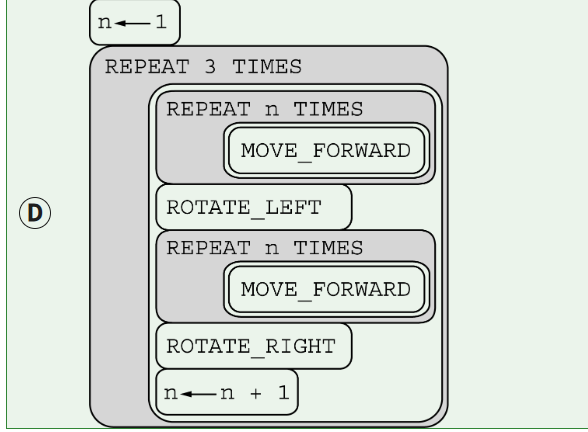
APCSP: Big Ideas 3: #3 PT 2 + Big Ideas 3: A&P #5
1/60
Earn XP
Description and Tags
Review Questions: Big Ideas 3 + Big Ideas 3 Algorithms and Programming 5
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
61 Terms
Which of the following best exemplifies the use of multifactor authentication to protect an online banking system?
A
When a user resets a password for an online bank account, the user is required to enter the new password twice.
B
When multiple people have a shared online bank account, they are each required to have their own unique username and password.
C
After entering a password for an online bank account, a user must also enter a code that is sent to the user’s phone via text message.
D
An online bank requires users to change their account passwords multiple times per year without using the same password twice.
After entering a password for an online bank account, a user must also enter a code that is sent to the user’s phone via text message.
Which of the following is an example of a phishing attack?
A
Loading malicious software onto a user’s computer in order to secretly gain access to sensitive information
B
Flooding a user’s computer with e-mail requests in order to cause the computer to crash
C
Gaining remote access to a user’s computer in order to steal user IDs and passwords
D
Using fraudulent e-mails in order to trick a user into voluntarily providing sensitive information
Using fraudulent e-mails in order to trick a user into voluntarily providing sensitive information.
Which of the following is a true statement about the use of public key encryption in transmitting messages?
A
Public key encryption enables parties to initiate secure communications through an open medium, such as the Internet, in which there might be eavesdroppers.
B
Public key encryption is not considered a secure method of communication because a public key can be intercepted.
C
Public key encryption only allows the encryption of documents containing text; documents containing audio and video must use a different encryption method.
D
Public key encryption uses a single key that should be kept secure because it is used for both encryption and decryption.
Public key encryption enables parties to initiate secure communications through an open medium, such as the Internet, in which there might be eavesdroppers.
An online gaming company is introducing several new initiatives to encourage respectful communication between players of online games. Which of the following best describes a solution that uses crowdsourcing?
A
The company allows individual players to endorse fellow players based on courteous interactions. Once a player receives enough endorsements, the player is given free rewards that can be used during gameplay.
B
The company eliminates chat from gameplay and sets the default chat policy to off. Players must actively turn on chat to converse outside of gameplay.
C
The company introduces software that monitors all chats. Inappropriate conversations are identified, and players involved in the conversations are banned from the game.
D
The company updates the acceptable content guidelines to explicitly describe appropriate and inappropriate behavior. All players must electronically sign an agreement to adhere to the guidelines.
The company allows individual players to endorse fellow players based on courteous interactions. Once a player receives enough endorsements, the player is given free rewards that can be used during gameplay.
Which of the following is an example of an attack using a rogue access point?
A
An unauthorized individual gains the ability to view network traffic by connecting to a network router that uses weak or no security measures.
B
An unauthorized individual physically disconnects an exposed network router, making the network unavailable to some users.
C
An unauthorized individual poses as a network administrator and attempts to trick a user into providing personal information.
D
A group of unauthorized individuals overwhelms a network router with traffic, making it unavailable to some users.
An unauthorized individual gains the ability to view network traffic by connecting to a network router that uses weak or no security measures.
Which of the following best explains why it is not possible to use computers to solve every problem?
Responses
A
Current computer processing capabilities cannot improve significantly.
B
Large-scale problems require a crowdsourcing model, which is limited by the number of people available to work on the problem.
C
The ability of a computer to solve a problem is limited by the bandwidth of the computer’s Internet connection.
D
There exist some problems that cannot be solved using any algorithm.
D
There exist some problems that cannot be solved using any algorithm.
A student wants to create an algorithm that can determine, given any program and program input, whether or not the program will go into an infinite loop for that input.
The problem the student is attempting to solve is considered an undecidable problem.
Which of the following is true?
A
It is possible to create an algorithm that will solve the problem for all programs and inputs, but the algorithm can only be implemented in a low-level programming language.
B
It is possible to create an algorithm that will solve the problem for all programs and inputs, but the algorithm requires simultaneous execution on multiple CPUs.
C
It is possible to create an algorithm that will solve the problem for all programs and inputs, but the algorithm will not run in reasonable time.
D
It is not possible to create an algorithm that will solve the problem for all programs and inputs.
It is not possible to create an algorithm that will solve the problem for all programs and inputs.
Which of the following statements is true?
A
Every problem can be solved with an algorithm for all possible inputs, in a reasonable amount of time, using a modern computer.
B
Every problem can be solved with an algorithm for all possible inputs, but some will take more than 100 years, even with the fastest possible computer.
C
Every problem can be solved with an algorithm for all possible inputs, but some of these algorithms have not been discovered yet.
D
There exist problems that no algorithm will ever be able to solve for all possible inputs.
There exist problems that no algorithm will ever be able to solve for all possible inputs.
A certain computer game is played between a human player and a computer-controlled player. Every time the computer-controlled player has a turn, the game runs slowly because the computer evaluates all potential moves and selects the best one. Which of the following best describes the possibility of improving the running speed of the game?
A
The game’s running speed can only be improved if the game is played between two human players instead of with the computer-controlled player.
B
The game’s running speed might be improved by using a process that finds approximate solutions every time the computer-controlled player has a turn.
C
The game’s running speed cannot be improved because computers can only be programmed to find the best possible solution.
D
The game’s running speed cannot be improved because the game is an example of an algorithm that does not run in a reasonable time.
B
The game’s running speed might be improved by using a process that finds approximate solutions every time the computer-controlled player has a turn.
A company delivers packages by truck and would like to minimize the length of the route that each driver must travel in order to reach n delivery locations. The company is considering two different algorithms for determining delivery routes.
Algorithm I
Generate all possible routes, compute their lengths, and then select the shortest possible route. This algorithm does not run in reasonable time.
Algorithm II
Starting from an arbitrary delivery location, find the nearest unvisited delivery location. Continue creating the route by selecting the nearest unvisited location until all locations have been visited. This algorithm does not guarantee the shortest possible route and runs in time proportional to n2.
Which of the following best categorizes algorithm II?
B) Algorithm II uses a heuristic approach to provide an approximate solution in reasonable time.
Consider the following algorithms. Each algorithm operates on a list containing n elements, where n is a very large integer.
An algorithm that accesses each element in the list twice
An algorithm that accesses each element in the list n times
An algorithm that accesses only the first 10 elements in the list, regardless of the size of the list
Which of the algorithms run in reasonable time?
A
I only
B
III only
C
I and II only
D
I, II, and III
D
I, II, and III
Which of the following programs is most likely to benefit from the use of a heuristic?
Responses
A
A program that calculates a student’s grade based on the student’s quiz and homework scores
B
A program that encrypts a folder of digital files
C
A program that finds the shortest driving route between two locations on a map
D
A program that sorts a list of numbers in order from least to greatest
C
A program that finds the shortest driving route between two locations on a map
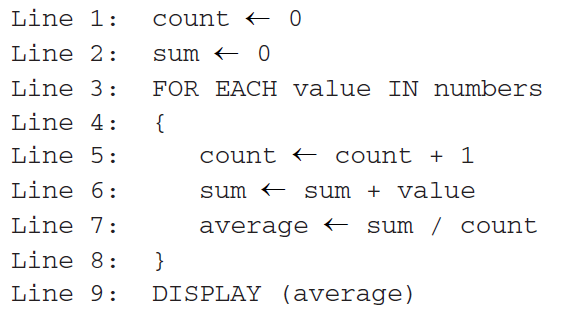
A programmer wrote the code segment below to display the average of all the elements in a list called numbers. There is always at least one number in the list.
The programmer wants to reduce the number of operations that are performed when the program is run. Which change will result in a correct program with a reduced number of operations performed?
Responses
A
Interchanging line 1 and line 2
B
Interchanging line 5 and line 6
C
Interchanging line 6 and line 7
D
Interchanging line 7 and line 8
D) Interchanging line 7 and line 8
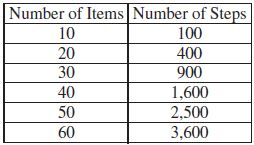
An online retailer uses an algorithm to sort a list of n items by price. The table below shows the approximate number of steps the algorithm takes to sort lists of different sizes.
Based on the values in the table, which of the following best characterizes the algorithm for very large values of n ?
A
The algorithm runs in reasonable time.
B
The algorithm runs, but not in reasonable time.
C
The algorithm attempts to solve an undecidable problem.
D
The algorithm attempts to find an approximate solution whenever it fails to find an exact solution.
A
The algorithm runs in reasonable time.
A video-streaming service maintains a database of information about its customers and the videos they have watched.
The program below analyzes the data in the database and compares the number of viewers of science fiction videos to the number of viewers of videos of other genres. It uses the procedure analysis (category) , which returns the number of unique users who viewed videos of a given category in the past year. The analysis procedure takes approximately 1 hour to return a result, regardless of the number of videos of the given genre. All other operations happen nearly instantaneously.

Which of the following best approximates the amount of time it takes the program to execute?
Responses
A
1 hour
B
2 hours
C
4 hours
D
5 hours
D
5 hours
Which of the following statements describes a limitation of using a computer simulation to model a real-world object or system?
Responses
A
Computer simulations can only be built after the real-world object or system has been created.
B
Computer simulations only run on very powerful computers that are not available to the general public.
C
Computer simulations usually make some simplifying assumptions about the real-world object or system being modeled.
D
It is difficult to change input parameters or conditions when using computer simulations.
C
Computer simulations usually make some simplifying assumptions about the real-world object or system being modeled.
RunRoutr is a fitness tracking application for smartphones that creates suggested running routes so that users can run with each other. Upon downloading the application, each user creates a username, a personal profile, and a contact list of friends who also use the application. The application uses the smartphone’s GPS unit to track a user’s location, running speed, and distance traveled. Users can use the application to review information and statistics about their previous runs.
At the beginning of a run, users indicate the distance they want to run from their current location, and the application suggests a running route. Once a user accepts a suggested route, the application shares the suggested route with other compatible users in the area so that they can run together. Users are considered compatible if they are on each other’s contact lists or if they typically run at similar speeds.
A basic RunRoutr account is free, but it displays advertisements that are targeted to individual users based on data collected by the application. For example, if a user’s running route begins or ends near a particular store, the application may display an advertisement for that store. Users have the ability to pay a monthly fee for a premium account, which removes advertisements from the application.
Businesses have the ability to target advertisements to different groups of people who use RunRoutr. Which of the following groups is LEAST likely to receive targeted advertisements?
Responses
A
Individuals who appear on each other’s contact lists
B
Individuals who are interested in running and fitness
C
Individuals who sign up for a premium account
D
Individuals whose running routes begin or end near a particular business location
C
Individuals who sign up for a premium account

