MSIS 2103 Exam 2
1/93
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
94 Terms
Ethics
Sets of principles about right and wrong. Used to make choices guiding decisions.
Law
System of rules, defines what we can and cannot do
Legal acts vs ethical acts
Legal acts conform to the law. Ethical acts conform to what an individual believes to be the right thing to do. (Legal activity does not mean it's ethical)
Problem statement
Clear, concise description of the issue being addressed in decision making.
Professional code of ethics
States the principles and core values that an organization wishes to develop in its leaders and members.
Fair information practices
Set of guidelines governing the collection and use of personal data
General Data Protection Regulation (GDPR)
Proposed set of regulations adopted by the European Union to protect Internet users from clandestine tracking and unauthorized personal data usage.
Fair Credit Reporting Act
Act that regulates credit-reporting bureaus regarding their collection, storage, and use of credit information.
Right to Financial Privacy Act
Act that protects the records of financial institutions' customers from unauthorized scrutiny by the federal government.
Fair and Accurate Credit Transitions Act
Act that allows consumers to request and obtain free credit reports.
Health Insurance Portability and Accountability Act (HIPAA)
Act that requires standardized electronic transactions, codes, and identifiers. Also requires health care providers to obtain written consent from patients prior to disclosing any information in their medical records. It also fully digitized medical records.
American Recovery and Reinvestment Act Title XIII
Includes strong privacy provisions for electronic health records (EHRs), including banning the sale of health information, promoting the use of audit trails and encryption, providing rights of access for patients, and mandating that each individual whose health information has been exposed be notified within 60 days after discovery of a data breach.
Family Educational Rights and Privacy Act (FERPA)
Act that assigns certain rights to parents regarding their children's educational records.
Children's Online Privacy Protection Act (COPPA)
A U.S. federal act that requires operators of online services or Web sites directed at children under the age of 13 to obtain parental consent prior to the collection, use, disclosure, or display of a child's personal information
Fourth Amendment
Protects against unreasonable search and seizure
First Amendment
Protects American's rights to freedom of religion, freedom of expression, and freedom to assemble peaceably. Some speech is not protected or forbidden.
Section 230 of the Communications Decency Act
Provides immunity to an Internet service provider (ISP) that publishes user-generated content
Internet filtering
Blocks access to certain Web sites containing material deemed inappropriate or offensive. May block too much
Children's Internet Protection Act (CIPA)
An act that requires federally financed schools and libraries to use some form of technological protection (such as an Internet filter) to block computer access to obscene material, pornography, and anything else considered harmful to minors.
Defamation
The making of either an oral (slander) or a written (libel) statement of alleged fact that is false and that harms another person. Harm is often of a financial nature.
Frequent defamation lawsuits
Considered a form of censorship. Seek to stop unwanted speech or writings.
Hate speech
Persistent or malicious harassment aimed at a specific person that can be prosecuted under the law.
Fake news
Form of censorship in the form of a false story presented as being factually accurate and appears to be news. Usually created to advance political view or agenda.
Safety-critical system
A system whose failure may cause human injury or death.
Database
A well-designed, organized, and carefully managed collection of data.
Entity
A person, place, or thing (object) for which data is collected, stored, and maintained
File
Collection of entities
Attribute
Characteristic of an entity
Domain
Range of allowable values for a data attribute
Data item
Specific value of a data attribute
Record
Collection of attributes about a specific entity
Primary key
Attribute or set of attributes that uniquely identifies the record
Foreign key
Attribute in one table that refers to the primary key in another table
Schema
Description defining the database's logical and physical structure. Identifies the table and the attributes in each table
Data Definition Language (DDL)
Collection of instructions and commands. Defines and describes data and relationships in a specific database
Data dictionary
Detailed description of data stored in the database
Concurrency control
Addresses situation where two or more users or applications access the same record at the same time
Selecting
Eliminating rows according to certain criteria
Projecting
Eliminating columns in a table
Joining
Combining two or more tables through common data attributes to create a new table
Data normalization
Eliminates data redundancy
SQL
A special-purpose programming language used for accessing and manipulating relational database data.
ACID properties
Properties (atomicity, consistency, isolation, durability) that guarantee relational database transactions are processed reliably and ensure the integrity of data in the database.
Data management
Integrated set of functions. Defines the processers by which data is obtained, certified fit for use, stored, secured, and processed. Ensures data accessibility, reliability, and timeliness meet the data users' needs.
