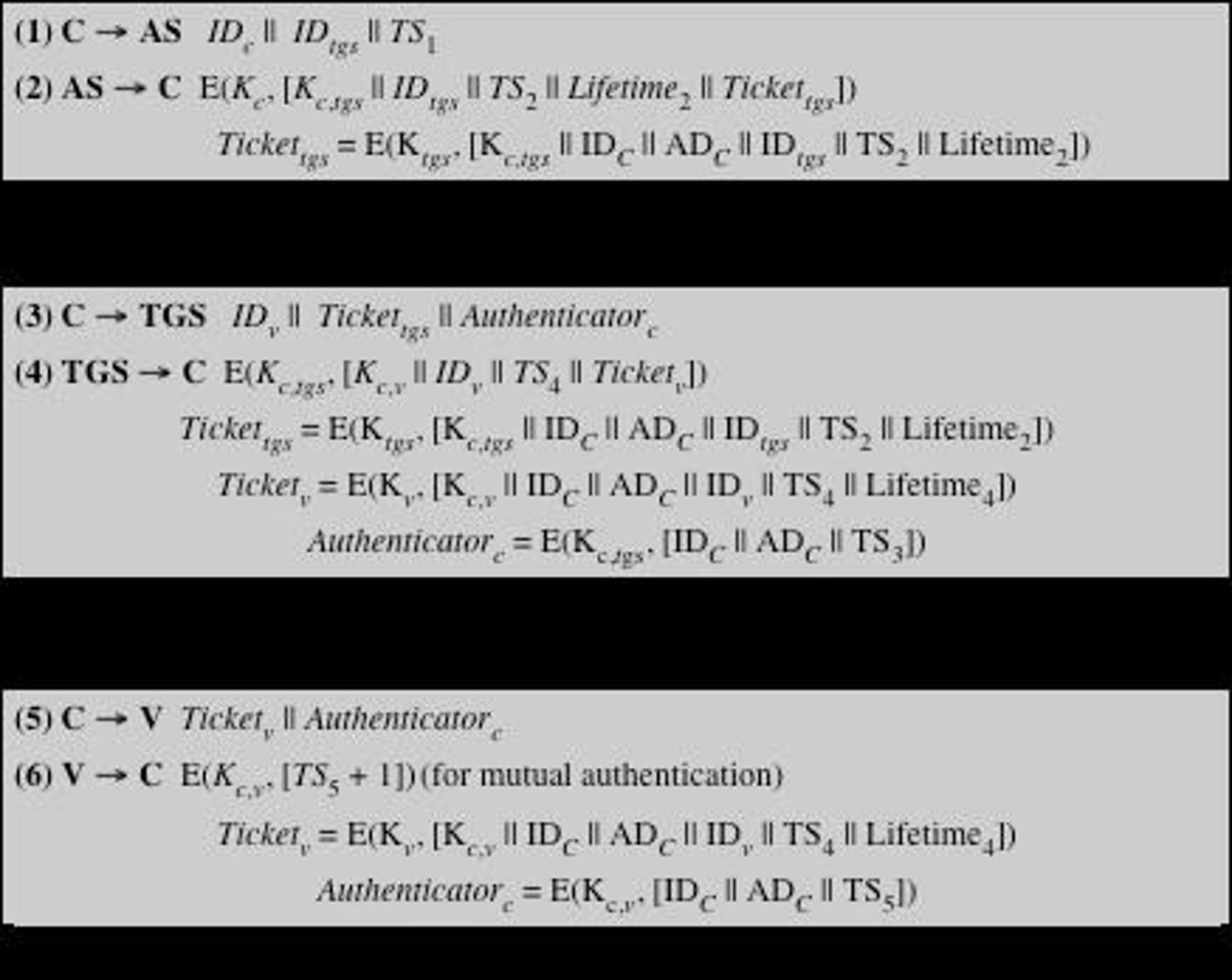
What are the requirements for Kerberos?
1. Secure. 2. Reliable. 3. Transparent. 4. Scalable.
What does Kerberos Version 4 use for authentication?
Data Encryption Standard (DES).
What is a ticket in Kerberos?
A data structure created by the authentication server that contains the user's ID and network address, encrypted with a shared secret key.
What is the role of the ticket-granting server (TGS) in Kerberos?
To issue tickets to users who have been authenticated by the authentication server.
What is a Kerberos realm?
