ISC- S1
1/47
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
48 Terms
1 NIST background

2 CSF core-6 parts definitions

3 CSF core-6 parts image graph
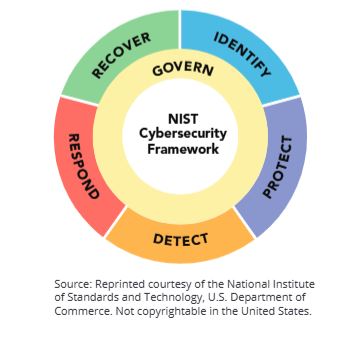
4 CSF tiers- tier 1 (partial), tier 2 (risk informed), tier 3 (repeatable), teir 4 (adaptive) chart
5 national institute of standards and technology (NIST) privacy framework
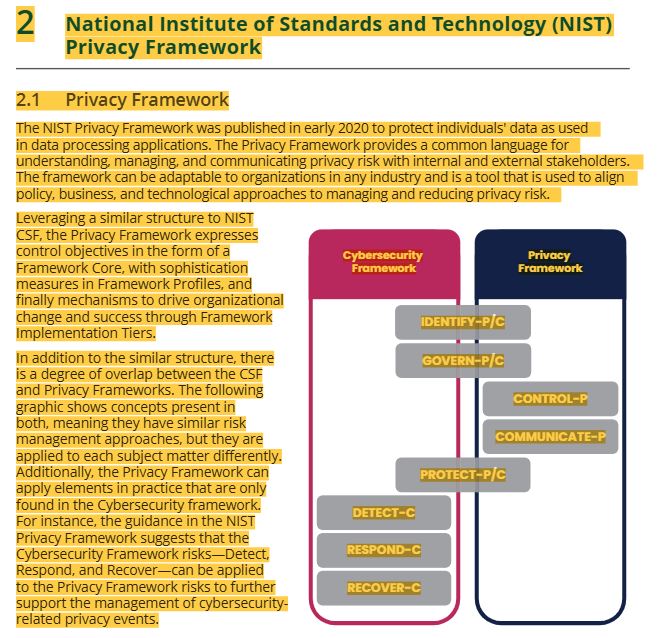
6 NIST privacy framework 8 questions (identify-P, govern-P, control-P, communicate-P, protect-P, detect, respond, recover
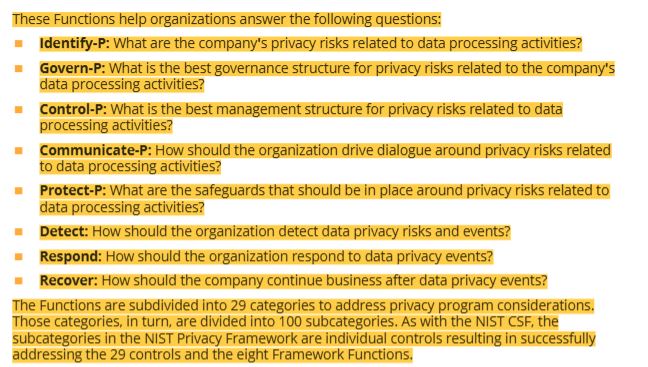
7 framework implementation tiers (key differences)
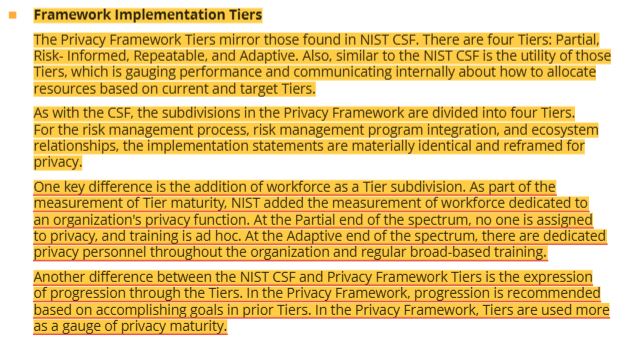
8 NIST security and privacy controls- SP 800-53, purpose and applicability, office of management and budget (OMB), federal information security modernization act (fisma)
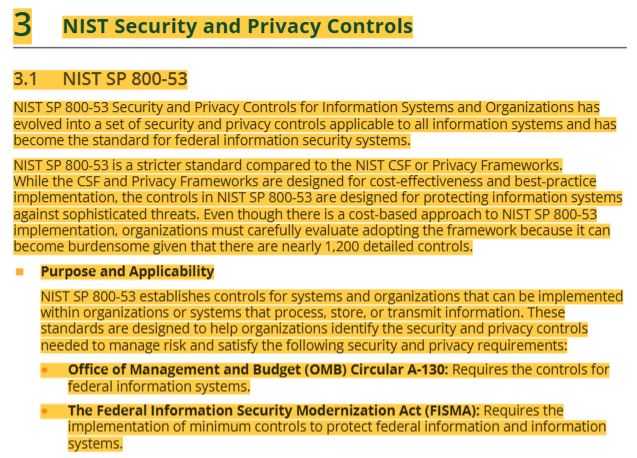
9 target audience intended for NIST SP 800-53

