D430: Fundamentals of Information Security - PASSED
1/235
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
236 Terms
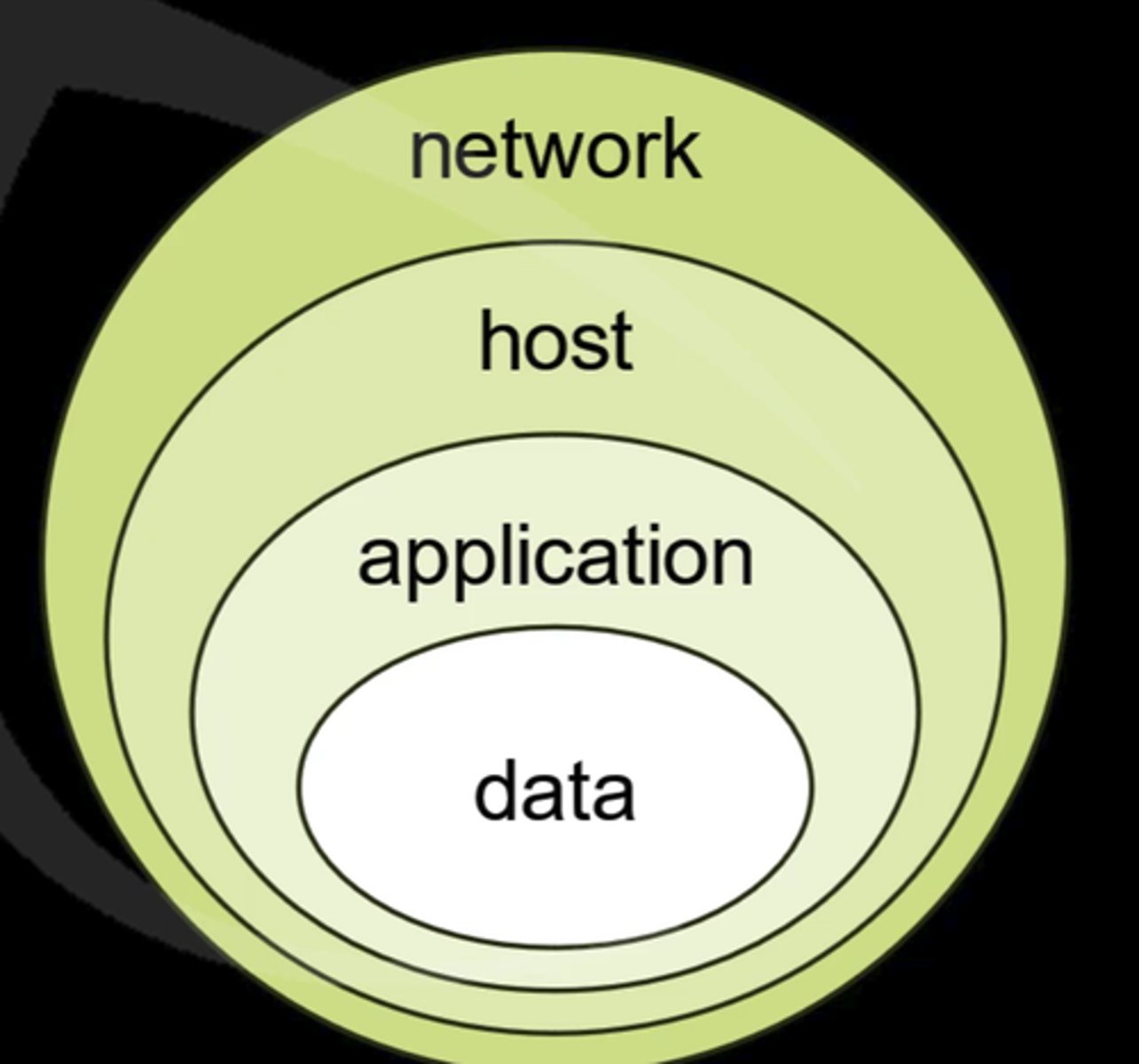
defense by layer
the layers of your defense-in-depth strategy will vary depending on situation and environment.
logical layers: external network, network perimeter, internal network, host, application, and data layers as areas to place your defenses.
defenses for layers can appear in more than one area. penetration testing, for example, can and should be used in all layers.