A researcher wrote a program to simulate the number of mice in an environment that contains predators. The program uses the following procedures.
Code for the simulation is shown below.
Based on the code, which of the following assumptions is made in the simulation?
Responses
A
The number of mice increases by 1 each day.
B
The number of mice does not change from day to day.
C
The number of predators increases by 1 each day.
D
The number of predators does not change from day to day.
D
The number of predators does not change from day to day.
A group of planners are using a simulation to examine whether or not a park that they are designing is going to affect foot traffic in the area. The simulation uses a model that includes input variables for the park such as the number of entrances, sidewalks, and bike trails and the square footage of open space (grassy areas). The simulation can then be run multiple times using different values for the input variables to represent different park designs.
However, the simulation takes a very long time to run. The planners update the model by removing some variables they consider less important than others.
Of the following, which is the most likely effect the updated model will have on the simulation?
Responses
A
The updated model is likely to decrease the runtime of the simulation because the time required for simulations generally depends on the complexity of the model used.
B
The updated model is likely to decrease the runtime of the simulation because simulations that use older models tend to require more time to run than simulations that use newer models.
C
The updated model is unlikely to decrease the runtime of the simulation because the simulation is computationally complex, regardless of the model used.
D
The updated model is unlikely to provide any benefit because removing details from a model will compromise the accuracy of the simulation.
A
The updated model is likely to decrease the runtime of the simulation because the time required for simulations generally depends on the complexity of the model used.
A population researcher is interested in predicting the number of births that will occur in a particular community. She created a computer model that uses data from the past ten years, including number of residents and the number of babies born. The model predicted that there would be 200 births last year, but the actual number of births last year was only 120.
Which of the following strategies is LEAST likely to provide a more accurate prediction?
Responses
A
Gathering data for additional years to try to identify patterns in birth rates
B
Refining the model used in the computer simulation to more closely reflect the data from the past ten years
C
Removing as many details from the model as possible so that calculations can be performed quickly
D
Taking into consideration more information about the community, such as the ages of residents
C
Removing as many details from the model as possible so that calculations can be performed quickly
A scientist wants to investigate several problems. In which of the following situations is using a simulation LEAST suitable for solving a problem?
Responses
A
When a scientific study requires performing a large number of trials that need to be conducted very quickly
B
When it is considered acceptable to make simplifying assumptions when modeling a real-world object or phenomenon
C
When performing an experiment that would be too costly or dangerous to conduct in the real world
D
When the solution to the problem requires real-world data inputs that are continually measured at regular intervals.
D
When the solution to the problem requires real-world data inputs that are continually measured at regular intervals.
A new bank plans to make customer convenience a priority by minimizing the amount of time a customer waits in line. The bank is considering two options: a single line where the customer at the front waits for the next available teller, or separate lines for each teller. The bank decides to use a computer simulation of these two options to determine the average wait time for customers.
Which of the following is NOT true about the bank’s plan?
Responses
A
The bank can incorporate other factors, such as the number of tellers, in the simulation.
B
The bank can use the simulation to investigate these two options without causing inconvenience for customers.
C
The bank may consider new alternatives based on the simulation results.
D
The simulation will not produce usable results because actual customer data are not available.
D
The simulation will not produce usable results because actual customer data are not available.
Consider the following code segment.
![The figure presents two blocks of code that consist of 5 total lines. Throughout the blocks of code there are nested blocks of code, as follows. Line 1: [begin block] i ← 1 [end block] [begin block] Line 2: REPEAT UNTIL [begin block] i greater than 4 [end block] [begin block] Line 3: [begin block] rand ← RANDOM [begin block] 1, i [end block] [end block] Line 4: [begin block] DISPLAY [begin block] rand [end block] [end block] Line 5: [begin block] i ← i + 1 [end block] [end block] [end block]](https://assets.learnosity.com/organisations/537/VR165845.g03.png)
Which of the following CANNOT be displayed as a result of executing the code segment?
Responses
A
1 1 1 1
B
1 2 3 2
C
1 2 3 4
D
1 3 2 4
D) 1 3 2 4
Consider the following code segment.
![The figure presents 2 blocks of code that consist of 2 total lines, as follows. Line 1: [begin block] ans ← RANDOM [begin block] 1, 3 [end block] + RANDOM [begin block] 2, 5 [end block] [end block] Line 2: [begin block] ans ← ans + RANDOM [begin block] 4, 8 [end block] [end block]](https://assets.learnosity.com/organisations/537/VR165700.g01.png)
Which of the following describes the possible values of ans as a result of executing the code segment?
Responses
A
Any integer value from 1 to 8, inclusive
B
Any integer value from 1 to 16, inclusive
C
Any integer value from 4 to 8, inclusive
D
Any integer value from 7 to 16, inclusive
D
Any integer value from 7 to 16, inclusive
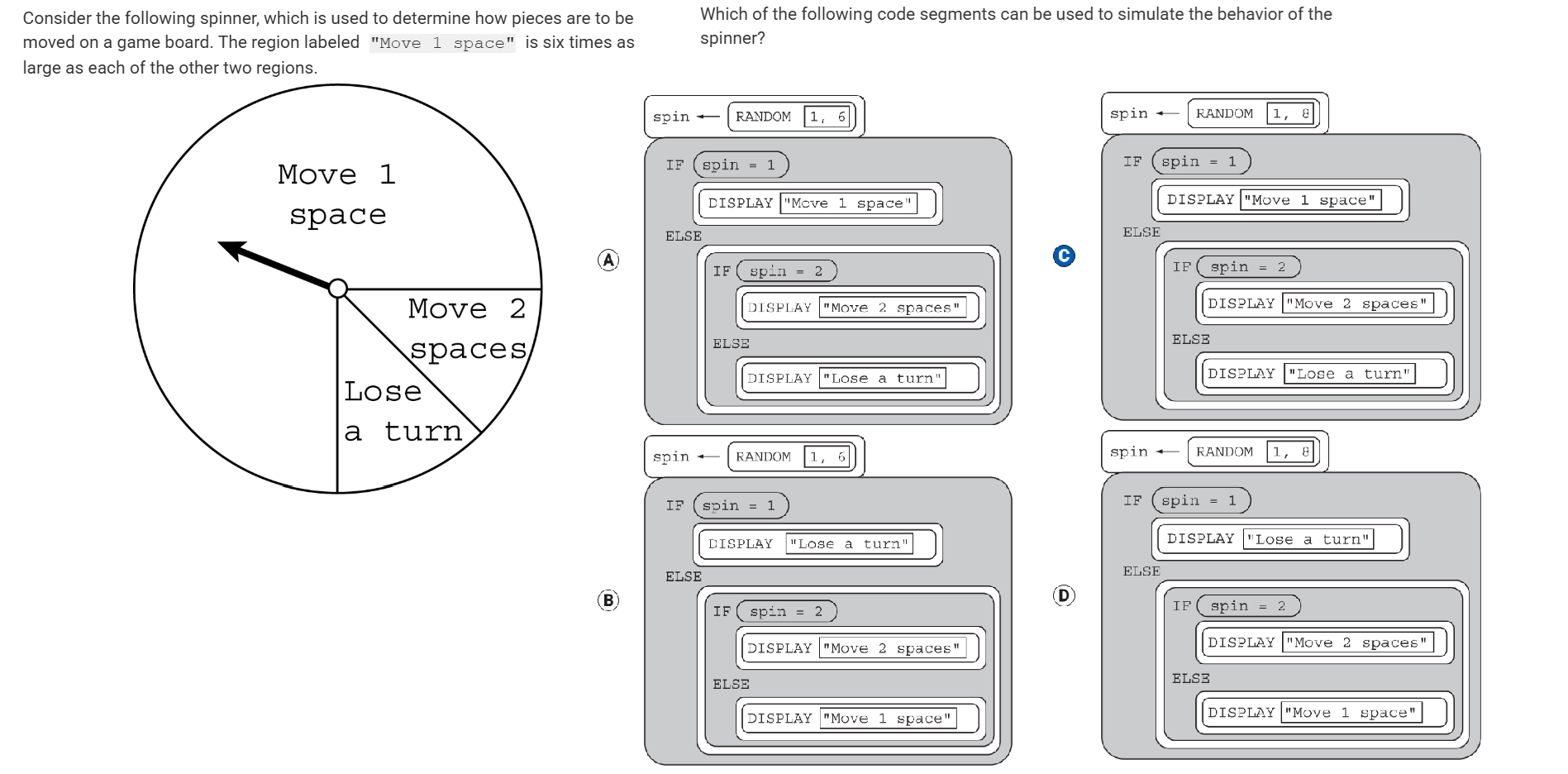
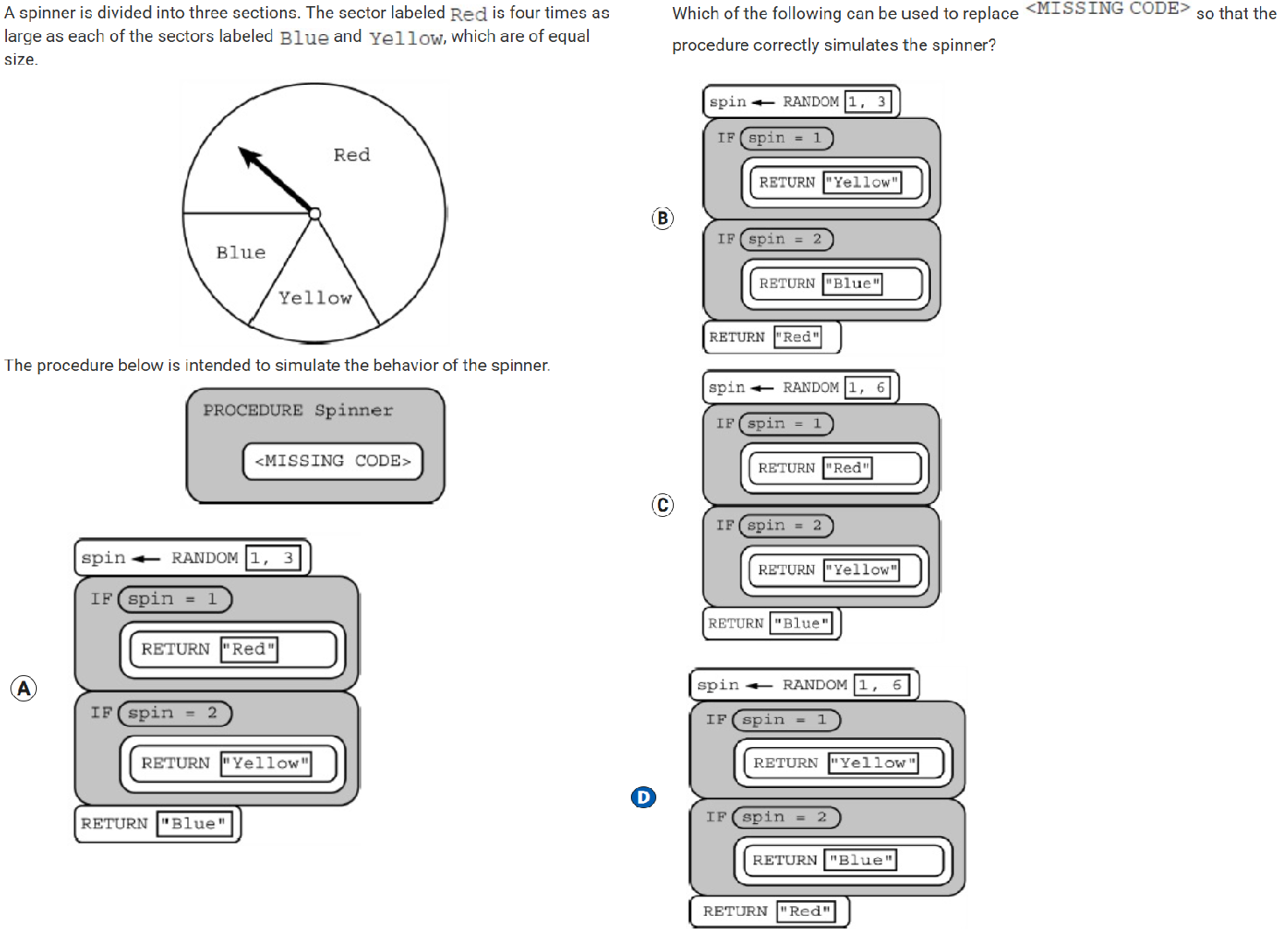
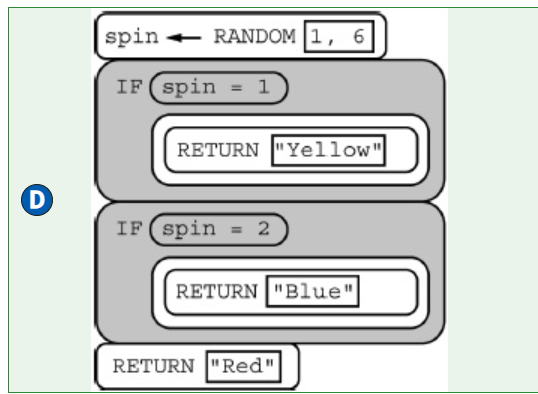
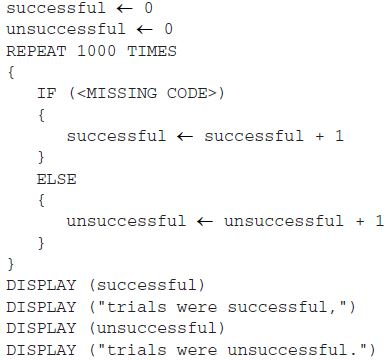
In a certain science experiment, 75 percent of trials are expected to be successful and 25 percent of trials are expected to be unsuccessful. The program below is intended to simulate the results of repeated trials of the experiment.
Which of the following can be used to replace <MISSING CODE> so that the simulation works as intended?
Responses
A

