CompTIA Security+ (SY0-701)
1/625
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
626 Terms
Control Categories & Control Types
Control Categories: Technical Control
Security Controls that are implemented using some type of technical system. (Firewalls, Antiviruses, System Logs, etc)
Control Categories: Managerial Controls
Overseeing a set of policies that explain the best way to manage their data, computer, and systems. If you are creating a series of security policies or a standard operating procedure, your managerial controls would fall under such series. Your are basically the manager of the security framework within an organization. (On/Offboarding policy, Compliance Policies, Separation Of Duties)
Control Categories: Operational Controls
These controls are implemented by individuals instead of systems. (Guard Shacks, Reception Desks, Property Patrols, Security Policy Training)
Control Category: Physical
A control category that limit a person’s physical access to a building, a room, or a device. (Door Locks, Fencing, Warning Signs)
Control Type: Preventive
A control type that limits someone's access to a certain resource. (Firewalls, On-Boarding Policy, Guard Shack, Door Lock)
Control Type: Deterrent
A control type that doesn’t prevent someone from accessing a resource, however it discourages a person from launching an attack. (Splash Screens, Demotions, Reception Desk, Warning Signs)
Control Type: Detective
A control type that can identify and log an intrusion attempt. (System Logs, Reviewing Log In Reports, Property Patrol, Motion Detectors)
Control Type: Corrective
A control type that is applied to after an event has been detected. Sometimes able to reverse the impact of an event, or be able to continue operating your business with minimum downtime. (Backup Recovery, Reporting Issues, Authority Contact, Fire Extinguisher)
Control Type: Compensating
A control type where if you don’t have the resources to reverse a security event which would allow you to have a different set of means to control the issue as a temporary solution. Only if your existing controls aren’t sufficient. (Firewalls/Blocked Access instead of a patch, Separation Of Duties, Multiple Security Staff required after an incident, Power Generator after an outage)
Control Type: Directive
A control type that is a relatively weak security control where you are directing someone to do something more secure than less secure. (file storage policies for encrypting valuable information, Compliance Policies, Security Policy Training, “Authorized Personnel Only” Sign)
CIA / AIC Triad
Confidentiality, Integrity, Availability
Confidentiality (CIA Triad)
Certain information should only be known to certain people, this prevents unauthorized information disclosure. Usually done through encryption, access controls, and 2FA.
Integrity (CIA Triad)
We want to ensure that the recipient is receiving exactly what was sent from the sender. Messages can’t be modified without detection. Typically done through hashing.
Availability (CIA Triad)
Systems and Networks must be up and running at all times even while we are implementing updates. Done through a multitude of ways (fault tolerance, high availability, load balancers, etc)
Non-Repudation
Ensures that a user cannot deny having performed a specific action—like sending data, logging in, or approving a transaction. Proof that data came from the stated sender and has not been changed (Proof of Origin/Identity through digital signatures).
Digital Signature
A cryptographic method used to verify the authenticity and integrity of a message, file, or digital document, proving the sender’s identity and preventing tampering.
AAA Framework
A security model that stands for Authentication, Authorization, and Accounting—used to control user access, verify identity, assign permissions, and track activity. Identification is usually apart of it, but technically not attached to the acronym.
CA
[Certificate Authority] An entity that issues and digitally signs public-key certificates for users or devices.
CRL
[Certificate Revocation List] A file containing a list of the revoked certificates. This list is maintained by the associated certificate authority
CSR
[Certificate Signing Request] Sent with the public key to the certificate authority in order to be signed. Once the certificate information has been verified, the CA will digitally sign the public key certificate.
OCSP
[Online Certificate Status Protocol] OCSP is a protocol used by the browser to check the revocation status of a certification.
Digital Certificate
An electronic document issued by a Certificate Authority (CA) that verifies the identity of an entity and contains its public key, enabling secure encrypted communication.
Certificate-Based Authentication
A method that uses digital certificates to verify a user’s or device’s identity, enabling secure access without relying on passwords.
Authorization Model
A framework or method that defines how permissions and access rights are assigned and enforced for users and resources in a system.
Gap Analysis
A process that compares current security controls or performance against desired standards or requirements to identify missing elements or weaknesses.
Zero Trust
A security model that assumes no user or device—inside or outside the network—is trusted by default; every access request must be verified continuously before granting permission.
Zero Trust: Control Plane
The overseer who manages all of the actions that are occurring in the data plane. This may be configuring rules or policies, or possibly setting up a forward policy. Anytime you're looking at a firewall rule, routing table, or understanding network address should be handled, you're configuring on the control plane.
