Thẻ ghi nhớ: ITA | Quizlet
1/257
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
258 Terms
Which of the following statement is correct?
A. Academic research has also found that top management support is more important if task interdependence is higher.
B. Academic research has also found that top management support is less important if task interdependence is higher.
C. Academic research has also found that top management support is little important if task interdependence is higher.
A
What does JAD stand for?
A. Joint Application Development
B. Japanese Application Development
C. Joint American Development
D. Joint Application Development Team
A
In the........... , we start with the key stakeholders. We don't try to convince everybody about the new system, we start with the key stakeholders and use them to communicate why this new system is being implemented.
A. revolutionary change
B. evolutionary change
C. radical change
D. incremental change
B (câu này chị hơi phân vân giữa B và D)
Is it true if the value from the system depends on lots of users performing interdependent tasks using the system, then top management support is more important?
A. True
B. False
A
How many interations are there in RAD methodology?
A. 3 interations
B. 4 interations
C. 5 interations
D. Depend on the project
D (Khi hỏi có mấy giai đoạn thì mới trả lời là 4)
Which of the following is NOT a critical success factor for implementing Information Systems?
A Top managements support
B Employee unvolvement
C. Project champian the best pterm-people full time
D. The best technical solution
D
ln the................ , the system is adapted to the employees and the employees adapt to the new system. So, in that sense, change is recursive, adaptive- However, in the.................. approach, we need to change the root structure of the firm
A. evolutionary change/ revolutionary change
B. revolutionary change/ evolutionary change
C. evolutionary change/ evolutionary change
D. revolutionary change/ revolutionary change
A
These more rigid software development processes tend to be more successful in a more..............
A. process-oriented organization
B. traditional hierarchical organization
C. project-oriented organization
D. balance matrix organization
B
Which of the following is a correct statement?
A. Academic research has found that peer support is very important in helping with adoption of new information systems.
B. Academic research has found that peer support is little important in helping with adoption of new information systems.
C- Academic research has found that peer support is NOT important in helping with adoption of new information systems.
A
Which of the followings are essentially building a version of the product that allows people to experiment with the product, but it's not necessarily production-ready?
A. Prototypes
B. lst version of software
C. Design
D. Tested software
A
Many large IT departments use a(n) _ team that reviews and tests all applications and systems changes to verify specifications and software quality standards.
A- beta testing
B- quality assurance
C. alpha testing
D- acceptance verifier
B
Which of the following are NOT an evolution change tactics?
A. Self-improvement
B- Use insiders
C. Use current anagers, and representative employees
D- Use outsiders- Bring a new management team
D
Which of the following are NOT an evolution change tactics for change management?
A. New system adapted to capabilities of the existing employees-
B- Phased/incremental approach to mitigate risk
C- Firm milestones
D- Flexible milestones
C
The type of disclosure process in which a new bug discovery is first reported to the software vendor whose product contains the bug is known as:
(a) Responsible Disclosure
(b) Full Disclosure
(c) Market Disclosure
(d) None of the above
a
Process standardization does not imply that all business units should use the same process, and this is something that ...................often struggled with, is trying to force fit those processes into areas where they might not apply
A. process-oriented organizations
B. traditional hierarchical organizations
C. project-oriented organizations
D. balance matrix organizations
A
Which of the following statements regarding Blockchain is NOT true?
(a) Blockchain is a list of records, called blocks, which are linked using cryptography and are accessible for verification by the public.
(b) Blockchain is a distributed digital ledger in which transactions can be recorded chronologically and publicly.
(c) Traditional databases also store transaction information chronologically. But secure databases are kept under the centralized control of a host organization and maintained by IT administrators.
(d) Blockchain is designed as a centralized solution so that a single entity can control it and validate all transactions.
d
Which of the following statements is NOT true?
(a) Ethereum is an example of a blockchain
(b) The cryptocurrency used in Ethereum are called Bitcoins
(c) Hyperledger is an example of open-source blockchain
(d) The cryptocurrency used in Ethereum are called Ethers
b
After spending a week getting to know the members of the team, including their strengths and weaknesses, and what has worked well (and not so well) for this particular team in the past, Roark realizes that one theme keeps recurring: the team has particularly weak communications skills. Which method is Roark least likely to use, given that he knows about the disadvantages of each method?
A- Structured analysis
B. Agile/adaptive methods
C. Object-oriented analysis
D- Rapid application development
B
Which of the following statements is true?
