Networking Flashcards
1/173
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
174 Terms
What is the purpose of the network model?
To standardize processes at each layer
What are some limitations of network models?
They are theoretical and a protocol may not necessarily represent every layer
What two methods help detect lost packets?
Acknowledgements and sequencing
What corporation regulates port usage?
ICANN (Internet Corporation for Assigning Names and Numbers)
What is the range of registered ports?
1024 - 49151
What identifies a service running on a server?
Port or socket numbers
Layers of the OSI model
Application, Presentation, Session, Transport, Network, Data Link, Physical
Layers of the TCP/IP model
Application, Transport, Internet, Link
What port is DHCP (Dynamic Host Configuration Protocol) on?
UDP ports 67 and 68
What port is NNTP (Network News Transport Protocol) on?
TCP port 119
What port is SNMP (Simple Network Management Protocol) on?
UDP ports 161 and 162
What port is DNS (Domain Name System) on?
TCP and UDP port 53
What port is Telnet on?
TCP and UDP port 23
What port is TFTP (Trivil File Transfer Protocol) on?
UDP port 69
How does TCP handle data sequencing?
It breaks data into segments, numbers each segment, places them in a sequence, sends each one in order, waiting for an acknowledgement before continuing to the next segment
What is the difference between TCP and UDP?
TCP is more reliable but slower/resource heavy, UDP is quicker and lighter but does not use acknowledgements
What is used to keep two concurrent downloads seperate?
Session ID
What does the MAC sublayer do in the OSI model?
Defines unique hardware addresses for each device and allows devices to have access to LAN
What is used to get the IP address of a host from a known MAC address?
BOOTP (Bootstrap Protocol) and RARP (Reverse Address Resolution Protocol)
Used to transfer files
FTP and TFTP
Used to identify routes through an internetwork.
Open Shortest Path First (OSPF) and Routing Information Protocol (RIP)
What does the application layer do?
Prepares data to be sent through the network
The transport layer breaks data into…
segments, adding sequencing and control information
The network layer converts segments into…
packets, adding logical network and device addresses
The data link layer converts packets into…
frames, adding physical device addressing information
The physical layer converts the frames into…
bits, for transmission across transmission media
What OSI layer does this: Logical topology, hardware addresses, media access, framing
Data Link
What OSI model layer does this: Logical device identification, path identification, and selection
Transport
What OSI model layer does this: Flow control, reliable data transfer, windowing, segmentation, and sequencing
Transport
What OSI model layer does this: Converting data to 0s and 1s, bit signaling, and synchronization
Physical
What does CRC (Cyclical Redundancy Check) do in network communications?
Detects data errors
What sends email messages between mail servers?
Simple Mail Transfer Protocol (SMTP)
What sends messages to groups of users?
Internet Group Membership Protocol (IGMP)
What assigns IP addresses to hosts?
The Dynamic Host Configuration Protocol (DHCP)
What is used to get the MAC address of a host from its IP
The Address Resolution Protocol (ARP)
What functions are performed by IP?
Routing datagrams to their destination and identifying hosts with the IP address
You want to implement an Ethernet network using the 100Base-FX standard and the minimum hardware specifications possible. You need to support distances of up to 1,000 meters without repeaters.
SC connectors, Single-mode fiber optic cable
What characteristics does each fiber optic connector have: ST, SC, LC, MT-RJ
ST uses a bayonet-type connector
SC uses a separate push-on, pull-off connector
LC is half the size of other connectors
MT-RJ connector uses metal guide pins
What are features of multimode fiber cables?
They support limited distance cable lengths, have a core diameter of around 50-100 microns, and transfer data through the core with multiple light rays
What are features of single-mode fiber cables?
Transfers data through core with a single light ray, supports large amounts of data, core diameter of around 10 microns, supports large cable distance
When should you use a straight-through cable?
When connecting different network devices, such as a computer and switch
When should you use a crossover cable?
When connecting similar network devices directly, such as computer to computer or switch to switch
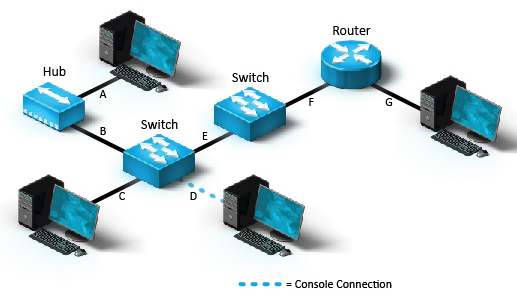
Determine whether each connection should use a straight-through or crossover cable.