Data at rest
data at rest is stored data not in the process of being moved; usually protected with encryption at the level of the file or the entire storage device.
Data in motion
data in motion is data that is in the process of being moved; usually protected with encryption, but in this case the encryption protects the network protocol or the path of the data.
Data in use
data in use is the data that is actively being accessed at the moment. protection includes permissions and authentication of users. could be conflated with data in motion.
Payment Card Industry Data Security Standard (PCI DSS)
a widely accepted set of policies and procedures intended to optimize the security of credit, debit and cash card transactions and protect cardholders against misuse of their personal information.
Health Insurance Portability and Accountability Act of 1996 (HIPAA)
a federal law that required the creation of national standards to protect sensitive patient health information from being disclosed without the patient's consent or knowledge.
federal information security management act (FISMA)
requires each federal agency to develop, document, and implement an information security program to protect its information and information systems.
m; applies to US federal government agencies, all state agencies that administer federal programs, and private companies that support, sell to, or receive grant money from the federal government.
Federal risk and authorization management program (FedRAMP)
defines rules for government agencies contracting with cloud providers; applies to both cloud platform providers and companies providing software as a service (SaaS) tools that are based in the cloud.
Sarbanes-oxley Act (SOX)
regulates the financial practice and governance for publicly held companies.
m; designed to protect investors and the general public by establishing requirements regarding reporting and disclosure practices.
places specific requirements on an organization's electronic recordkeeping, including the integrity of records, retention periods for certain kinds of information, and methods of storing electronic communications.
Gramm-leach-bliley Act (GLBA)
requires financial institutions to safeguard their customers financial data and identifiable information.
m; mandates the disclosure of an institution's information collection and information sharing practices and establishes requirements for providing privacy notices and opt-outs to consumers.
Children's Internet Protection Act (CIPA)
requires schools and libraries to prevent children from accessing obscene or harmful content over the internet.
Children's Online Privacy Protection Act (COPPA)
protects the privacy of minors younger than 13 by restricting organizations from collecting their PII (personally identifiable information), requiring the organizations to post a privacy policy online, make reasonable efforts to obtain parental consent, and notify parents that information is being collected.
Family educational rights and privacy act (FERPA)
defines how institutions must handle student records to protect their privacy and how people can view or share them.
International organization for standardization (ISO)
a body first created in 1926 to set standards between nations.
These documents lay out best practices for managing risk, controls, privacy, technical issues, and a wide array of other specifics.
National institute of standards and technology (NIST)
provides guidelines for many topics in computing and technology, including risk management.
two commonly referenced publications on risk management are SP 800-37 and SP 800-53.
SP 800-37 lays out the risk management framework in six steps: categorize, select, implement, assess, authorize, and monitor.
Confidentiality (CIA triad)
refers to our ability to protect data from those who are not authorized to view it.
can be compromised in a number of ways; losing laptop with data, someone looking over your shoulder while entering password, email attachments sent to wrong people, attackers could penetrate your system.
Integrity (CIA triad)
the ability to prevent people from changing your data in an unauthorized or undesirable manner.
Availability (CIA triad)
the ability to access our data when we need it.
Possession/Control (parkerian hexad)
refers to the physical disposition of the media on which the data is stored; enabling you to discuss the loss of data in the physical sense.
ex; an encrypted hard-drive is stolen, it is considered a loss because you no longer physically have the hard-drive.
Authenticity (parkerian hexad)
allows you to say whether you've attributed the data in question to the proper owner or creator.
ex; if something is altered to appear to have come from someone other than the proper owner or creator
Utility (parkerian hexad)
refers to how useful the data is to you.
ex; for an attacker, encrypted data would be of very little use as it's unreadable, unencrypted data would be useful because it's readable.
