Networking WebXam Practice
1/103
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
104 Terms
Application layer
integrates network function into the host operating system, and enables network services
Doesn't not include specific applications that provide services, but rather provides the capability for services to operate on the network...HTTP
Presentation (Layer 6)
layer formats or "presents" data into a compatible form for receipt by the Application layer or the destination system. Specifically, the Presentation layer ensures:
Formatting and translation of data between systems.
Negotiation of data transfer syntax between systems, through converting character sets to the correct format.
Encapsulation of data into message envelopes by encryption and compression.
Restoration of data by decryption and decompression.
Session (Layer 5)
primary function is managing the sessions in which data is transferred. Functions at this layer include:
Management of multiple sessions (each client connection is called a session). A server can concurrently maintain thousands of sessions.
Assignment of the session ID number to each session to keep data streams separate.
Set up, maintain, and tear down communication sessions.
Transport (Layer 4)
provides a transition between the upper and lower layers of the OSI model, making the upper and lower layers transparent from each other. Transport layer functions include:
End-to-end flow control.
Port and socket numbers.
Segmentation, sequencing, and combination.
Connection services, either reliable (connection-oriented) or unreliable (connectionless) delivery of data.
Data is referred to as a segment.
Network (Layer 3)
describes how data is routed across networks and on to the destination. Network layer functions include:
Identifying hosts and networks using logical addresses.
Maintaining a list of known networks and neighboring routers.
Determining the next network point to which data should be sent. Routers use a routing protocol to take into account various factors such as the number of hops in the path, link speed, and link reliability to select the optimal path for data.
Data
is referred to as a packet.
Data Link (Layer 2)
Logical Link Control (LLC)
Media Access Control (MAC)
defines the rules and procedures for hosts as they access the Physical layer. These rules and procedures specify or define:
How hosts on the network are identified (physical or MAC address).
How and when devices can transmit on the network medium (media access control and logical topology).
How to verify that the data received from the Physical layer is error free (parity and CRC).
How devices control the rate of data transmissions between hosts (flow control).
Data is referred to as a frame.
Physical (Layer 1)
sets standards for sending and receiving electrical signals between devices. Protocols at the Physical layer identify:
How digital data (bits) are converted to electric pulses, radio waves, or pulses of lights.
Specifications for cables and connectors.
The physical topology.
Data is referred to as bits.
he TCP/IP model incorporates the general concepts and structure of the OSI model. The layers of the TCP/IP model are as follows:
Application
Host-to-host
Internet
Network Access
Application TCP/IP
corresponds to the Session, Presentation, and Application layers of the OSI model. Protocols associated with the Application layer include FTP, HTTP, Telnet, Smtp, DNS, and SNMP.
Host-to-host TCP/IP model
is comparable to the Transport layer of the OSI model and is responsible for error checking and reliable packet delivery. Here, the data stream is broken into segments that must be assigned sequence numbers so that the segments can be reassembled correctly on the remote side after they are transported. Protocols associated with the Host-to-host layer include Transport Control Protocol (TCP) and User-Datagram Protocol (UDP).
Internet TCP/IP model
s comparable to the Network layer of the OSI model. It is responsible for moving packets through a network. This involves addressing of hosts and making routing decisions to identify how the packet traverses the network. Protocols associated with the Internet layer include Address Resolution Protocol (ARP), Internet Control Message Protocol (ICMP), and Internet Group Management Protocol (IGMP).
Network Access TCP/IP model i
corresponds to the functions of the Physical and Data Link layers of the OSI model. It is responsible for describing the physical layout of the network and how messages are formatted on the transmission medium.
Bus Topology
A physical topology consists of a trunk cable with nodes either inserted directly into the trunk, or nodes tapping into the trunk using offshoot cables called drop cables.
Signals travel from one node to all other nodes on .
A device called a terminator is placed at both ends of the trunk cable.
Terminators absorb signals and prevent them from reflecting repeatedly back and forth on the cable.
The physical :
Requires less cable than the star
Can be difficult to isolate cabling problems
A broken cable anywhere breaks the termination and prevents communications between any device on the network.