B

C

D

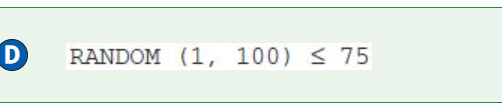
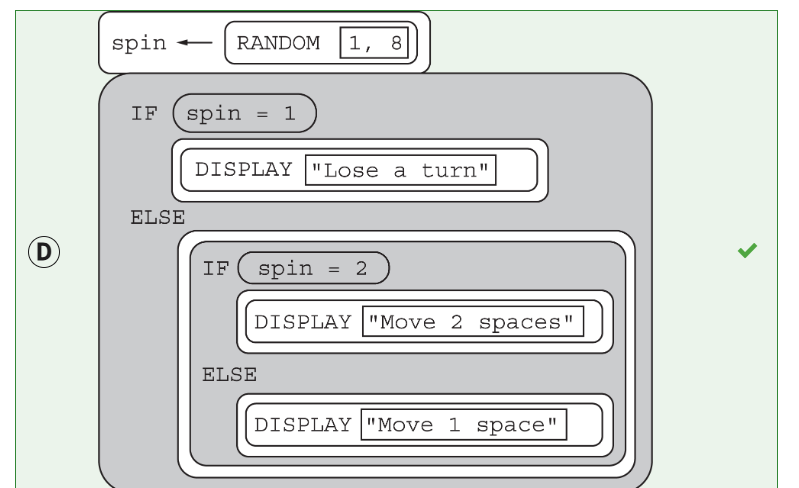
n a certain district, 20 percent of the voters are expected to vote for Candidate A in an election. The computer program below is intended to simulate the result of the election with voters, and display the number of votes received by Candidate A.

Which of the following can be used to replace in line 4 so that the program works as intended?
Select two answers.
A

B

C

D

A

D

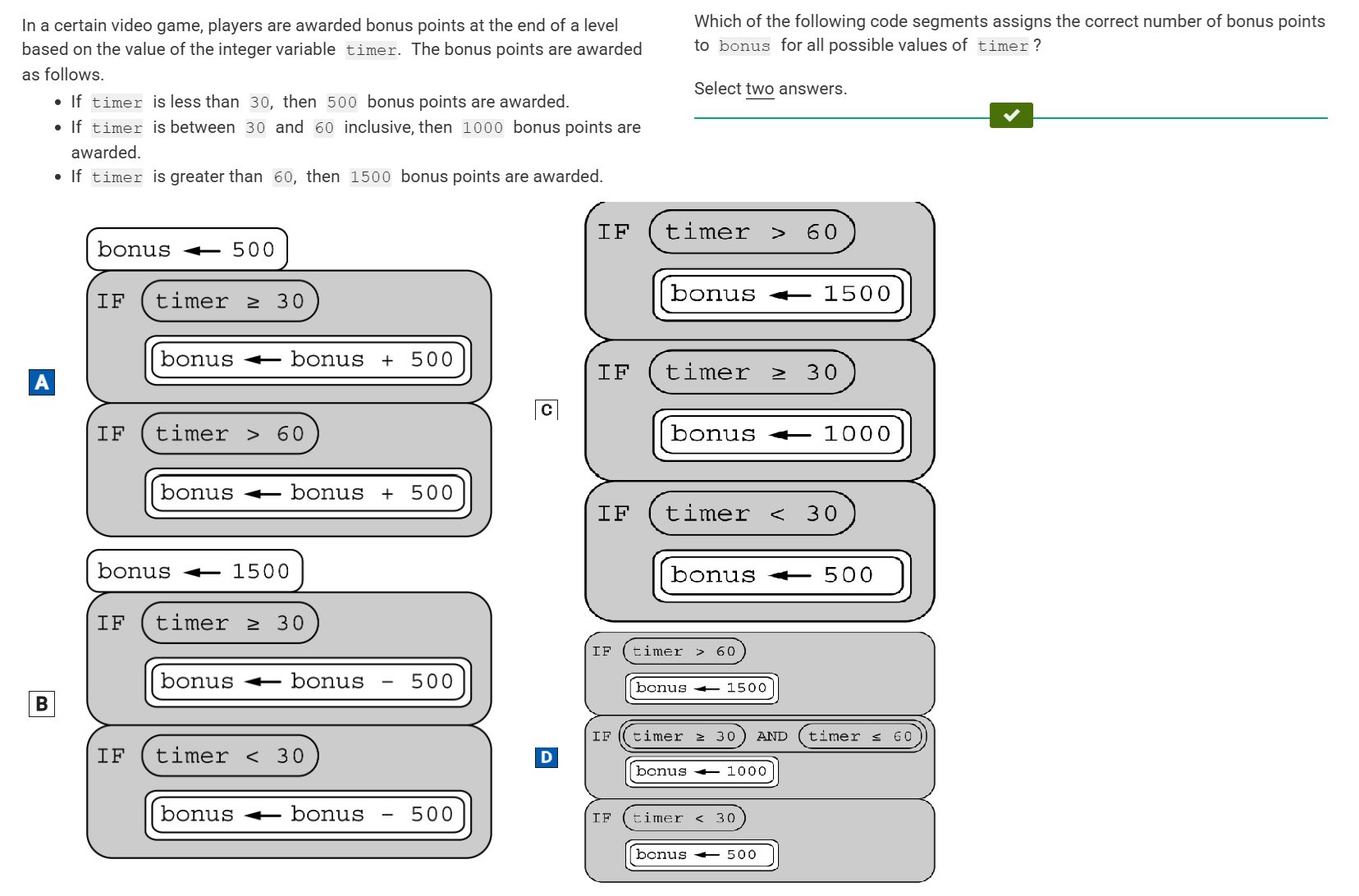
In a certain game, a player may have the opportunity to attempt a bonus round to earn extra points. In a typical game, a player is given 1 to 4 bonus round attempts. For each attempt, the player typically earns the extra points 70% of the time and does not earn the extra points 30% of the time.
The following code segment can be used to simulate the bonus round.
![The figure presents eight blocks of code that consists of 10 total lines. Throughout the blocks of code there are nested blocks of code, as follows. Line 1: [begin block] success ← 0 [end block] Line 2: [begin block] attempts ← RANDOM [begin block] 1, 4 [end block] [end block] [begin block] Line 3: REPEAT attempts TIMES [begin block] [begin block] Line 4: IF [begin block] RANDOM [begin block] 1, 10 [end block] less than or equal to 7 [end Block] [begin block] Line 5: [begin block] success ← success + 1 [end block] [end block] [end block] [end block] [end block] Line 6: [begin block] DISPLAY [begin block] “The player had” [end block] [end block] Line 7: [begin block] DISPLAY [begin block] attempts [end block] [end block] Line 8: [begin block] DISPLAY [begin block] “bonus round attempts and” [end block] [end block] Line 9: [begin block] DISPLAY [begin block] success [end block] [end block] Line 10: [begin block] DISPLAY [begin block] “of them earned extra points.” [end block] [end block]](https://assets.learnosity.com/organisations/537/VR168421.g01.png)
Which of the following is NOT a possible output of this simulation?
A
The player had 1 bonus round attempts and 1 of them earned extra points.
B
The player had 2 bonus round attempts and 0 of them earned extra points.
C
The player had 3 bonus round attempts and 7 of them earned extra points.
D
The player had 4 bonus round attempts and 3 of them earned extra points.
C
The player had 3 bonus round attempts and 7 of them earned extra points.
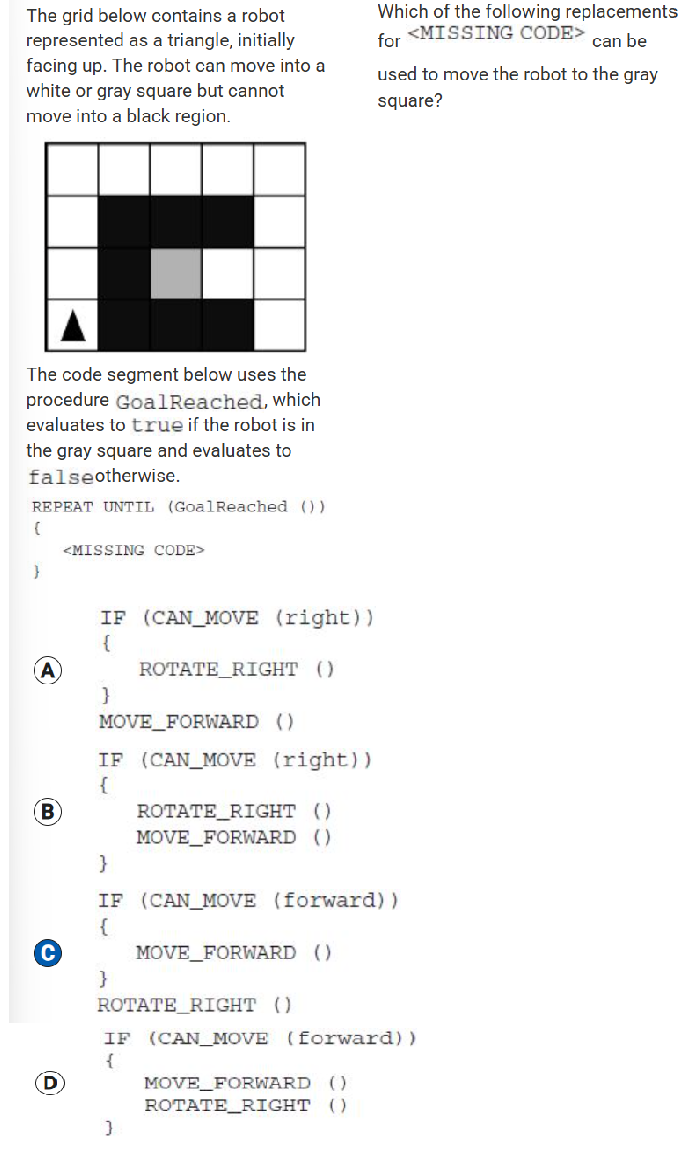
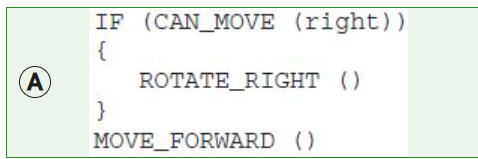
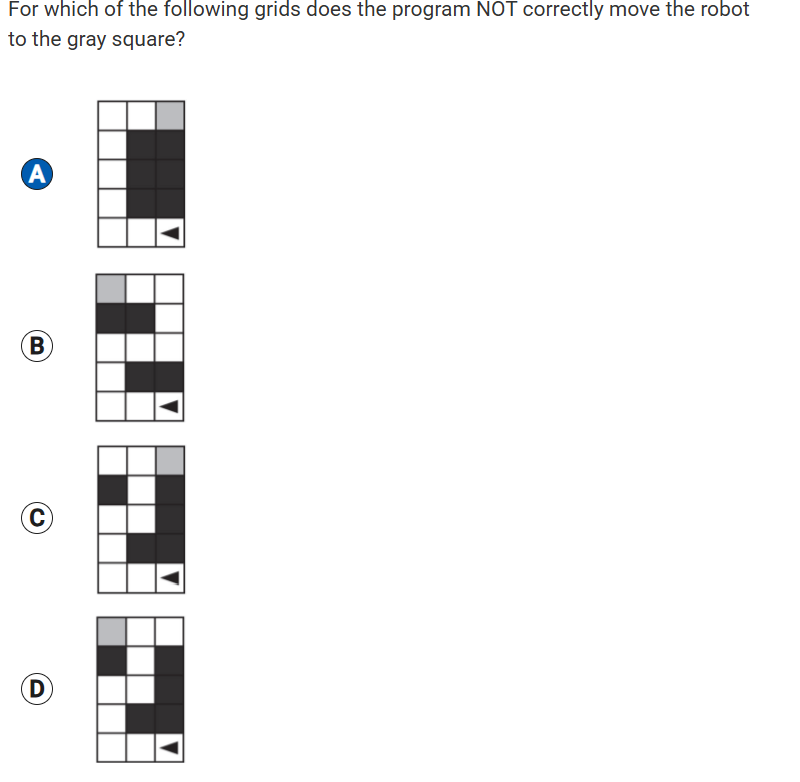
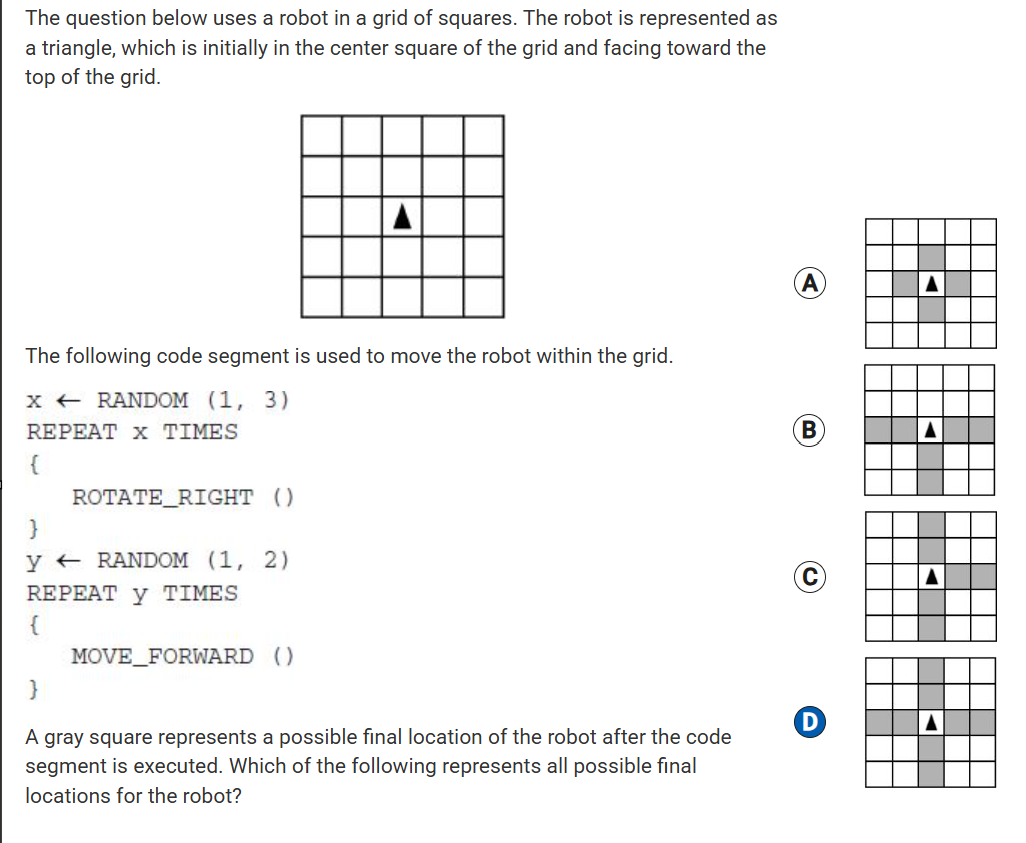
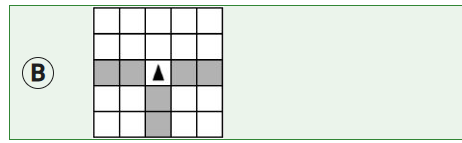
The program segment below is intended to move a robot in a grid to a gray square. The program segment uses the procedure GoalReached, which evaluates to true if the robot is in the gray square and evaluates to false otherwise. The robot in each grid is represented as a triangle and is initially facing left. The robot can move into a white or gray square but cannot move into a black region.

