Info Systems Final
1/203
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
204 Terms
Managers can help their organizations gain _____ through cost leadership, differentiation, or focus.
technology infrastructure
information systems expertise
a set of procedures
a competitive advantage
a competitive advantage
Franklin is responsible for helping to ensure that his organization meets the Payment Card Industry Data Security Standard when handling customers' credit card information. Franklin maintains information systems with influence within the _____.
workgroup sphere
personal sphere
enterprise sphere
interorganizational sphere
enterprise sphere
Autumn develops a strategic plan that will allow her organization to take advantage of opportunities and trends by _____.
reacting passively
being proactive
staying focused on costs
remaining in state of flux
being proactive
When entering a customer order, Josie ensures that the desired end result is achieved and any problems are reported to the correct person by following a(n) _____.
procedure
EDI standard
supply chain
process
procedure
Jude, a senior executive, and the managers who report to him must make many decisions for their business units. To assist them with
this, they rely on strategic planning to provide _____.
new and loyal customers
a reactive approach to market changes
a framework and a clearly defined direction
the human and material resources they need
a framework and a clearly defined direction
Which type of information system do organizations use to define structured interactions among employees or between the organizational
and external customers, suppliers, or business partners?
workgroup information system
interorganizational information system
enterprise information system
personal information system
enterprise information system
Which of the following components forms the foundation of every computer-based information system and includes resources such as
hardware, software, and data center facilities?
people
processes
structure
technology infrastructure
technology infrastructure
Collaboration between two or more organizations that lowers costs and reduces manual effort among employees is enabled by a(n) _____.
interorganizational information system
workgroup information system
personal information system
enterprise information system
interorganizational information system
A high-level IS manager has his firm utilize sophisticated information systems to digitally design its products so that design defects can be detected and removed early in the process, reducing development cost. What business strategy does this represent?
focus
differentiation
cost leadership
high standards
cost leadership
A senior IS manager implements a vendor-managed inventory system that reduces both the administrative costs of managing inventory and inventory holding costs. What business strategy does this represent?
focus
high standards
cost leadership
differentiation
cost leadership
Fabiola's IS management team is formulating their IS strategic plan. Fabiola reminds them that they must consider __.
limiting communication with lower-level managers
corporate strategy and business unit strategies
the IS organization isolated from the rest of the organization
previous but not future IT investments
corporate strategy and business unit strategies
An IS manager recommends that his organization invest in improving its customer information system so as to more clearly define the target market and improve service to that market. What business strategy does this represent?
focus
high standards
differentiation
cost leadership
focus
Janelle is helping create a strategic plan for her organization. What should she anticipate will be stable--that is, change little, if at all--over time?
economic growth
suppliers
importance of planning
competitiors
importance of planning
Companies that share data with other organizations in a manner that conforms to rigidly defined industry standards are using a type of ________.
workgroup information system
interorganizational information system
personal information system
enterprise information system
interorganizational information system
What does Doug, an IS manager, consult when he needs to identify competencies for his organization to invest in?
information system strategic plan
high-demand certifications list
procedural certifications list
enterprise information system
information system strategic plan
In terms of information systems, a collaboration tool that helps a team communicate, organize, plan, schedule, track, and delegate jobs would be an example of _________.
a personal information system
an organizational complement
a workgroup information system
an enterprise information system
a workgroup information system
To improve his score on a security self-assessment, Saul set up his laptop so that the first thing he must do when he turns it on is _____.
run a file backup procedure.
log in to his employer's VPN.
install new software updates.
enter a strong security password.
enter a strong security password.
