Digital Solutions External
5.0(5)
5.0(5)
Card Sorting
1/19
Earn XP
Description and Tags
Last updated 7:30 AM on 10/31/22
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
20 Terms
1
New cards
Describe encryption and authentication strategies appropriate for securing data transmissions and their differences.
Encryption can be symmetric or asymmetric. Symmetric encryption is where the same key is used to encrypt and decrypt the plain text, whereas asymmetric encryption is where different keys are used to encrypt and decrypt. This results in asymmetric encryption being much more secure.
Authentication is the process of verifying that someone is who they say they are. A digital signature is data encrypted with the private key of a user using a mathematical scheme. An application token is a digital key that can be used to access protected data, and any program or user with the token can access the data.
Authentication is the process of verifying that someone is who they say they are. A digital signature is data encrypted with the private key of a user using a mathematical scheme. An application token is a digital key that can be used to access protected data, and any program or user with the token can access the data.
2
New cards
Describe features of symmetric (DES, Triple DES, AES) and asymmetric (RSA) encryption algorithms.
TripleDES encrypts data three times using a different key for at least one of the encryption iterations. It is slower than most other methods as the encryption process is repeated three times. (DES is only encrypted once but is not as secure.)
Advanced Encryption Standard (AES) uses a block cipher. This breaks up the data into blocks, which is then coded and decoded using the same key.
In RSA, a public key is used to encrypt the message and a private key is used to decrypt it. The strength of the algorithm is attributed to the large prime numbers and keys used in the encryption calculations. However, the size of the integers also results in a slower encryption and decryption process.
Advanced Encryption Standard (AES) uses a block cipher. This breaks up the data into blocks, which is then coded and decoded using the same key.
In RSA, a public key is used to encrypt the message and a private key is used to decrypt it. The strength of the algorithm is attributed to the large prime numbers and keys used in the encryption calculations. However, the size of the integers also results in a slower encryption and decryption process.
3
New cards
Describe how data compression, encryption and hashing are used in the storage and transfer of data.
Data compression: the reduction in the number of bits needed to represent the data. This can save storage capacity, speed up file transfer and decrease costs for storage hardware and network bandwidth.
Encryption: Helps protect the confidentiality of digital data either stored on computer systems or transmitted through a network like the Internet.
Hashing: algorithms create a fixed-length, unique string of text for any form or size of data. Passwords are often saved in a database as a hash value as, if you input your password, the hash value will always be the same. Databases will run inputted passwords through a hashing algorithm and cross-check it with their databases to find a password match.
Encryption: Helps protect the confidentiality of digital data either stored on computer systems or transmitted through a network like the Internet.
Hashing: algorithms create a fixed-length, unique string of text for any form or size of data. Passwords are often saved in a database as a hash value as, if you input your password, the hash value will always be the same. Databases will run inputted passwords through a hashing algorithm and cross-check it with their databases to find a password match.
4
New cards
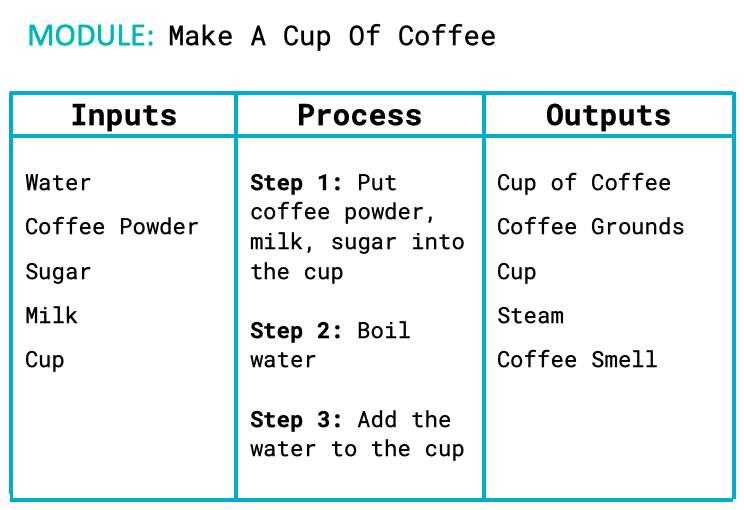
Describe how simple algorithms consist of input, process and output at various stages.