For which of the following grids does the program NOT correctly move the robot to the gray square?
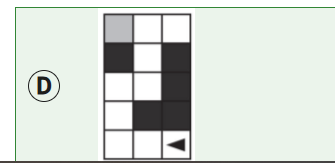
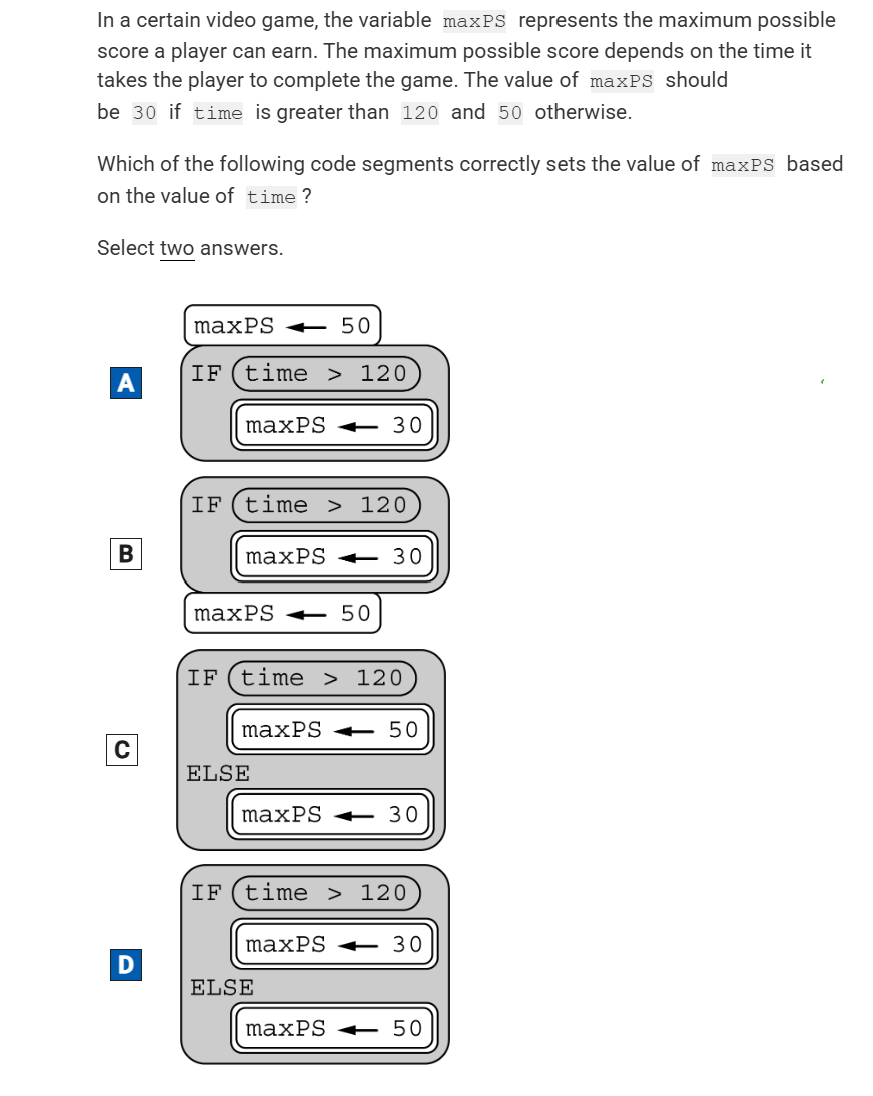
An algorithm has been developed to compute the sum of all the elements in a list of integers. Which of the following programming structures must be added to the existing algorithm so that the new algorithm computes the sum of only the even integers in the list?
Responses
A
Iteration
B
Searching
C
Selection
D
Sequencing
C
Selection
Consider the following code segment.
![The figure presents one block of code that consists of 4 total lines. [Begin Block] Line 1: IF [begin block] x is greater than y [end block] [begin block] Line 2: [begin block] DISPLAY [begin block] x plus y [end block] [end block] [end block] Line 3: ELSE [begin block] Line 4: [begin block] DISPLAY [begin block] x minus y [end block] [end block] [end block] [End Block]](https://assets.learnosity.com/organisations/537/VR167821.g01.png)
If the value of x is 3 and the value of y is 5, what is displayed as a result of executing the code segment?
Responses
A
-2
B
2
C
8
D
Nothing will be displayed.
A) -2
Consider the following code segment.
![The figure presents six blocks of code that consist of 10 total lines. Line 1: [begin block] num1 ← 6 [end block] Line 2: [begin block] num2 ← 4 [end block] Line 3: [begin block] num3 ← 10 [end block] [Begin Block] Line 4: IF [begin block] num1 is less than num2 [end block] [begin block] Line 5: [begin block] num1 ← num2 [end block] [end block] Line 6: ELSE [begin block] Line 7: [begin block] num3 ← num2 [end block] [end block] [End Block] [Begin block] Line 8: IF [begin block] num2 is greater than or equal to num3 [end block] [begin block] Line 9: [begin block] num1 ← num2 plus num3 [end block] [end block] [End Block] Line 10: [begin block] sum ← num1 plus num2 plus num3 [end block]](https://assets.learnosity.com/organisations/537/VR165938.g01.png)
What is the value of sum after the code segment is executed?
Responses
A
12
B
14
C
16
D
18
C) 16
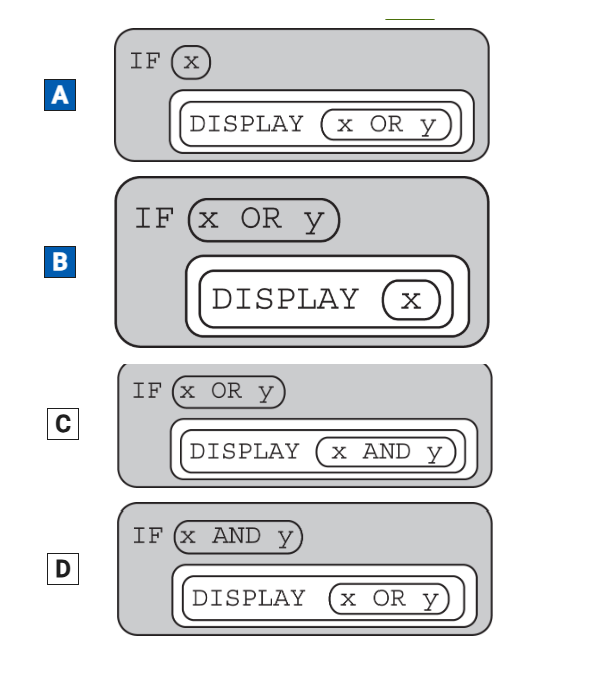
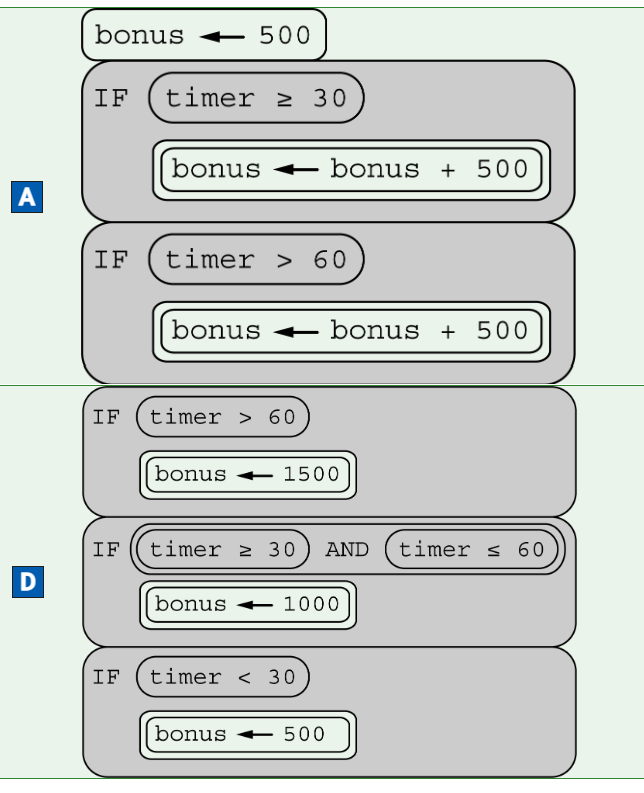
Assume that the Boolean variable x is assigned the value true and the Boolean variable y is assigned the value false. Which of the following will display the value true ?
Select two answers.
![<p>In the following statement, <span>val1</span>, <span>val2</span>,<span> </span>and <span>result</span> are Boolean variables.</p><img src="https://assets.learnosity.com/organisations/537/VR112589.g02.png" data-width="50%" data-align="center" alt="The figure presents a block of code that consists of one line. The block of code contains a nested block of code. Line 1: [begin block] result ← val1 AND [begin block] NOT val2 [end block] [end block]"><p class="stem_paragraph">Which of the following code segments produce the same result as the statement above for all possible values of <span>val1</span> and <span>val2</span> ?</p><p class="stem_paragraph">Select <span>two</span> answers.</p>](https://knowt-user-attachments.s3.amazonaws.com/1075a48d-b592-4989-b018-7db8572c498d.png)