A: straight-through (two different devices)
B: crossover (hub and switch are similar)
C: straight-through (two different devices)
E: crossover (two switches connected)
F: straight-through (two different devices)
G: crossover (PC is directly connected to router)
What is true about CAT 6 cabling?
It supports 10 GB ethernet connections, has a PVC insulation that surrounds each copper wire
What pins are used in Cat 5 ethernet UTP cable?
1, 2, 3, and 6. For Cat 5e and above, all eight pins are used.
You want to implement an Ethernet network using the 1000BaseT standard using the minimum hardware specifications possible. Which of the following should you include in your plan?
Cat5e twisted pair cable, RJ-45 connectors
Which fiber optic cable requires the exposed fiber tip to be polished as part of the assembly process?
Field terminated epoxy connectors
What connectors do fiber optic cables use?
LC, ST, or SC connectors. 100BaseFX, 1000BaseSX, and 1000BaseLX are all standards that use fiber optic.
What does RP (Address Resolution Protocol) do?
If a router does not know a destination device’s MAC address, it sends an ARP broadcast containing the destination device’s IP address and requesting its MAC address
What TCP/IP layer breaks data into pieces?
Transport
What TCP/IP layer prepares data to be sent?
Application
Which TCP/IP layer adds physical addresses?
Link
Which TCP/IP layer adds logical addresses?
Internet
What is the purpose of the frame check sequence (FCS) footer?
Checksum error detection
What does the OSI model call frames, packets, and segments?
Protocol data unit (PDU)
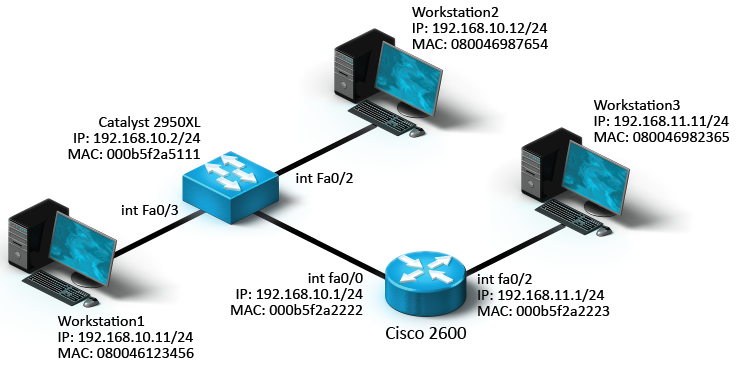
Workstation2 needs to send data to Workstation3. Identify the Layer 2 and Layer 3 addresses Workstation2 will use to send the data
The source Layer 2 address is its own MAC address, 080046987654.
The source Layer 3 address is its own IP address, 192.168.10.12.
The destination Layer 2 address is the MAC address of the default gateway router, 000b5f2a2222. The MAC address is the address of the interface connected to the same subnet as Workstation2.
The destination Layer 3 address is the IP address of the destination device (Workstation3), 192.168.11.11.
The process of breaking a message into packets, adding control information and other information, and then transmitting the message through the transmission medium is known as…
Encapsulation
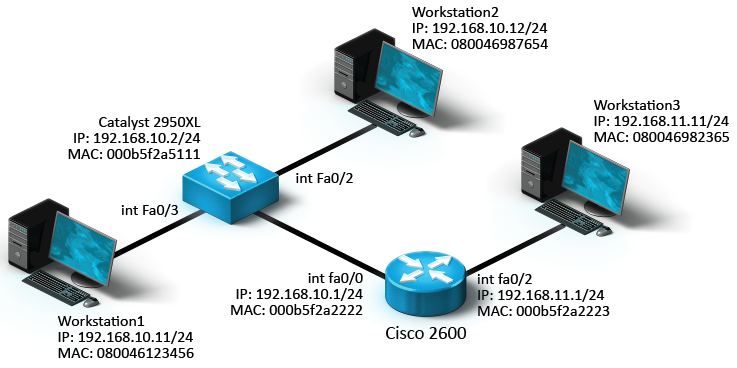
Workstation3 has started communicating with Workstation2. It sends a frame to the default gateway. Identify the Layer 2 and Layer 3 addresses used by the Cisco 2600 router to forward the data to Workstation2
The Cisco 2600 router is the default gateway. When it receives a frame from Workstation3, it examines the Layer 3 address in the packet to locate the destination device. Then it creates a new frame and modifies the source and destination Layer 2 addresses (MAC addresses) as follows:
The source Layer 2 address is its own MAC address on the same segment as the destination device, 000b5f2a222.
The destination Layer 2 address is the MAC address of the destination device, 080046987654.
The source and destination Layer 3 addresses (IP addresses) do not change.