Assessing damage following a computer incident, investigating the unauthorized disclosure of corporate confidential data, and confirming or evaluating the impact of industrial espionage are tasks most appropriate
for _____.
computer forensicsthe CIA security triadmanaged security service providersa security dashboard
computer forensics
A data breach at your business resulted in the loss of some customer
data. Several angry customers have filed charges. What is a
recommended course of action to prepare for future events?
meet with your lawyers to prepare to counter-sue the customers
activate the forensics analysis team and prepare documentation
release a media statement denying the customer allegations and asserting
that all customer data is safe
settle with the customers, however much it may cost
activate the forensics analysis team and prepare documentation
Samantha owns a small business that handles a lot of sensitive customer
data and would be devastated by a data breach. Her IS department,
which consists of one part-time consultant named Nikki, is overwhelmed
by the number of alerts and false alarms constantly issued by her
security-monitoring systems and expresses concerns about their data
security. What should Samantha do about this?
research different security software options
ask Nikki to disable the alerts and alarms
change her passwords more often
consider a managed security service provider
consider a managed security service provider
Assume your organization is experiencing an intruder attack. You have an intrusion detection system (IDS) set up. Which of the following events occurs first?
The network router sends traffic to the firewall as well as to the IDS.
Messages from the IDS are routed to the network security team.
The network security team decides to block traffic from that IP address.
The IDS warns the firewall of suspicious traffic.
The network router sends traffic to the firewall as well as to the IDS.
You work for a company that is growing. Originally, all the users in all
departments had access to all the data in the database. It is considered a
security risk. What is an appropriate action to reduce the risk?
Assign roles and privileges to users so that only job-relevant data is
accessible to the user.
Tweak the firewall parameters so that outgoing traffic can be better
controlled.
Install and provide stronger anti-virus software on the users' computers.
Install a two-step login procedure, where the user has to key in additional
information for logging in.
Assign roles and privileges to users so that only job-relevant data is accessible to the user.
You wish to use your personal laptop computer at work, but the IT
department folks will not allow this. The likely reason is that ______.
your productivity could not be accurately measured.
you will use your laptop for non-work-related activities.
your non-work-related use of the laptop could increase vulnerability.
your activities could not be monitored.
your non-work-related use of the laptop could increase vulnerability.
Kenneth is assisting with step 7 of his organization's security risk
assessment. He and his team compare the risks of potential security
breaches against the estimated costs of preventing them from happening.
Why is this an important step?
Data availability requires implementing products, services, policies, and procedures to ensure that data are accessible.
No amount of resources can guarantee a perfect security system, so one must balance risks with prevention costs.
Taking action to prevent cyberattacks, such as installing protective software, makes them much less likely to occur.
Periodic security audits are needed to ensure that individuals are following established policies.
No amount of resources can guarantee a perfect security system, so one must balance risks with prevention costs.
Which of the following is considered the most likely source of cyberattacks, based on a poll of global executives, information security
managers, and IT leaders?
careless insiders
lone wolf attackers
MSSPs
cyberterrorists
careless insiders
Your business has a web server that has suddenly become unresponsive. When you study the server's logs there are a huge number of requests from what appear to be legitimate computers. The problem is likely because of _____.
a CAPTCHA issue
a logic bomb
a distributed denial-of-service attack
too many Spam emails
a distributed denial-of-service attack
Ethical business practices _____.
often raise an organization's priority with suppliers and other business partners
create a negative discrepancy between employee and organizational values
increase employee turnover when workers feel their actions are overly restricted
are usually more expensive for a business over the long term than unethical ones
often raise an organization's priority with suppliers and other business partners
How do fair information practices in the United States and the European
Union differ?
Unlike the EU, the U.S. has no single, overarching national data privacypolicy.Unlike the U.S., the EU has implemented numerous data privacy laws.Unlike the EU, the U.S. addresses potential abuses by private industry but notby the government.Unlike the U.S., the EU divides their data privacy laws into three ares:financial, health related, and child specific.
Unlike the EU, the U.S. has no single, overarching national data privacy policy.