IPO tables
5
New cards
Describe how useability principles are used to inform solution development.
Accessibility: ability to be used by many different people, even people with disabilities.
Effectiveness: ability of users to use the system to do the work they need to do, includes reliability.
Safety: ability for users to make errors and recover from the mistake.
Utility: ability of the system to provide all the functionality that users need.
Learnability: how easy the system is to learn.
Effectiveness: ability of users to use the system to do the work they need to do, includes reliability.
Safety: ability for users to make errors and recover from the mistake.
Utility: ability of the system to provide all the functionality that users need.
Learnability: how easy the system is to learn.
6
New cards
Describe how the elements and principles of visual communication inform user interface development.
Elements: scale, space, colour, shape, form, texture, tone, line and proportion.
Principles: balance, contrast, alignment, proximity, harmony, repetition and hierarchy.
Principles: balance, contrast, alignment, proximity, harmony, repetition and hierarchy.
7
New cards
Explain Australian Privacy Principles and ethics applicable to the use of personally identifiable or sensitive data from a digital systems perspective.
1. Entities should handle personal information openly and honestly. This includes a policy that describes how your personal information is managed.
2. Individuals should be allowed to remain anonymous if they so desire, and use pseudonyms for personal data when possible.
3. Organisations must demonstrate that it needs personal data for its functions or activities.
4. Organisations must prove that if personal information is solicited it could be collected according to Principle 3.
5. An entity collecting personal information should notify the individual from whom the data is collected.
6. Entities should only use personal data that is relevant to the original purpose for which the information was collected. If the individual explicitly allows use of their data for another purpose, or if the entity could reasonably expect such use, they may collect other data.
7. Organisations may not use private information for marketing unless individuals can reasonably expect such use of their information or individuals have provided their consent and have a clear way to opt out.
8. When an entity shares personal data with someone outside Australia, the recipient must comply with the Australian Privacy Principles via contractual obligation. This is unless the entity sharing the data believes the recipient maintains a similar privacy regulation to the APP in their location, or the individual consented to sharing of their data with overseas parties and understands the entity does not take responsibility over the privacy practices of the recipient.
9. An entity may not use a government-related identifier as their own, or disclose an identifier of a person, unless the entity is authorised to do so by laws, or the identifier is needed to verify the identity of the individual.
10. All information received by the entity must be accurate, complete and up to date, and the organisation may only disclose and use information if it verifies this.
11. Entities are required to implement measures specifically designed for the protection of stored personal information from data interference, loss, misuse and modification, as well as unauthorised access and disclosure.
12. Entities must give the individual access to their personal information on request.
13. Entities must collect accurate and complete information, update personal information, collect only relevant, non-misleading information, notify affected entities when any corrections are made while collecting personal data.
2. Individuals should be allowed to remain anonymous if they so desire, and use pseudonyms for personal data when possible.
3. Organisations must demonstrate that it needs personal data for its functions or activities.
4. Organisations must prove that if personal information is solicited it could be collected according to Principle 3.
5. An entity collecting personal information should notify the individual from whom the data is collected.
6. Entities should only use personal data that is relevant to the original purpose for which the information was collected. If the individual explicitly allows use of their data for another purpose, or if the entity could reasonably expect such use, they may collect other data.
7. Organisations may not use private information for marketing unless individuals can reasonably expect such use of their information or individuals have provided their consent and have a clear way to opt out.
8. When an entity shares personal data with someone outside Australia, the recipient must comply with the Australian Privacy Principles via contractual obligation. This is unless the entity sharing the data believes the recipient maintains a similar privacy regulation to the APP in their location, or the individual consented to sharing of their data with overseas parties and understands the entity does not take responsibility over the privacy practices of the recipient.