(a) In blockchains, any change or new transactions can be realized only by adding a new block of information to the historical transaction records.
(b) In blockchains, one doesn't erase or override the past records, it adds transactions in a chronological order to a growing list.
(c) Unlike the ledgers maintained by banks, Bitcoin's blockchain is replicated on networked machines around the world; hence it is called a "Distributed Ledger".
(d) All of the above.
d
Which of the following is NOT true for Bitcoin mining?
(a) The technology uses a pair of keys for encryption
(b) The private key is used by the sender to encrypt the payment message
(c) Miners use the sender's public key to validate that the payment request was indeed made by the sender
(d) Miners will use the public key to compute the private key of the sender
d
Which of the following statement is true?
(a) The process of adding blocks to a blockchain is computationally expensive, and even more so to change blocks further back in the chain.
(b) Any miner trying to add a new block of data is required to provide a cryptographic proof called Proof of Work.
(c) To produce the Proof of Work, a miner will have to perform multiple rounds of hashing with the data of the previous block such that the resultant hash value begins with a specified number of zeros.
(d) All of the above.
d
Which of the following is an application area for smart contracts?
(a) Supply chains are often inefficient because of paper-based systems and need for multi-party approvals, validation cost, potential for loss and fraud. Smart contracts can provide a secure, accessible digital version to all parties on the blockchain to automate contracts and payment.
(b) Peer-to-peer buying and selling of goods and services (e.g., in electricity smart grids and ridesharing services) can benefit from smart contracts executed between various parties participating in the blockchain.
(c) Buyers and sellers of insurance can agree on and claim reparation compensation using smart contracts.
(d) All of the above.
d
Suppose your organization needs multiple people to store and update transaction records while ensuring immutability. Which one should you choose?
(a) Traditional database
(b) Blockchain
b
Suppose the requirements that your organization has in regards to storing transaction information can be met with either a traditional database or a blockchain. Which one should you choose?
(a) Traditional database
(b) Blockchain
a
Suppose your organization needs to store transaction data that should be kept private, immutable, verifiable, but also control who can read and write to it in order to maintain scalability. What should you choose?
(a) Traditional database
(b) Permissioned blockchain
(c) Public blockchain
(d) None of the above
b
Which of the following statements is true?
(a) A blockchain's technology and process ensure truthful-reporting and provides incentives for participation.
(b) Cryptography principles implement validation of digital signatures, security, and immutability in a blockchain.
(c) A blockchain's distributed realization and public accessibility helps overcome censorship.
(d) All of the above.
d
Which of the following is very inflexible?
A. waterfall model
B. agile model
C. incremental model
D. RUP model
A
The system implementation approach also differs between evolutionary and revolutionary change. In the............ , we take a phased incremental approach to implement the new system because we have things that are going fairly well
A. evolutionary change
B. revolutionary change
C. radical change
D. incremental change
A
Revolutionary change is the change that challenges the status quo and accomplishes fundamental change in the values, norms, work practices, and structures?
A. True
B. False
A
Evolutionary change is the change that complies with the current values, norms, skills, structures and incentive systems?
A. True
B. Fale
A (chắc chắn 100%)
Who is in a sense a translator from the business world into the software developers or implementers who need to write or configure the software?
A. Designer
B. BA
C. Project manager
D. Developer
B
Completion of vision in the magic quadrant refers to whether a ERP vendor/provider has a good understanding of the industry to provide ERP features that meets their future needs.
A. True
B. False
A
If my company has many specialized and sophisticated business processes, and is operating in a business environment causes rapid changes to business needs, what type of ERP should I shortlist based on the magic quadrant?
A. Leaders
B. Challengers
C. Visionaries
D. Niche Players
a
Using a work breakdown structure (WBS) allows one to manage a project as one large task.
A. True
B. False
B
If I run a simple business that does not have complicated business processes and is not subjected to rapid changes in the business environment, I should shortlist ERPs from the _________ quadrant.
A. Leaders
B. Challengers
C. Visionaries
D. Niche Players
d
If a company buys all its ERP module from a single vendor, it is said to be pursuing a
A. Best of Suite Strategy
B. Best of Breed Strategy
C. All of the above
a
What are the advantages of using a Best of Suite Strategy?