Zero Trust: Data Plane
The data plane is the part of the device that is actually performing the security process; this could be a firewall, switch, or router that is processing frames, packets, and network data.
Adaptive Identity
We are examining the identity of an individual, and then applying security controls of what the user tells us along with the other resources.
Attack Surface
All the points in a system or network where an attacker can try to enter or extract data.
Threat Scope Reduction
Decreasing the number of possible entry points to the network
Policy Driven Access Control
An access control method where permissions are granted based on predefined policies that evaluate user attributes, context, and rules.
Policy Enforcement Point (PEP):
The component that enforces access control decisions by allowing or denying user requests based on security policies.
Policy Decision Point (PDP)
The system component that evaluates access requests against policies and makes the authorization decision. Instructs the PEP to allow/disallow traffic.
Policy Administrator (PA):
The entity or system responsible for creating, managing, and updating security policies used for access control decisions.
Honeypots
Decoy systems or resources set up to attract attackers, detect intrusions, and gather information about attack methods.
Honeynets
Networks of interconnected honeypots designed to trap and analyze attackers on a larger scale
Honeyfiles
Fake files planted to lure attackers and detect unauthorized access.
Honeytokens
Decoy data or credentials that alert defenders when accessed or used by attackers.
Change Management
A structured approach to planning, implementing, and monitoring changes in an organization’s systems or processes to minimize risks and ensure smooth transitions.
Change Management: Formal Process
A defined sequence of steps—including request, approval, planning, implementation, and review—to control and document changes in IT systems or business processes. Documenting scope, time, purpose, risk, gathering approval, etc.
Change Management: Owner & Stakeholders
individual or group responsible for overseeing and managing the change process, ensuring the change meets their requirements, coordinating testing, and representing stakeholders impacted by the change.
Change Management: Backups/Version Control
Key components of change management that ensure failed changes can be safely reversed (backout plan) and previous system states or code versions can be restored accurately (version control).
Impact Analysis
The process of identifying and evaluating the potential effects and consequences a proposed change may have on systems, processes, and stakeholders
Sandbox Testing Environment
A isolated, controlled setting where software or changes can be safely tested without affecting the live production system. Can also be an area where malware or a vulnerability is isolated in order to be analyzed, tested, and erradicated.
Allow List
A security mechanism that permits access only to pre-approved, trusted entities—such as IP addresses, applications, or users—while blocking everything else by default.
Deny List
A security mechanism that blocks specific, known untrusted entities—such as IP addresses, applications, or users—while allowing all others by default.
Public Key Infrastructure (PKI)
The policies/procedures whether it be hardware/software that is responsible for creating, distributing, managing, storing, and revoking processes associated with digital certificates. Also refers to the binding of public keys to people or devices, usually in accordance with a certificate authority. Based on how much you can trust a specific user is truly who they claim to be.
Symmetric Encryption
An encryption method where the same key is used to both encrypt and decrypt data, requiring secure key sharing between parties.
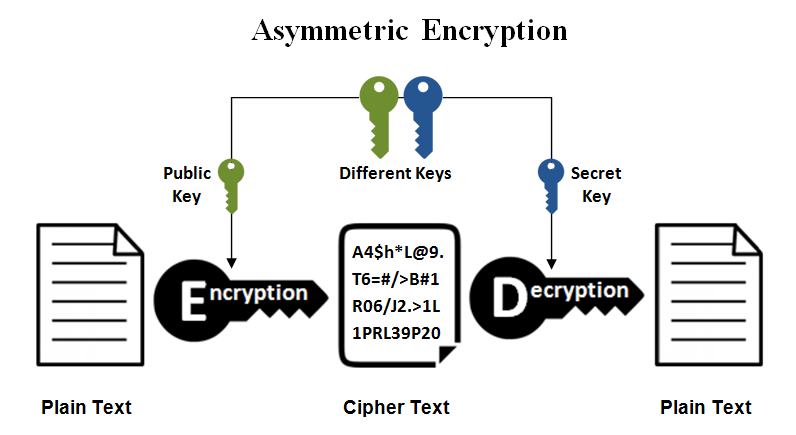
Asymmetric Encryption
An encryption method that uses a pair of keys—one public and one private—where data encrypted with one can only be decrypted with the other, enabling secure key exchange and digital signatures.
Key Escrow
A security arrangement where encryption keys are held by a trusted third party, allowing access to encrypted data if needed for recovery or legal reasons.
Record-Level Encryption
Encrypting individual records within a database, allowing fine-grained security and selective access to specific data entries.
Transparent Encryption
Encryption that occurs automatically at the system or database level without requiring user intervention, securing data at rest seamlessly. Encrypting data at rest.