A set of managed nodes that share the same Kerberos database.
What are the differences between Kerberos Version 4 and Version 5?
Version 5 addresses limitations in environmental shortcomings and technical deficiencies such as double encryption and session keys.
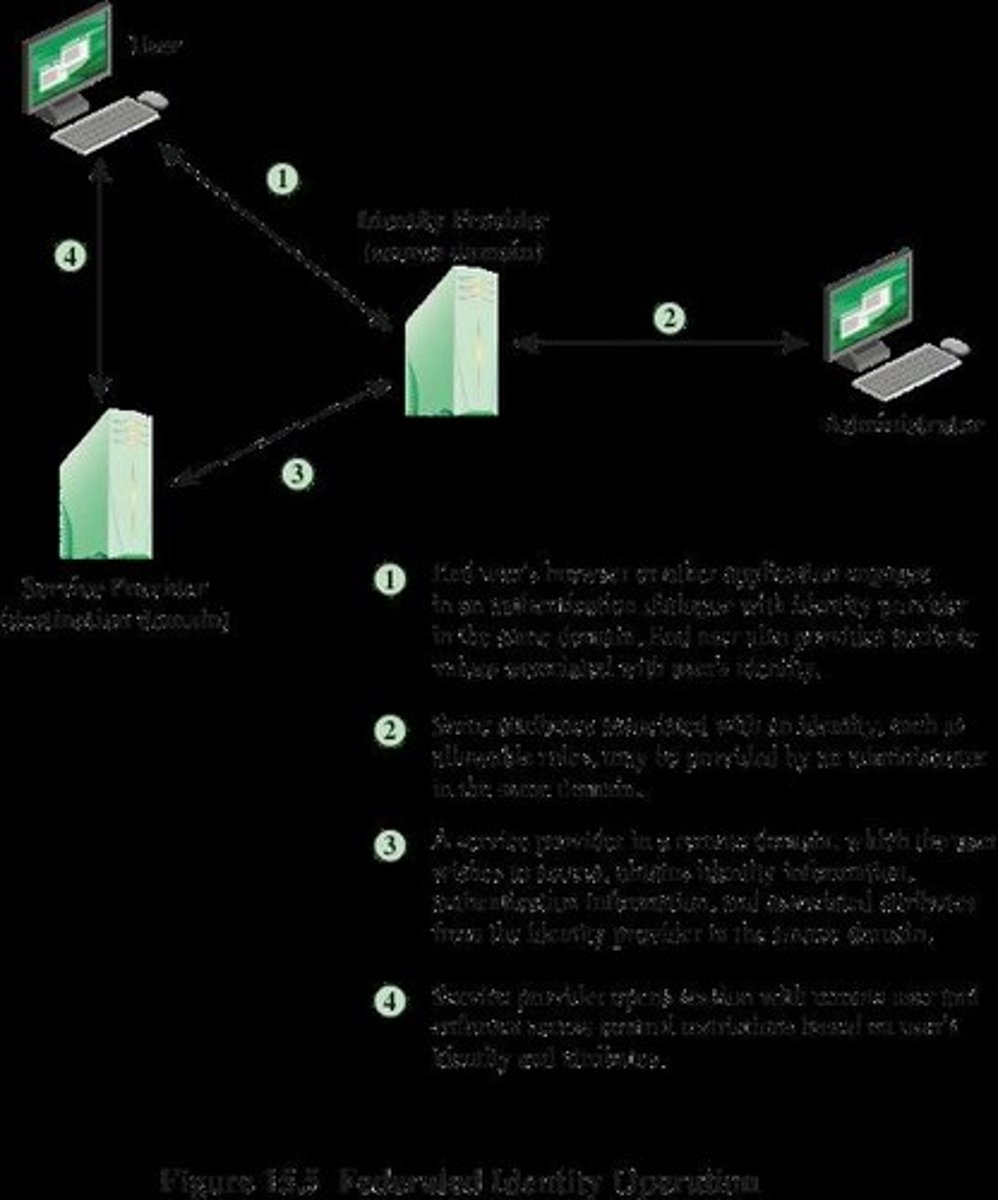
What is federated identity management?
A system that allows authorized users to access multiple applications and domains using a single set of credentials.
What does the Denning protocol require for suppressing replay attacks?
Reliance on synchronized clocks throughout the network.
What is the challenge/response method in authentication?
