AQA GCSE Computer Science
1/68
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
69 Terms
Data
Consists of raw facts and figures without context or meaning.
Information
What exists when data has been given context or meaning.
Clock Speed
The clock speed of a CPU is measured in Hertz (Hz). One Hz means one operation per second.
Factors which can Influence the Speed of a CPU
The speed of other components, the CPU might be waiting for a hard disk or printer to perform some task before the next instruction is addressed.
The size of the cache, the larger the cache, the more it scan store, and the faster the CPU appears to work because it is not waiting as long to receive data or instructions.
The number of cores, each core can fetch, decode and execute. More cores mean a faster CPU.
Cache Memory
High-speed memory that stores frequently needed instructions or data. Stores copies of data or instructions from the RAM that are accessed very regularly.
RAM
Random access memory. The RAM is volatile, when the computer is turned off or subject to a loss of power, the content of the RAM is lost. When a program is loaded from a computer hard disk, its data and instructions are loaded into the RAM.
ROM
Read-only memory. Means that the content cannot be edited or deleted. It stores data or instructions that will not need to be updated.
Flash Memory
Uses electronic chips as storage but, it is non-volatile. This means it continues to store data without a source of electricity. Flash drives are portable and are often used to transfer data from one computer to another.
Virtual Memory
Sometimes a computer does not have enough RAM to run programs as it is required to. In these circumstances, the operating system will treat some part of secondary storage as if it were the RAM. This is called virtual memory.
Magnetic Storage Devices
Include the internal hard disk as well as floppy disks, which are no longer widely used.
Optical Storage Media
CDs, DVDs, Blu Ray Disks are written to and read using lasers. The surface of the disk will have billions of locations where holes can be either physically burned by a laser, or not burned, to represent either 1 or 0. Capacity: CDs 700MB, DVDs 4.7GB, Blu-Rays 25GB. Speed is highly variable. Small and light but not as easy to carry as a USB flash drive. Sturdy, although the surface can be scratched and make the data irretrievable. Useful for posting data from one location to another.
Solid-State Storage Devices
Use electronic circuits and no moving parts to store data electronically. Ranges from 1GB to 64GB. Transmits data at a rate of 5 million bits per second. Very small and light, designed to be moved between computers. Sturdy. Used by students who always need to access work on different computers.
Cloud Storage
Refers to data being stored away from the computer it is accessed on, typically accessible over the internet. Capacity, virtually unlimited. Speed, depends on the internet connection speed but it is generally slower than storing data on the computer which will be used to access it. You can access your data anywhere in the world. Data is backed up multiple times so durability is not an issue.
Internal Hard Disk
Keeps programs and data stored when the computer is turned off. Capable of storing more than its main memory. Capacity, variable, data transfer is usually far quicker than from any external device. Difficult and time consuming to move an internal drive from one machine to another. Well protected inside the computer. Most programs are stored on here.
Units of Data
(Size and Example of Storage)
Bit - Single binary digit. Either a '1' or '0'.
Nibble - A sequence of four bits. A whole number between 0 and 15.
Byte - A sequence of eight bits. An individual keyboard character such as 'k' or '#'.
Kilobyte - Approximately 1,000 bytes. A paragraph of text.
Megabyte - Approximately 1,000 kilobytes. Around one minute of MP3 music.
Gigabyte - Approximately 1,000 megabytes. About 90 minutes of video.
Terabyte - Approximately 1,000 gigabytes. Several hundred hours of video.
ASCII
ASCII characters, requiring only seven bits, need less storage space but can only store 128 different characters.
How Dates can be Stored
As a sequence of ASCII characters, every individual character can be stored using its ASCII code.
As a series of numbers.
There are more commonly stored as numbers, because this requires less storage space and two dates can easily be compared to see which is earlier or later.
Images
An image is divided into pixels. A pixel can only be one colour at a time, and when a picture is saved, the colour of each pixel must be stored in binary. The more bits that are used to store each pixel, the more colours are potentially available.
Sound
When converting sound to digital format, two things influence how much storage space is needed:
Sampling rate - Refers to how often the computer takes a measure of the sound, including the volume and frequency. A higher sampling rate results in better sound quality, but requires more storage space.
