2 Data transmission
1/62
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
63 Terms
What is data broken down into to be transmitted?
packets
What is the structure of a packet?
packet header, payload, trailer
What does the packet header have?
destination address, packet number, originator’s address
What does the payload have?
the actual data
What does the trailer have?
a method of identifying end of the packet, error checking method
Describe the process of packet switching
1) Data is broken down into packets
2) Each packet could take a different route
3) A router controls the route a packet takes
4) Packets may arrive out of order
5) Once the last packet has arrived, packets are reordered
6) If the packet is missing/corrupted, it is requested again
Draw the process of packet switching
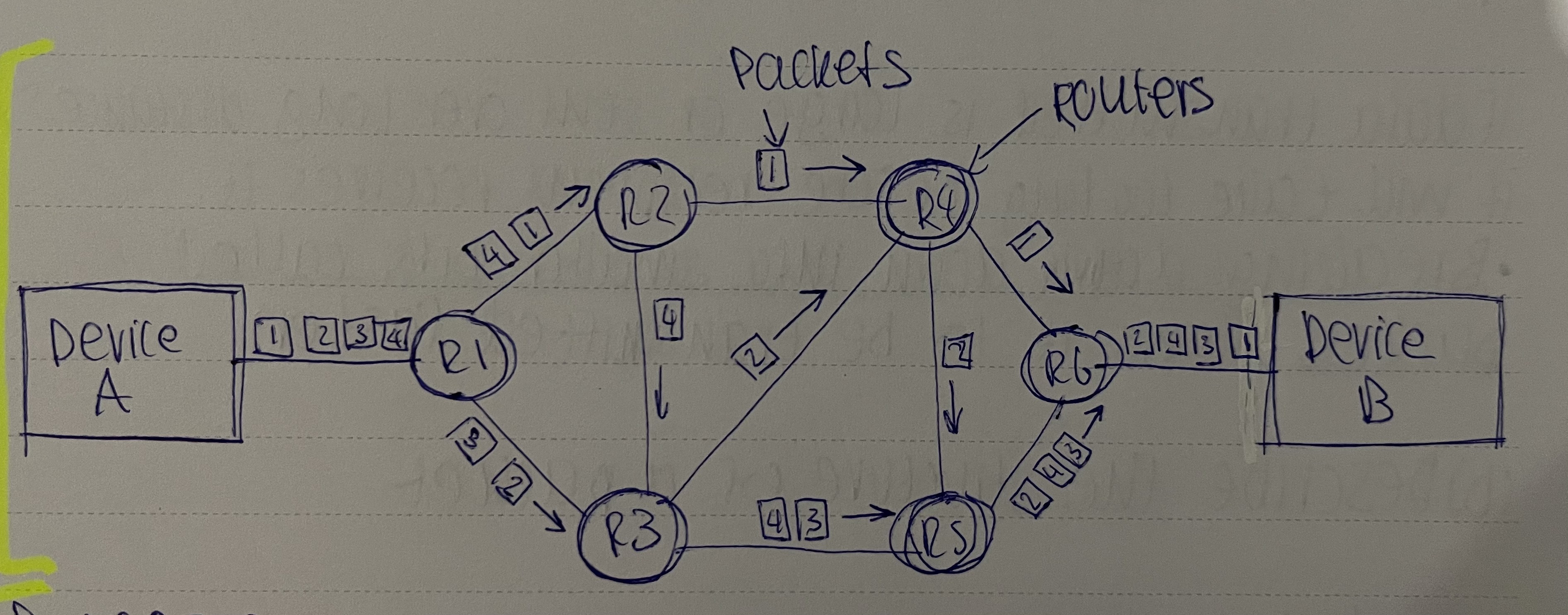
Advantages of packet switching
-there is no need to tie up a single communication line
-can overcome failed or busy nodes
-high data transmission speed
-easy to expand package usage
Disadvantages of packet switching
-packets may be lost and need resending
-method is more prone to errors
-delay at destination as packets need to be reordered
What is the time to live value?
the maximum amount of time a packet can stay on a network before it is delivered, and this is measured in hops ( a hop is the number of routers a packet moves across before getting to its destination computer)
What is the method to stop lost packets from clogging up a network and how does it work?
Hopping is used.
-a hop number is added to the packet number
-this number is reduced by 1 every time the packet leaves a router
-once a hop number reaches 0 and the packet isn’t at destination, the packet is deleted
-the missing packet will be flagged by receiving computer and a request to re-send packet will be made
What are the 2 methods of data transmission?
serial transmission and parallel transmission
What is serial data transmission?
Data is sent one bit at a time over a single wire
Advantages of serial data transmission
-reliable over long distances
-data arrives in order
-less likely to experience interface
-less likely to have errors
-cheaper as only one wire is required
Disadvantages of serial data transmission
-slow transmission
-not suitable for large amounts of data
What is parallel data transmission?
Data is sent several bits at a time simultaneously over several and separate wires
Advantages of parallel data transmission
-fast transmission
-good for short distances
Disadvantages of parallel data transmission
-unreliable over long distances (data can become skewed)
-bits arrives out of order
-more expensive as there are multiple wires
What are the 3 transmission modes?
simplex data transmission, half-duplex data transmission, full-duplex data transmission
What is simplex data transmission?
Data can be sent in one direction only
Advantages and disadvantages of simplex data transmission
Advantages:
-no traffic issues
Disadvantages:
-slow
-2 devices can’t communicate
What is half-duplex data transmission?
Data can be sent in both directions but not at the same time
Advantages and disadvantages of half-duplex data transmission
Advantages:
-2 devices can communicate
-troubleshooting is easy
Disadvantages:
-slow
-delay in data transmission
What is full-duplex data transmission?