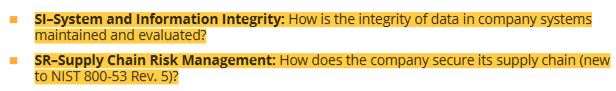
10 nist sp 800-53 different control families with 20 questions they seek to answer

10 nist sp 800-53 different control families with 20 questions they seek to answer (final 2 questions)
11 health information technology for economic and clinical health (HITECH) act of 2009

12 general data protection regulation (GDPR)

13 privacy shield

14 the 6 goals and 12 requirements for PCI DSS
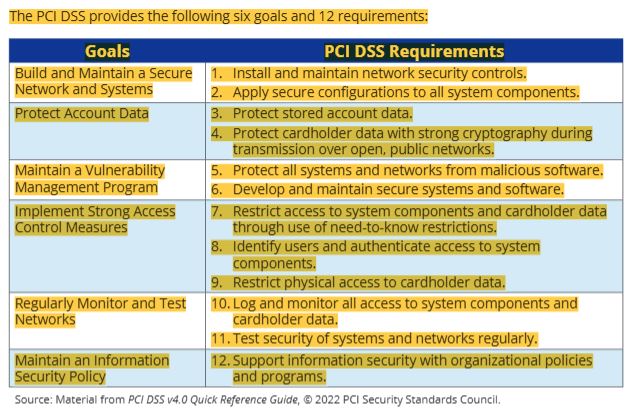
15 adhering to each of the 12 PCI DSS requirements involves the following (12 things)

16 implementation groups- IG1, IG2, IG3

16 design principles of CIS controls-context, coexistence, consistency

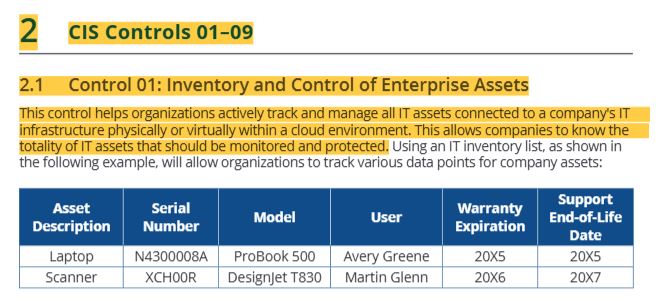
17 CIS controls-control 01 inventory and control of enterprise assets
18 CIS controls-control 02 inventory and control of software assets

19 CIS controls-control 03 data protection

20 CIS controls-control 04 secure configuration of enterprise assets and software

21 CIS controls-control 05 account management

22 CIS controls-control 06 access control management

23 CIS controls-control 07 continuous vulnerability management

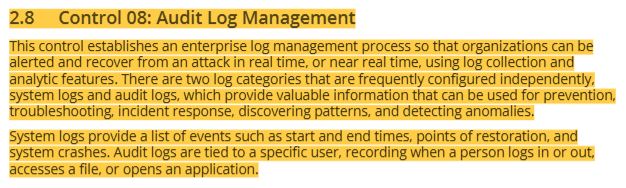
24 CIS controls-control 08 audit log management
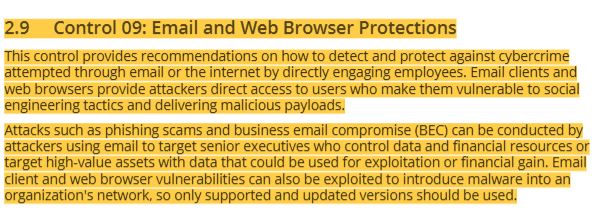
25 CIS controls- control 09 email and web browser protections
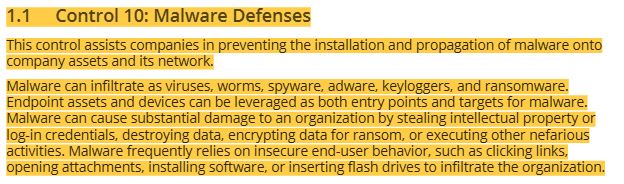
26 CIS controls- control 10 malware defenses
27 CIS controls- control 11 data recovery