Bit rate - How many bits are used to each sample and this can vary widely. Again, higher bit rates result in higher quality of sound but also higher storage requirements.
Software Development Life Cycle
Spells out what steps take place in the process of developing software and the order in which they take place. There are several models of the life cycle.
Cyclical Model (Definition, Advantages and Disadvantages)
The processes happen repeatedly, and in the same order during each cycle.
+ It is easy to arrange subtasks and set milestones.
+ Clearly defined stages make management straightforward.
- A testable program is not available until late in the cycle.
- It is difficult to accommodate change once you have passed the relevant process.
Waterfall Model (Definition, Advantages and Disadvantages)
Each process takes place, from top to bottom, to completion before the next process begins.
+ It is easy to manage, as the whole process is readily divisible into smaller processes.
+ It is easily understood and used.
- Unsuitable for larger projects or projects with changing requirements.
- Not all projects can be so easily broken down into processes like this, some processes may overlap.
Spiral Model (Definition, Advantages and Disadvantages)
Similar to the cyclical mode, except each process is visited multiple times in that sequence. Each time a process occurs, it occurs in a more developed way than the last time it occurred.
+ Good approach for larger projects, as changes can be implemented throughout the project.
+ A working prototype can be made available fairly early.
- Each spiral model approach will be different, meaning less reusability.
- Not appropriate for smaller projects where multiple passes may be unnecessary.
Feasibility Study
The main purpose of this is to examine an existing system to find out whether or not it is worthwhile replacing it with a different system. Replacing a system has certain costs:
Money for software developers, hardware etc.
Time, designing and installing the new system is time consuming.
Human resources, specialist staff are needed to design and install the system and existing staff would need to be retrained to operate it.
Benefits of replacing a system:
May be possible to do a job faster.
May be cheaper to operate, requiring less staff.
Analysis
The main purpose is to understand the existing system as well as the requirements of the proposed system. The following steps may be taken:
Using the current system as a current user might use it.
Studying system documentation.
Interviews/questionnaires of customers/staff to seek their opinion.
Observing the current system in use.
Exploring data requirements.
Producing diagrams showing processing and entities.
Design
Designing a new system is split into a number of sections. A design is simply a detailed plan for the proposed system.
Designing algorithms - They must be well designed otherwise it can affect the speed of a process, such as searching or sorting.
Designing HCI - Involves the design of how the computer and human will interact with each other, involving hardware and software.
Designing data structures - Records, arrays, variables etc. need to be decide upon.
Testing
Is the point at which the program is checked to address two main questions:
Does the program do what it was intended to do?
Does the program function correctly?
Changeover
Is the point where at which the user moves from the old system to the new system. There are several ways in which this can take place:
Direct - Where the changeover is sudden and complete.
Parallel - Both systems run at the same time for a while, this is beneficial because in the event of a problem, the old system is still available for use.
Phased - Elements of the new system as introduced one at a time.
Pilot - A single department may change to the new system in a company, and then the rest of the organisation would follow later.
When choosing, it is important to consider the cost of implementing it and the disruption that could be caused.
Maintenance
When the changeover is complete, the work of the developer is not complete. Maintenance means ensuring the product continues to be beneficial to the customer.
Perfective maintenance - Making the system easier to use or adding new features, making the system as good as it can be for the purpose.
Adaptive maintenance - Making changes to the system as the needs of the customer change.
Corrective maintenance - Solving problems that occurred during the creation of the new system that wee not discovered at the time.
Documentation
At various points during the life cycle, documentation needs to be provided by the developer for a variety of purposes:
Design documentation, of the interface and the processes, are needed by the end user as soon as possible to check what is going to be produced is what is required.
Program documentation, including annotated code and design of data structures, must be available to the developer during testing and maintenance.
During testing, a log of results will be produced in an ongoing cycle, until the system is deemed to be working correctly.
User manuals must be available to the customer to provide details on how to operate the system.
Technical manuals are also needed to detail things such as security procedures, backup procedures and system recovery procedures.
Prototyping
One way of developing solutions in which a basic version of the finished product is created quickly.
End user uses prototype --> Feedback from end user is obtained --> Prototype is updated.
+ Because the end user is always involved, time spent on unnecessary features is minimized.
+ There are multiple opportunities for errors to be detected, so they are usually detected sooner.