A. Less risks in term of system integration as the modules are from the same vendor
B. Less costly implementation cost as there is less integration complexity
C. It provides the best features across all ERP offerings
D. A and B only
d
What are the advantages of using a Best of Breed Strategy?
A. Less risks in term of system integration as the modules are from the same vendor
B. Less costly implementation cost as there is less integration complexity
C. It provides the best features across all ERP offerings
D. B and C only
c
In the opening case of Target's ERP implementation, what were the bad managerial decisions made that led to a failed outcome?
A. Top management decided to pursue an aggressive and tight implementation timeline.
B. When populating the ERP system, mid-managers utilized the benchmark figures from the US operations to forecast the sales demand in Canada
C. Appropriate checks and balances are not in place, leading store managers to turn off auto-replenishment feature in the system.
D. All of above
d
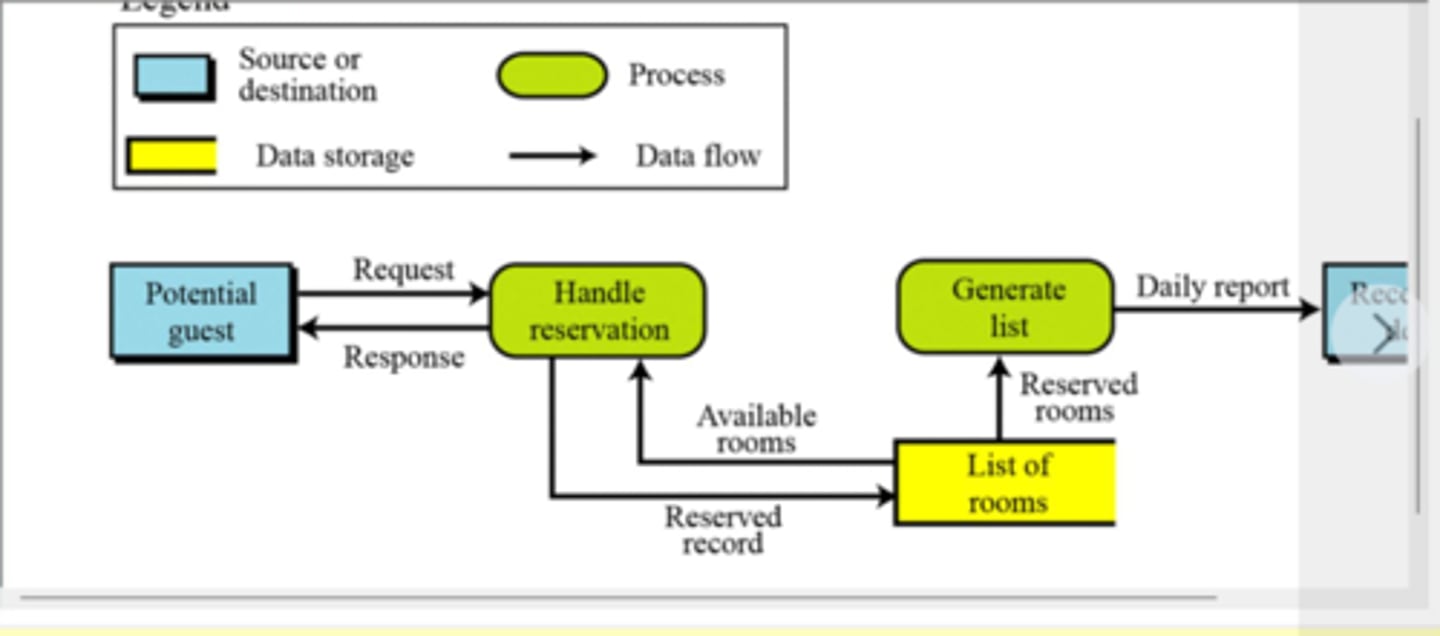
Below is an example of................... ?
A. Context diagram
B. Data flow diagrarn
C. Swim lane díagram
D. Entity relationship diagram
B
Change Management is:
A. People side of technology project
B. A systematic approach to dealing with change
C. Only appropriate for ERP-related projects
D. A and B only
d
When assessing the possible areas of changes during an ERP implementation, it is important to consider elements of
A. People
B. Process
C. Technology
D. All of above
d
Constant communication of project benefits to the users and a clear illustration of milestones are useful change management techniques for keeping motivation levels high during ERP implementation.