Data governance
Defines roles, responsibilities, and processes. Ensures data can be trusted and used by the entire organization
Big data
Enormous data (terabytes or more) where traditional processes of dealing with them are incapable
Online Transaction Processing (OLTP) systems
Traditionally used to capture data. Do not support data analysis required today
Data warehouse
Large database that holds business information from many sources in the enterprise.
Extract Transform Load (ETL) process
Edits and transforms data into a data warehouse format. Extracts data from a variety of sources and loads data into the warehouse
Data mart
Subset of a data warehouse. Used by small and medium-sized businesses and departments within large companies to support decision making.
Data lake
Takes a "store everything" approach to big data. Saves all data in its raw and unaltered form.
NoSQL database
Database modeled without using table relations. More flexible than relational databases and provides improved access speed. Uses horizontal scaling and does not conform to true ACID properties when processing transactions.
Key-value NoSQL databases
Database with two columns ("key" and "value")
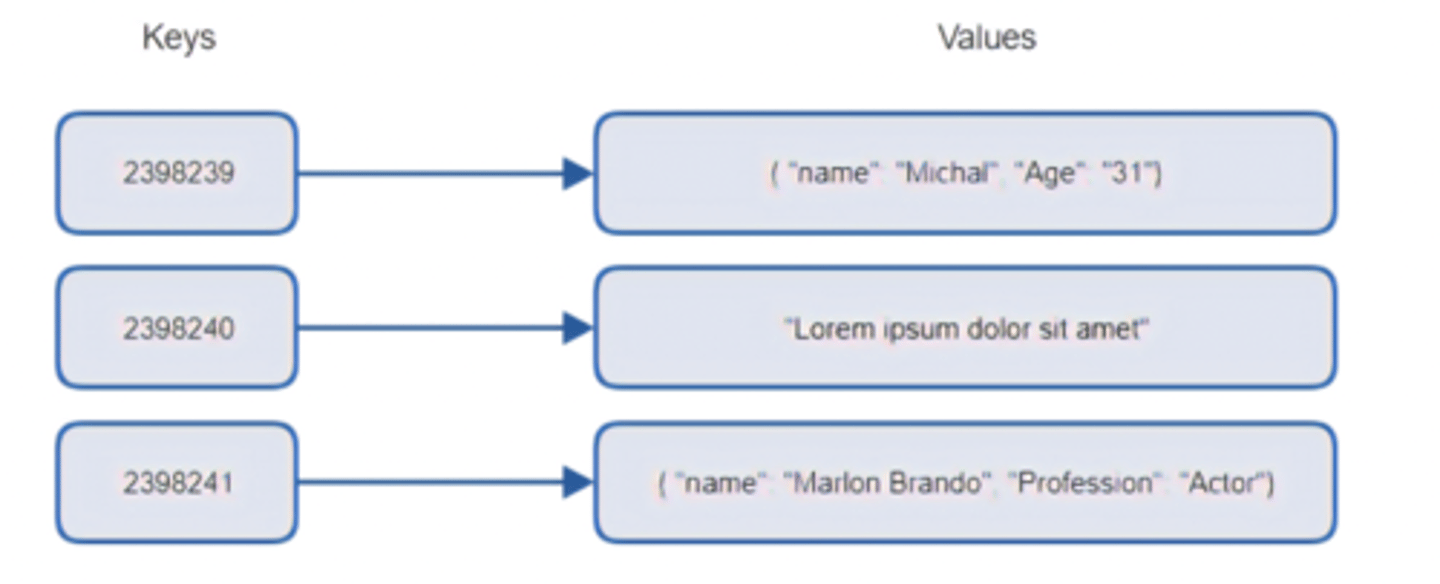
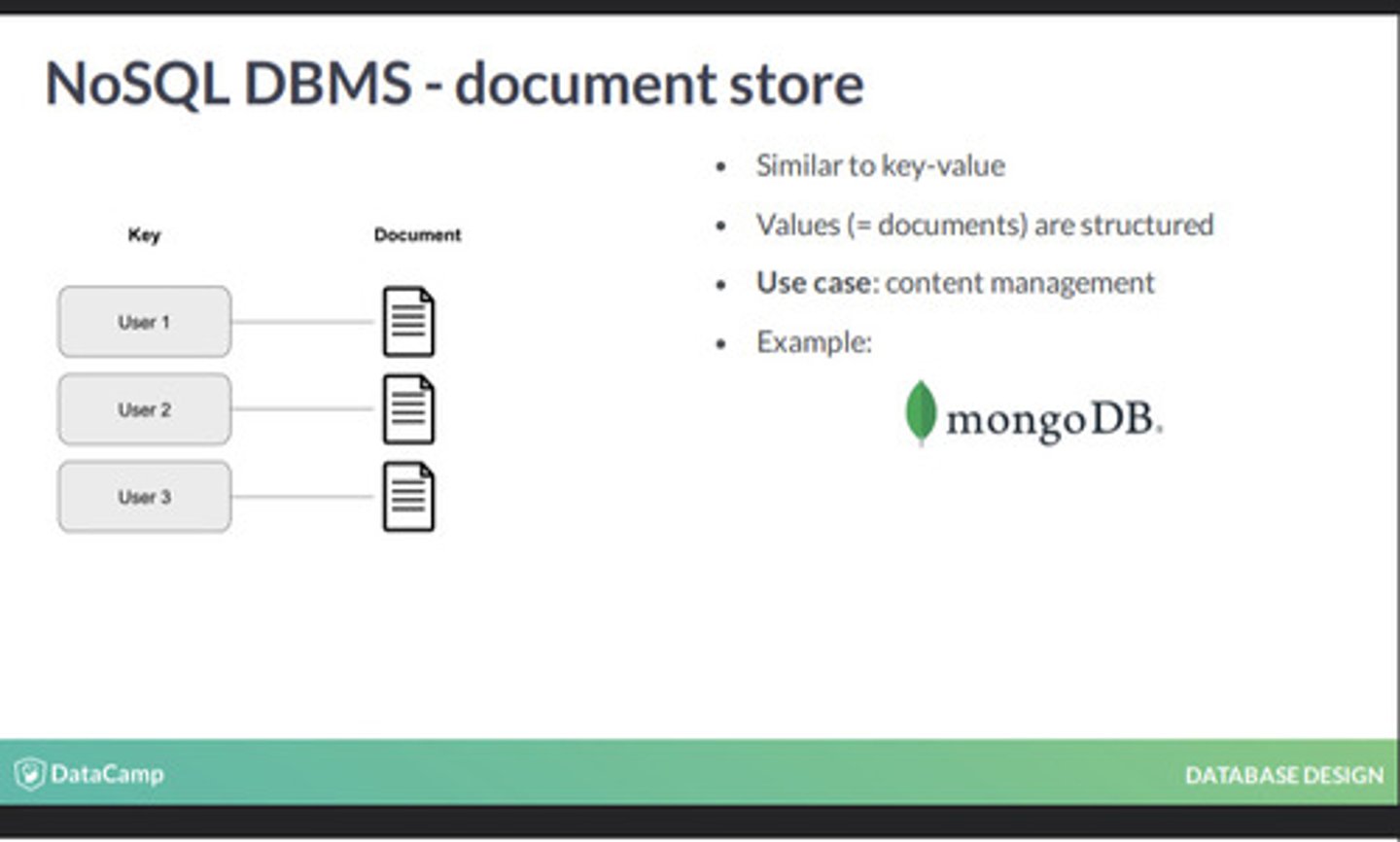
Document NoSQL databases
Store, retrieve, and manage document-oriented information
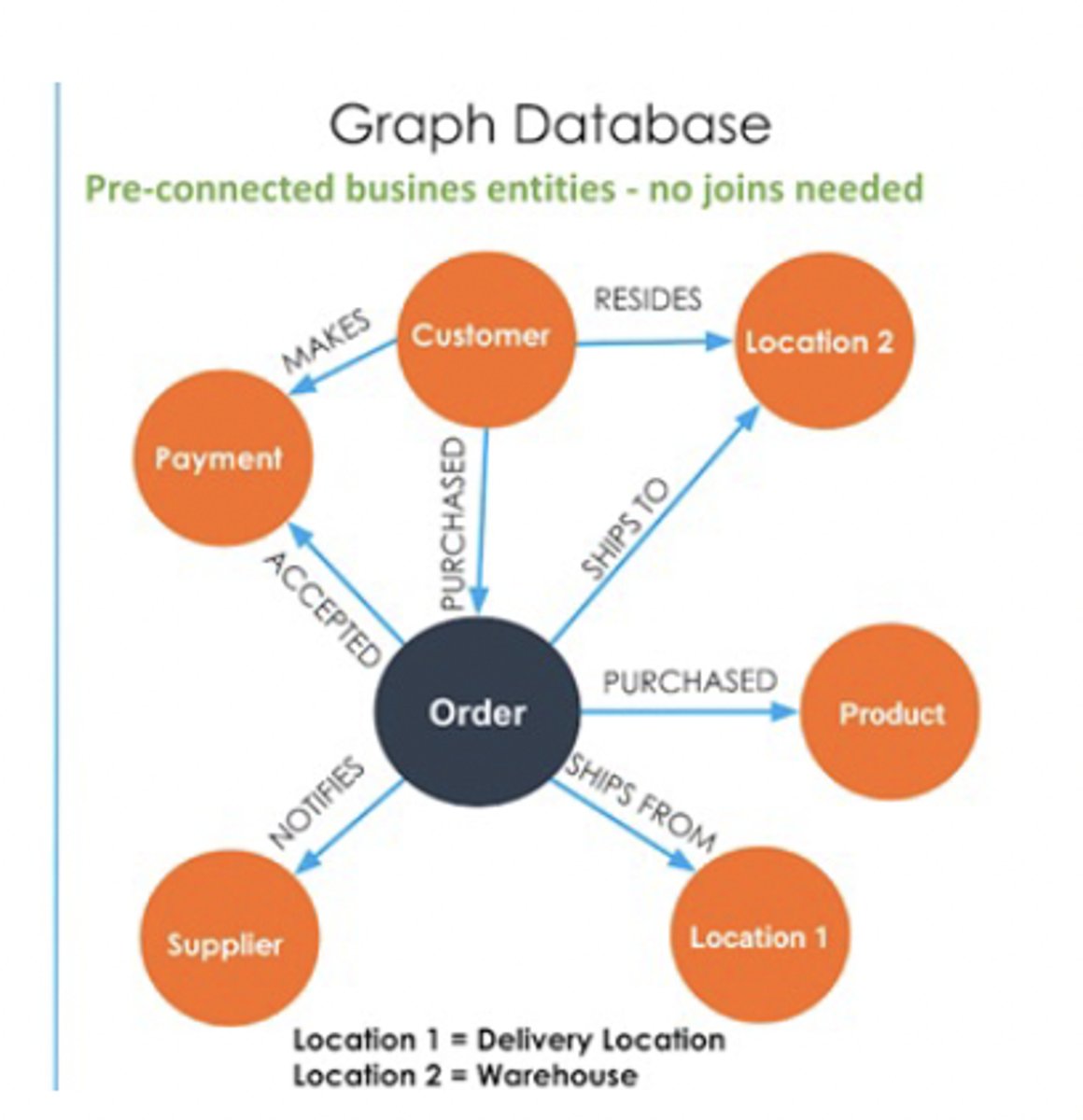
Graph NoSQL databases
Database that is well-suited for analyzing interconnections
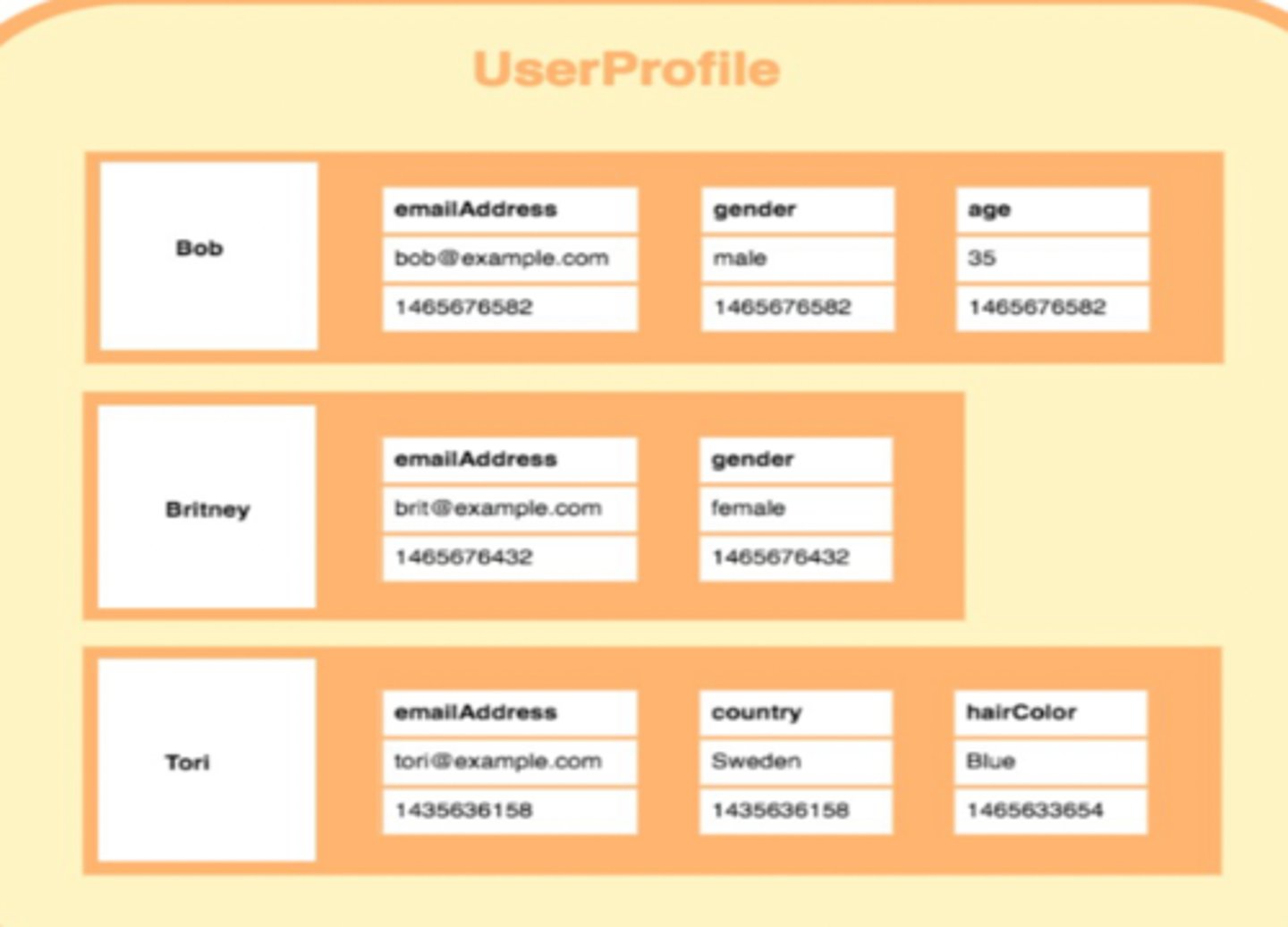
Column NoSQL databases
Database that stores data in columns
Hadoop
Open-source software framework that enables distributed parallel processing of huge amounts of data across many inexpensive computers.
Hadoop Distributed File System (HDFS)
A system used for data storage that divides the data into subsets and distributes the subsets onto different servers for processing.
Descriptive Analysis
Preliminary data processing stage that identifies data patterns. Includes 2 types: Visual Analytics and Regression Analysis. Answers questions: "Who, what, where, when, and to what extent."
Visual Analytics