A method where one party sends a nonce (challenge) to another party, which must respond with the correct nonce value.
What is the main risk associated with using timestamps in authentication?
Clocks can become unsynchronized, allowing for suppress-replay attacks.
What is the main function of Kerberos?
To provide centralized authentication for users to servers and servers to users.
What is the significance of a master key in the KDC?
It is shared between each party and the KDC to secure key distribution.
What is the purpose of federated identity solutions?
To link a user's identity across multiple identity management systems, allowing secure and efficient access to different applications without separate logins.
What types of applications can users access with federated identity solutions?
Web applications, partner websites, Active Directory, and other applications.
What is the basis of how federated identity works?
It operates on mutual trust relationships between a Service Provider (SP) and an Identity Provider (IdP).
What roles do the Service Provider (SP) and Identity Provider (IdP) play in federated identity?
The IdP creates and manages user credentials, while the SP and IdP agree on an authentication process.
Can multiple Service Providers participate in a federated identity agreement?
Yes, multiple SPs can participate in a federated identity agreement with a single IdP.
What is an example of federated identity in action?
Logging into a third-party website using Gmail login credentials.
What is required for the IdP and SP to function in a federated identity system?
Mutual trust agreements between the IdP and the SP.
What is the benefit of Federated Identity regarding user access?
Users do not have to create new credentials to access multiple websites with a federated agreement, such as YouTube, Fitbit, Waze, and Picasa.
What are some key standards associated with Federated Identity?
Key standards include SAML (Security Assertion Markup Language), SOAP (Simple Object Access Protocol), and WS-Security.
What is SAML?
SAML is an XML-based markup language that enables the exchange of security information between online business partners.
What are the benefits of Federated Identity?