True
False
T
Workers do not need time to adjust to newly implemented ERP if they are well-trained to use the new system prior to its launch.
True
False
F
What are indicators of ERP implementation success?
A. On time implementation
B. On budget implementation
C. On scope implementation
D. All of above.
d
A small company with small amount of capital that has finished implementing a small scale ERP system. The consulting team concludes that there are little risk of of go-live problems as the system does not involve complex interdependencies due to its small scale. What might be a good approach in the rollout of this system?
A. Big Bang
B. Phased Approach
a
If users have invested significant time and effort to learn and master using the current system, they are more likely to resist the implementation of a new system:
A. True
B. False
A
In which of the following phases, BA will contribute to the job?
1. Identify the problem
2. Calculate project value
4. Draft an approach
4. Create the plan
A. Plan
B. Analyze
C. Design
D. Implement
B
A large company with operations in multiple countries has just finished upgrading its legacy system to an Oracle ERP system. The consultant team believes that the risk of go-live problems can be subtantial, given that there are multiple interdependencies across business units. What might be a good approach in the roll out of this system?
A. Big Bang
B. Phased Approach
b
A retail company has zero experience with ERP implementation. They have hired an external consultant to help them with the implementation of SAP. The retail company is very amendable to the recommendations provided by their consultants. What role should the consultants take on, in general?
A. Foot soldiers
B. Commanders
C. Diplomats
b
A client company wanted to implement a large scale ERP system. The project scope appears to be highly uncertain and the client does not seem to know what features are to be included in the final deliverable. What would be a good pricing model to use here when charging the client?
A. Fixed Price
B. Time and Material
b
Businesses can use virtualization technology to:
1 / 1 point
(a) Improve efficiency
(b) Lower cost
(c) Provide faster maintenance
(d) All of the above
d
Does lT Governance lead to IT business alignment and IT business alignment leads to superior firm performance?
A. True
B. False
A
Why does the opex model (such as pay-as-you-go) work for the cloud providers?
1 / 1 point
(a) It allows them to generate a steady source of revenue over time from their clients
(b) It allows them to offer freemium model to potential clients who can try out the service without significant commitment
(c) It allows them to offer any available resources on-demand and charge based on usage
(d) All of the above
d
Which of the following is used to distribute incoming requests among various servers that form a computer cluster?
1 / 1 point
(a) Hypervisor
(b) Load balancer
(c) Database
(d) None of the above
b
Which of the following statements is NOT true for web applications?
1 / 1 point
(a) Software runs on the web app provider's server
(b) They can be accesses using a client's web browser
(c) Even if client machines can fail, the data and applications can be still accessed from another client device
(d) Requires virtualization of the client's machine
d
Which of the following is an example of a hypervisor?
1 / 1 point
(a) VMware ESXi
(b) Citrix Xenserver
(c) Microsoft Hyper-V
(d) All of the above
d
Which is the core technology behind "cloud computing"?
1 / 1 point
(a) HTTP
(b) Virtualization
(c) Thin clients
(d) Remote Desktop
b
Google's cloud platform offering is a:
1 / 1 point
(a) Public cloud
(b) Private cloud
(c) Hybrid cloud
(d) None of the above
a
Which kind of infrastructure will you prefer if you are operating a business in which some applications have to comply with strict regulatory compliance requirements on data security, while others require automated scalability and load balancing?
1 / 1 point
(a) Fog computing
(b) Private Cloud
(c) Public Cloud
(d) Hybrid Cloud
d
You are the CIO of a company that wants to create a new software application that would require customizing the operating system for optimal performance. What kind of cloud service are you basically looking for?
1 / 1 point
(a) SaaS
(b) PaaS
(c) IaaS
c
What kind of estimate will be used to decide whether this project is worth pursuing?
A. An order of magnitude estimate.
B. Budget estimate
C. The definitive estimate
D. Schedule Estimate
A
Which of the following statements is true for data centers?
1 / 1 point
(a) Datacenters with fully connected topology improves host-to-host capacity
(b) Blade servers in a rack are interconnected using the TOR switch
(c) Hardware maintenance on a server in a datacenter can be performed without interrupting the software applications because of virtualization
(d) All of the above
d
Which of the following statements is NOT true?
A. Different wireless technologies occupy different frequency bands.
B. WiFi is a wireless technology that offers higher data speed but lower coverage area than cellular network technology
C. Wireless technologies that offer high data speed/rate also offer greater coverage area
D. None of the above
C
Which of the following statements is true about base stations in a cellular network?