+ Testing of the solution can begin far sooner than in the cyclical development model, allowing more time to find errors.
- It is quite easy for the solution to become more complex than initial plans.
- Beginning the process by producing a prototype might mean the analysis stage is not completed as thoroughly as it should be.
- Lots of opportunities exist for the end user to change their minds, which can result in higher costs in terms of money and time.
Unit/Modular Testing
Solutions can be broken down into modules. This makes the solution easier to understand and allows straightforward distribution of tasks among a team of programmers.
Alpha Testing
Carried out by the developer. Individual algorithms tested, with the values of variables being traced through the program, often line by line. This type of testing makes use of trace tables, where expected variable values are compared with the actual outcome.
Beta Testing
Carried out by prospective purchasers of the finished product. Users use it as they would normally use such a program, reporting any errors back to the developers.
Acceptance Testing
Carried out by the end user. This type of testing is intended to answer the question 'does the program do what I wanted it to do' rather than 'does the program work'.
Network
Collection of computers and other hardware that has been connected together in order to allow communication and sharing of resources. Also, networks allow software to be installed and controlled across the network from a single computer, rather than individually on every machine.
LAN
Local area network, which might occupy an office or building.
WAN
Wide area network, the largest of which is the internet.
Advantages of Networks
Communication - Email, instant messaging and the transferring of files is possible across a network.
Sharing of resources - Files on one computer can be accessed by others, multiple computers on a network can share a single printer and within a LAN, a connection to the Internet can be shared.
Network management - You may be able to log onto any computer within a LAN and have access to your own files, which is particularly useful in schools and colleges.
Disadvantages of Networks
Viruses and other malware can only move from computer to computer via shared disks or through a network. A network computer is more likely to become infected compared to a stand alone computer.
Failure of a single resource can impact upon all computers on a network. If a logon server fails, it may be nobody can access their account.
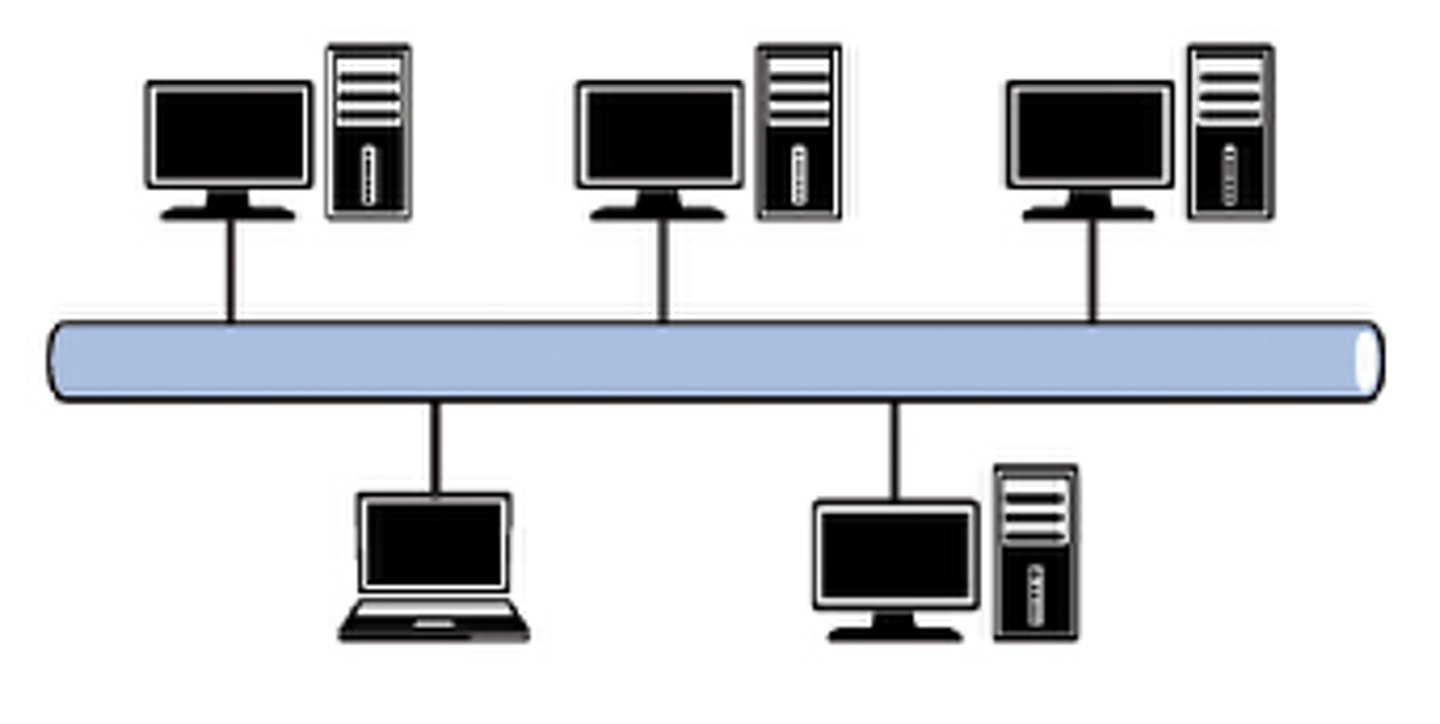
Bus Topology
All devices are attached to a common connection medium, known as the backbone. Any communication must travel through this medium. A server may be attached, or a printer or a router if the network needs to provide access to the internet. At either end of the backbone is a terminator, which marks the end of a network.
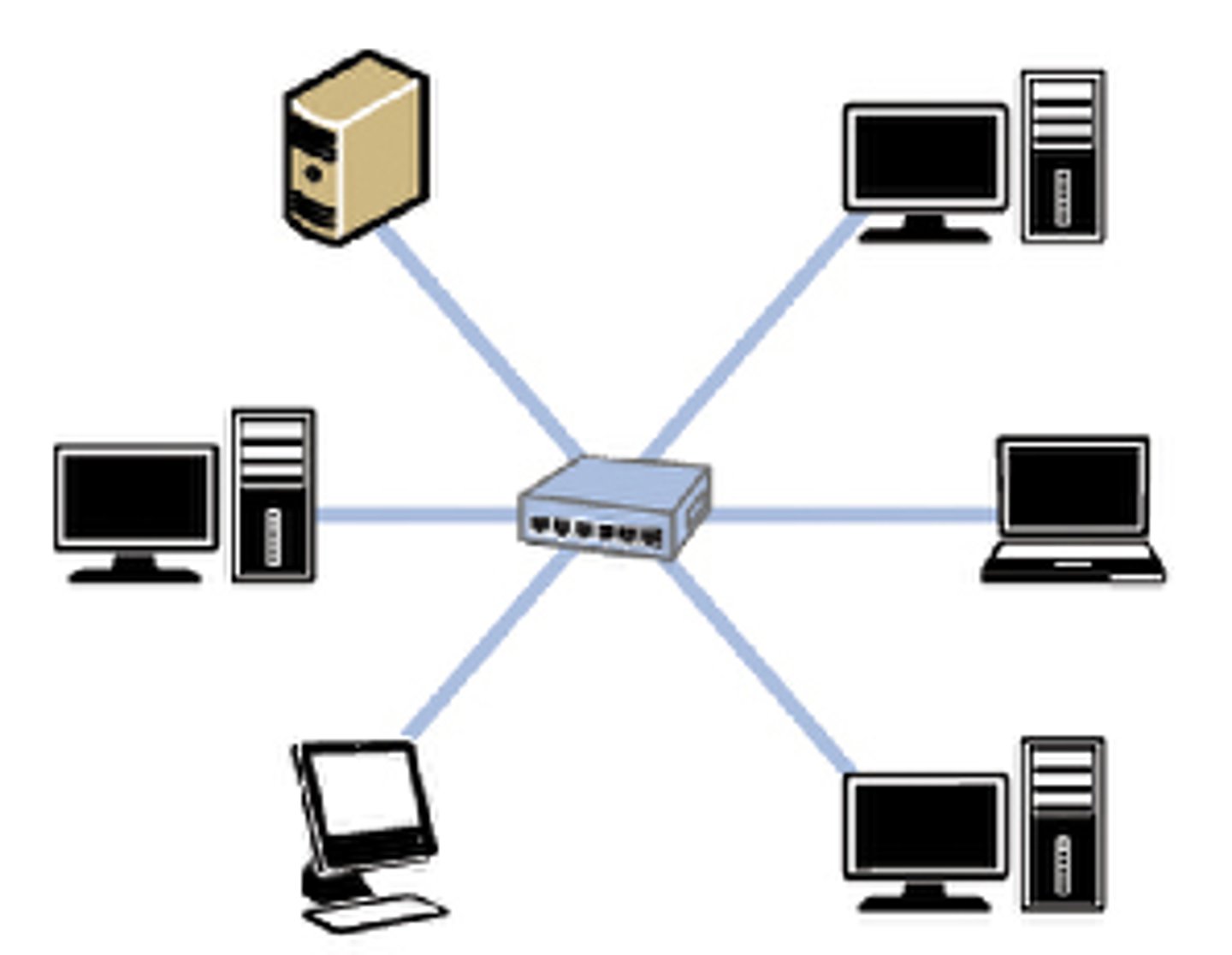
Star Topology
All devices are connected to a single central device, such as a switch or a hub. Communications must go via this central device. Servers, printers and routers would also be connected to this device.