28 CIS controls- control 12 network infrastructure management

29 CIS controls- control 13 network monitoring and defense

30 CIS controls- control 14 security awareness and skills training

31 CIS controls- control 15 service provider management

32 CIS controls- control 16 application software security

33 CIS controls- control 17 incident response management

34 CIS controls- control 18 penetration testing

35 control objectives for information and related technologies (COBIT)
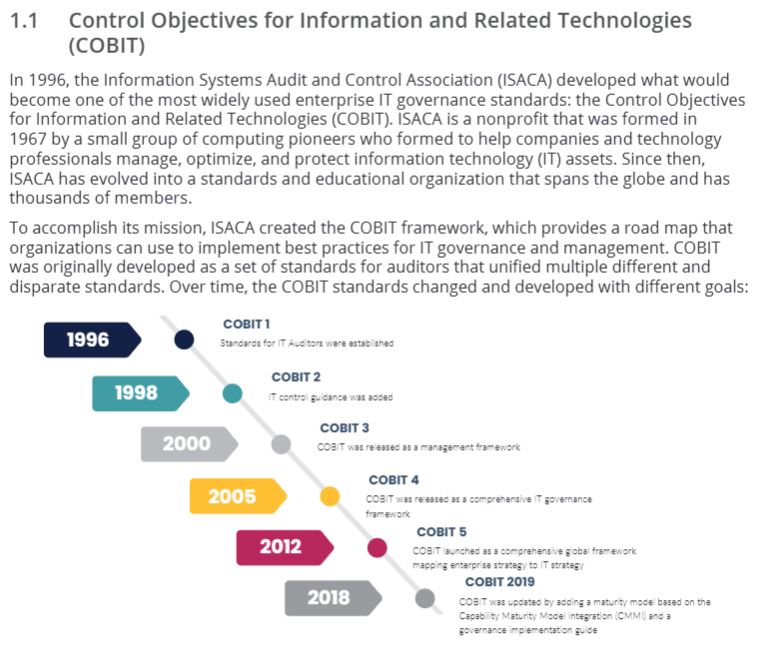
36 COBIT 2019 overview
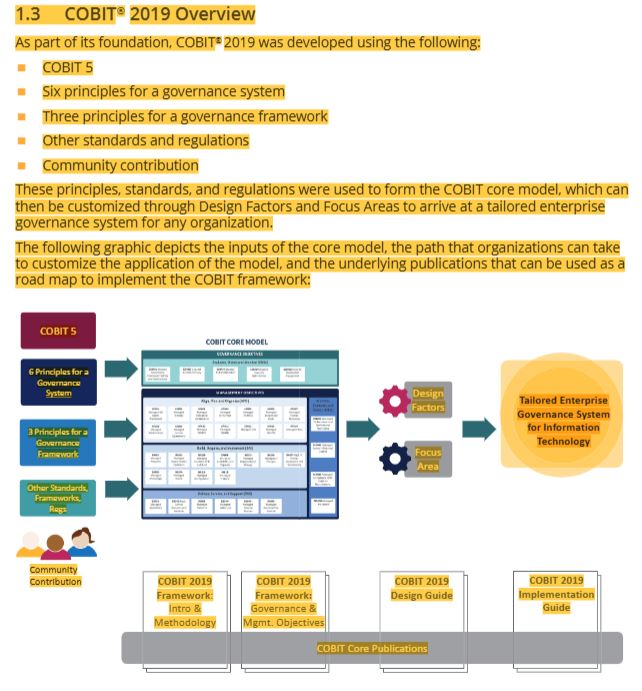
37- 6 principles for a governance system