(a) Base stations provide coverage over the area of a cell
(b) Base stations will use different frequencies in adjacent sectors
(c) Adjacent base stations participate in the handover process of ongoing mobile conversations
(d) All of the above
d
Suppose an airport is using RFID tags on ventilation units for monitoring and reporting of their functional status, PDAs for technicians, and SAP Mobile Asset Management software. Which of the following activities can be achieved using these solutions?
1 / 1 point
(a) Inspectors can easily check the status of the units from the ground without having to get up and manually inspect them, thus increasing operational efficiency.
(b) Automatic reporting from the ventilation units will improve error-free reporting and safety of the building.
(c) Automatic reporting also serves as evidence for genuine repairs
(d) All of the above
d
Which of the following will be most useful for enabling wider usage of QR codes?
1 / 1 point
(a) Include built-in QR scanner app in the smartphones
(b) Encourage creation of ad-supported third-party apps for QR code scanners
(c) Encourage creation of QR code scanning app by individual vendors
(d) None of the above
a
Which of the following statements is NOT true about WiFi networks?
1 / 1 point
(a) WiFi operates in an unlicensed spectrum band
(b) WiFi and cellular networks use the same set of frequencies
(c) WiFi is an example of Wireless Local Area Networks (WLAN)
(d) All of the above
b
Which of the following statements is NOT true about femtocells?
1 / 1 point
(a) When registered mobile phone users arrive under coverage area of a femtocell, they switch over from the cellular network to femtocell automatically
(b) When mobile phone users leave the coverage area of a femtocell, they switch over from the femtocell to a cellular network seamlessly
(c) Existing WiFi or DSL routers can be upgraded to a femtocell without the need for any new hardware
(d) All of the above
c
Which of the following pairing of technology to its coverage area is mismatched?
1 / 1 point
(a) Bluetooth - Wireless Personal Area Network (WPAN)
(b) GSM - Wireless Wide Area Network (WWAN)
(c) WiFi - Wirelss Metropolitan Area Network (WMAN)
(d) CDMA - Wireless Wide Area Network (WWAN)
c
Which of the following is the primary technology used in a mobile payment system like Apple Pay?
1 / 1 point
(a) Near Field Communication (NFC)
(b) QR code
(c) Radio Frequency Identification (RFID)
(d) None of the above
a
Users involved in the development of the information system is important because.............
A. It affects productivity outcomes such as time and budget goals and project quality
B. It affects productivity outcomes such as time and budget goals and project deliverables
C. It affects productivity outcomes such as time and budget goals
A
A shopping mall plans to send targeted offers to customers connected to their WiFi network. Which type of data about the customer will be most valuable to send these offers?
1 / 1 point
(a) Time of day
(b) Geolocation
(c) Weather
(d) None of the above
b
Which of the following issues cannot be addressed effectively with flat rate pricing of network bandwidth?
A. There is a large differential between peak and off-peak hour demand
B. Some users are consuming a disproportionate amount of bandwidth in peak time
C. Some applications are poorly designed and consume too much bandwidth
D. All of the above
D
Denial of service (DOS) security attacks are intended to compromise a system's _______.
1 / 1 point
(a) Confidentiality
(b) Availability
(c) Integrity
(d) Authenticity
b
Which of the following statements is true for malwares?
1 / 1 point
(a) They are computer programs that can infect other programs
(b) Many of them can propagate by attaching themselves to files and emails
(c) They may not always do outright damage
(d) All of the above
d
Which of the following techniques system administrators use to reduce the risk of password hacking?
1 / 1 point
(a) Preventing users from using alphanumeric passwords
(b) Enforcing a cap on the number of password retries at login before the account gets locked
(c) Encouraging usage of easy to remember dictionary words as passwords
(d) All of the above
b
A good BA is involved in all phases with the strongest contributions coming during the implement phase?
A. True
B. False
B
Which of the following statements about basic encryption techniques NOT true?
1 / 1 point
(a) The key used in Caesar cipher should be kept private between the sender and the receiver
(b) The key used in Caesar cipher should be made publicly available to allow the receiver to decrypt the message
(c) The keys used in one-time pads need to be kept private between the sender and the receiver
(d) The keys used in one-time pads are a pre-selected sequence of random numbers
b
Which of the following statements about private key cryptography is true?