Using the values held by his organization, Don has defined an ethical
approach for dealing with the needs of his team members and their
customers that he has implemented within his department. His team
members know what is expected of them, and their customers know what to
expect from the organization. The primary benefit of this approach for Don's
department is _____.
fostering good business practices
avoiding publicity
protection from legal action
consistent operation
consistent operation
Anne and Jordan have two preteen sons and they're concerned about what their kids might see and share on the Internet. They should probably invest in _______.
filtering software
privacy screening
security passwords
Internet licensing
filtering software
It is not against the law for Ethel to possess an automatic weapon, but she believes possessing one is the wrong thing to do. For Ethel, possessing an automatic weapon is _____.
illegal and unethical
legal but unethical
legal and ethical
illegal but ethical
legal but unethical
In the United States, legislation that protects people from data privacy abuses by corporations _____.
requires firms to respond within one month to data requests from individuals
was passed only recently
is almost nonexistent
is quite similar to the EU's General Data Protection Regulation
is almost nonexistent
Because Marigold wants to join CompTIA (the Computer Technology Industry Association), she agrees to adhere to this organization's professional code of ethics. This means that she _____.
is prioritizing CompTIA's principles of right and wrong over her own
believes CompTIA has provided answers to every ethical dilemma she might face
has promised to behave in a way that CompTIA has defined as desirable
wants to rely on CompTIA's guidelines primarily to avoid violating the law
has promised to behave in a way that CompTIA has defined as desirable
Felicity, who works at a bank, opens multiple credit card accounts for
customers without their authorization in order to improve her customer sales,
and thus her apparent job performance. This behavior is explicitly forbidden
by bank policies and the instructions her manager gave her. Which
statement is true in this situation?
This situation demonstrates how bad organizational ethics can lead to bad
business results.
The principle called respondeat superior, meaning "let the master answer,"
does not apply.
The bank can be held responsible for Felicity's behavior despite its ethical
policies.
The bank cannot be held responsible for Felicity's actions since they were
contrary to bank policies.
The bank can be held responsible for Felicity's behavior despite its ethical policies.
Which of the following is a defining feature of a safety-critical software system?
performs quickly and efficiently
minimum system downtime
defects could result in human injury
meets users' needs completely
defects could result in human injury
JoAnn is a developer hired to help code the software that will control a
nuclear power plant reactor. Compared with her previous project, which
involved software for sophisticated video games for PCs and home game
consoles, JoAnn's current project will most likely _____.
have a much larger budget and a much shorter development schedule
have a much smaller budget and a much longer development schedule
have a much larger budget and a much longer development schedule
have a much smaller budget and a much shorter development schedule
have a much larger budget and a much longer development schedule
A _____ is a conditional statement that links conditions to actions or outcomes.
THEN-IF statement
case
simulation
rule
rule
The _____ stores all relevant information, data, rules, cases, and relationships that an expert system uses.
knowledge base
data warehouse
user interface
inference engine
knowledge base
How does an artificial neural network make a decision and produce its final result?
It matches the current data to past cases and attempts to reuse or modify previous decisions.
It quantitatively evaluates several possible choices using a fitness function.
It identifies rules linking conditions from the data to actions or outcomes.
It compares the values associated with the networked connections through which data is filtered.
It compares the values associated with the networked connections through which data is filtered.
Which of the following statements about unsupervised learning is accurate?
Unsupervised learning requires an unlabeled training data set.
In unsupervised learning, tests have formal, predetermined correct answers.
In unsupervised learning, each piece of data must be associated with a name.
Unsupervised learning is like a child learning a game after being informed of the rules.
Unsupervised learning requires an unlabeled training data set.
What overall strategy is used to train artificial neural network programs?
unsupervised learning
forward chaining
supervised learning
backward chaining
supervised learning
An artificial neural network uses the feedback it receives to _____.
select the option with the lowest weight
assign the most "points" to the choice with the least feedback
generate new data
weight its connections
weight its connections
_____ systems can superimpose images and data over a person's view of the real world.
Augmented reality
Forward chaining
Immersive virtual reality
Neural network
Augmented reality
Since the early 1800s, automation has often aroused workers' fears about _____.
job loss
minimum wages
workplace hazards
unions
job loss
Thomas and Emily are discussing the effect of AI on future employment. Emily correctly points out that _____.
until the introduction of AI, workers welcomed automation as a way to increase safety
historically, technology has seldom created labor that is chapter or faster than human labor
technology often replaces high-paying jobs but creates more low-paying jobs
the introduction of new technology has always resulted in the creation of more jobs than were lost
the introduction of new technology has always resulted in the creation of more jobs than were lost
A key difference between virtual reality and augmented reality is that augmented reality _____.