Interception (types of attacks)
an attack allowing unauthorized users access to data, applications, or environments and are primarily attacks against confidentiality.
ex; unauthorized file viewing or copying, eavesdropping on phone conversations, or reading someone else's email.
you can conduct it against data at rest or in motion. THESE attacks can be difficult to detect.
Interruption (types of attacks)
an attack making assets unusable or unavailable.
are often attacks against availability (ex; a DoS attack). could be considered an integrity attack (or both) if it involves loss or corruption of data during the attack.
Modification (types of attacks)
an attack involving the tampering of assets. are often attacks against integrity.
can be an availability attack if the tampering involves how a service behaves.
Fabrication (types of attacks)
an attack involving generating data, processes, communications, or other similar material (usually fakes) with a system. are often attacks against integrity.
can be an availability attack if those things cause enough traffic to render a service unavailable.
asset
THIS is anything of value within an organization, composed of; the people, property, and information.
threat
something that has the potential to cause harm to an asset.
ex; a virus may be problematic on the windows operating system, but the same virus will be unlikely to have any effect on a linux operating system.
vulnerabilities
weaknesses or holes of an asset that threats can exploit to cause harm.
ex; could be an operating system, the physical location of a building, servers generating more heat that the air-conditioning can handle, etc..
risk
the likelihood that something bad will happen because of the potential for a threat to exploit a vulnerability.
impact
THIS takes into account the value of the asset being threatened and uses it to calculate risk.
ex; if the asset is your journal, you can say there is no risk. if the asset is your bank account information, you can say the risk is very high.
risk management process
identify assets > identify threats > assess vulnerabilities > assess risks > mitigate risks.
identify important assets, figure potential threats against them, assess vulnerabilities, then take steps to mitigate these risks.
identify assets (risk management process)
THIS is one of the first and most important parts of risk management. if you can't identify the impact, then protection becomes a difficult task.
ex; acquisition of another company leads to THIS possibly being required to keep the business functional.
identify threats (risk management process)
once the impact of assets are assessed, THIS is required to see how potential attacks might affect the assets.
m; being concerned with losing control of data, maintaining accurate data, and keeping the system up and running allows you to be able to look at areas of vulnerability and potential risk.
assess vulnerabilities (risk management process)
assets can have millions of threats, but only a fraction will be relevant; THIS is done to see if those relevant threats pose a risk.
ex; if data is exposed, it could lead to a breach. if your data is encrypted, this is not a risk.
ex; if the system goes down, business operations will also go down, this is a risk.
assess risks (risk management process)
once the threats and vulnerabilities are identified, THIS is done to have an overall idea of the risk so you can start to mitigate them.
m; a vulnerability with no matching threat or a threat with no matching vulnerability does not constitute a risk.
mitigate risks (risk management process)
THIS is putting measures (called controls) in place to account for each threat. there are three categories of control: physical, logical, and administrative.
physical controls/measures (mitigate risks)
THIS protects the physical environment in which your systems sit or where your data is stored. also controls access of such environments.
ex; includes fences, gates, locks, bollards, guards, and cameras, but also systems that maintain the physical environment, such as heating and air-conditioning systems, fire suppression systems, and backup power generators.
m; one of the most critical controls. makes other controls useless if an attacker has direct access to your system.
logical (or technical) controls/measures (mitigate risks)
THIS protects the systems, networks, and environments that process, transmit, and store your data.
ex; THIS can be things such as passwords, encryption, access controls, firewalls, and intrusion detection systems.
m; enables the prevention of unauthorized activities unless the attacker is able to subvert the controls.
administrative controls/measures (mitigate risks)
THIS dictates how the users of your environment should behave; the rules, laws, policies, procedures, guidelines, and other items that are "paper" in nature.