1 / 1 point
(a) The same key is used by both the sender and the receiver to encrypt and decrypt a message
(b) The sender uses one key to encrypt a message and the receiver uses another key to decrypt it.
(c) The sender and the receiver do not have to agree upon a shared key in advance
(d) All of the above
a
Which of the following statements is true for public key cryptosystem?
1 / 1 point
(a) A secret message should be encrypted using the public key of the sender and decrypted using the private key of the receiver
(b) A secret message should be encrypted using the private key of the sender and decrypted using the public key of the receiver
(c) A secret message should be encrypted using the private key of the sender and decrypted using the public key of the receiver
(d) A secret message should be encrypted using the public key of the receiver and decrypted using the private key of the receiver
d
In case of digital signatures, which of the following statements will be true? (Digital signatures are not meant to be secret messages, instead they are used to demonstrate that the message must have originated from a particular sender who signed it).
1 / 1 point (quizlet giới hạn từ nên rút bớt)
(a) The message will need to be encrypted using the sender's private key. Anyone can then use the sender's public key.....particular sender.
(b) The message will need to be encrypted using the sender's public key. Anyone can then use the sender's private key .... particular sender
(c) The message will need to be encrypted using the sender's private key. Anyone can then use the sender's private key .... by that particular sender.
(d) The message will need to be encrypted using the sender's public key. Anyone can then use the sender's public key ...... by that particular sender.
A
Which of the following statements is NOT true about these cyber defense systems?
1 / 1 point
(a) Honeypots are legitimate parts of the site that are actually isolated and monitored, and act as traps for attackers
(b) Honeypots can be used to learn about organization's security weaknesses
(c) Intrusion detection systems cannot look inside the contents of the data packets, and therefore only use traffic filtering rules.
(d) None of the above
c
Which of the following should be practiced to prevent confidential data loss from cyberattacks?
1 / 1 point
(a) Store the encrypted data and the encryption key at different locations
(b) Use a two-factor access control
(c) Limit third-party access to the internal network
(d) All of the above
D
User participation do not affect productivity outcomes such as time and budget goals and project quality such as functionality that meets user requirements- True or False?
A. True
B. False
B
Which of the following methodology favor individuals and interactions over processes and tools, working software over documentation, responding to change over following a plan?
A. Spiral
B. Waterfall
C. RUP
D. Agile
D
Below is example of.....?(Câu này có cái hình)
A. Context diagram
B. Data flow diagram
C. Swim lane diagram
D. Entity relationship
diagram
A
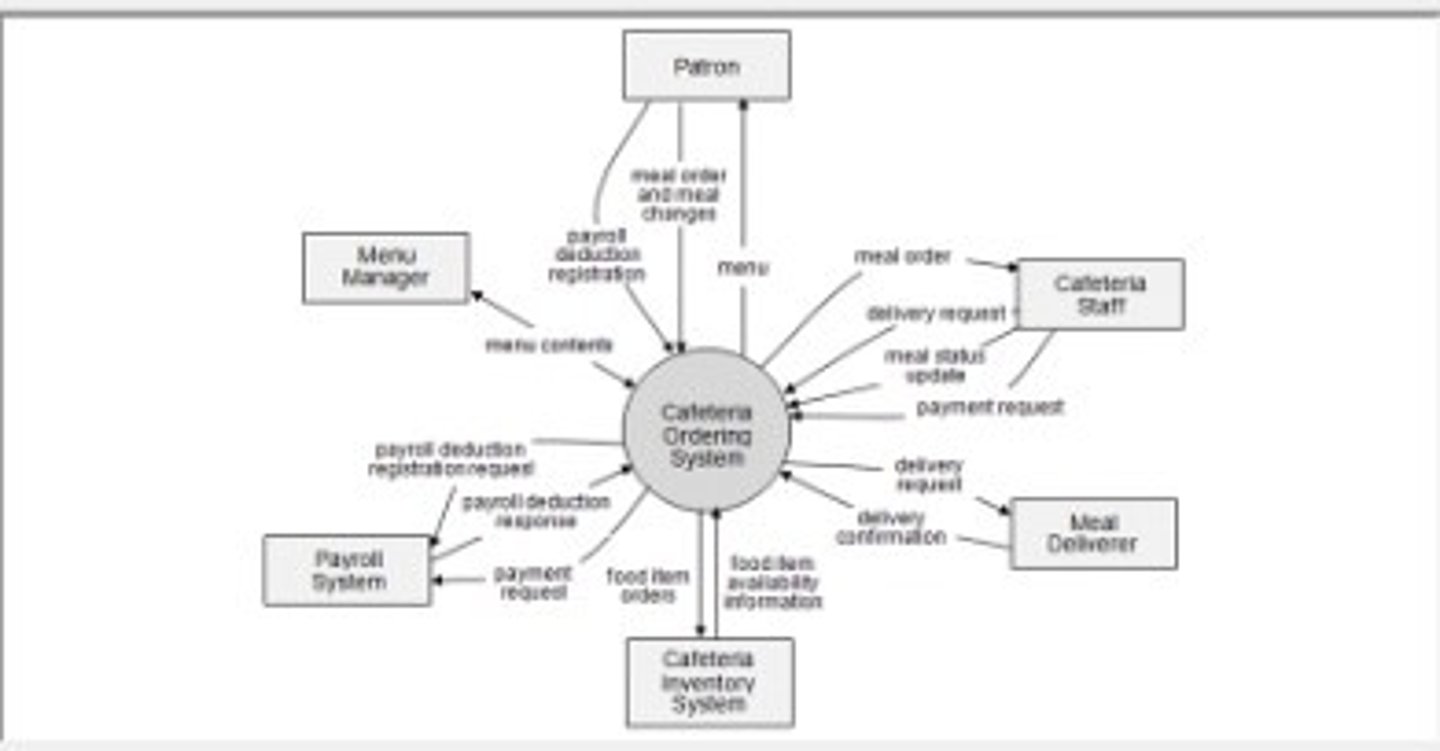
.........shows the system, and in boxes around the system, we have what are called external entities. There are several components or dimensions to a business process and those are labeled in this diagram.