9. An entity may not use a government-related identifier as their own, or disclose an identifier of a person, unless the entity is authorised to do so by laws, or the identifier is needed to verify the identity of the individual.
10. All information received by the entity must be accurate, complete and up to date, and the organisation may only disclose and use information if it verifies this.
11. Entities are required to implement measures specifically designed for the protection of stored personal information from data interference, loss, misuse and modification, as well as unauthorised access and disclosure.
12. Entities must give the individual access to their personal information on request.
13. Entities must collect accurate and complete information, update personal information, collect only relevant, non-misleading information, notify affected entities when any corrections are made while collecting personal data.
8
New cards
Explain network transmission principles, including latency, jitter, guarantee and timeliness of delivery, and protocols relevant to the transmission of data over the internet, e.g. HTTP, HTTPS, FTP, VPN, streaming and broadcasting data packets.
Latency is the time it takes for data to pass from one point on a network to another. The longer it takes for the data to transfer, the higher the latency is. A positive user experience will have low latency.
Jitter is when there is a time delay in the sending of data packets over network connection. This is often caused by network congestion. The higher the congestion, the higher the jitter, meaning low jitter ensures a positive user experience.
Hypertext Transfer Protocol (HTTP) is used to load web pages using hypertext links. It is primarily used for communication between web browsers and web servers.
Hypertext Transfer Protocol Secure is the secure version of HTTP. It encrypts and digitally signs normal HTTP requests and responses.
File Transfer Protocol (FTP) is a set of rules that governs how computers transmit files from one system to another over the Transmission Control Protocol (TCP) or Internet Protocol (IP).
Virtual Private Network (VPN) is a service that protects your internet connection and privacy online. It creates a private network from a public internet connection.
Streaming is a method of transmitting or receiving data over a computer network as a steady, continuous flow, allowing playback to start while the rest of the data is still being received.
Broadcasting refers to transmitting a data packet that will be received by every device on the network. The scope of the broadcast is limited to a broadcast domain.
Jitter is when there is a time delay in the sending of data packets over network connection. This is often caused by network congestion. The higher the congestion, the higher the jitter, meaning low jitter ensures a positive user experience.
Hypertext Transfer Protocol (HTTP) is used to load web pages using hypertext links. It is primarily used for communication between web browsers and web servers.
Hypertext Transfer Protocol Secure is the secure version of HTTP. It encrypts and digitally signs normal HTTP requests and responses.
File Transfer Protocol (FTP) is a set of rules that governs how computers transmit files from one system to another over the Transmission Control Protocol (TCP) or Internet Protocol (IP).
Virtual Private Network (VPN) is a service that protects your internet connection and privacy online. It creates a private network from a public internet connection.
Streaming is a method of transmitting or receiving data over a computer network as a steady, continuous flow, allowing playback to start while the rest of the data is still being received.
Broadcasting refers to transmitting a data packet that will be received by every device on the network. The scope of the broadcast is limited to a broadcast domain.
9
New cards
Explain methods for data exchange used to transfer data across networked systems including REST, JSON and XML.
Representational State Transfer (REST) is a framework used to exchange data using an Internet-accessible data resource instead of an advertised data service. It relies on standard HTTP requests using embedded internet security protocols and each request is processed independently.
JavaScript Object Notation (JSON) is a common data exchange format used to structure data in key-value pairs. It is supported by a wide range of programming languages, including JavaScript and HTML.
Extensible Markup Language (XML) is an extension to HTML that allows developers to create data tags for storing formatted data in a webpage. It follows a similar hierarchal structure to HTML.
JavaScript Object Notation (JSON) is a common data exchange format used to structure data in key-value pairs. It is supported by a wide range of programming languages, including JavaScript and HTML.
Extensible Markup Language (XML) is an extension to HTML that allows developers to create data tags for storing formatted data in a webpage. It follows a similar hierarchal structure to HTML.
10
New cards
Symbolise, explain, analyse and evaluate Caesar, Polyalphabetic (e.g. Vigenere and Gransfield), and one-time pad encryption algorithms.