m; an important aspect of THIS is the ability to enforce it. can cause threats and vulnerabilities if left unchecked.
incident response
something to be done in the event of an attack and should be directed in a way that is based on the impact the attack has towards the organization.
m; steps in THIS process: preparation, detection and analysis, containment, eradication, recovery, post-incident activity.
preparation (incident response)
the phase where things are done before an incident occurs.
ex; policies and procedures that govern incident response and handling, conducting training for the response team and those who report incidents, and developing and maintaining documentation.
m; decisions should already be made regarding what needs to be done, who needs to do it, and how to do it.
detection and analysis (incident response)
the phase where issues are detected, a decision is made whether it's actually an incident, and the appropriate response to it. the second part of this requires human judgement and decision making.
m; usually detected with a security tool or service such as an intrusion detection system (IDS), antivirus (AV) software, firewall logs, proxy logs, or alerts from a security information and event monitoring (SIEM) tool or managed security service provider (MSSP).
containment (incident response)
THIS involves stopping an incident from doing anymore damage or at least to lessen any ongoing harm.
ex; if malware-infected by a remote attacker, this might involve disconnection, blocking with a firewall, and updating signatures or rules on an intrusion prevention system (IPS) to halt the malware traffic.
eradication (incident response)
THIS involves attempting to remove the effects of the issue from your environment.
ex; once the attack is contained, THIS would be the step to remove it; such as scanning hosts of others in the environment to ensure the malware is gone, including the examination of server and network logs the infected computer communicated with.
recovery (incident response)
THIS is going back to the state prior to the incident.
m; involves restoring devices or data from backup media, rebuilding systems, or reloading applications.
can be a painful task because your knowledge of the situation might be incomplete or unclear. you may not be able to verify the cleanliness of the backup.
post-incident activity or post-mortem (incident response)
attempting to determine specifically what happened, why it happened, and what you can do to keep it from happening again after an incident.
m; the purpose of THIS is to ultimately prevent or lessen the impact of future such incidents.
defense in depth
the basic concept is to formulate a multilayered defense; the goal is to place enough defensive measures between your truly important assets and the attacker so that you'll notice that an attack is in progress and have enough time to prevent it.
identification
the assertion of who we are; including as people or a system over a network.
m; THIS is a weak concept as, by itself, is easily faked, duplicated, or changed.
a claim of THIS is not enough as simple verification lends itself to gaps in security. THIS is often falsified, often requiring only name, address, and social security number to impersonate someone.
authentication
a set of methods used to establish whether a claim of identity is true.
THIS has several approaches, known as factors, when trying to prove a claim of identity; something you know, something you are, something you have, something you do, and where you are.
something you know (factor)
a common authentication factor based on knowledge.
ex; your passwords and PINs.
m; this factor is somewhat weak, if the information is exposed then your authentication method may no longer be unique.
something you are (factor)
a factor based on the unique physical attributes of an individual.
ex; simple identifiers are height, weight, hair color, or eye color, but these aren't distinct enough for security. complex identifiers are fingerprints, iris or retina patterns, or facial characteristics and are more common for security purposes.
m; this factor is stronger than a password because forging or stealing a copy of a physical identifier is more difficult, although not impossible.
something you have (factor)
a factor generally based on a physical possession, although it can extend into some logical concepts.
ex; automatic teller machine (ATM) cards, state or federally issued identity cards, or software-based (texted) security codes.
m; the strength of this factor varies on implementation. a code sent to a device is more secure than a code sent to an email address.
something you do (factor)
a factor based on the actions or behaviors of an individual.
ex; handwriting or delay between keystrokes.
m; a strong factor that is hard to falsify. a downside is the potential to reject legitimate users at a higher rate than other factors.
where you are (factor)
a factor based on geography; operates differently from other factors as it requires the user to be in a specific location.
ex; when changing an atm pin, you may be required to go into a branch.
m; although potentially less useful than other factors, this factor is difficult to counter without entirely subverting the system performing the authentication.
multifactor authentication
THIS is using one or more authentication factors.
m; the level of THIS should take into account practicality, the cost, and customer satisfaction or dissatisfaction.
mutual authentication
an authentication mechanism in which both parties in a transaction authenticate each other.
m; typically software-based. relies on digital certificates, which both parties would have one to authenticate each other.