Data can be sent in both directions simultaneously
Advantages and disadvantages of full-duplex data transmission
Advantages:
-fast
-best performance
-no delay
Disadvantages:
-requires more bandwidth
What is the Universal Serial Bus (USB)?
a form of serial data transmission, its an interface connecting devices to a computer over a reasonably short distance via USB cable
What does the USB cable consist of?
-Two wires for power (red and black)
-Two wires for data transmission (white and green)
What happens when a device is plugged into a computer using a USB port/
1) the computer automatically detects that a device is present
2) the device is automatically recognised and the appropriate device driver software is loaded up
3)the computer and device can communicate
Benefits of USB
-industry-standard/universal
-automatically detected
-only fit one way (prevents incorrect connections)
-supports different data transmission rates
-can transfer power and data
-backwards compatible(older versions are still supported)
Drawbacks of USB
-maximum cable length is 5m
-early USB standards may nit be supported by latest computers
-multiple connectors so device needs the right cable
How can errors occur during data transmission?
interference, problems during packet switching, skewing of data
What can errors lead to?
data loss, data gain, data change
Name error detection methods
parity checks, parity blocks, checksum, echo check, check digits, automatic repeat query
What is a parity check?
A method of checking whether a byte has been sent correctly by checking whether the total number of 1s in the byte is odd or even
What does even parity check and how does it work?
Checks if there is an even number of 1-bits in the byte
1) the number of 1s are counted
2) a parity bit (0 or 1) is added to each byte before transmission to make the sum of the bits even
3) after transmission, if the number is even, no error has occurred
4)after transmission, if the number is odd, an error is detected
What does odd parity check and how does it work?
Checks if there is an odd number of 1-bits in the byte
1) the number of 1s are counted
2) a parity bit (0 or 1) is added to each byte before transmission to make the sum of the bits odd
3) after transmission, if the number is odd, no error has occurred
4)after transmission, if the number is even, an error is detected
What are limitations of parity checks?
-transposition errors is when bits position switches but still results in even/odd amounts passing the check (two bits change)
-can’t identify location/which bit was corrupted
How to overcome limitations of parity checks?
parity blocks
What is a parity block?
horizontal and vertical parity check on a block of data being transmitted
Why can parity blocks detect errors the parity bits can’t?
it identifies the horizontal and vertical position of all changes
What is a checksum?
A method of error detection using compared calculations performed on data when sending and when receiving
How does a checksum work?
1) data is sent in blocks together with a calculated value known as the checksum
2) the receiving computer will perform the same calculation on the data to regenerate the checksum
3) the two checksum values are compared
4) if there is a mismatch, then an error has occurred, and the receiving computer will request the sending computer to resend the data. This process is repeated until the correct data is received.
How to calculate the checksum?
1) If the sums of the bytes is less than or equal to 255 then this value is the checksum
1) If the sums of the bytes is more than 255 then:
-Divide sum of bytes by 256
-Round down to integer
-Multiply by 256
-Subtract number from sum of bytes
What is an echo check?
A method of error detection where the receiving computer sends the full data back to the sending computer, and the sending computer compares against what it originally sent
How does an echo check work?
1) sending computer sends data
2) receiving computer receives data sends back an exact copy to the sending computer
3) sending computer compares the returned data with the original
4) If they match, the data was sent with no errors
If they don’t match, an error has occurred
Disadvantages of echo checks
-can’t tell if data was corrupted during transit to destination or the way back
-slow since dats has to be sent twice
What is a check digit?
A check digit is an extra digit added to a number that can be calculated from the other digits in the number. it is the last digit of the code.
What are check digits used for?
Barcodes such as the ISBN and VIN
How to calculate check digit?
1) Put all digits except the last one into a table
2) Give it a multiplier, repeating 1 and 3
3) Multiply multiplier with original digit
4) Add all digits after multiply together
5) Round down to integer
6) Find difference between 4) and 5)

What is an automatic repeat request (ARQ)?
A set of rules used for error control during transmission.
How does an ARQ work?
1) receiving device receives an error detection code as part of the data transmission
2) it sends a message back to the sending device known as acknowledgements (ACK) to indicate whether transmission was successful
3) Positive ACK is sent if no errors were detected
Negative ACK is sent if an error was detected and requests re-transmission of dat
4) This process is repeated until receives the complete packet or until time out
What is time-out?
What is encryption?
the process of making data meaningless using encryption keys without correct decryption key the data can not be decoded.
What is the need of encryption?
prevents data from being understood not stolen
What is used to encrypt data?
an encryption algorithm that only people with the same algorithm can decrypt
What is plain text?
text that is not encrypted.
What is cipher text?
text that has been encrypted.
What is symmetric encryption?
uses the same key to encrypt and decrypt data
How does symmetric encryption work?
1) sending computer sends encrypted message and the key separately
2) receiving computer uses key to decrypt message
Disadvantages of symmetric encryption
Difficult to keep encryption key a secret: if a malicious user intercepts the key, they can read the message
What is asymmetric encryption?
two separate keys are used. one key is used for encryption and the other key is used for decryption.
What are the two keys in asymmetric encryption?
Public key- available to all computers that want to exchange an encrypted message, used to encrypt
Private key- only known to the computer user, used to decrypt
How does asymmetric encryption work? (with Alex & Michael)
1) Alex uses an algorithm to generate a matching pairs of keys (private and public) that is stored in his computer
2) Alex sends his public key to Michael
3) Michael uses Alex’s private key to encrypt the document he wants to send to Alex
4) Michael sends his encrypted document back to Alex
5) Alex uses his private key to decrypt it