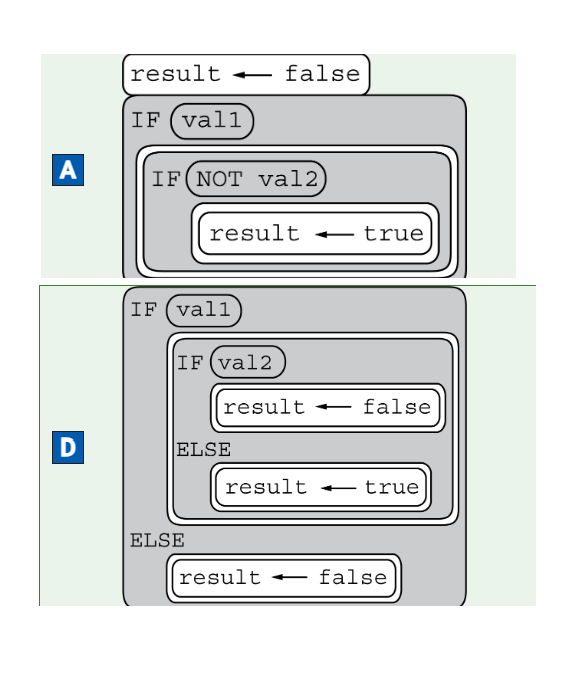
In the following statement, val1, val2, and result are Boolean variables.
![The figure presents a block of code that consists of one line. The block of code contains a nested block of code. Line 1: [begin block] result ← val1 AND [begin block] NOT val2 [end block] [end block]](https://assets.learnosity.com/organisations/537/VR112589.g02.png)
Which of the following code segments produce the same result as the statement above for all possible values of val1 and val2 ?
Select two answers.
Consider the following code segment, where exam and presentation are integer variables and grade is a string variable.
IF((exam > 90) AND (presentation > 80))
{
grade ← "A"
}
IF((exam > 80) OR (presentation > 75))
{
grade ← "B"
}
ELSE
{
IF((exam > 70) OR (presentation > 60))
{
grade ← "C"
}
ELSE
{
IF(exam > 60)
{
grade ← "D"
}
ELSE
{
grade ← "F"
}
}
}
Under which of the following conditions will the value "C" be assigned to the variable grade ?
Responses
A
When the value of exam is 70 and the value of presentation is 50
B
When the value of exam is 70 and the value of presentation is 80
C
When the value of exam is 80 and the value of presentation is 60
D
When the value of exam is 80 and the value of presentation is 80
C
When the value of exam is 80 and the value of presentation is 60
In the program below, the initial value of x is 5 and the initial value of y is 10.
What is displayed as a result of running the program?
Responses
A
Foxtrot
B
Hotel
C
November
D
Yankee
C
November
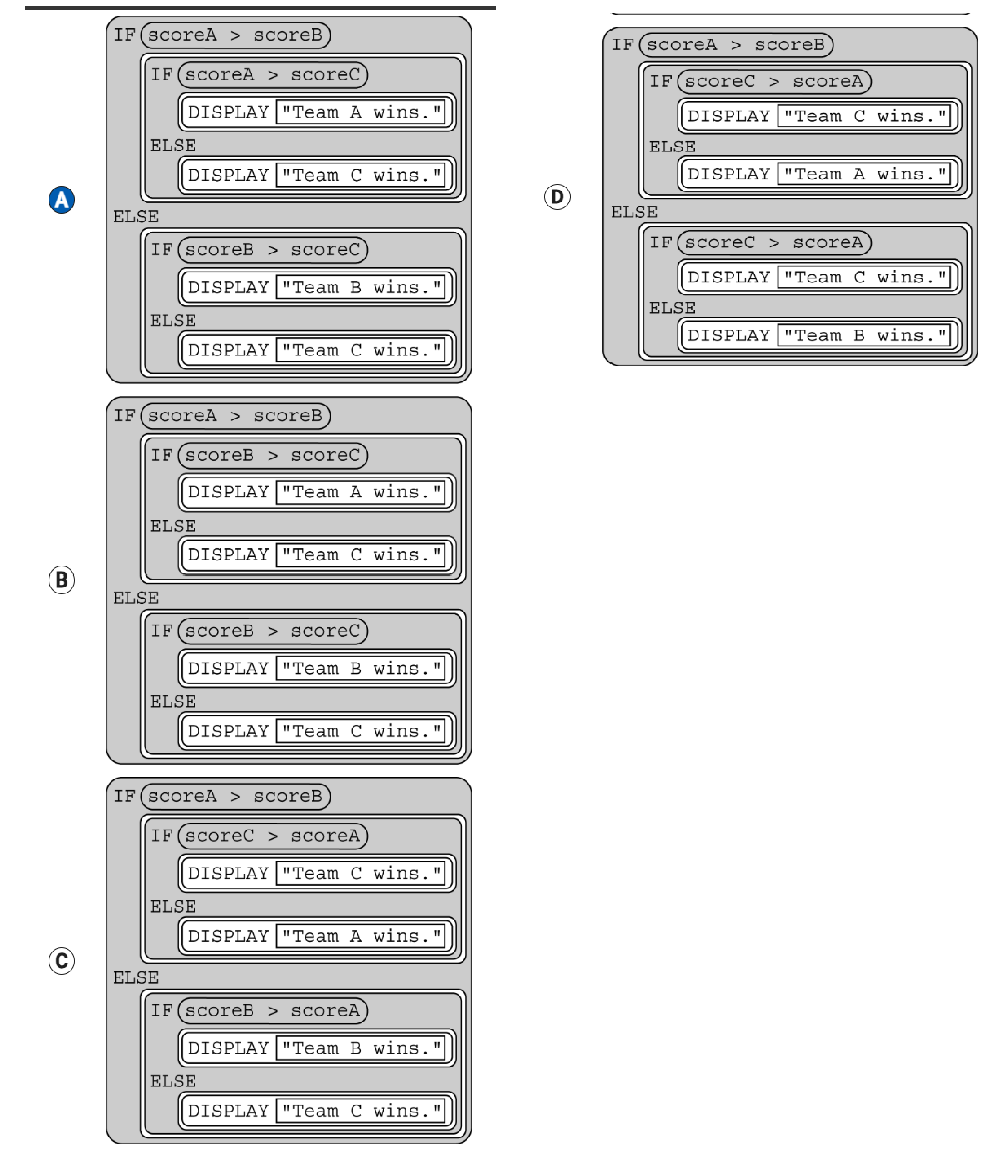
Three teams (Team A, Team B, and Team C) are participating in a trivia contest. Let scoreA represent the number of correct questions for Team A, scoreB represent the number of correct questions for Team B, and scoreC represent the number of correct questions for Team C. Assuming no two teams get the same number of correct questions, which of the following code segments correctly displays the team with the highest number of correct questions?
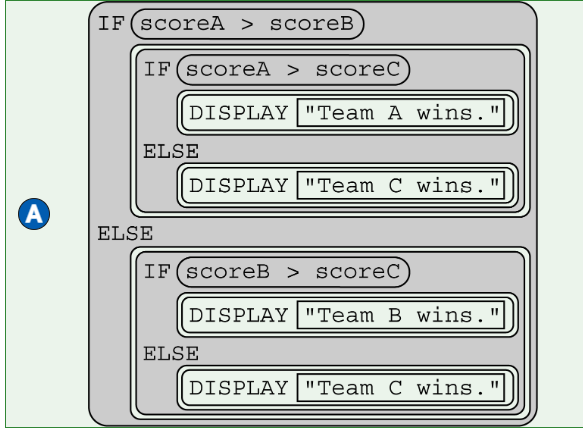
A
II only
B
I and II only
C
I and III only
D
II and III only
D
II and III only
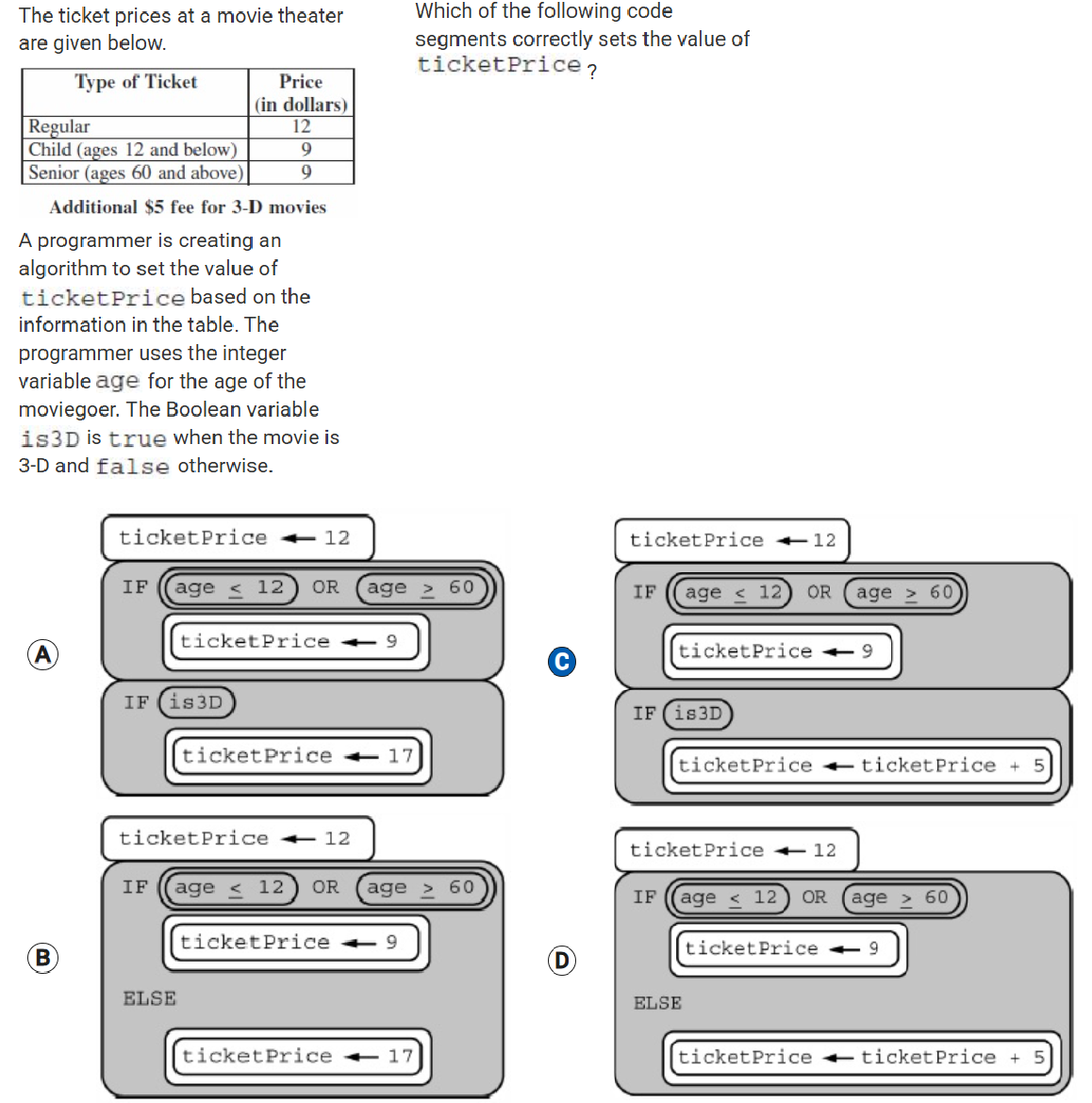
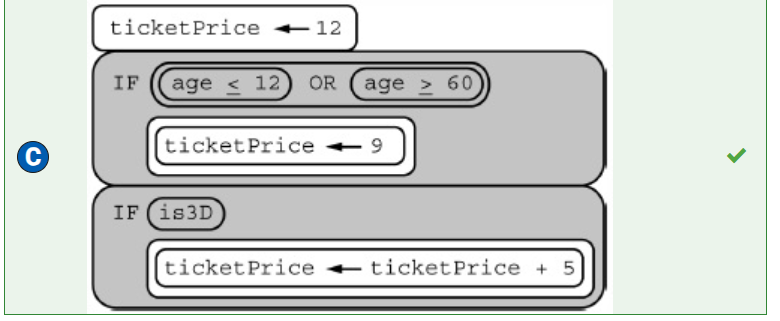
Ticket prices for a science museum are shown in the following table.
Type of Ticket | General Admission Cost(in dollars) | Guided Tour Cost(in dollars) |
Regular (ages 13 and up) | 8 | 10 |
Child (ages 12 and below) | 6 | 8 |