Transport Encryption
Protecting data as it moves across networks using protocols like TLS/SSL to prevent interception or tampering during transmission. Encrypting data in motion
Key Stretching
A technique that strengthens weak or short cryptographic keys (like passwords) by applying repeated hashing to make brute-force attacks more difficult.
Out-of-Band Key Exchange
The process of sharing cryptographic keys through a separate, secure channel outside the main communication path (e.g., sending a key by phone while using email).
In-Band Key Exchange
The process of exchanging cryptographic keys within the same communication channel used for data transfer, often protected by encryption protocols like TLS.
Session Key
A temporary encryption key used for a single communication session to securely encrypt and decrypt data, then discarded after the session ends.
Key Exchange Algorithm
An cryptographic method used to securely share encryption keys between parties over an insecure channel, enabling encrypted communication (e.g., Diffie-Hellman).
Trusted Platform Module (TPM)
Platform security, ensuring the integrity of the device's hardware and software, enabling secure boot processes, and protecting cryptographic keys used for local data encryption. Burned in during manufacturing, has both persistant and versatile memory. Password protected from brute force attacks.
Hardware Security Module (HSM)
A specialized, highly secure hardware device used in large environments to store and manage cryptographic keys, provide fast cryptographic processing with dedicated hardware (like plug-in cards), and ensure high availability through clustering and redundancies. Meant for high performance, scalability, and key management. These are separate devices!
Obfuscation
The process of deliberately making code or data difficult to understand or interpret to protect it from unauthorized access or reverse engineering.
Tokenization
A type of obfuscation that replaces sensitive data with non-sensitive placeholders (tokens) that have no meaningful value outside the system.
Steganography
A type of obfuscation that conceals data within other harmless-looking files (like images or audio) to hide its existence.
Data Masking
A type of obfuscation that hides or alters data (e.g., showing only last 4 digits of a credit card) to protect sensitive information while maintaining usability.
Hash
A fixed-size output generated by a hash function from input data, used to verify data integrity. Usually used to store passwords in databases.
Collision
When two different inputs produce the same hash output, potentially compromising hash reliability. (MD5)
Salt Hash
A hash combined with a random value (salt) added to the input to prevent attackers from using precomputed hash tables.
Rainbow Tables
Precomputed tables of hashed values used by attackers to reverse common hashes and crack passwords faster,
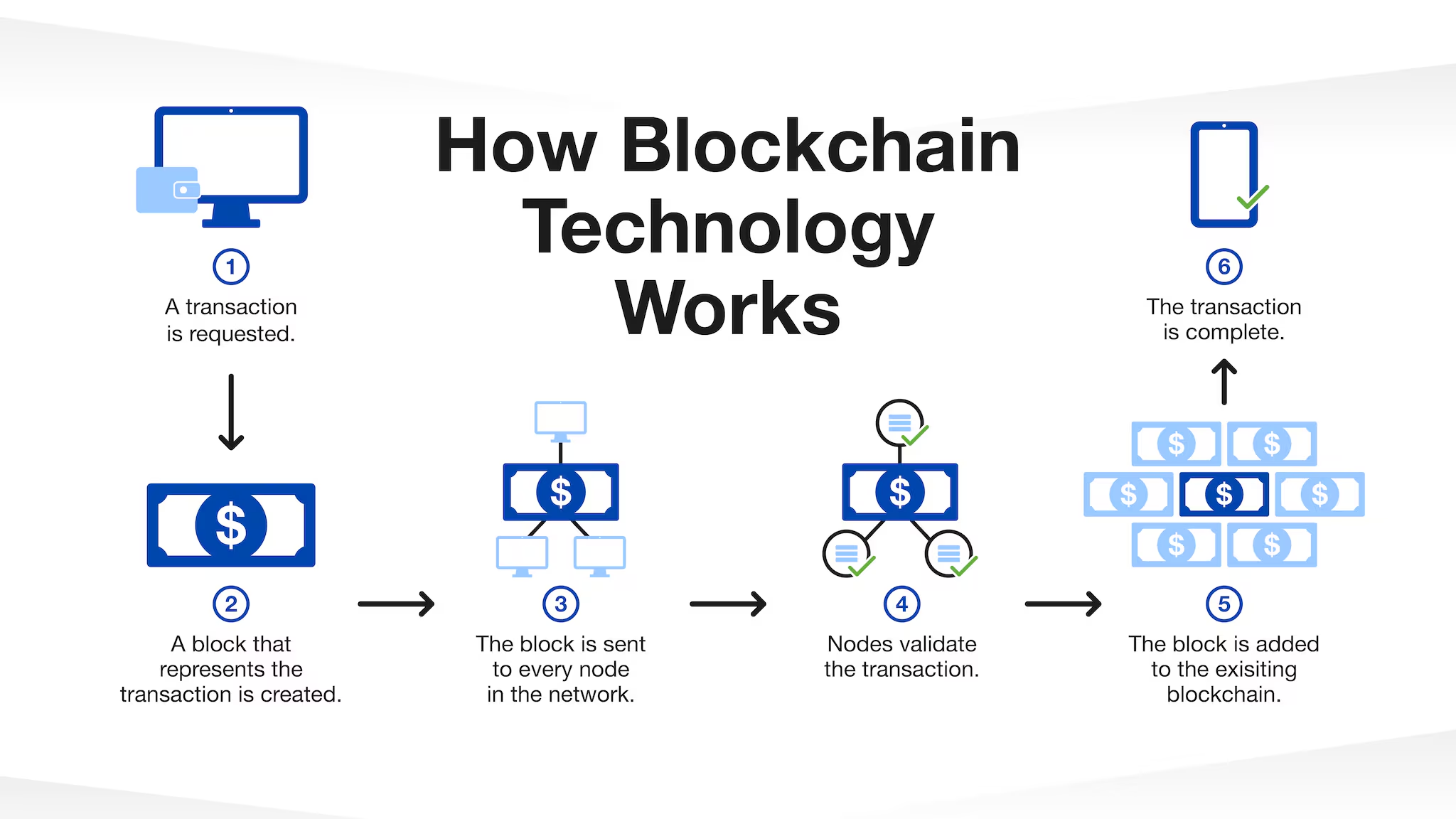
Blockchain Technology
A decentralized, distributed ledger system that securely records transactions in linked blocks, ensuring transparency, immutability, and resistance to tampering. (Bitcoin)
Web of Trust
A decentralized trust model where individuals validate each other’s identities through mutual endorsements, commonly used in PGP encryption (where users sign each other keys)