is not yet used in the medical field
can make objects seem to appear in your current surroundings
allows you to "walk through" different scenes from your current location
is much a newer technology
can make objects seem to appear in your current surroundings
The constraint that all foreign keys must have either null values or the value of a primary key in another table is referred to as
_____________________.
foreign key value rulereferential integrity rulenull value rulemob ruleentity integrity rule
referential integrity rule
What is each row in a relational database table called?
relation
entity
anomaly
attribute
tuple
tuple
Functional dependencies are similar to ________ keys.
secondary
foreign
primary
useful
foreign
The relational data model portrays data as being stored in ________________.
tables
objects
heirarchies
files
tables
Which of the following attributes in the Cash Receipts table would most likely be a foreign key? For our non-accounting friends, the Cash Receipts table represents payments received from customers.
customer name
customer check number
customer number
cash receipt date
cash receipt number
customer number
A ________ relationship exists when three entities are associated.
binary
tertiary
ternary
unary
ternary
________ refers to the maximum number of times an instance of one entity can be associated with an instance in the related entity.
Business rules
Cardinality
Data dictionary
Modality
Cardinality
A ________ relationship exists when two entities are associated.
solitary
unary
ternary
binary
binary
Two vertical lines represent the ________ cardinality symbol.
mandatory single
optional many
mandatory many
optional single
mandatory single
Microsoft Access uses ________ to conduct queries.
RFID
TPS
QBE
ETL
QBE
A circle with a "chicken leg" to the entity represents the ________ cardinality symbol.
mandatory many
optional many
optional single
mandatory single
optional many
A ________ relationship exists when an association is maintained within a single entity.
ternary
binary
unary
solitary
unary
How the user conceptually organizes and understands the data is referred to as the ________________.
logical view
data organization view
data model view
physical view
logical view
Which of the following is an individual user's view of the database?
internal-level schema
conceptual-level schema
logical-level schema
external-level schema
external-level schema
Which of the following is the software that runs the database system?
DQL
DBMS
DDL
DML
DBMS
The constraint that all primary keys must have nonnull data values is referred to as the ____________________.
entity integrity rule
normalization rule
referential integrity rule
relational data model rule
personal integrity rule
entity integrity rule
________ is the most popular query language used for interacting with a database.
RFID
ETL
TPS
SQL
SQL
Which of the following attributes would most likely be a primary key?
supplier number
supplier phone number
supplier name
supplier account balance
supplier zip code
supplier number
Which of the following would managers most likely use to retreive information about sales during the month of October?
DML
DSL
DHL
DQL
DDP
DDL
DQL
What is Zim'z favorite type of visualization?
bar chart
map
heat map
pie chart
scatterplot
tree map
map
Instead of a pie chart, Zim says that most of the time you can draw this type of chart instead
bar chart
scatterplot
tree map
heat map
bar chart
What is the difference between a dashboard and a story in Tableau.
there is no real difference; both terms can be unsed interchanably.
A story is for sharing an explcit message; a dashboard gives an impartial window into the organization.
A dashboard is made up of linking several stories together.
A dashboard is for sharing an explcit message; a story gives an impartial window into the organization.
A story is for sharing an explcit message; a dashboard gives an impartial window into the organization
What is Zim'z LEAST favorite type of visualization?