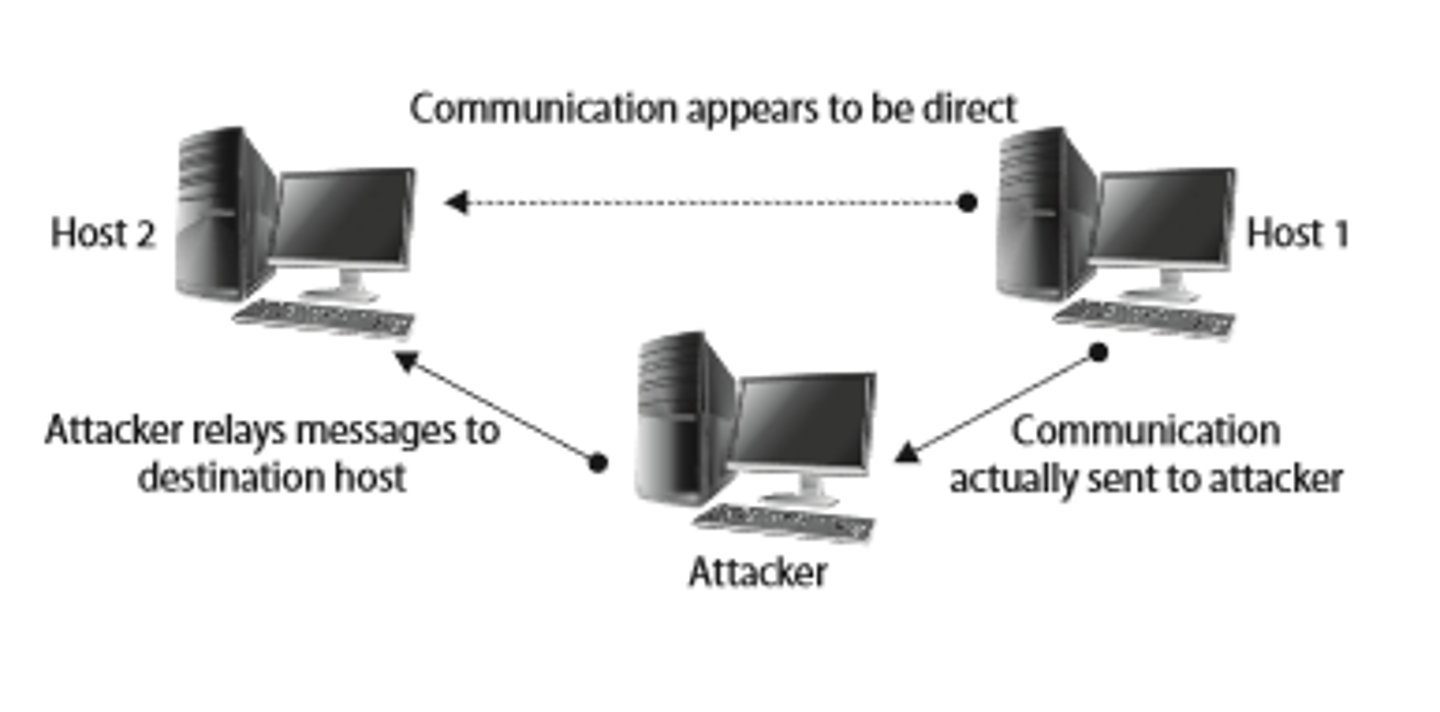
man-in-the-middle attacks
an attack where the attacker inserts themself between the client and the server.
done by circumventing the normal pattern of traffic and then intercepting and forwarding the traffic that would normally flow directly between the client and the server.
m; you open yourself to THESE attacks when you don't perform mutual authentication; because an attacker only needs to subvert authentication from the client to the server and not both ways.
biometrics
the unique characteristics of individuals that can be used in processes to verify an identity claim; the process can also be reversed and used as a method of identification.
ex; a reversal is using a left-behind fingerprint to identify someone.
m; may include noting certain elements of the characteristic (known as minutiae).