The Caesar cipher is a substitution cipher where each letter in the plaintext is replaced by a letter some fixed number of positions down in the alphabet. It is not very secure as once the fix number is discovered, the entire plaintext can be decrypted.
A polyalphabetic cipher is a cipher based on substitution, using multiple solution alphabets. A key is created and multiplied according to the length of the plaintext. The first letter in the plaintext is matched to the first letter of the key and the subsequent encrypted letter is outputted according to the key's position in the alphabet. (In the image example, the key is AYUSH and the plaintext is GEEKS.) Polyalphabetic ciphers are much more secure than monoalphabetic ciphers as, due to the multiple alphabets, it takes a lot longer to decrypt the entire message.
A one-time pad (OTP) is a system in which a randomly generated private key is used only once to encrypt a message that is then decrypted by the receiver using a matching one-time pad and key. OTP is extremely secure as it cannot be retrieved without the encrypting key. However, it is not completely secure as, even though the key is randomly generated, it is just as likely to be a complete scramble of letters as it is to be a string of the same letter, which is not secure.
A polyalphabetic cipher is a cipher based on substitution, using multiple solution alphabets. A key is created and multiplied according to the length of the plaintext. The first letter in the plaintext is matched to the first letter of the key and the subsequent encrypted letter is outputted according to the key's position in the alphabet. (In the image example, the key is AYUSH and the plaintext is GEEKS.) Polyalphabetic ciphers are much more secure than monoalphabetic ciphers as, due to the multiple alphabets, it takes a lot longer to decrypt the entire message.
A one-time pad (OTP) is a system in which a randomly generated private key is used only once to encrypt a message that is then decrypted by the receiver using a matching one-time pad and key. OTP is extremely secure as it cannot be retrieved without the encrypting key. However, it is not completely secure as, even though the key is randomly generated, it is just as likely to be a complete scramble of letters as it is to be a string of the same letter, which is not secure.
11
New cards
Explain how application sub-systems, e.g. front end and back end, work together to constitute a solution.
"Front end" refers to the user interface, while "back-end" means the server, application and database that work behind the scenes to deliver information to the user.
The user enters a request through the interface. It's then verified and communicated to the server, which pills the necessary data from the database and sends it back to the user.
The user enters a request through the interface. It's then verified and communicated to the server, which pills the necessary data from the database and sends it back to the user.
12
New cards
Explain secure data transmission techniques and processes, including the use of encryption, decryption, authentication, hashing and checksums.
Encryption is the process of transforming data into an unintelligible form to prevent the unauthorised use of the data. To read an encrypted file, you must have access to a secret decryption key or password.
Authentication is used by a server when the server needs to know exactly who is accessing their information or site. It is also used when transmitting data so the data can only be received by the correct person or people.
Hashing enables people to get data authorisation without knowing the content on the data. Hashing algorithms and databases are used to store passwords, instead of saving them as plaintext.
A checksum is a value that represents the number of bits in a transmission message and is used to detect high-level errors within data transmissions. A transmitter computes a numerical value according to the number of bits in a message and sends it along with each message frame. At the receiver end, the same checksum function is applied to the message frame to retrieve the numerical value.
Authentication is used by a server when the server needs to know exactly who is accessing their information or site. It is also used when transmitting data so the data can only be received by the correct person or people.
Hashing enables people to get data authorisation without knowing the content on the data. Hashing algorithms and databases are used to store passwords, instead of saving them as plaintext.
A checksum is a value that represents the number of bits in a transmission message and is used to detect high-level errors within data transmissions. A transmitter computes a numerical value according to the number of bits in a message and sends it along with each message frame. At the receiver end, the same checksum function is applied to the message frame to retrieve the numerical value.
13
New cards
Explain the basic constructs of an algorithm, including assignment, sequence, selection, condition, iteration and modularisation.
An assignment statement sets and/or re-sets value/s in a database according to their variable name.
Sequencing is the specific order in which instructions are performed in an algorithm.