bar chart
tree map
heat map
scatterplot
pie chart
map
pie chart
This type of visualization is good for looking for relationships between data
bar chart
tree map
heat map
scatterplot
scatterplot
What type of data is associated with this symbol? # with a circle around it
Numeric
String
Geographic
Date
Geographic
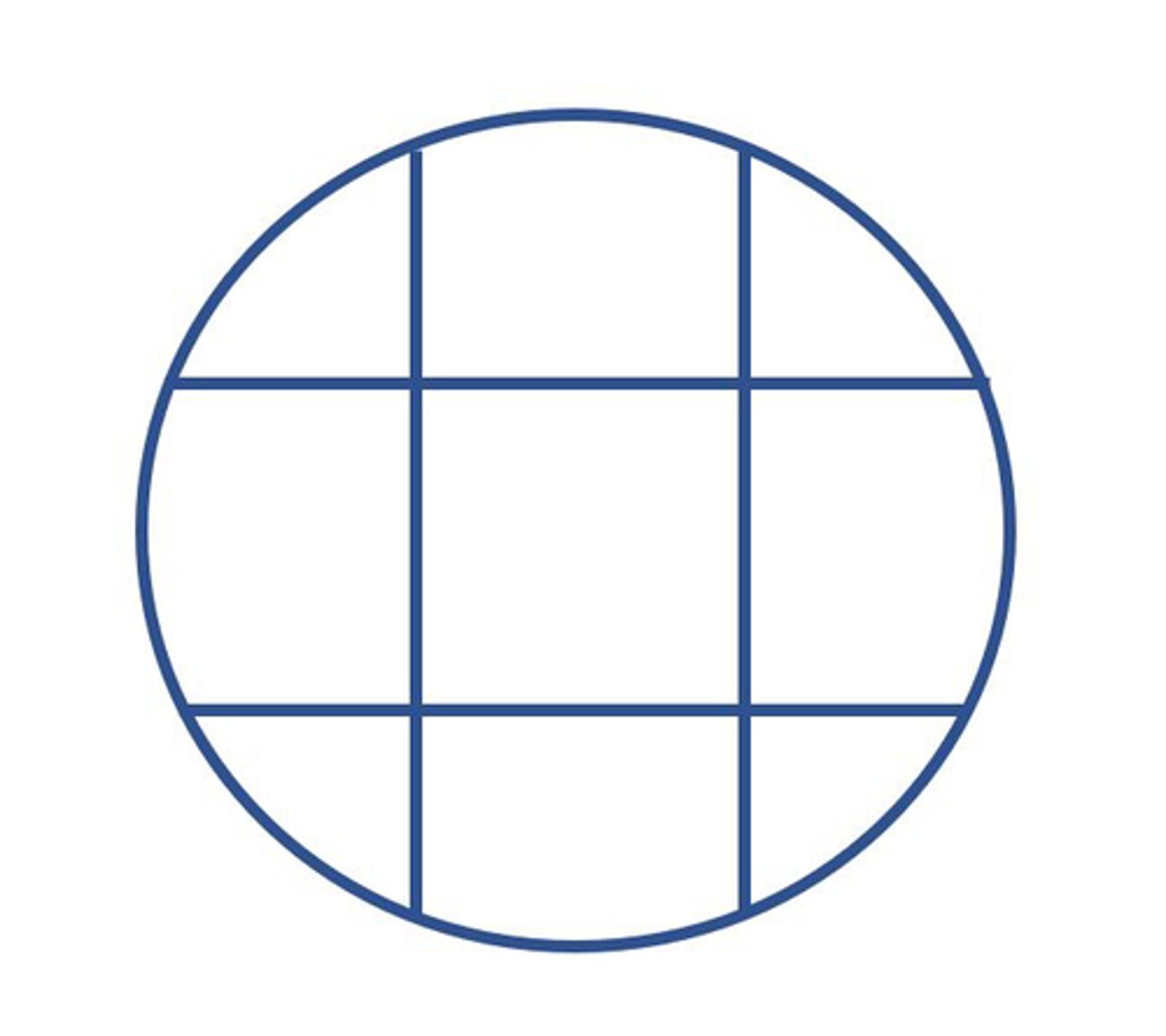
What type of operation do we do to make a tall, narrow dataset?