THESE are: universality, uniqueness, permanence, collectability, performance, acceptability, and circumvention.
universality (biometrics)
the chosen characteristic should be found in the majority of people expected to enroll in the system.
ex; while a scar can be an identifier, most people won't have a scar. while most people will have fingerprints, some people may be missing fingers.
uniqueness (biometrics)
a measure of how distinct a characteristic is among individuals.
ex; height is only distinct at extreme ends, so this is a poor factor. more distinctive characteristics should be used, such as dna or finger prints.
m; however, nothing is truly distinct, intentionally or not. identical twins share the same dna and finger prints can be replicated.
permanence (biometrics)
how well a characteristic resists change over time and with advancing age.
ex; weight fluctuates, making it a poor characteristic for biometrics. fingerprints are unlikely to change without deliberate action.
collectability (biometrics)
measures how easy it is to acquire a characteristic.
ex; commonly used biometrics, such as fingerprints, are easy to acquire. dna samples are more difficult to authenticate with, again-and-again.
performance (biometrics)
measures how well a given system functions based on factors such as speed, accuracy, and error rate.
m; two of the many ways to measure THIS are false acceptance rate (FAR) and false rejection rate (FRR).
measuring performance (of biometrics)
false acceptance rate (FAR); measures how often you accept a user who should be rejected and is sometimes called a false positive.
false rejection rate (FRR); measures how often we reject a legitimate user and is sometimes called a false negative.
you should aim for a balance between the two, referred to as an equal error rate (EER); EER is sometimes used as a measure of the accuracy of biometric systems.
acceptability (biometrics)
a measure of how tolerable the characteristic is to the users of the system.
ex; systems that are slow, difficult or awkward to use are less likely to be tolerable by users.
circumvention (biometrics)
describes how easy it is to trick a system by using a falsified biometric identifier.
ex; the "gummy finger," a fingerprint is lifted from a surface and used to create a mold for fraudulent purposes.
m; biometric systems may have secondary features to defeat such attacks: temperature, pulse, etc..
hardware token (or dongles)
a small device that provides a certificate or unique identifier for the purposes of authentication to access a resource.
authorization
the process of determining exactly what an authenticated party can do.
access controls
the tools and systems you use to deny or allow access; implementing authorization.
ex; a key to lock or unlock doors, badge for entry at work, password to use a computer.
m; THIS has four basic tasks: allowing access, denying access, limiting access, and revoking access.
allowing access (access controls)
giving a party access to a given resource.
ex; permitting the use of a file or permitting someone into your home.
denying access (access controls)
preventing a given party from accessing the resource in question.
ex; not allowing use of a file or not allowing someone into your home.
limiting access (access controls)
allowing only some degree of access to your resources.
m; a way to restrict access is by running sensitive applications in sandboxes, which are isolated environments containing a set of resources for a given purpose.
revoking access (access controls)
taking access away from a party after you've granted it. THIS is vital to security.
ex; you'd want to take any and all access away from people who no longer work in your organization.
access control lists (ACLs)
lists containing information about what kind of access certain parties are allowed to have to a given system.
file system ACLs
THIS has three types of authorizations that allow access to specific resources in a specific manner.
read, which allows a user to access the contents of a file or directory.
write, which allows a user to write to a file or directory.
execute, which allows a user to execute the contents of a file.
network ACLs
filters access for network traffic based on chosen identifiers; such as internet protocol (IP) addresses, media access control addresses, and ports.
m; usually works in a binary way, either allowing or denying some activity. THESE typically grant permissions for traffic rather and being user-specific.