Type of Descriptive Analysis that presents data graphically.
Word cloud
Visual depiction of a set of words where words are grouped together based on frequency of their occurrence

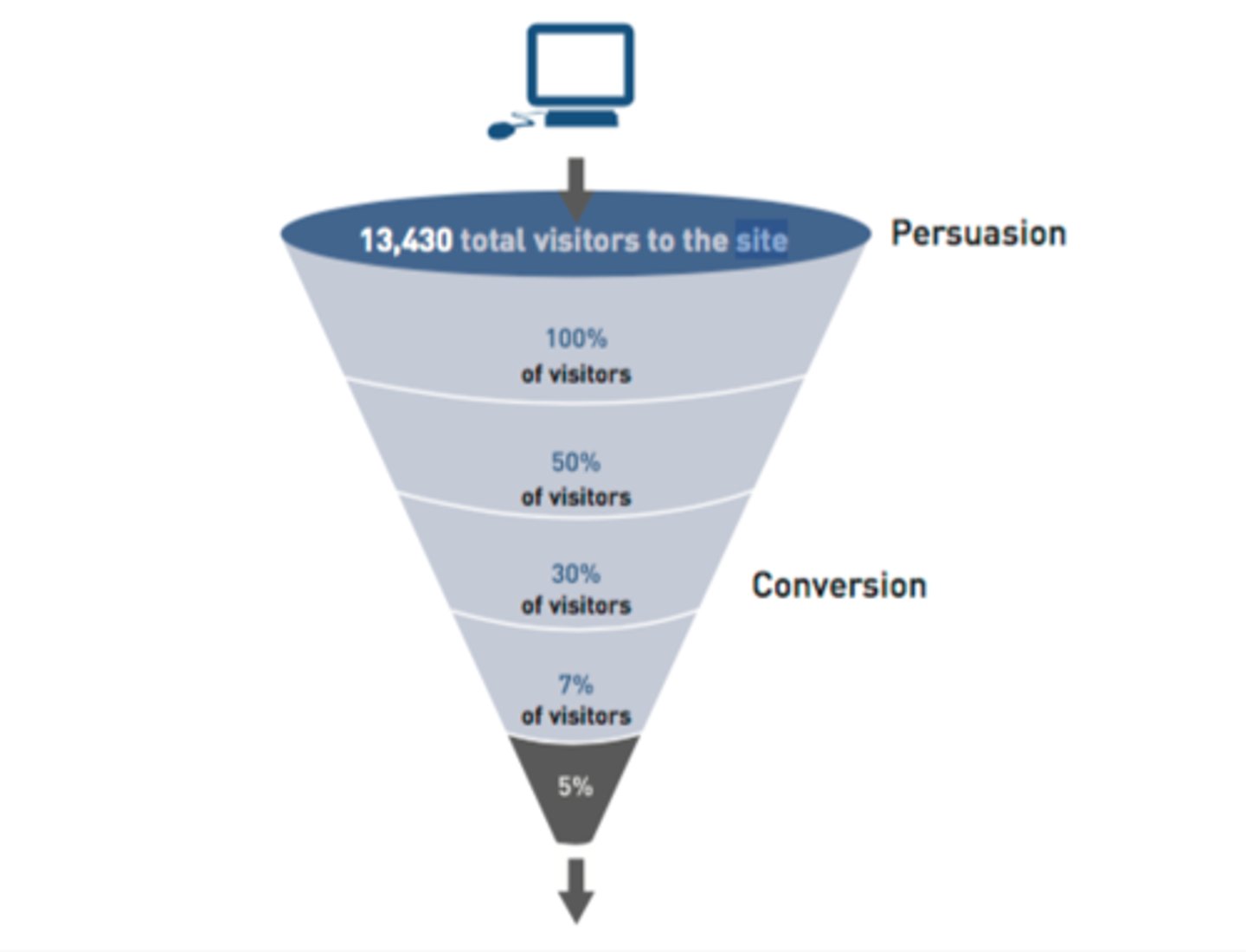
Conversion Funnel
A graphical representation that summarizes the steps a consumer takes in making the decision to buy your product and become a customer.
Regression Analysis
Type of Descriptive Analysis that determines the relationship b/w a dependent variable and one or more independent variables. Produces a regression equation
Predictive Analytics
Techniques to analyze current data that identifies future probabilities and trends.
Time Series Analysis
Uses statistical methods and analyzes time series data to extract meaningful statistics and characteristics.
Data mining
A BI analytics tool used to explore large amounts of data for hidden patterns to predict future trends and behaviors for use in decision making
Genetic Algorithm
An artificial intelligent system that mimics the evolutionary, survival-of-the-fittest process to generate increasingly better solutions to a problem