38- 3 principles for a governance framework
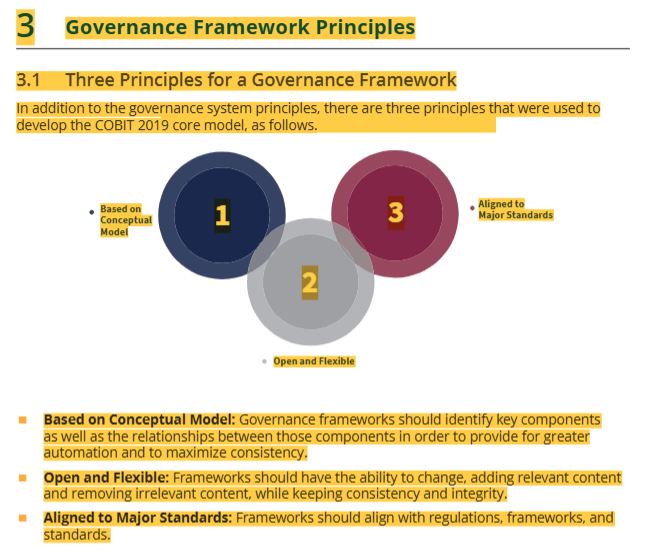
39 COBIT core model definition

40 COBIT core model chart
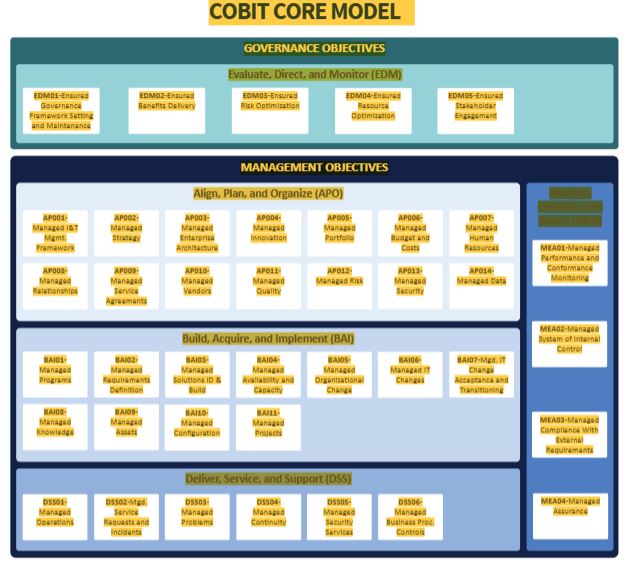
41 governance objectives are grouped into one domain-evaluate, direct and monitor (EDM)

42 management objectives have 4 domains- align plan and organize (APO), build acquire and implement (BAI), deliver service and support (DSS), monitor evaluate and assess (MEA)

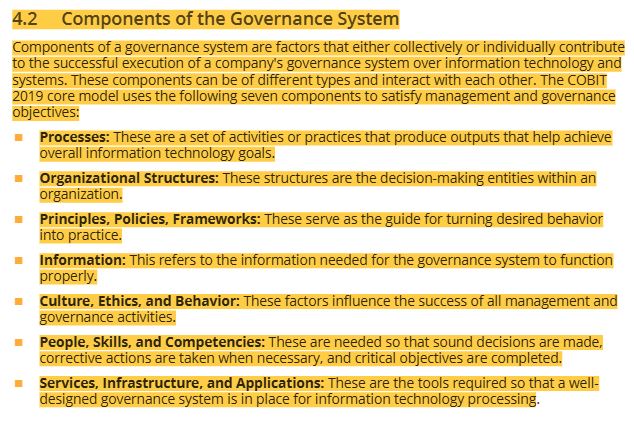
43 components of the governance system-7 components
44 design factors (5 of the 11 components)
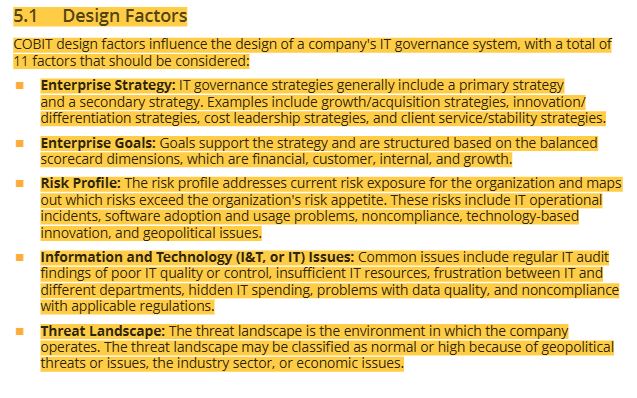
45 design factors (6-11 components continued)

46 COBIT core publications