media access control (network ACLs)
THESE addresses are unique identifiers hard-coded into each network interface in a given system.
m; a poor choice as a unique identifier as changing THIS address is easy.
internet protocol (IP) address (network ACLs)
theoretically unique and assigned to each device on any network that uses the internet protocol for communication.
m; can be falsified and are frequently changed, by itself THIS is not a strong choice as a unique identifier.
blocking THESE on a large-scaled is called blackholing.
port (network ACLs)
a numerical designation for one side of a connection between two devices, and we use them to identify the application to which traffic should be routed.
you can control the use of many applications over the network by allowing or denying traffic originating from or sent to THESE.
socket
a combination of more than one network ACLs that provides more security; ip address, mac address, and port.
confused deputy problem
a category of attack when software is tricked into misusing its greater level of authority to carry out an attack.
m; typically occurs when the software has a greater level of permission to access the resource than the user who is controlling the software.
systems that use ACLs to manage permissions are vulnerable to this type of attack.
social engineering attacks
a category of attack that tricks individuals into handing over sensitive information.
m; relies on the willingness of people to help others leading them to click on dangerous links or giving out their passwords and sensitive information.
cross-site request forgery (CSRF)
an attack that misuses the authority of the browser on the user's computer.
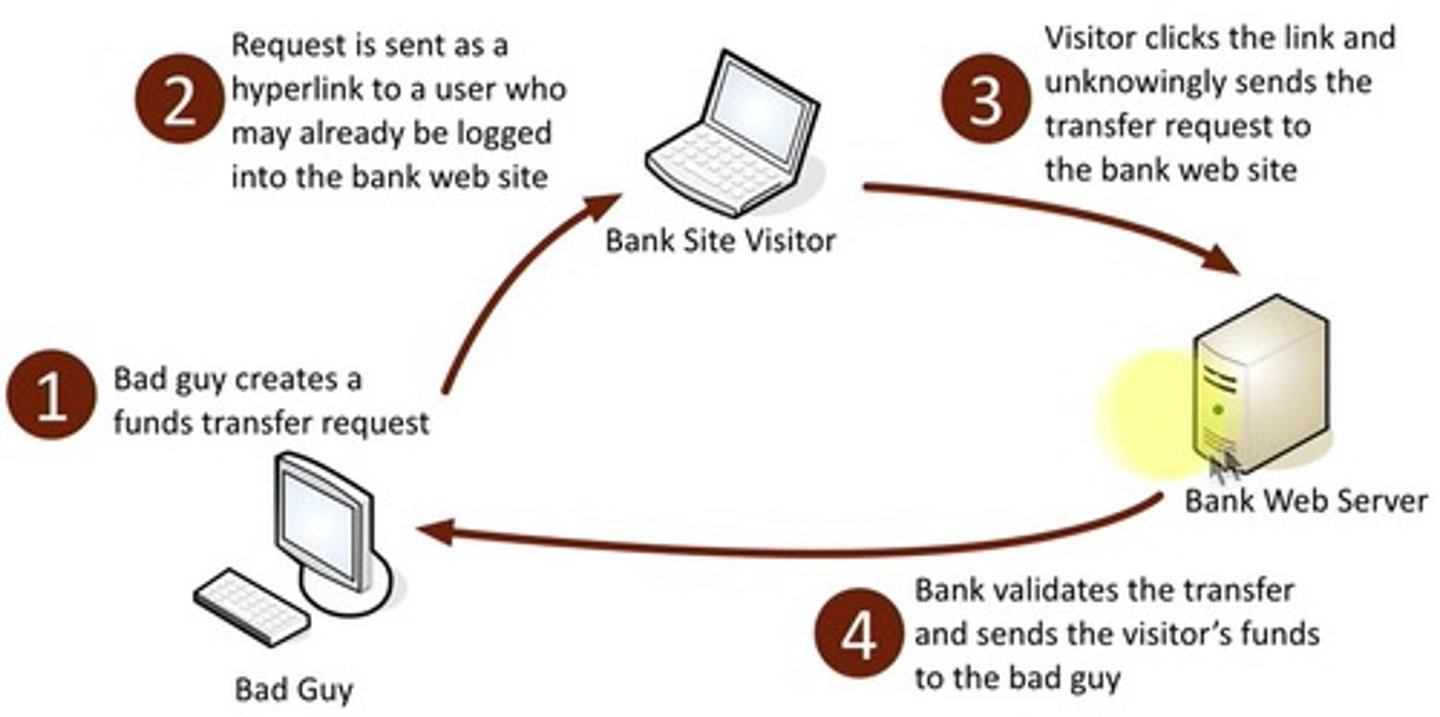
clickjacking (user interface redressing)
when an attacker places an invisible layer over something a client would normally click, causing the client to execute unwanted activities that's different than the one they think they're performing.