join
select
split
pivot
pivot
What type of data is associated with this symbol? #
String
Date
Geographic
Numeric
Numeric
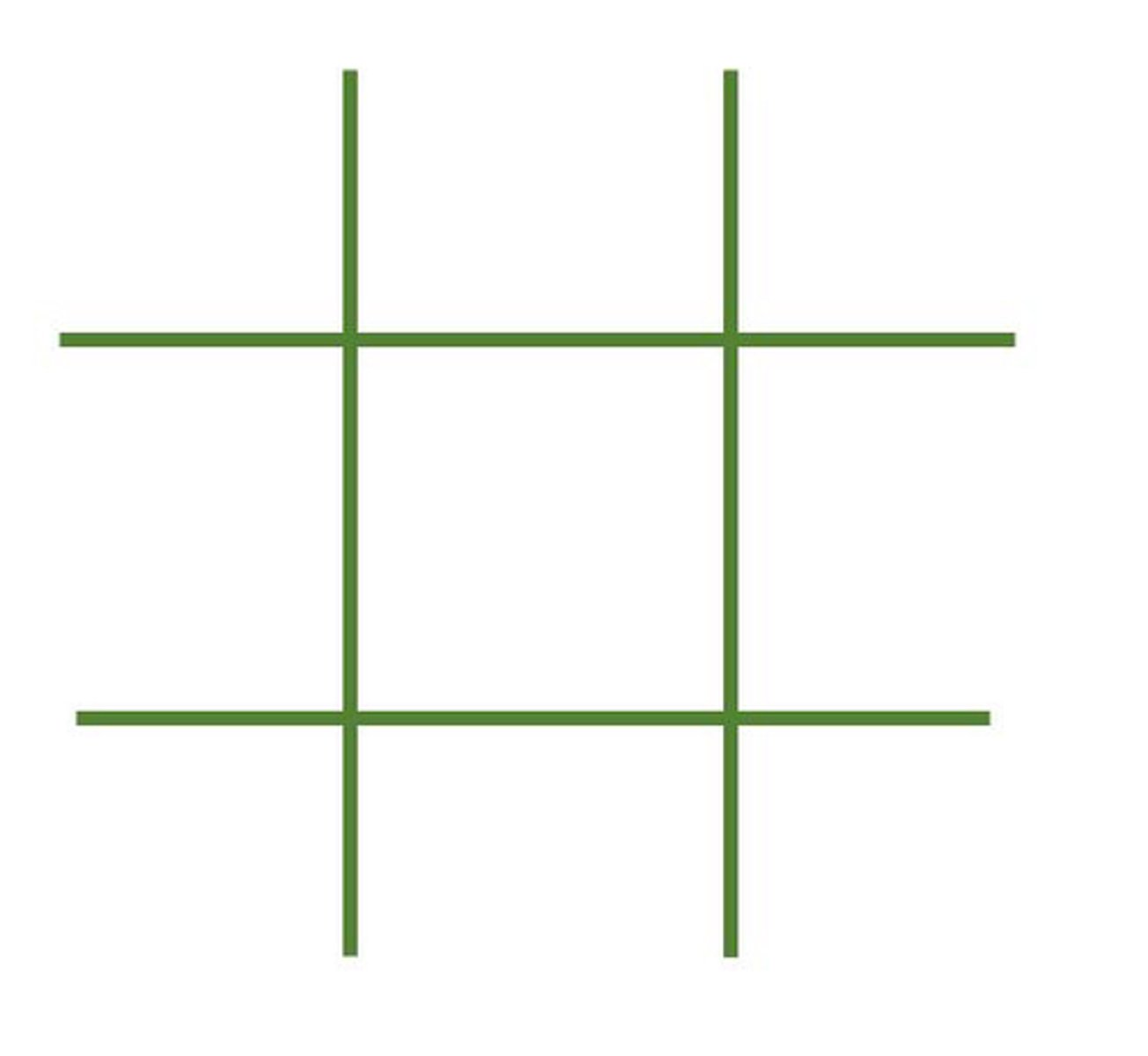
I made a very big deal about this in the audio. When do you need to be careful when creating a new variable?
When creating additive terms (i.e. adding variables together)
When creating interactions (i.e. multiplying variables together)
When creating delta terms (i.e. subtracting variables)
When creating ratios (i.e. dividing variables)
When creating ratios (i.e. dividing variables)
In Tableau, when you place a dimension on the rows shelf, it
comes into the view as itself.
adds a trend line to the viz.
comes into the view as an aggregate.
takes on as many different colors as it has unique values.
comes into the view as itself.
In the first PowerPoint, who is the guy that created four statistically equivalent datasets, but all four had radically different properties when examined visually?