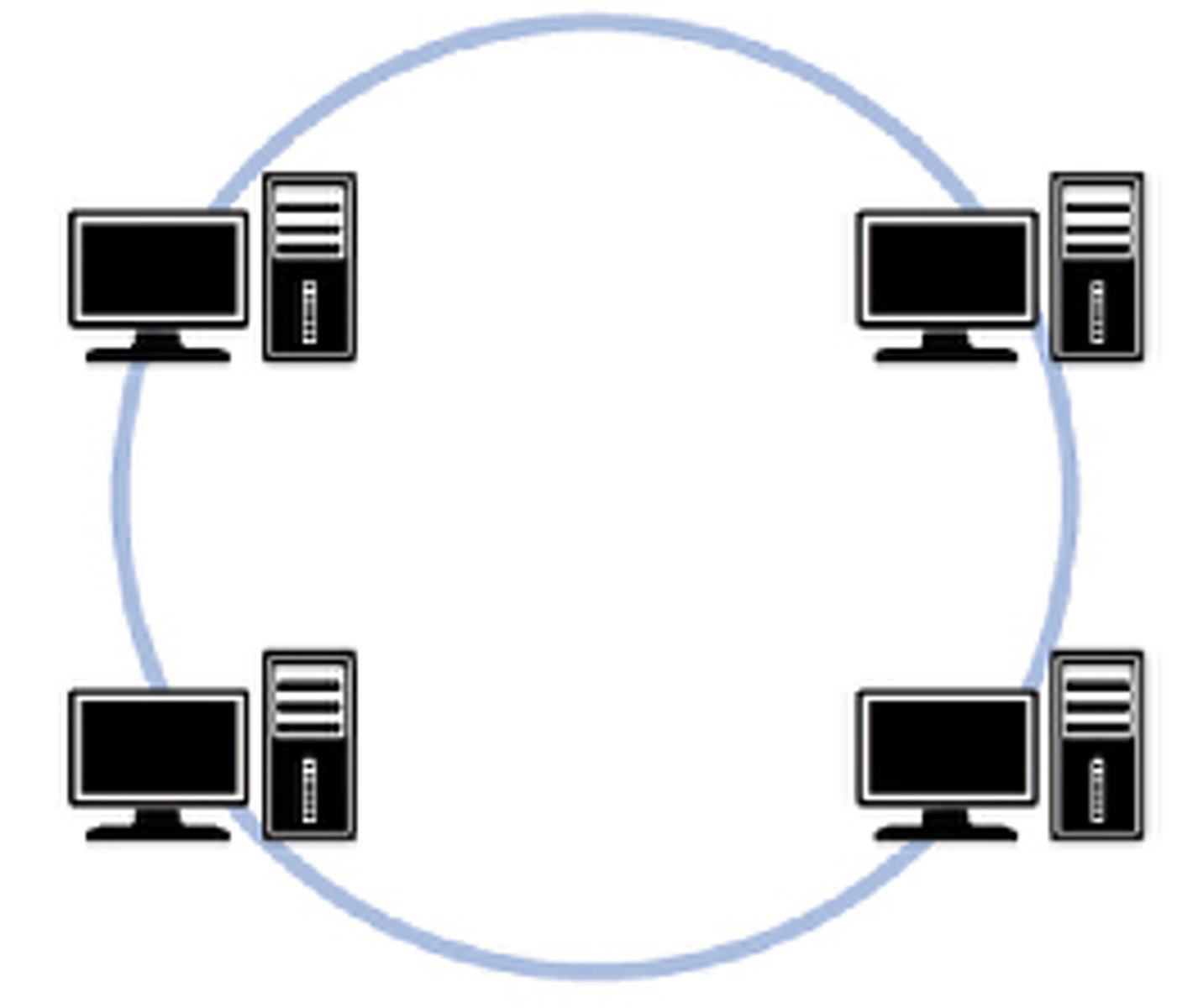
Ring Topology
Each device is connected to two other devices, so that the devices and connection media make up a shape of a ring. To communicate with a particular device, a signal often has to pass through several other devices en route.