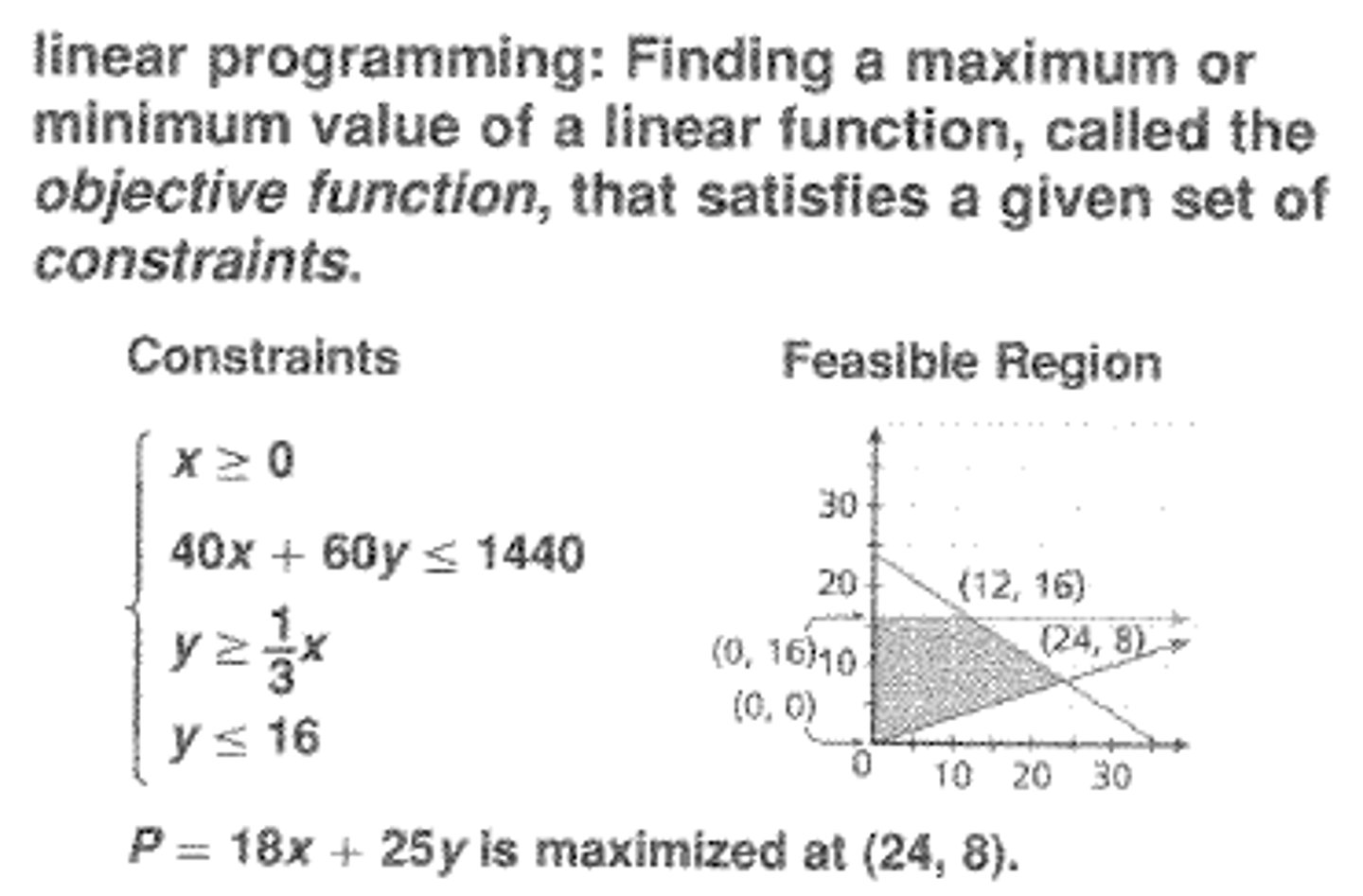
Linear programming
Finds the optimum value of a linear expression calculated based on the value of a set of decision variables (variables subject to a set of contraints)
Scenario Analysis
Predicts future values based on certain potential events
Monte Carlo simulation
Provides a spectrum of thousands of possible outcomes. Considers the many variables involved and the range of potential values for each variable
Text analysis
Process for extracting value from large quantities of unstructured text data
Video analysis
Process of obtaining information or insights from video footage
Cloud Computing
Computing environment in which software and storage are provided as an Internet service and accessed with a Web browser
Benefits of public cloud computing
Reduced costs, flexible computing capacity, and increased redundancy in the event of disaster
Issues with public cloud computing
Complex pricing arrangements, wide variations in performance over time, inadequate data security, and vendor lock-in