Ring
connects neighboring nodes until they form a ring. Signals travel in one direction around the ring. In ring topologies, each device on the network acts as a repeater to send the signal to the next device. With a ring:
Installation requires careful planning to create a continuous ring.
Isolating problems can require going to several physical locations along the ring.
A malfunctioning node or cable break can prevent signals from reaching nodes further along on the ring.
Star
a hub or switch to concentrate all network connections to a single physical location. Today it is the most popular type of topology for a LAN. With the star:
All network connections are located in a single place, which makes it easy to troubleshoot and reconfigure.
Nodes can be added to or removed from the network easily.
Cabling problems usually affect only one node.
Requires more cable than any other topology. Every node has its own cable.
Mesh
exists when there are multiple paths between any two nodes on a network. created using point-to-point connections. This increases the network's fault tolerance because alternate paths can be used when one path fails. Two variations of topologies exist:
Partial --Some redundant paths exist.
Full --Every node has a point-to-point connection with every other node.
Full topologies are usually impractical because the number of connections increases dramatically with every new node added to the network. However, a full topology becomes more practical through the implementation of an ad-hoc wireless network. With this topology, every wireless network card can communicate directly with any other wireless network card on the network. A separate and dedicated network interface and cable for each host on the network is not required.
Logical Topology [Bus] Physical Topology bus/star
Messages are sent to all devices connected to the bus.
Logical Topology [Ring] ring/star
Messages are sent from device-to-device in a predetermined order until they reach the destination device.
Logical Topology [star]
Messages are sent directly to (and only to) the destination device.
Web browsing Protocol
HyperText Transfer Protocol (HTTP)
HTTP over SSL (HTTPS)
HyperText Transfer Protocol (HTTP)
is used by Web browsers and Web servers to exchange files (such as Web pages) through the World Wide Web and intranets.
can be described as an information requesting and responding protocol. It is typically used to request and send Web documents, but is also used as the protocol for communication between agents using different TCP/IP protocols.
HTTP over SSL (HTTPS)
is a secure form of HTTP that uses SSL to encrypt data before it is transmitted.
Security protocols
Transport Layer Security (TLS)
Transport Layer Security (TLS).
ensures that messages being transmitted on the Internet are private and tamper proof.is implemented through two protocols:
Record--Can provide connection security with encryption (with DES for example).
Handshake--Provides mutual authentication and choice of encryption method.
File transfer Protocol
File Transfer Protocol (FTP
Trivial File Transfer Protocol (TFTP)
Secure File Transfer Protocol (SFTP)
Secure Copy (SCP)
File Transfer Protocol (FTP)
provides a generic method of transferring files. It can include file security through usernames and
passwords, and it allows file transfer between dissimilar computer systems. can transfer both binary and text files, including HTML, to another host. FTP URLs are preceded by ftp:// followed by the DNS name of the FTP server. To log in to an FTP server, use: ftp://username@servername.
Trivial File Transfer Protocol (TFTP)
s similar to FTP. It lets you transfer files between a host and an FTP server. However, it provides no user authentication and no error detection. TFTP is often used when transferring files such as video, audio, or images. Because it does not perform error detection, TFTP is faster than FTP, but might be subject to file errors.
Secure File Transfer Protocol (SFTP)
s a file transfer protocol that uses Secure Shell (SSH) to secure data transfers. SSH ensures that SFTP transmissions use encrypted commands and data which prevent data from being transmitted over the network in clear text.
Secure Copy (SCP)
is associated with Unix/Linux networks and used to transfer files between systems. Like SFTP, SCP relies on SSH to ensure that data and passwords are not transmitted over the network in clear text.
E-mail Protocol
Simple Mail Transfer Protocol (SMTP)
Post Office Protocol 3 (POP3)
Simple Mail Transfer Protocol (SMTP)
is used to route electronic mail through the internetwork. is used:
Between mail servers for sending and relaying mail.
By all e-mail clients to send mail.
