9.1: Side Channels in Hardware
1/15
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
16 Terms
Side Channel Attacks
A method of breaking a secure system by looking at signals produced by a device whilst it’s working on something to figure out what’s happening.
Timing Attacks
Timing the amount of time that a program takes to execute to determine what values are being compared in if statements.
Preventing Timing Attacks
Ensuring code is written in a way such that every possible route takes a constant time to execute.
Often with bitwise operators - otherwise optimising compilers may give you a bit of a headache
Simple Power Analysis
A side channel analysis of voltage, showing a rough voltage drop over the resistor for every clock cycle that corresponds with what a processor is doing.
Simple Power Analysis - Example
Take a method that squares an input and multiplies an input when a bit of the key is equal to 1.
Multiplication voltage amplitude compared to square is visible
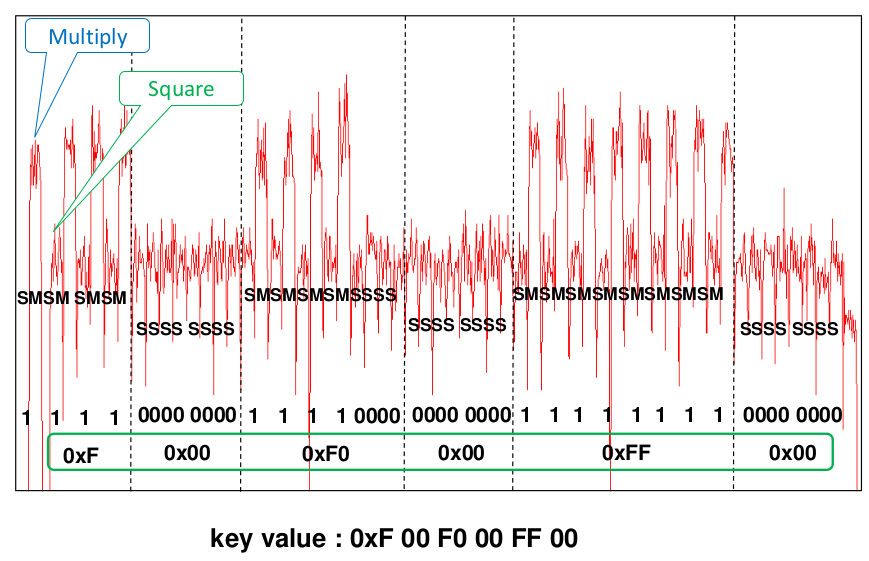
Simple Power Analysis - Prevention
Adding noise
Decreasing the signal (balance the power consumption)
Fix the algorithm
Other Possible Side Channels
Temperature
Sound
Electromagnetic Output
Photonic Emissions
etc.
AES - SPA Attack on MixColumns
Send a plaintext x, and “read” MSB(Bo) from the power trace
Higher voltage means MSBit is 1, lower means MSBit is 0
For each key candidate, compute the hypothetical MSB(B0)
Repeat with next input/trace until only one candidate remains
Repeat for each key byte separately
AES - Protection against SPA
Implement xtime as a constant
Compilers may optimise and CPUs may have a non-constant time multiplication
T-tables optimisation
AES - Timing Attack
Focus on a single byte, go over all 256 candidates, go over many (x, T) pairs - like with SPA
For each key candidate k, compute if MSBit = 1 or 0
Assign the measured time into two “heaps”, one for if MSBit = 1 and one for if MSBit = 0
Compute each heap’s average for every candidate
Find the candidate with the highest difference in averages - that’s one of the key bytes
Repeat for all key bytes
AES - Why the Timing Attack Works
When the key candidate is correct, one term in the sum is predicted correctly, so that T0^ = 0 + noise + Trest and T1^ = 1 + noise + Trest, and the difference often leans towards 1
When the key candidate is incorrect, only noise is predicted and will often lean towards 0.
Differential Power Analysis
Employs techniques of both Simple Power Analysis and Timing Attacks to potentially leak secrets.
AES - Differential Power Analysis Attack
For each candidate in k,
For each x in the plaintext,
Compute hypothetical MSBit(B0)
If MSBit(B0) is 0, put it in P0 (heap)
Else, put it in P1 (another heap)
Compute the pointwise averages of P0 and P1
Calculate the difference in averages
Find the maximum difference in averages amongst candidates - this is the key candidate byte
Differential Power Analysis - Countermeasures (AES)
Hiding amplitude - noise generation, balanced logic style…
Hiding time - random delays, dummy cycles, unstable clock…
Masking the S-Box
Differential Power Analysis - Countermeasure Limitations
Substantial area and speed overhead
Requires good randomness (difficult on embedded devices)
Partially depends on the algorithm
Can be attacked with higher-order DPA/CPA
Differential Power Analysis - System Level Countermeasures
Detect - shadow accounts, logging
Minimise impact - key diversification