Advantages and Disadvantages of a Bus Topology
Very cheap, as it requires minimal amount of cabling.
Easy to add or remove computers.
Failure in the main cable will cause failure of the network.
The network can be significantly slowed by high network traffic.
Advantages and Disadvantages of a Star Topology
If one cable fails, only the device attached to it is isolated from the network.
Faults are easy to find.
It is easy to add extra devices.
The system is secure, as data is only sent to devices that need that data.
Lots of cable, which means more expensive to install than other topologies.
Advantages and Disadvantages of a Ring Topology
No collisions, as there is typically only one batch of data allowed on the network at any one time.
Very high rates of transmission are possible.
Failure of a single cable can bring down the entire network.
Failure of a single device can bring down the entire network.
Security is not ensured, as data passes through other devices en route to its final destination.
Client Server Model
Many networking applications take place according to the client server model. The 'client' and the 'server' are two machines that communicate with one another. The server provides some service that the client uses. The client machine would, based on some user input, request something from the server, which the server would then supply.
Handshaking
This is a pre-planned system of signals designed to check that each device is ready to send/receive signals.
Web Application Concepts
When developing client server applications, some code may reside within the client machine, and some within the server machine. There are certain tasks that lend themselves to be server-side and others that are usually client-side.
Client-Side Code
Code stored on the client machine can run even when there is not a connection to the server is client-side code. This code will normally be downloaded in full as a web page is opened and it is likely to carry out some of the following:
Making buttons change colour when the mouse rolls over them.
Displaying pop-up messages.
Clearing all text boxes in a form.
Validating entries into text boxes (checking that all text boxes contain appropriate data before a form is transmitted).
Server-Side Code
Stored on the server machine and is run when a request is received by the server from the client. Any attempt to run server-side code requires a connection between the client and the server. Tasks typically performed by sever-side code include the following:
Accessing a small part of an online database too large to be downloaded in full.
Providing security, controlling what users have access to.
Providing a login facility with user accounts, such that a user can only see their own account.
E-commerce applications involving shopping carts and payment options.
CSS
One language that allows for programmers to use code they have written in the past and code other programmers have written. It specifies how web pages are to be formatted.
Advantages and Disadvantages of CSS
+ There is no limit to the number of HTML documents you can link in a single CSS document, so you could potentially change the formatting of a million web pages by changing one CSS document.
+ By adopting this approach, a website would have a consistent, professional appearance, with all web pages having the same layout and colour scheme.
- Initial set up of a CSS document can be time consuming and if the website consists of only a few pages, using CSS might not be an efficient use of time.
- Any error in the CSS document would essentially replicate itself across the entire site.
Other Languages
When writing a program, you might want to make use of the code you have written yourself previously or code that someone else has written. Obtaining code from external sources comes in three forms:
Importing - A class allows you to use procedures and functions without having to engage with that class's code at all.
Copying and Pasting - Used particularly when so much code is available on the Internet.
Executable files - Can simply be run by your own program.
Advantages and Disadvantages of Code from External Sources
+ Usually quicker than creating it yourself.
+ Generally have been tested by its creator, so it is usually reliable.
+ Much code is available free of charge.
- There is no guarantee that it is good quality code.
- If you copy and paste, you may need to spend time resolving variable names and imports.
- Relying on executable files might not work on other computers, which could have their files in different locations.