m; takes advantage of the page rendering features that are available in newer web browsers.
the attacker must legitimately control or have taken control of some portion of a website to make this attack possible.

capability
a user's token or key that grants whoever currently has possession of it access to the resources the token has the permissions for.
ex; the badge you might use to open the door of a building.
access control model
a way of determining who should be allowed access to what resources.
the most common of THESE are: discretionary access control, mandatory access control, rule-based access control, role-based access control, attribute-based access control, and multilevel access control.
discretionary access control (DAC) (access control model)
a model where the owner of the resource determines who gets access to it and exactly what level of access they can have.
mandatory access control (MAC) (access control model)
a model where the owner of the resource doesn't get to decide who gets to access it, a separate group or individual has the authority to set access to resources.
rule-based access control (access control model)
a model allowing access according to a set of rules defined by the system administrator. if the rule is matched, access to the resource will be granted or denied accordingly.
role-based access control (RBAC) (access control model)
a model allowing access based on the role of the individual being granted access.
attribute-based access control (ABAC) (access control model)
a model based on the specific attributes of an individual, resource, or environment.
subject attributes belong to an individual. ex; height, "you must be this tall to ride."
resource attributes belong to a resource, such as an operating system. ex; this type of access control requires someone to use specific software or protocols for communication.
environmental attributes are based on environmental conditions. ex; time, "this can only be accessed during these times."
multilevel access control (access control model)
a model that combines several of the access control models together when they aren't considered robust enough alone to protect the information to which you're controlling access.
physical access controls
concerned with controlling the movement of individuals and vehicles; regulating movement in and out of buildings, often using badges that open doors.
ex; keeping vehicles from moving through unauthorized area using simple barriers like one-way spike strips or fences.
tailgating (or piggybacking)
occurs when you authenticate your physical access control measure, such as a badge, and another person follows directly behind you without also being authenticated.
accountability
making sure individuals are responsible for their actions.
THIS is done by using identification, authentication, and authorization processes so you can know who a given event is associated with and what permissions allowed them to carry it out.
nonrepudiation (accountability)
a situation when an individual is held accountable due to being unable to deny a statement or action because there is sufficient evidence that they did it.
m; in information security, proof is produced from logs or through digital forensics of the environment.
ex; can be established using encryption technology to digitally sign data.
deterrence (accountability)
accountability causes THIS against misbehavior in your environments.
m; the key to THIS is making it clear to people that they will be held accountable for their actions; achieved through auditing and monitoring.
intrusion prevention systems (IPS), (accountability)
works from information sent by the IDS; takes action based on events happening in the environment.
ex; in response to an attack over the network, THIS might refuse traffic from the source of the attack.
audit
the process of reviewing an organization's records or information.
ensures that people comply with laws, policies, and other bodies of administrative control.
ex; passwords must be company policy compliant, software licenses must be law compliant (not illegally using software unlicensed), internet traffic must be administratively compliant.
logging (audit)
THIS is used to create records of the activities that take place in the environment.
m; a reactive tool allowing auditing from the created records.