Benefits include enhanced security, enhanced user experience, single-point provisioning, secure resource-sharing, and cost savings.
What is Personal Identity Verification (PIV)?
PIV is a user authentication method based on the possession of a smart card, which resembles a credit card and has an electronic interface.
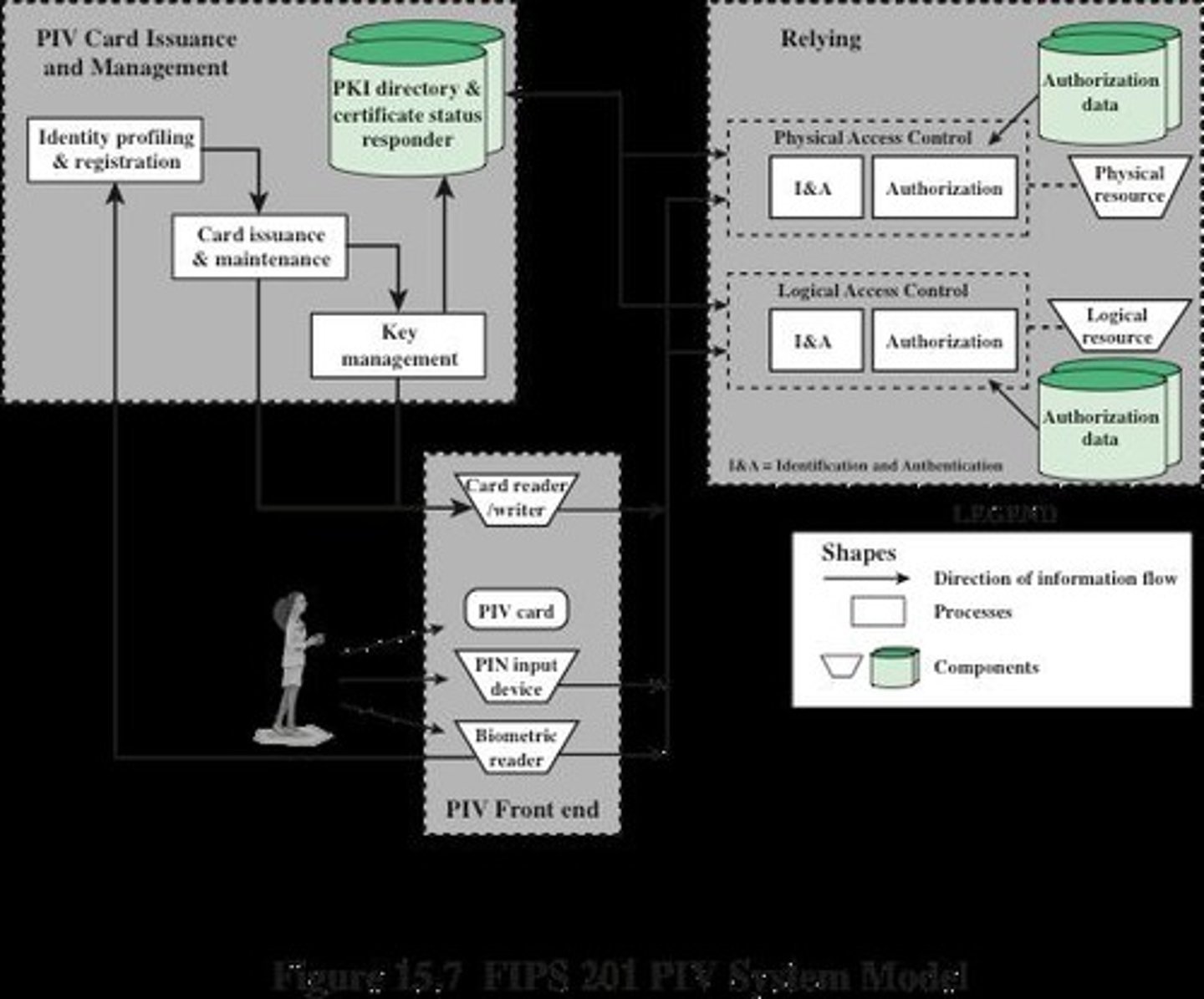
What types of memory does a smart card contain?
A smart card includes Read-only memory (ROM), Electronically erasable programmable ROM (EEPROM), and Random access memory (RAM).
What is the purpose of the Personal Identification Number (PIN) in PIV?
The PIN is required to activate the card for privileged operations.
What is the Cardholder Unique Identifier (CHUID)?
The CHUID includes the Federal Agency Smart Credential Number (FASC-N) and the Global Unique Identification Number (GUID), uniquely identifying the card and cardholder.
What is the function of the PIV Authentication Key?
The PIV Authentication Key is an asymmetric key pair and corresponding certificate used for user authentication.
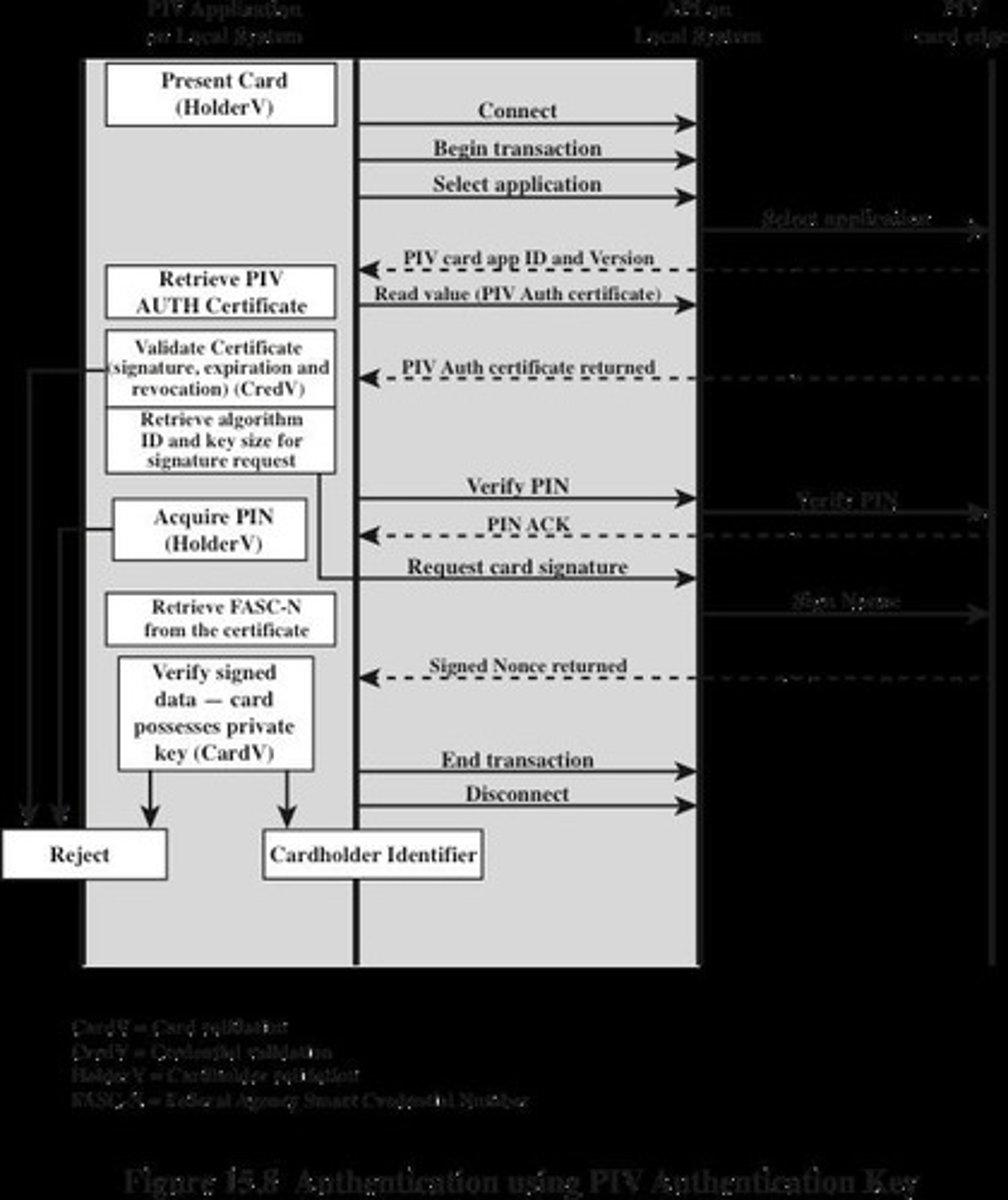
What is the role of the Card Authentication Key in PIV?
The Card Authentication Key is used to authenticate the cardholder by matching fingerprint samples to the signed biometric data element.
What is the BIO authentication mechanism?
BIO uses electronic credentials on a PIV card to authenticate the cardholder by matching fingerprint samples with signed biometric data, requiring the PIN for activation.
What is the difference between BIO and BIO-A authentication mechanisms?
BIO requires the PIN for activation, while BIO does not require the PIN and is used in environments where a low level of assurance is acceptable.
What does the PKI authentication mechanism involve?
PKI authentication uses the Card Authentication Key in a challenge-response protocol, allowing contact or contactless authentication without the holder's active participation.
What is the purpose of the Digital Signature Key in PIV?
The Digital Signature Key is an asymmetric key pair and certificate that supports document signing and signing of data elements.
What is the significance of biometric authentication in PIV?