By some e-mail client programs, such as Microsoft Outlook, for receiving mail from an Exchange server.
Post Office Protocol 3 (POP3)
is part of the TCP/IP protocol suite and is used to retrieve e-mail from a remote server to a local client over a TCP/IP connection. With POP3, e-mail messages are downloaded to the client.
An e-mail client that uses POP3 for receiving mail uses SMTP for sending mail.
Network services Protocol
Dynamic Host Configuration Protocol (DHCP)Domain Name System (DNS)
Network Time Protocol (NTP)
Lightweight Directory Access Protocol (LDAP)
Dynamic Host Configuration Protocol (DHCP
s a method for automatically assigning addresses and other configuration parameters to network hosts. Using a DHCP server, hosts receive configuration information at startup, reducing the amount of manual configuration required on each host.
Domain Name System (DNS)
s a system that is distributed throughout the internetwork to provide address/name resolution. For example, the name www.mydomain.com would be identified with a specific IP address.
Network Time Protocol (NTP)
is used to communicate time synchronization information between systems on a network.
Lightweight Directory Access Protocol (LDAP
used to allow searching and updating of a directory service. The LDAP directory service follows a client/server model. One or more LDAP servers contain the directory data, the LDAP client connects to an LDAP Server to make a directory service request.
Network management Protocol
Simple Network Management Protocol (SNMP)
Remote Terminal Emulation (Telnet)
Secure Shell (SSH)
Simple Network Management Protocol (SNMP)
s a protocol designed for managing complex networks. SNMP lets network hosts exchange configuration and status information. This information can be gathered by management software and used to monitor and manage the network.
Remote Terminal Emulation (Telnet)
allows an attached computer to act as a dumb terminal, with data processing taking place on the TCP/IP host computer. It is still widely used to provide connectivity between dissimilar systems. Telnet can also be used to test a service by the use of HTTP commands.
Secure Shell (SSH)
allows for secure interactive control of remote systems. SSH uses RSA public key cryptography for both connection and authentication. SSH uses the IDEA algorithm for encryption by default, but is able to use Blowfish and DES. SSH is a secure and acceptable alternative to Telnet.
Transport protocols
Transmission Control Protocol (TCP)
User Datagram Protocol (UDP)
Transmission Control Protocol (TCP)
provides services that ensure accurate and timely delivery of network communications between two hosts. TCP provides the following services to ensure message delivery:
Sequencing of data packets
Flow control
Error checking
User Datagram Protocol (UDP
is a host-to-host protocol like TCP. However, it does not include mechanisms for ensuring timely and accurate delivery. Because it has less overhead, it offers fast communications, but at the expense of possible errors or data loss.
Control protocols
Internet Control Message Protocol (ICMP)
Internet Group Membership Protocol (IGMP)
Internet Group Membership Protocol (IGMP)
is a protocol for defining host groups. All group members can receive broadcast messages intended for the group (called multicasts). Multicast groups can be composed of devices within the same network or across networks (connected with a router).
Internet Control Message Protocol (ICMP)
works closely with IP in providing error and control information, by allowing hosts to exchange packet status information, which helps move the packets through the internetwork. Two common management utilities, ping and traceroute, use ICMP messages to check network connectivity. ICMP also works with IP to send notices when destinations are unreachable, when devices' buffers overflow, the route and hops packets take through the network, and whether devices can communicate across the network.
Twisted pair cables
Two wires that carry the data signals (one conductor carries a positive signal; one carries a negative signal). They are made of 22 or 24 gauge copper wiring.
Phone cable
RJ-11
Used to connect a PC to a phone jack in a wall outlet to establish a dial-up Internet connection.
Has two pairs of twisted cable (a total of 4 wires).
Cat 3
RJ-45
Designed for use with 10 megabit Ethernet or 16 megabit token ring.
Cat 5
RJ-45
Supports 100 megabit Ethernet and ATM networking. Cat 5 specifications also support gigabit (1000 Mb) Ethernet.
Cat 5e
RJ-45
Similar to Cat 5 but provides better EMI protection. Supports 100 megabit and gigabit Ethernet.