The source IP address is the IP address of Workstation3 is 192.168.11.11.
The destination IP address is the IP address of Workstation2 is 192.168.10.12.
What are features of full-duplex ethernet?
collision-free, uses direct point-to-point connections
What is the backoff on an Ethernet network?
The random amount of time a device waits before retransmitting after a collision.
What is true of CSMA/CD (Carrier Sense Multiple Access with Collision Detection)?
If collisions are detected, an interrupt jam signal is broadcast to stop all transmissions, A device with data to send first listens to the transmission medium to determine whether it is free.
What is true of Gigabit Ethernet?
It uses CSMA/CD and can use both copper and fiber optic cabling
What is the maximum number of hosts supported on a subnet?
1024
The ethernet frame component that is a set of ones and zeroes terminated by two ones.
Preamble
The ethernet frame component that is information that needs to be transmitted between hosts
Packet
Ethernet frame component that verifies that the data arrived uncorrupted
Frame Check Sequence
Ethernet frame component that identifies the receiving host’s MAC address
Destination address
Ethernet frame component that is junk data required to make 64 bytes
Pad
Ethernet frame component that identifies the sending host’s MAC address
Source address
Ethernet frame component that specifies the network/internet layer protocol being used
Type
What is true of half-duplex ethernet?
It uses collision detection and recovery, and sends both signals along the same wire
What is the maximum cable length for UTP Ethernet T implementations?
100 meters
What do bridges do?
They connect two network segments with the same network address and convert one type of transmission medium into another
What is the function of a dedicated wireless access point on a network?
It acts as a bridge between the wireless and wired segments on the same subnet
Why is DNS important?
It translated human-readable domain names into IP addresses
What are the advantages of using routers on a network?
Routers provide multiple links between devices to support load balancing, they provide feature like flow control, error detection, congestion control, etc. and support multiple routing protocols for better flexibility
You have been put in charge of connecting two company networks that were previously separated.
You need to connect a 100BaseTx Ethernet network with an older token ring network. Most traffic will be localized within each network, with only a little traffic crossing between networks. Both networks are using the TCP/IP protocol suite.
Which connectivity device would be the best choice in this situation?
Router. Both networks use a different architecture but are using the same protocol.
What does DHCP (Dynamic Host Configuration Protocol) do?
Automatically assigns IP addresses to devices
What layer of the OSI model do network switches operate that do not support routing?
Data Link. Multi-layer switches operate at higher layers than this.
What is the difference between Telnet and SSH?
SSH provides encrypted communication while Telnet transmits data in plaintext. Having both enabled could undermine the security of Telnet.
You are troubleshooting a network switch that has lost remote connectivity due to a misconfiguration. Remote access methods such as SSH and HTTPS are no longer functional.
Which of the following actions should you take to regain access to the switch and resolve the issue?
Connect a console cable to the switch and access it through a terminal application on your computer.
What memory type stores the running-config gile, routing tables, and ARP tables?
RAM
What memory type stores the startup-config file?
NVRAM
What memory type stores the Cisco IOS software?
FLASH
What memory type stores POST and the boot loader software?
ROM
You have issued the following command and received the response as shown.
Router#sh start
%%Non-volatile configuration memory has not been set up or has bad checksum
Which of the following is a reason for this response?
No config file has been saved to NVRAM.
If you need to use Telnet on a legacy router, how could you make it more secure?
Use Telnet over a secure VPN connection.
What are the necessary components to make a console connection from PC to router?
Rollover cable, console port, and terminal emulation program
What should you do to properly implement HTTPS on a wireless controller that supports both HTTP and HTTPS?
Install a valid SSL/TLS certificate on the wireless controller and disable HTTP access. HTTPS relies on SSL/TLS encryption to secure communication.
What cable do you use to connect a laptop to a router for troubleshooting?
Rollover cable
What should you do to secure access to a router?
Keep the router in a locked room, set a password and use the login command.
What is the order of events during the boot sequence?
Power-on self-test checks hardware, boot loader software is loaded, IOS is loaded, and the startup-config is loaded.
What command should you use to save the NVRAM config file to a TFTP server?
copy start tftp
Which command would you use to remove the contents of NVRAM?
erase nvram
What command do you use to see the previous list of commands stored in the history buffer on a cisco device?
show history
What should you use to view a list of commands available in the current mode on a cisco device?
?
What command should you use to save the current config to NVRAM?
copy run start
What command should you use to load the current configuration saved in NVRAM into memory?
copy start run
What command saves the current config to a network server?
copy run tftp
What command copies a config file from a network server into NVRAM?
copy tftp start