Selection is a decision or question. At some point in an algorithm there may need to be a question because the algorithm has reached a step where one or more options are available. Depending on the answer given, the algorithm will follow certain steps and ignore others.
A condition is a step in an algorithm where a decision must be made. (Condition is the question, selection is the answer.)
Iteration is the process of repeating steps until a particular condition has been met.
Modularisation is the process by which we select and group programming instructions that fulfil a specific function.
Sequencing is the specific order in which instructions are performed in an algorithm.
Selection is a decision or question. At some point in an algorithm there may need to be a question because the algorithm has reached a step where one or more options are available. Depending on the answer given, the algorithm will follow certain steps and ignore others.
A condition is a step in an algorithm where a decision must be made. (Condition is the question, selection is the answer.)
Iteration is the process of repeating steps until a particular condition has been met.
Modularisation is the process by which we select and group programming instructions that fulfil a specific function.
14
New cards
SQL SELECT query structure
SELECT [column/s] FROM [table1]
INNER JOIN [table2] ON [table1].[column] = [table2].[column]
WHERE [condition]
GROUP BY [column]
HAVING [condition]
ORDER BY [column name] [ASC/DESC];
INNER JOIN [table2] ON [table1].[column] = [table2].[column]
WHERE [condition]
GROUP BY [column]
HAVING [condition]
ORDER BY [column name] [ASC/DESC];
15
New cards
SQL ALTER and DROP query structure
ALTER TABLE [table]
DROP COLUMN [column];
DROP COLUMN [column];
16
New cards
Identify and explain the 7 layers of TCP
1. Physical: Actual hardware sits at this layer. It transmits signals over media.
2. Data link: Translates binary/bits into signals and allows upper layers to access media.
3. Network: This layer determines how data is sent to the receiving device. It’s responsible for packet forwarding, routing, and addressing.
4. Transport: This layer coordinates data transfer between system and hosts, including error-checking and data recovery.
5. Session: This layer establishes and terminates connections between devices. It also determines which packets belong to which text and image files.
6. Presentation: This layer converts data to and from the Application layer. In other words, it translates application formatting to network formatting and vice versa. This allows the different layers to understand each other.
7. Application: Most of what the user actually interacts with is at this layer. Web browsers and other internet-connected applications (like Skype or Outlook) use Layer 7 application protocols.
2. Data link: Translates binary/bits into signals and allows upper layers to access media.
3. Network: This layer determines how data is sent to the receiving device. It’s responsible for packet forwarding, routing, and addressing.
4. Transport: This layer coordinates data transfer between system and hosts, including error-checking and data recovery.
5. Session: This layer establishes and terminates connections between devices. It also determines which packets belong to which text and image files.
6. Presentation: This layer converts data to and from the Application layer. In other words, it translates application formatting to network formatting and vice versa. This allows the different layers to understand each other.
7. Application: Most of what the user actually interacts with is at this layer. Web browsers and other internet-connected applications (like Skype or Outlook) use Layer 7 application protocols.
17
New cards
What is the difference between data security and data protection?
Data protection is the mechanism of making copies of your data to restore in the event of a loss or corruption.
Data security is where you keep your data safe from unauthorised access and distribution using various mechanisms.
Data security is where you keep your data safe from unauthorised access and distribution using various mechanisms.
18
New cards
What are some external and internal threats to data security?
External: nation-states, terrorists, hackers/cybercriminals, competitors (industrial espionage)
Internal: malicious insiders, poorly trained/careless staff, disgruntled employees
Other: natural disasters and power outages
Internal: malicious insiders, poorly trained/careless staff, disgruntled employees
Other: natural disasters and power outages
19
New cards
What are the three data storage security principles?
Confidentiality, integrity and availability (CIA).
20
New cards
What are the best data security practices?
- data storage security policies (CIA)
- access control
- encryption
- data loss prevention
- strong network security
- strong endpoint security
- redundancy
- backup and recovery
- access control
- encryption
- data loss prevention
- strong network security
- strong endpoint security
- redundancy
- backup and recovery