- May be that the code you require is simply too complex for you to understand it and integrate it into your solution.
Database
A collection of related data items stored systematically in a file system. Databases consist of several key elements.
Tables, Fields, Records
The table stores data. There are records within a table, a record is one instance of something. There are also fields, a field is a placeholder for a single piece of information about each record.
Primary Key
A table has a primary key. This is a field that uniquely identifies a record.
Foreign Key
Some tables have a foreign key. This is used to link two tables together. A relationship is said to exist between two tables, usually between a primary key and a foreign key, but sometimes between two primary keys.
Relational Database
Is one that contains more than one table with at least one relationship.
Flat File Database
Contains one table, with no relationships.
Query
A query is a way of interrogating a database to find out specific information, without having to read through whole database tables yourself.
Structured Query Language (SQL)
This is a language used to manipulate the content of database tables. It can be entered directly into a database console or embedded in another language. There are four SQL commands: SELECT, INSERT, UPDATE and DELETE.
Evaluating Effectiveness
In determining how effective a program is, the success criteria needs to be examined. Success criteria are a list of objectives that must be met in order for a program to be considered successful. The list is drawn up at the start of a project and is consulted at the end to see how successful the project was. Examples include:
- The program will run on 500 computer simultaneously.
- 99% of SQL commands will be executed in under 0.1 seconds.
- The interface font size can be adjusted to anywhere between sizes 10 and 40.
- The program will function identically on all major web browsers.
Determining success might require different approaches, including talking to end users, testing that required features exist and work properly, observing the program being used or timing processes to check that they run quickly enough.
Ethical Issues
Ethical refers to something being right or wrong.
- Would it be ethical for a government to store an electronic profile of the DNA of its entire population, of criminals, of immigrants, etc.?
- Is it ethical to use cheap labour in foreign countries to produce software less expensively, or would it be more ethical to use local labour?
- What are the ethical challenges of living in a world were not everyone has access to computers, either for financial, political or disability-related reasons?
Good Practice (Computers)
Considering the consequences of a program that you are writing. For instance, will it cost jobs? Will it collect too much personal data on people?
Using a computer in a way that is considerate towards others. Think about what you say on social networking sites about other people or organisations, particularly given the fact that it is virtually impossible to delete something completely from the internet.
Only claiming to be competent in areas in which you are actually competent. If you were to write some kind of health-care program that was flawed in some way, lives could be lost.
Seeking out and following any formal or informal code of ethics that already exists within a particular industry or profession. What do others do with regard to their own ethics?
Making sure that anything that should be confidential, remains confidential. Are your own passwords difficult to guess? Are they changed regularly? Do you have access to anyone else's passwords or personal information?
Bad Practice (Computers)
Using a computer to help any kind of criminal enterprise.
Using a computer to gain access to information you have no right to access.
Being careless or malicious with any personal information or passwords you have access to.
Passing off the work of someone else as your own.
Using a program or any other resource you have not paid for.
Legal Issues
Computer Misuse Act - This makes hacking illegal. Hacking is gaining access to computer material that you are not allowed to have access to, possibly stealing a password.
Data Protection Act - If you store the personal data of anyone, you are required to keep it secure and up to date.
Copyrights, Designs and Patents Act - It is illegal to make a copy of any publication without the permission of the copyright owner.
Health and Safety at Work Act - This law makes employers responsible for the safety of their staff, as well as staff responsible for the safety of other staff. In terms of
computers, the following are considerations:
Trailing cables, tripping hazard.
Too much time spent at a computer can cause eye strain or repetitive strain injury from typing or using the mouse.
A poorly positioned chair, can cause back problems.
A monitor not at eye level, can cause neck problems.
Social Issues
Computer technology has had a massive impact upon society, including both positive and negative impacts. Whether the positive aspects outweigh the negative is not a straightforward issue, and is likely to remain debatable.
More people can telecommute (work from home) than in previous years. This has had a positive impact upon traffic congestion and time spent commuting, but a negative impact upon workplace relationships and face-to-face communication and an impact upon work-life balance.
There are far more ways to communicate now than face-to-face, letter writing and phone calls. It could be argued that social media has brought people together, as international communication is now easy, or it could be argued that it has alienated people by reducing the amount of face-to-face communication.