A programmer is creating an algorithm to display the cost of a ticket based on the information in the table. The programmer uses the integer variable age for the age of the ticket recipient. The Boolean variable includesTour is true when the ticket is for a guided tour and is false when the ticket is for general admission.
Which of the following code segments correctly displays the cost of a ticket?
Responses
A
cost ← 6
IF ((age > 12) OR includesTour)
{
cost ← cost + 2
}
DISPLAY (cost)
B
cost ← 6
IF (age > 12)
{
cost ← cost + 2
}
IF (includesTour)
{
cost ← cost + 2
}
DISPLAY (cost)
C
cost ← 6
IF (age > 12)
{
IF (includesTour)
{
cost ← cost + 2
}
}
DISPLAY (cost)
D
cost ← 6
IF (age > 12)
{
cost ← cost + 2
}
ELSE
{
IF (includesTour)
{
cost ← cost + 2
}
}
DISPLAY (cost)
B)
cost ← 6
IF (age > 12)
{
cost ← cost + 2
}
IF (includesTour)
{
cost ← cost + 2
}
DISPLAY (cost)
Consider the following code segment with integer variables x and y.
![The figure presents one block of code that consists of 10 total lines. Throughout the block of code there are nested blocks of code. [Begin Block] Line 1: IF [begin block] x is greater than 10 [end block] [Begin Block] [begin block] Line 2: IF [begin block] y is less than 10 [end block] [begin block] Line 3: [begin block] DISPLAY [begin block] “ONE” [end block] [end block] [end block] Line 4: ELSE [begin block] Line 5: [begin block] DISPLAY [begin block] “TWO” [end block] [end block] [end block] [end block] [End Block] Line 6: ELSE [Begin Block] [begin block] Line 7: IF [begin block] y is greater than 3 [end block] [begin block] Line 8: [begin block] DISPLAY [begin block] “THREE” [end block] [end block] [end block] Line 9: ELSE [begin block] Line 10: [begin block] DISPLAY [begin block] “FOUR” [end block] [end block] [end block] [end block] [end block] [End block]](https://assets.learnosity.com/organisations/537/VR167931.g01.png)
If x has a value of 7 and y has a value of 20, what is displayed as a result of executing the code segment?
Responses
A
ONE
B
TWO
C
THREE
D
FOUR
C) three
Consider the following code segment.
result ← 1
IF(score1 > 500)
{
result ← result + 1
IF(score2 > 500)
{
result ← result + 1
}
ELSE
{
result ← result + 2
}
}
ELSE
{
result ← result + 5
IF(score2 > 500)
{
result ← result + 1
}
ELSE
{
result ← result - 1
}
}
If the value of score1 is 350 and the value of score2 is 210, what will be the value of result after the code segment is executed?
Responses
A
3
B
4
C
5
D
7
C) 5
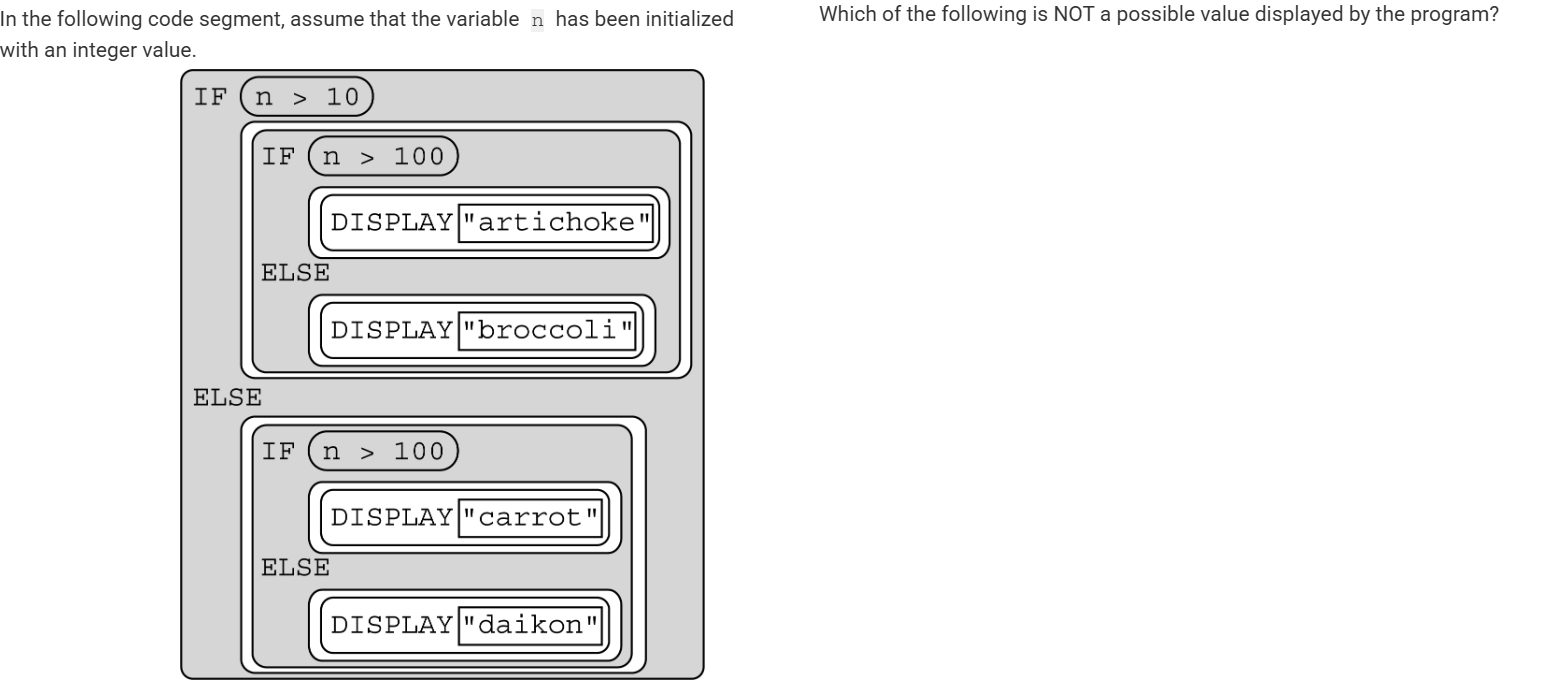
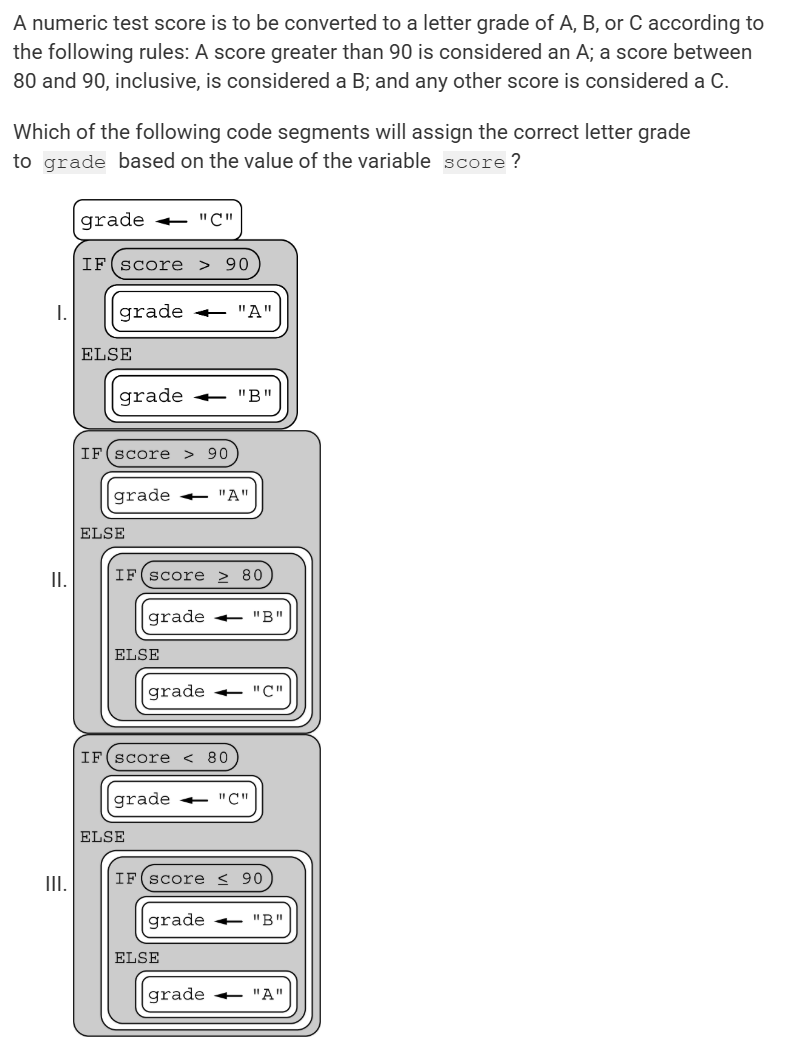
A) “artichoke “
B) “broccoli”
C) “carrot”
D) “daikon”
C) carrot
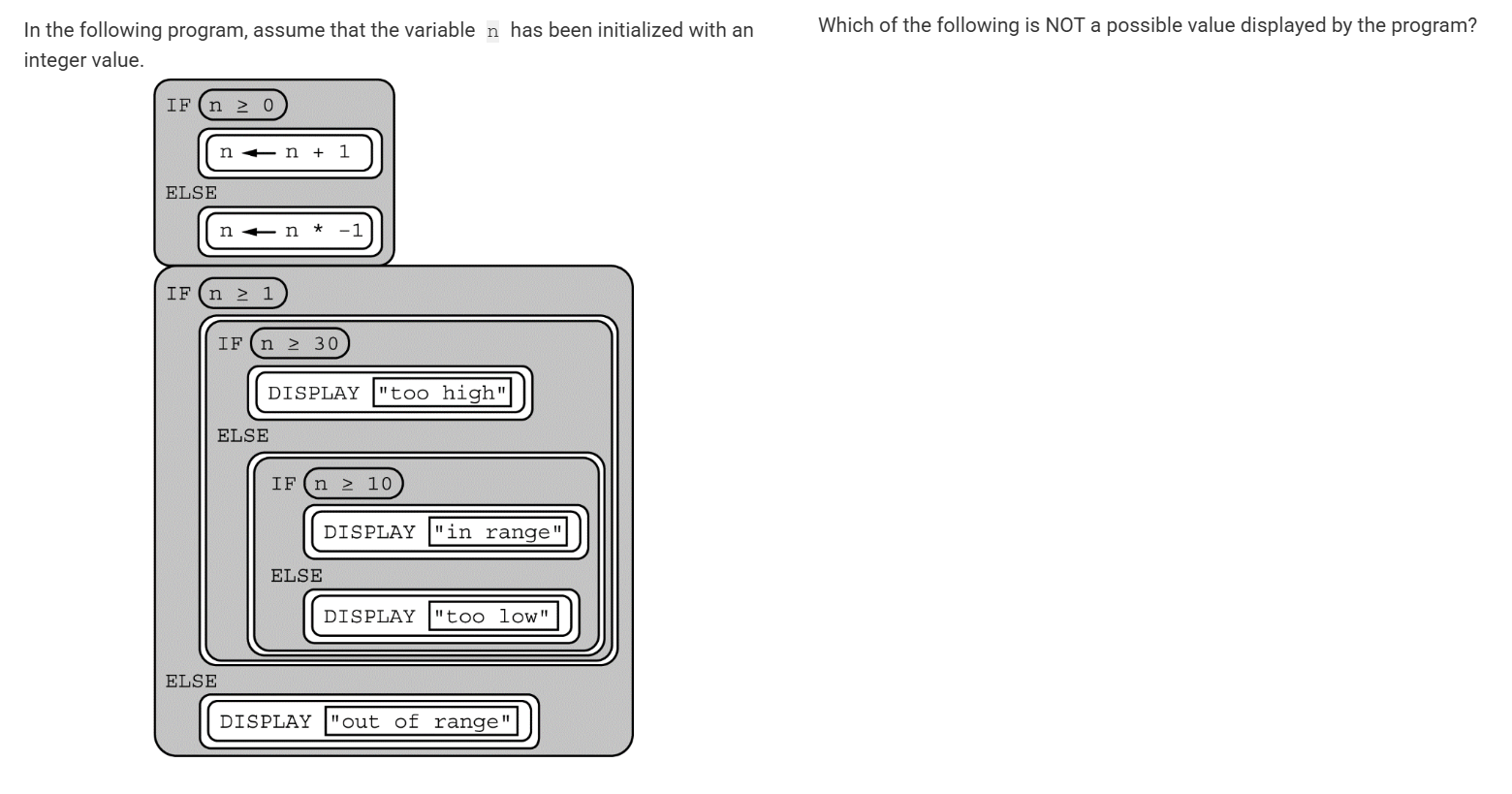
A) Too high
b) In range
C) too low
D) out of range
D) out of range
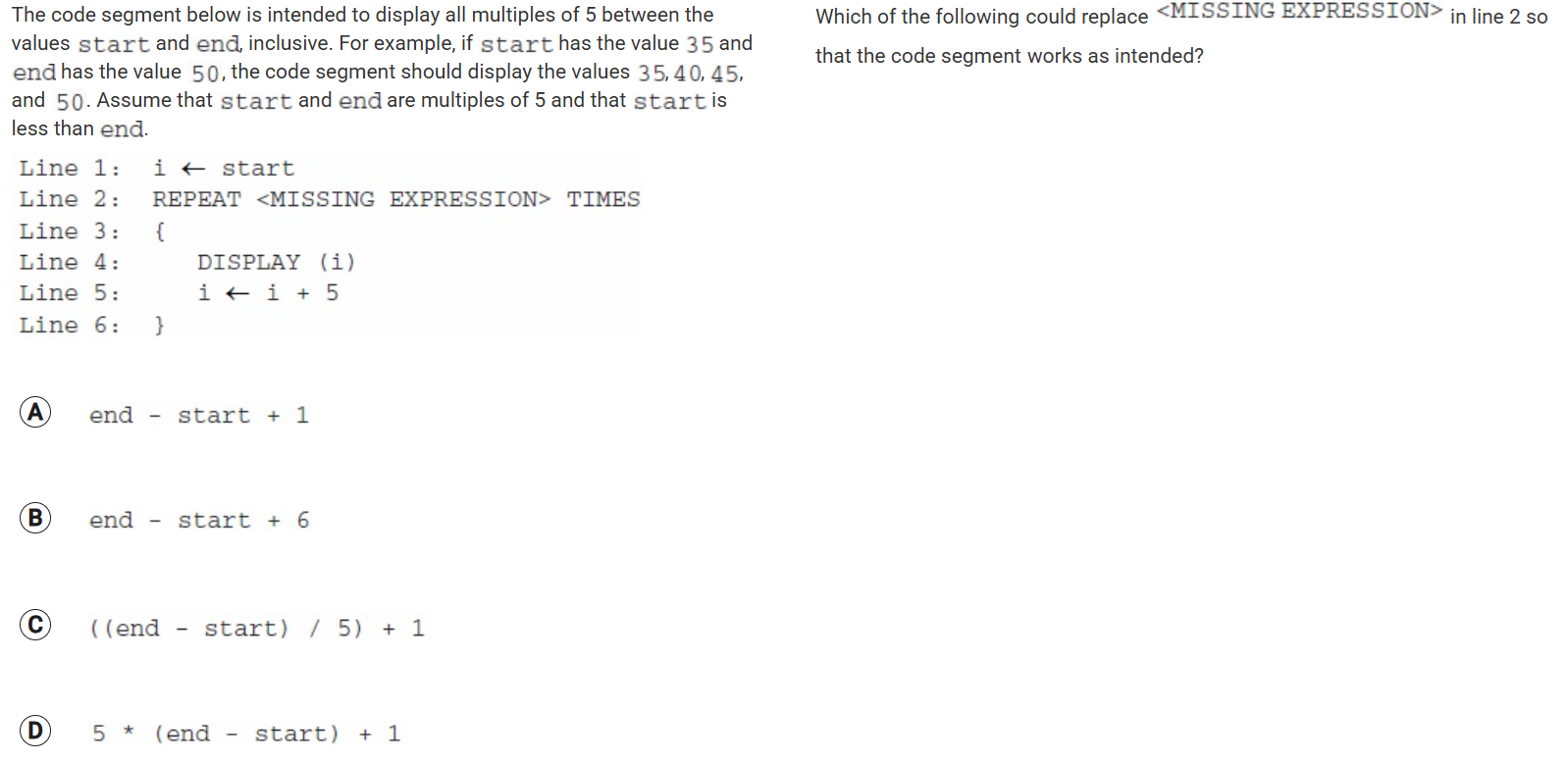
C