Cat 6
RJ-45
Supports 10 gigabit Ethernet and high-bandwidth, broadband communications.
Cat 6 cables often include a solid plastic core that keeps the twisted pairs separated and prevents the cable from being bent too tightly.
Additional standards for Cat 6 include Cat 6a (advanced) and Cat 6e (enhanced) which provide better protection against EMI.
RJ-11
Has 4 connectors
Supports up to 2 pairs of wires
Uses a locking tab to keep connector secure in outlet
Used primarily for telephone wiring

RJ-45
Has 8 connectors
Supports up to 4 pairs of wires
Uses a locking tab to keep connector secure in outlet
Used for Ethernet and some token ring connections
RG-58
50 ohms
10Base2 Ethernet networking (also called Thinnet)
RG-59
75 ohms
Cable TV and cable networking
RG-6
75 ohms
Cable TV, satellite TV, and cable networking
RG-6 has less signal loss than RG-59, and is a better choice for networking applications, especially where longer distances (over a few feet) are involved.
RG-8
50 ohms
10Base5 Ethernet networking (also called Thicknet)
F-Type
Twisted onto the cable
Used to create cable and satellite TV connections
Used to connect a cable modem to a broadband cable connection

BNC
Molded onto the cable
Used in 10Base2 Ethernet networks

fiber optic cables
you need two fiber strands. One strand transmits signals, and the other strand receives signals.
Single Mode
Transfers data through the core using a single light ray (the ray is also called a mode)
The core diameter is around 10 microns
Supports a large amount of data
Cable lengths can extend a great distance
Multi-mode
Transfers data through the core using multiple light rays
The core diameter is around 50 to 100 microns
Cable lengths are limited in distance
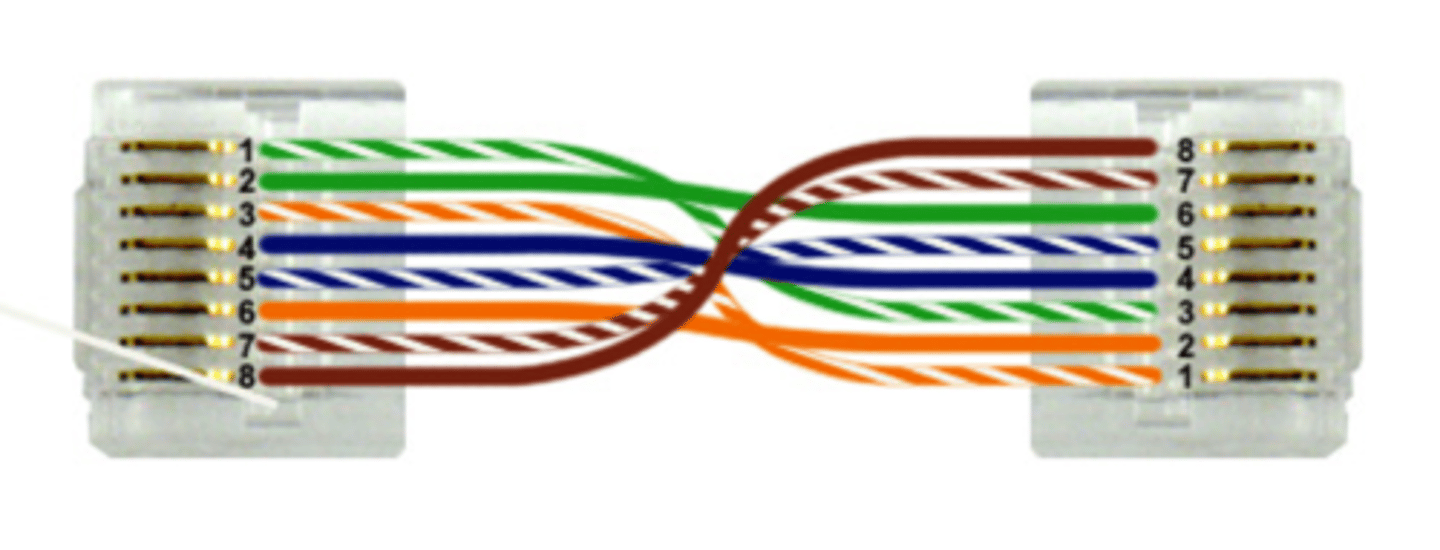
T568A
to use this standard, arrange the wires from pins 1 to 8 in each connector in the following order: GW, G, OW, B, BW, O, BrW, Br.