Biometric authentication enhances security by using unique biological traits, such as fingerprints or iris images, to verify the identity of the cardholder.
What is the Asymmetric Card Authentication Key?
The Asymmetric Card Authentication Key is used for card authentication and involves an asymmetric key pair and corresponding certificate.
How does the PIV card support biometric authentication?
The PIV card supports biometric authentication through fingerprint templates, electronic facial images, and iris images.
What is the function of the Key Management Key in PIV?
The Key Management Key supports key establishment and transport using an asymmetric key pair and corresponding certificate.
What is the significance of the Random Access Memory (RAM) in a smart card?
RAM holds temporary data generated when applications on the smart card are executed.
What does the term 'secure resource-sharing' refer to in the context of Federated Identity?
Secure resource-sharing refers to the ability to share resources securely among multiple online business partners through federated identity systems.
What is the purpose of the Electronic facial image in PIV?
The Electronic facial image is used for biometric authentication to verify the identity of the cardholder.
What does the term 'message integrity' mean in the context of web services?
Message integrity ensures that the data exchanged between web services remains unchanged and authentic during transmission.
What is the role of the PIV Card Application Administration Key?
The PIV Card Application Administration Key is a symmetric key associated with the card used for managing biometric authentication.
What is the focus of Lecture 4 in CCS6224?
Securing the Local Area Network.
What are the main components of Endpoint Security?
Host-Based protection, Antivirus/Antimalware, SPAM Filtering, URL Filtering, Blacklisting, Data Loss Prevention (DLP).
What is a CAM Table Attack?
An attack where an intruder fills the CAM table of a switch, causing it to flood all traffic to all ports.
What is the result of a successful CAM Table Attack?
The switch floods all traffic, allowing the attacker to capture sensitive data.