Public Cloud Computing
A service provider owns and manages the infrastructure with cloud user organizations (tenants) accessing slices of shared hardware resources via the Internet
Private cloud computing environment
Single tenant cloud, organizations often implement due to concerns that their data will not be secure in a public cloud
Hybrid Cloud Computing
Composed of both private and public clouds integrated through a private network. Organizations typically use the public cloud to run applications w/ less sensitive security requirements but run more critical applications on the private cloud
Business benefits of IoT
1. Reduce costs to achieve a competitive advantage
2. Deepen the organization's understanding of consumer preferences and behaviors
3. Improve customer service and experience
4. Improve workplace safety
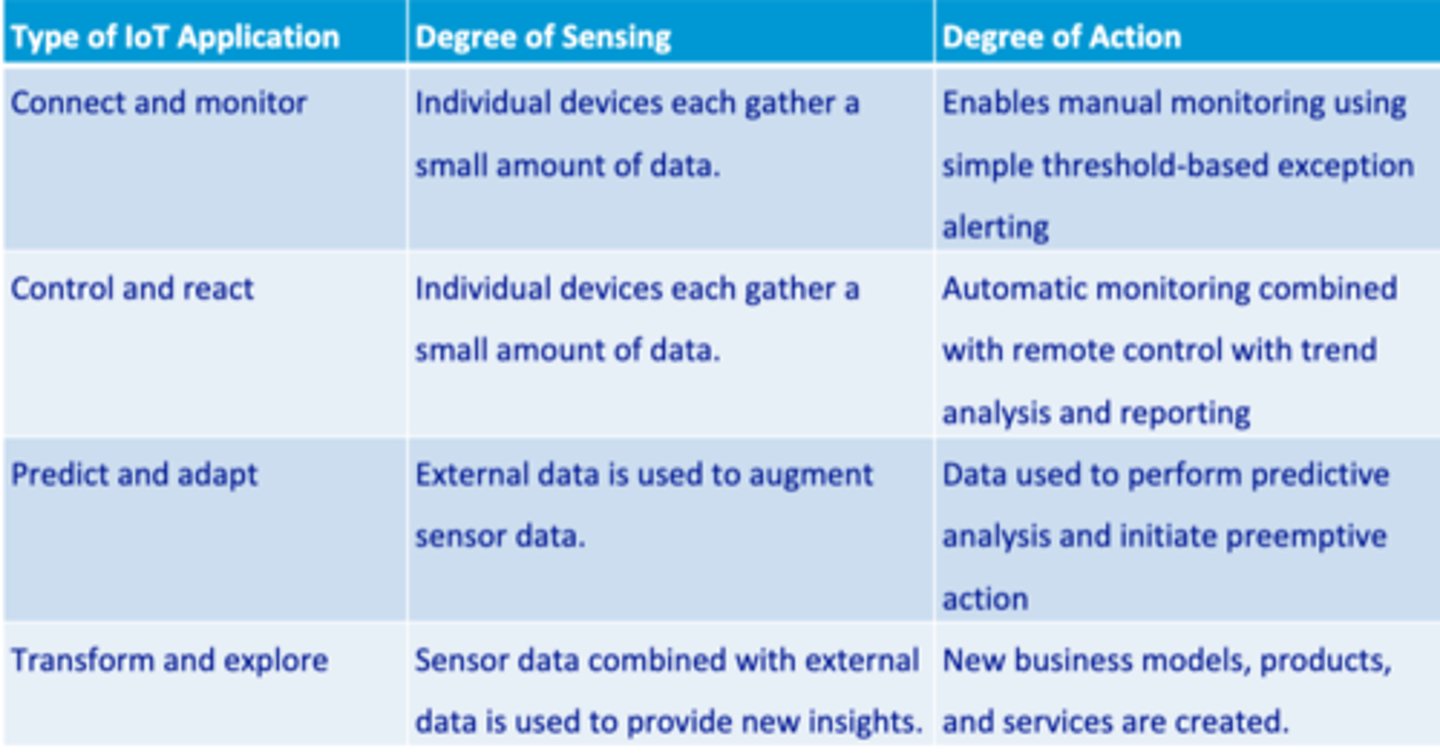
Types of IoT applications
1. Connect and monitor
2. Control and react
3. Predict and adapt
4. Transform and explore
Potential issues with Iot Applications