T568B
To use this standard, arrange the wires from pins 1 to 8 in each connector in the following order: OW, O, GW, B, BW, G, BrW, Br.
Cross-over
Computers can connect directly to one another using a crossover cable. The easiest way to create a crossover cable is to arrange the wires in the first connector using the T568A standard and arrange the wires in the second connector using the T568B standard.
Tx+
is a pin used for transmitting
Rx
is a pin used for receiving
Demarcation point (demarc)
is the line that marks the boundary between the telco equipment and the private network or telephone system.
Main Distribution Frame (MDF)
is the main wiring point for a building
LEC (local exchange carrier)
typically installs the demarc to the MDF.
Intermediate Distribution Frame (IDF)
is a smaller wiring distribution point within a building are typically located on each floor directly above the MDF, can be added on each floor as necessary.
Patch panel
is a device that typically connects individual stranded wires into female RJ-45 connectors. For example, you might connect 4 pairs of wires from a punchdown block to a port on the patch panel. On the patch panel, you then connect drop cables (cables with RJ-45 connectors) to the patch panel on one end and a computer on the other end.
punch down tool
insert wires into 66 or 110 blocks.
The punch down tool pushes the wire into the block and cuts off the excess wire.
Be sure to position the blade on the side of the clip towards the end of the wire.
The blade for a 66 block is straight, while the blade for a 110 block has a notch in the blade
Modem
is shorthand for modulator/demodulator, its job is to convert (or modulate) digital data from a Pc into analog telephone signals and transit them throough a telephone network.
Media converter
operates in Layer 1 (Physical layer)
translates frames into bits and transmits them on the transmission medium.
doesnot alter of use the MAC address or the IP address
Layer 2
the mac address is added to make the data into a frame.
Layer 3
the IP address is added to the packet.
MAC address
12 hexadecimal digits
ranging form 0-9/A-F
Identifies the physical address of the network adapter
IPv4
32 bits
octets of decimal numbers between 0-255
IPv6
64bit address that uses 32 hexadecimal numbers
Bridge
connects twodevices that use different network architectures: wired network to wireless clients
Hub/repeater
connects devices using the same media type
Address Resolution Protocol (ARP)
uses this protocol to discover MAC address of a host
network card NIC
allows a device to send and receive messages over the transmission media.
Ethernet
10BaseT
10BaseFL
10BaseT
10 Mbps (half duplex)
20 Mbps (full duplex)
Twisted pair (Cat3, 4, or 5)
100 meters
Fast Ethernet
100BaseTX
100BaseFX
1000BaseT
1,000 Mbps (half duplex)
2,000 Mbps (full duplex)
Twisted pair (Cat5 or higher)
Special copper (150 ohm)
100 meters
10 Gigabit Ethernet
10GBaseT
10GBaseSR/10GBaseSW
10GBaseLR/10GBaseLW
10GBaseER/10GBaseEW
Straight-through
• T568A GW, G, OW, B, BW, O, BrW, Br.
• T568B
OW, O, GW, B, BW, G, BrW, Br.