What are some mitigation strategies for Layer 2 Security Threats?
Mitigation strategies include monitoring and limiting access to the CAM table, implementing VLANs, and using DHCP snooping.
What services does Data Loss Prevention (DLP) provide?
DLP provides detailed logging, user/administrator notifications, real-time prevention and blocking, and quarantine of confidential data.
What is the purpose of SPAM Filtering in Endpoint Security?
To identify and block unwanted or malicious email communications.
How does URL Filtering contribute to Endpoint Security?
It restricts access to harmful or inappropriate websites.
What is the role of Blacklisting in network security?
To block known malicious IP addresses or domains from accessing the network.
What are the questions to consider after a malware attack?
Where did it come from? What was the threat method and point of entry? What systems were affected? What did the threat do? Can I stop the threat and root cause? How do we recover from it? How do we prevent it from happening again?
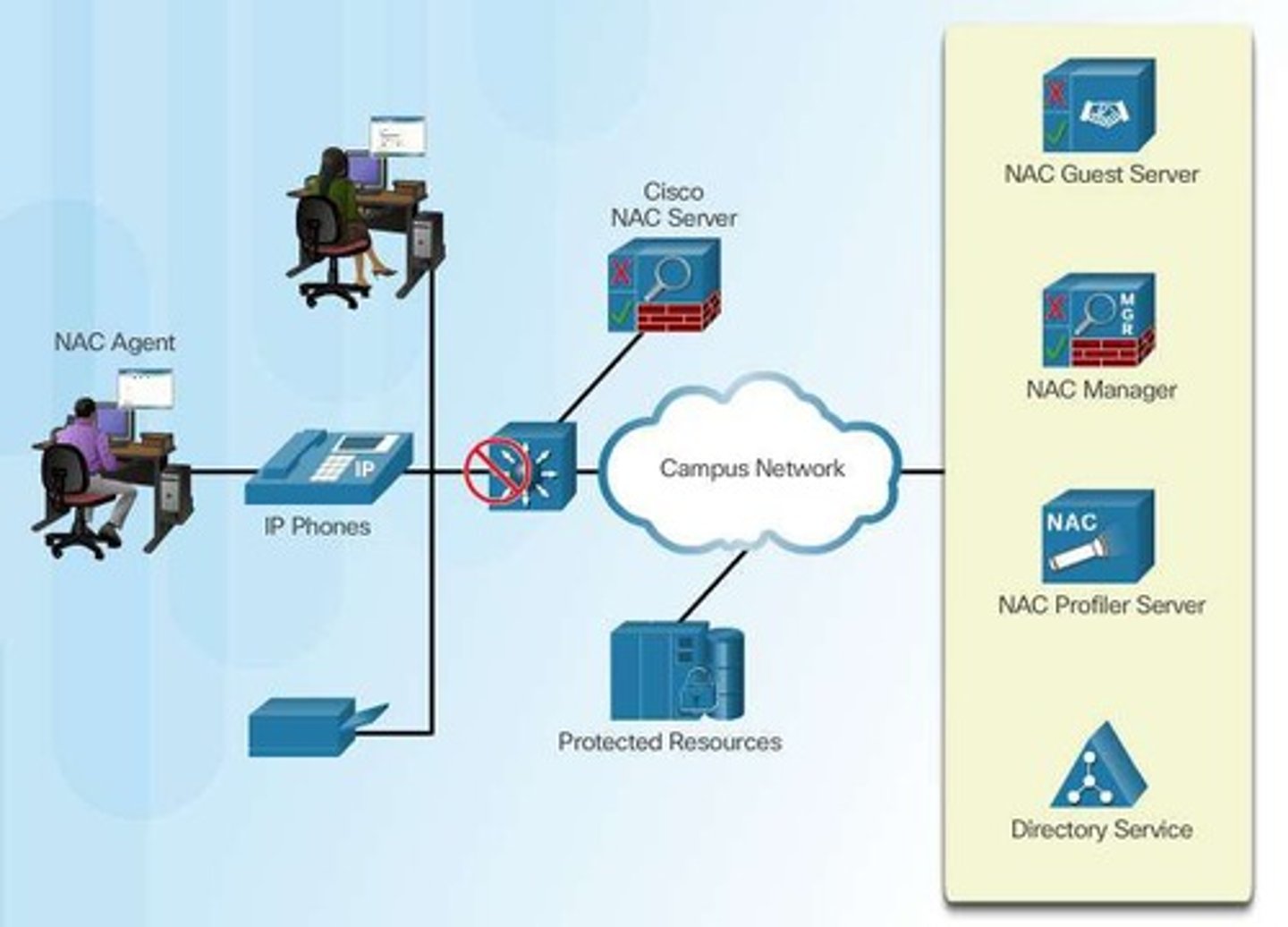
What is the function of Cisco Network Access Control (NAC)?