Consider the following program code.

Which of the following best describes the result of running the program code?
Responses
A
The number 0 is displayed.
B
The number 6 is displayed.
C
The number 10 is displayed.
D
Nothing is displayed; the program results in an infinite loop.
D
Nothing is displayed; the program results in an infinite loop.
Consider the following program.
![The figure presents four blocks of code that consist of 6 lines. Throughout the third and fourth blocks of code there are nested blocks of code. Line 1: [begin block] val ← 0 [end block] Line 2: [begin block] sum ← 0 [end block] [Begin Block] Line 3: REPEAT 10 TIMES [Begin Block] Line 4: [begin block] val ← val + 2 [end block] Line 5: [begin block] sum ← sum + val [end block] [End Block] [End Block] Line 6: [Begin Block] DISPLAY [begin block] sum [end block] [End Block]](https://assets.learnosity.com/organisations/537/VR012544.g03.png)
Which of the following describes the result of executing the program?
Responses
A
The program displays the sum of the even integers from 2 to 10.
B
The program displays the sum of the even integers from 2 to 20.
C
The program displays the sum of the odd integers from 1 to 9.
D
The program displays the sum of the odd integers from 1 to 19.
B
The program displays the sum of the even integers from 2 to 20.
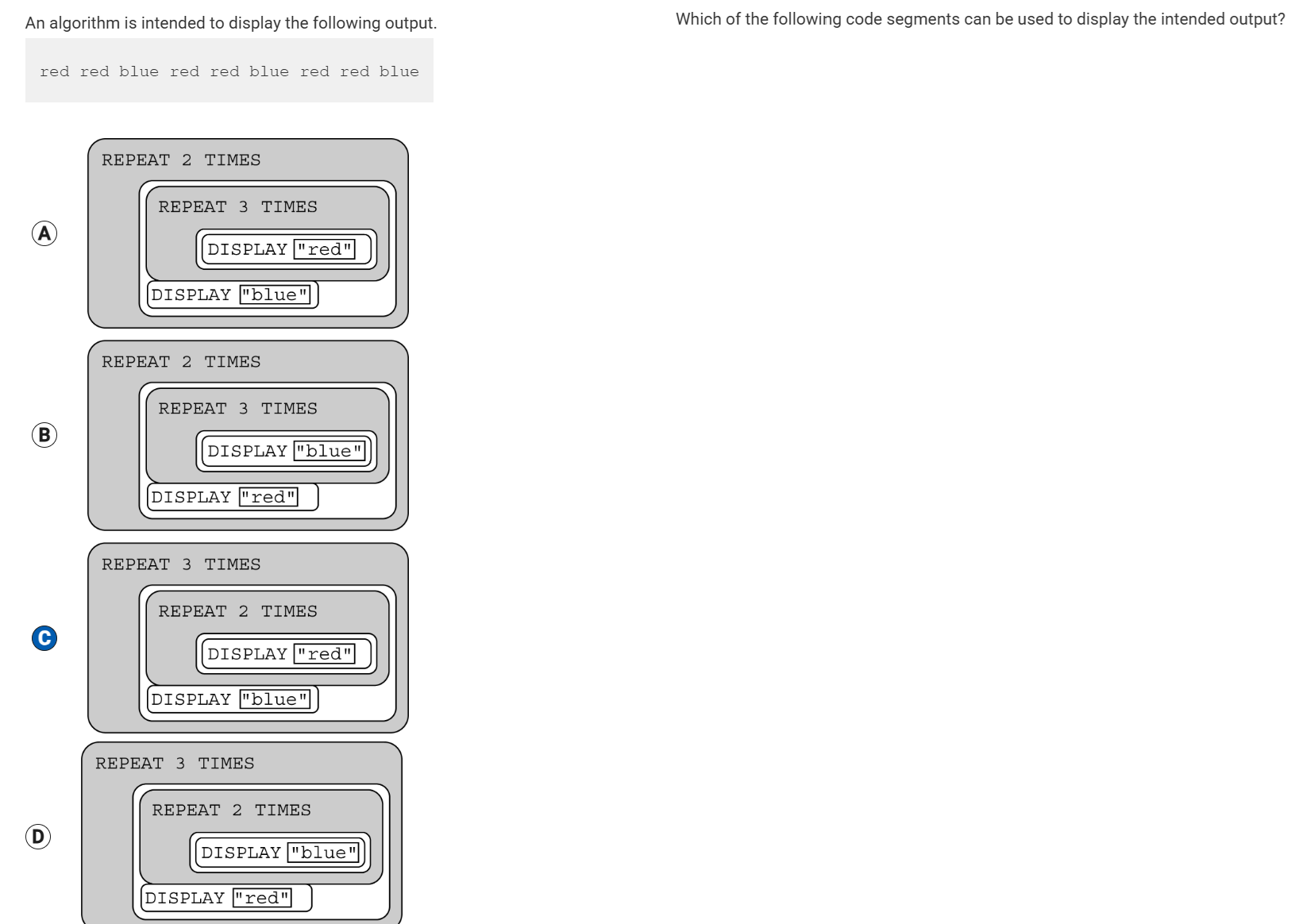