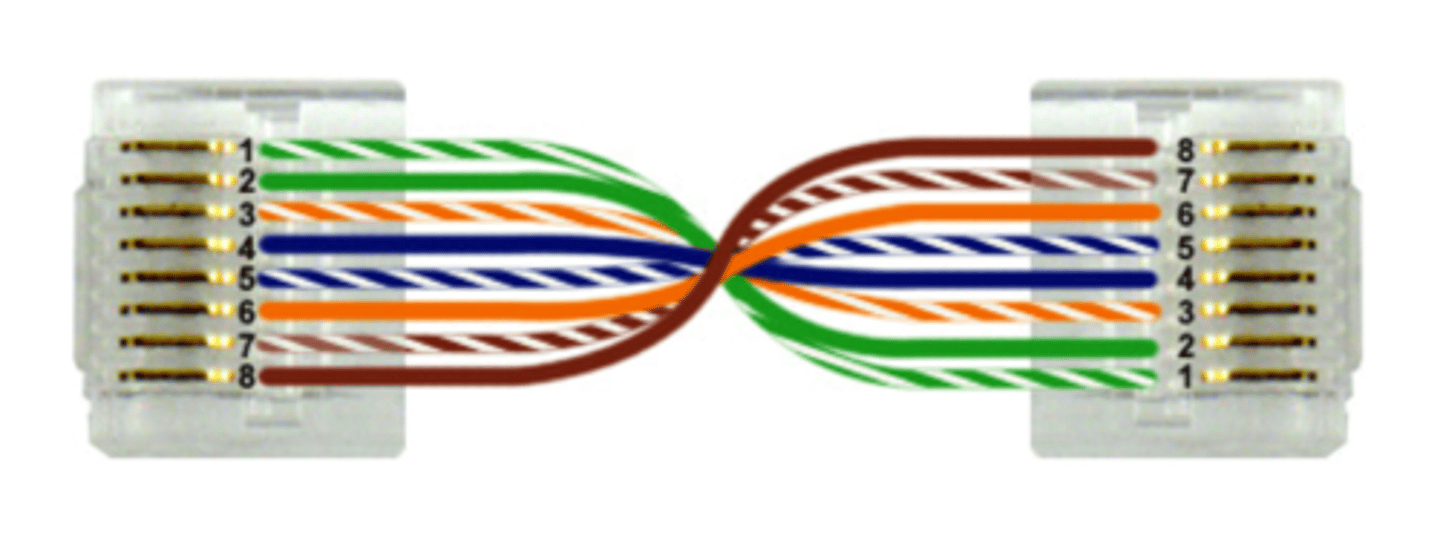
cross over
The easiest way to create a crossover cable is to arrange the wires in the first connector using the T568A standard and arrange the wires in the second connector using the T568B standard.
DHCP
When a client boots, it contacts the DHCP server for IP configuration information.
Automatic Private IP Addressing (APIPA)
APIPA is a Microsoft implementation of automatic IP address assignment without a DHCP server. Using APIPA, hosts assign themselves an IP address on the 169.254.0.0 network (mask of 255.255.0.0). With APIPA:
The host is configured to obtain IP information from a DHCP server (this is the default configuration).
If a DHCP server can't be contacted, the host uses APIPA to assign itself an IP address.
The host only configures the IP address and mask. It does not assign itself the default gateway and DNS server addresses. For this reason, APIPA can only be used on a single subnet.
Use APIPA:
On small, single-subnet networks where you do not need to customize the IP address range.
As a fail safe for when a DHCP server is unavailable to provide limited communication capabilities.
Static (manual) assignment
Using static addressing, IP configuration information must be manually configured on each host. Use static addressing:
On networks with a very small number of hosts.
On networks that do not change often or that will not grow.
To permanently assign IP addresses to hosts that must always have the same address (such as printers, servers, or routers).
For hosts that cannot accept an IP address from DHCP.
To reduce DHCP-related traffic.
32-bit binary number
represented as four octets or four 8 bit numbers. each octet is separated by a period.
Class A
Address Range
1.0.0.0 to 126.255.255.255
First Octet Range
1-126 Default
Subnet Mask
255.0.0.0
(00000001--01111110 binary)
Class b
Address Range
128.0.0.0 to 191.255.255.255
First Octet Range
128-191
(10000000--11011111 binary)
Default Subnet Mask
255.255.0.0
Class C
Address Range
192.0.0.0 to 223.255.255.255
First Octet Range
192-223
Default Subnet Mask
255.255.255.0