Mintzberg
Zimmer
Deming
Anscombe
Anscombe
In the PowerPoints, I gave several examples demonstrating how powerful color can be in a visualization. What caveat did I present about using color?
Avoid using a red to green color scale because color blindness
Only use 5 colors when presenting continuous data
Always use at least two different colors when incorporating color into a visualization
Use a color ramp (where the color fades from one to another) when presenting discrete data
Avoid using a red to green color scale because color blindness
Which of the following is a visualization best practice?
avoid System 1 thinking
leverage System 1 thinking
leverage System 2 thinking
avoid System 2 thinking
leverage System 1 thinking
According to what Zim talks about in the PowerPoint audio, ________________ is the most common type of visualizations you'll see in Tableau
Heat maps
Histograms
Bar charts
Line graphs
Scatterplots
Bar charts
A green pills means the data is ________________.
a dimension.
continuous
discrete
categorical
continuous
What is a limitation of a filled map?
Only one measure can be used to fill the map.
It disproportionately draws the viewer's attention to larger countries (or states).
Small regions do not show up very well.
Limitation? Haven't you been listening to Zim? Maps are awesome because they have no limitations!
Only one measure can be used to fill the map.
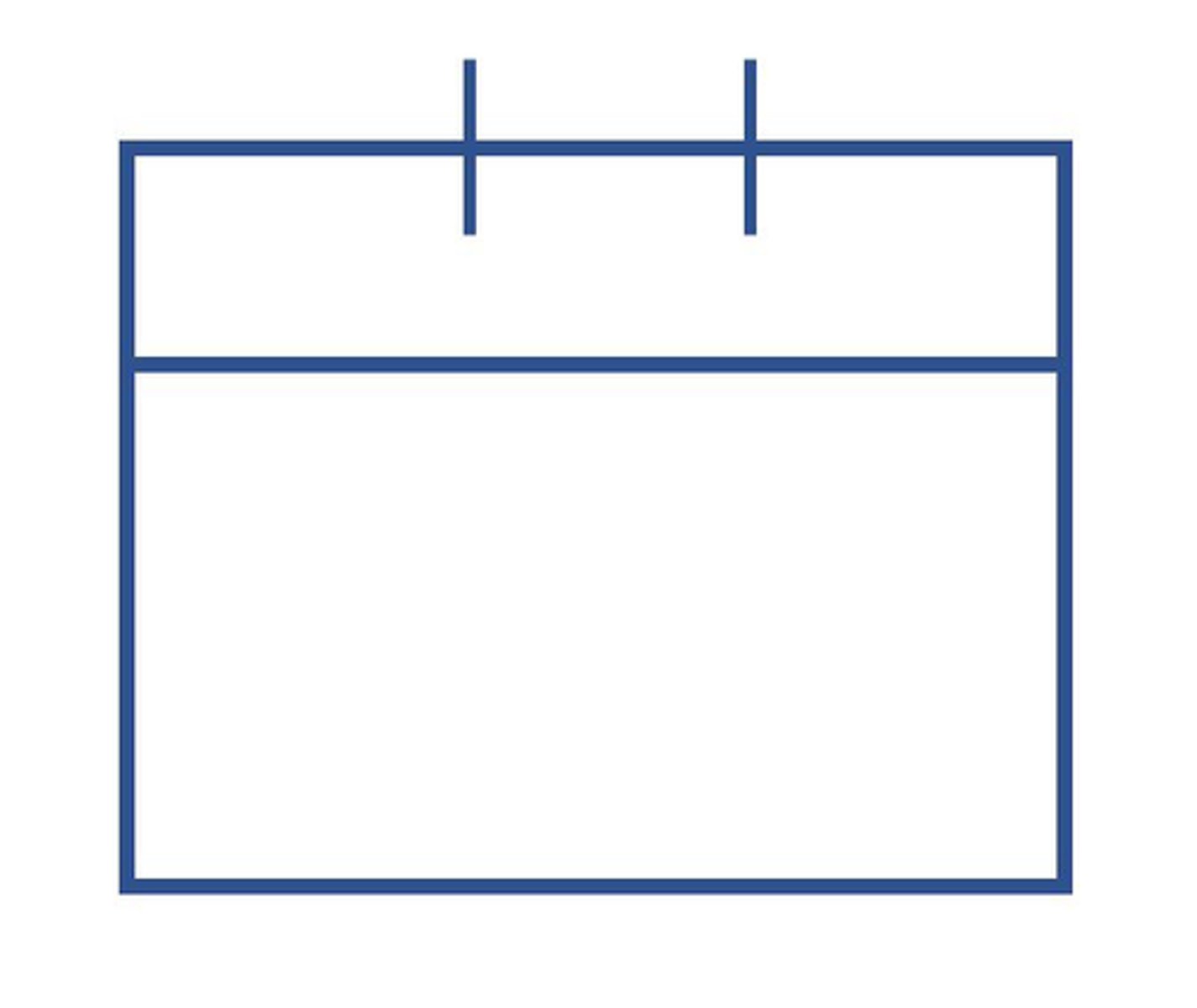
In the picture below, what is the section of the screen that is highlighted called? Where the data is to the left.