Many issues with the receipt and usability of sensor data, and security is a very major issue
E-commerce
Conducting business activities electronically over computer networks
Business-to-Business (B2B) E-commerce
A subset of e-commerce in which all the participants are organizations. Useful for connecting business partners in a virtual supply chain to cut resupply times and reduce costs
Business-to-Consumer (B2C) E-Commerce
A form of e-commerce in which customers deal directly with an organization and avoid intermediaries. Steady growth with cheaper goods and services online.
Consumer-to-Consumer (C2C) E-Commerce
Involves electronic transactions b/w consumers facilitated by a third party (eBay, Etsy, ...). Sales must not violate the rules of various county, state, and country legal jurisdictions
E-Government
Use of information and communications technology to: simplify information sharing, speed formerly paper-based processes, and improve relationships b/w citizens & government
Government-to-consumer (G2C)
refers to the electronic commerce activities performed between a government and its citizens or consumers including paying taxes, registering vehicles, providing information and services, and so on.
Government-to-business (G2B) e-commerce
occurs when a government entity sells products and services to businesses
Government-to-government (G2G) e-commerce
e-commerce activities within a nation's government (can also refer to e-commerce activities between 2 or more nations' governments)
Mobile commerce (m-commerce)
electronic commerce transactions that are conducted with a mobile device
Advantages of E/M - Commerce
Conversion to an e- or m-commerce system enables organizations to:
- Reach new customers
- Reduce costs
- Speed the flow of goods and information
- Increase the accuracy of orders
- Improve customer service
How to attract customers to e-commerce
- Obtain and register a domain name
- Make your site search-engine friendly
Authentication technologies
Used by many organizations to confirm the identity of a user requesting access
Certificate authority (CA)
Trusted third-party organization or company that issues digital certificates