To enforce security policies on devices attempting to access the network.
What happens during a DHCP Attack?
An attacker can respond to DHCP requests with malicious IP addresses, leading to man-in-the-middle attacks.
What is the purpose of VLAN Attack mitigation?
To prevent unauthorized access to VLANs and protect against VLAN hopping.
What is the significance of logging in Data Loss Prevention?
It provides forensic evidence for security incidents and helps in compliance.
What is a common tool used in CAM Table Attacks?
Attack tools that can fill the CAM table, causing traffic flooding.
What is a countermeasure for CAM Table Attacks?
Port Security
What are the steps to enable Port Security?
1. Enable Port Security 2. Set maximum number of MAC addresses 3. Configure MAC addresses manually or dynamically.
What are the security violation modes in Port Security?
1. Protect 2. Restrict 3. Shutdown
What is the purpose of Port Security Aging?
To remove inactive MAC addresses from the MAC address table after a specified time.
How does Port Security work with IP Phones?
Port Security can limit the number of MAC addresses to prevent unauthorized devices from connecting.
What is a VLAN Hopping Attack?
An attack where an end station can spoof as a switch to gain access to all VLANs.
What is the default behavior of trunk ports in VLANs?
Trunk ports have access to all VLANs by default.
What encapsulation methods can be used in VLAN Hopping Attacks?
802.1q or ISL.
What is a Double-Tagging VLAN Hopping Attack?
An attack where an attacker sends frames with two VLAN tags to gain access to multiple VLANs.
What is the best way to mitigate VLAN Hopping Attacks?
Ensure the native VLAN of the trunk port is different from any user ports.
What should not be used for any VLAN configuration?
VLAN1.
What is the function of a DHCP server?
Dynamically assigns IP addresses on demand and provides configuration information.
What is a DHCP Starvation Attack?
A Denial of Service attack where an attacker leases all available DHCP addresses.
How does a Gobbler perform a DHCP Starvation Attack?
It uses a new MAC address to request multiple DHCP leases.
What is a method to mitigate DHCP Starvation Attacks?
Restrict the number of MAC addresses allowed on a port.
What happens when a rogue DHCP server is present?
It can provide incorrect IP configuration information to clients.
What is the potential problem with incorrect information from a rogue DHCP server?
Clients may receive incorrect IP addresses or configurations, leading to network issues.
What is the role of DHCP options?
To deliver additional configuration information along with the IP address.
What is the process of DHCP address assignment?
1. DHCP Discovery (Broadcast) 2. DHCP Offer (Unicast) 3. DHCP Request (Broadcast) 4. DHCP Ack (Unicast).
What is the impact of a rogue DHCP server on network security?
It can redirect traffic, perform man-in-the-middle attacks, or disrupt network services.
What is the significance of lease time in DHCP?
It determines how long an IP address is assigned to a client before it must be renewed.
What happens when there is a wrong default gateway in a network?
The attacker becomes the gateway.
What is the consequence of a wrong DNS server configuration?
The attacker becomes the DNS server.
How can an attacker exploit a wrong IP address in a network?
The attacker can perform a Denial of Service (DOS) attack using an incorrect IP.
What is DHCP Snooping?
A security feature that helps mitigate rogue DHCP server attacks by validating DHCP messages.
What is the purpose of configuring a maximum number of MAC addresses in DHCP Snooping?
To limit the number of devices that can connect to a network segment, enhancing security.
What is the process for verifying DHCP Snooping?
It involves checking the DHCP snooping database and ensuring that only valid DHCP messages are processed.
What is the function of ARP in networking?
ARP (Address Resolution Protocol) maps an IP address to a MAC address.
What is ARP Spoofing?
An attack where an attacker sends false ARP messages to associate their MAC address with the IP address of another device.
How does Dynamic ARP Inspection mitigate ARP attacks?
It uses the DHCP snooping binding table to validate ARP requests and replies.