Data Frame
Menus & Toolbars
Data Window
Shelves & Cards
Data Window
What type of data is associated with this symbol? Looks like a calendar
Numeric
String
Date
Geographic
Date
An inner join _______________ null values; an outer join __________________ null values once the query runs.
minimizes, minimizes
maximizes, maximizes
minimizes, maximizes
maximizes, minimizes
minimizes, maximizes
The most common type of join you'll see is the ______________ join.
right
inner
left
outer
inner
Typically I want this type of dataset
a tall narrow dataset
a short narrow dataset
a tall wide dataset
a short wide dataset
a tall narrow dataset
In the picture below, what is the section of the screen that is highlighted called? Top where columns and rows are.
Shelves & Cards
Menus & Toolbars
Drawing Pane
Data Window
Shelves & Cards
What type of data is associated with this symbol? Abc
Numeric
String
Date
Geographic
String

All of the following are problems with pie charts except
Pie charts are poor ways to present percentile data
It is hard to compare angles of a pie chart against each other
They are ineffective when there are more than 5 groups to present
They do not show the count (or frequency) of data very well.
Pie charts are poor ways to present percentile data
You can also call a discrete variable a ___________________.
continuous dimension
ordinal variable
dimension
measure
dimension
This type of chart is good for showing relative proportions or proportions of a whole
scatterplot
tree map
heat map
bar chart
tree map
Pie charts are...
...to be avoided
...a good way to present qualitative data
...a good way to present quantitative data
...are usually OK to use, but should never be used when trying to present percentile data
to be avoided
How can I quickly tell if something is a table calculation?
It says "TC" next to the variable
It has a delta symbol (a triangle) next to it in the pill
You click on the variable, opening the dialogue box and look for the line "aggregate measures" to have a check mark next to it
if you mouseover (place your cursor on it but DO NOT click) a box appears that says "Table Calculation"
It has a delta symbol (a triangle) next to it in the pill
What function did I talk about in the PowerPoints that would have been helpful to know when you were working on the Access project?
DATEPART
DATETIME
DATEFROMPARTS
GETDATE
DATEDIFF
DATEADD
DATEDIFF
Why do we use tools like Tableau?
to help us make better decisions
to impress our bosses with our technological skills
to be able to put it on our resume so as to get a better job
to turn lots of numbers into easy to read pictures
to help us make better decisions
A blue pills means the data is _____________.
a measure
continuous
ordinal
discrete
discrete
According to Tableau, you should use _______ colors (at most) in your visualization.
6
8
5
7
8
What is the first step in understanding your data?
examine it visually
calculate the means of all numeric data
calculate summary statistics on all your fields
clean up the odd or otherwise weird values
examine it visually
Which of the following statements is correct?
A label is tied to continuous data
An axis is tied to a measure
A label is tied to a measure
An axis is tied to a dimension
An axis is tied to a measure
Corporate strategy, business unit strategies, innovative thinking, and technology innovations are all _____.
drivers that set information system organizational strategy
spheres of influence for types of information systems
elements of the value chain
components of Leavitt's Diamond
drivers that set information system organizational strategy