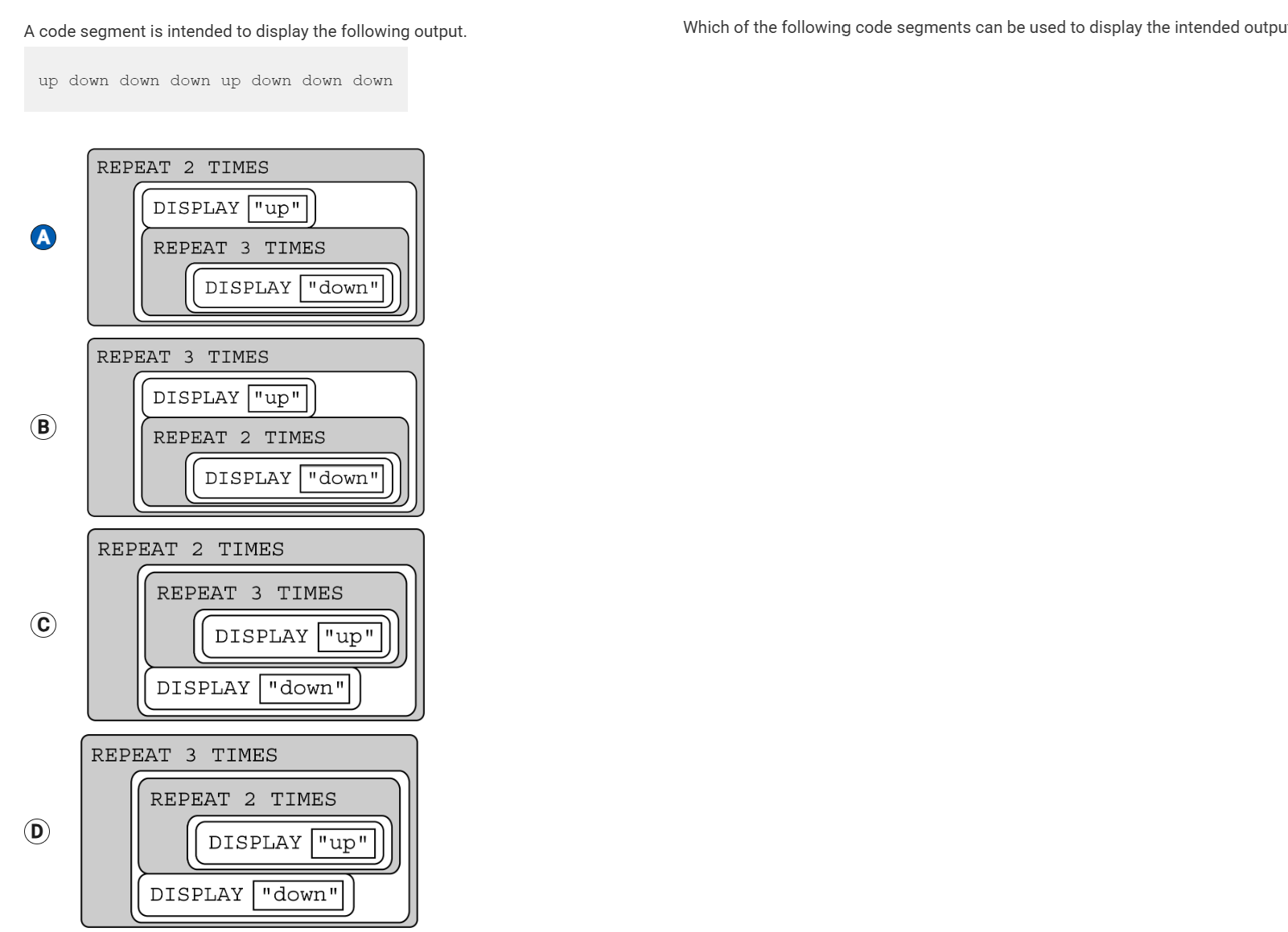
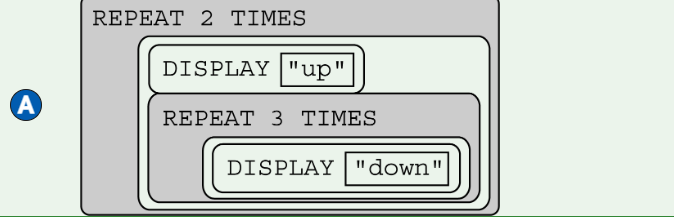
There are 32 students standing in a classroom. Two different algorithms are given for finding the average height of the students.
Algorithm A
Step 1: All students stand.
Step 2: A randomly selected student writes his or her height on a card and is seated.
Step 3: A randomly selected standing student adds his or her height to the value on the card, records the new value on the card, and is seated. The previous value on the card is erased.
Step 4: Repeat step 3 until no students remain standing.
Step 5: The sum on the card is divided by 32. The result is given to the teacher.
Algorithm B
Step 1: All students stand.
Step 2: Each student is given a card. Each student writes his or her height on the card.
Step 3: Standing students form random pairs at the same time. Each pair adds the numbers written on their cards and writes the result on one student’s card; the other student is seated. The previous value on the card is erased.
Step 4: Repeat step 3 until one student remains standing.
Step 5: The sum on the last student’s card is divided by 32. The result is given to the teacher.
Which of the following statements is true?
Responses
A
Algorithm A always calculates the correct average, but Algorithm B does not.
B
Algorithm B always calculates the correct average, but Algorithm A does not.
C
Both Algorithm A and Algorithm B always calculate the correct average.
D
Neither Algorithm A nor Algorithm B calculates the correct average.
C
Both Algorithm A and Algorithm B always calculate the correct average.
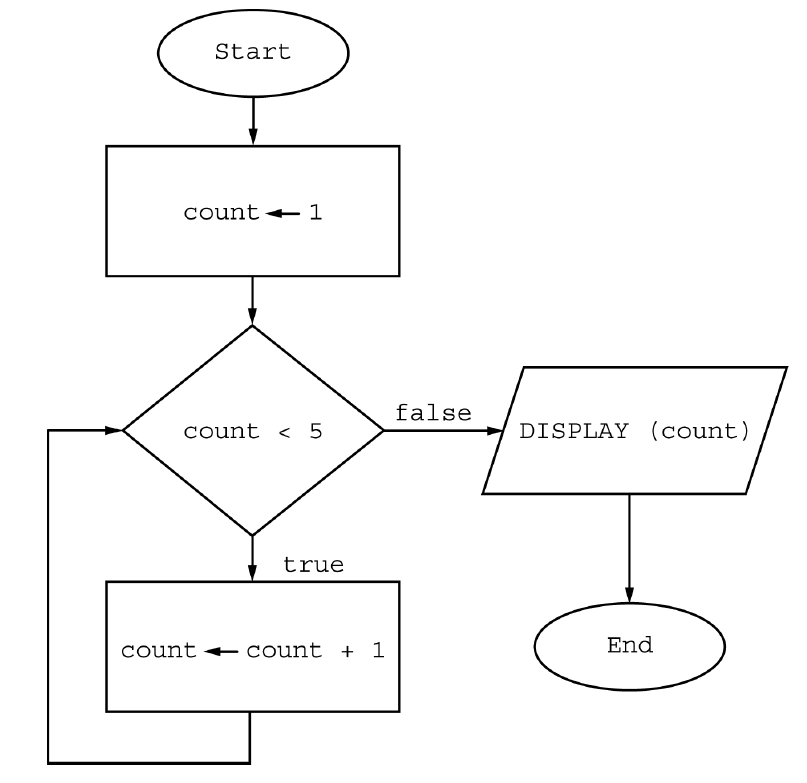
A flowchart is a way to visually represent an algorithm. The flowchart below uses the following building blocks.
What is displayed as a result of executing the algorithm in the flowchart?
Responses
A
5
B
15
C
1 2 3 4
D
1 2 3 4 5
A) 5
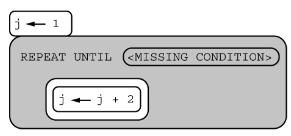
Consider the following code segment.
Which of the following replacements for <MISSING CONDITION> will result in an infinite loop?
Responses
A
j = 6
B
j ≥ 6
C
j = 7
D
j > 7
A) j= 6
In the program below, y is a positive integer (e.g., 1, 2, 3, …).
What is the value of after running the program?
Responses
A
y + 3
B
3y
C
y³
D
3^y
B) 3y
A flowchart provides a way to visually represent an algorithm and uses the following building blocks.
Block | Explanation |
Oval | The start or end of the algorithm |
Rectangle | One or more processing steps, such as a statement that assigns a value to a variable |
Diamond | A conditional or decision step, where execution proceeds to the side labeled true if the condition is true and to the side labeled false otherwise |
Parallelogram | Displays a message |
In the flowchart below, assume that j and k are assigned integer values.

Which of the following initial values of j and k will cause the algorithm represented in the flowchart to result in an infinite loop?
Responses
A
j = -5, k = 5
B
j = 0, k = 5
C
j = 5, k = 0
D
j = 5, k = -5
D
j = 5, k = -5
The following grid contains a robot represented as a triangle. The robot is initially facing right.

Which of the following code segments can be used to move the robot to the gray square along the path indicated by the arrows?
Responses