A. The data flow diagram
B. The context diagram
C. Theswimlane diagram
D. The entity relationship diagram
B
The primary role of the __ is to manage and mediate communication
A. business analyst
B. designer
C. developer
D. project manager
A
In the __ approach, success, that is mastering of the system, is due to osmosis, growth, and adaptation
A. project management
B. learning
C. software devetopment
D. product development
B
Below statement is correct?
An individual's coworkers can be an important source of help in overcoming knowledge barriers
A. True
B. False
A
User training is more important for high complexity information systems than for low complexity information systems.
A. True
B. False
A
The planning and analysis phases in Waterfall are mapped roughly with ............. of RAD methodology.
A. the identify objectives and information requrrements
B. work with users to design system
C. burld the system
D. introduce the system
A
Which of the following is NOT a revolution change tactic?
A. Self-improvement
B. Impending crisis or failed
C. Use outsiders. Bring a new management team
D. Involve only the best of breed, and employees dissatisfied with status quo
A
____ approach for employee involvement, we use current managers and representative employees
A. In the evolutionary change
B. lntherevoiution change
C. In incremental change
D. In management change
A
Top management support and commitment is very important in information systems implementation because ___
A. top management is responsible for allocating scarce matenal and managerial resources
B. top management is responsible for estimating and planning scarce material and managerial resources
C. top management support evaluation technical solutions of the information system
A
Several years ago, I had to make a last minute trip to Europe.
When I opened my passport, I realized that my passport expired in less than 90 days, and that wasn't goodenough to get me into Europe. I had to renew my passport, and I had to do it within just a few days. Thankfully, I logged in to the US Passport Administration's website, and I found that we had a passport office here in Minneapolis where I live. I was able to make an appointment via an automated phone system, go down to the passport office the next day, and I had my passport in hand by the end of the next day.
The above case study was an example of ___ ?
A. a highly automated business process
B. the description about howto get a passport
C. the definition of what is a business process
D. the definition of what is a usecase
A
____ is motivated by self-improvement, we want to implement evolutionary change when things are going well but we want to improve things
A. Evolutionary change
B. Revolutionary change
C. Radicaliy change
D. Incremental change
A
In a(n) ___ model, the result of each phase is called a deliverable, which flows into the next phase.
A. iterative
B. spiral
C. waterfall
D. interactive
C
It's important that the BAs remain with the project past the analysis phase and into the design phase because they're often a good reference or resource for the software developers or implementers to check their work and make sure that they're followrng the requirements accordingly?
A. True
B. False
A