Root of Trust
A trusted, foundational component (hardware or software) that anchors security in a system, serving as the base for all trust decisions and cryptographic operations. (Example: TPM (Trusted Platform Module))
Private Certificate Authority
An internal CA operated by an organization to issue and manage digital certificates for secure communication within its own network or systems, not publicly trusted outside that environment.
Wildcard Certificate
An SSL/TLS certificate that secures a domain and all its subdomains using a “*” in the domain name (e.g., .example.com covers mail.example.com, shop.example.com, etc.).
SAN
[Subject Alternative Name] An extension in a digital certificate that allows multiple domain names or IP addresses to be secured by one certificate. a certificate for www.example.com could also secure mail.example.com, shop.example.com, and example.net. A SAN certificate explicitly lists specific domains or subdomains rather than covering all subdomains automatically (wildcard certificate)
Threat Actor
An individual, group, or entity that conducts malicious activities to compromise or damage information systems or data.
Attributes of Threat Actor
Internal/External, Resources/Funds, Sophistication, etc
Nation-State Actor
A government-sponsored threat actor engaged in cyber operations to advance national interests, often possessing significant resources and capabilities.
APT
[Advanced Persistent Threat] A prolonged and targeted cyberattack by a skilled threat actor aiming to gain and maintain unauthorized access to a network for espionage or sabotage.
Unskilled Attackers
Individuals who carry out cyberattacks without advanced technical knowledge, often relying on readily available tools or methods.
Hacktivisit
Individuals who are hackers with purposes such as political, philosophical, or revenge reasons.
Insider Threats
These individuals tend to be motivated by revenge or financial gain from the organization. Because they are an insider threat they have the organization’s resource at their hands to use to attack.
Organized Crime
Organizations of criminals who are motivated by solely financial gain. These individuals are almost always an external entity, these organizations may have a corporate structure: one doing the hacking, one managing the exploits, another selling the data, and an individual handling customer support especially with one fighting an organization with ransomware. These individuals are very sophisticated and usually have large amounts of capital to fund hacking efforts.
Shadow IT
Use of information technology systems, devices, software, or applications within an organization without explicit approval from the IT department.
Threat Vector (Attack Vector)
A method or pathway used by an attacker to gain access to or infect a targeted system.
Message-Based Vector
A threat vector involving malicious content delivered through messages such as email, SMS, or direct messages, often including phishing or malware.
Phishing Attack
A cyberattack where attackers send deceptive messages with malicious links or attachments to steal sensitive information or deliver malware.
Social Engineering Scam
A manipulation technique where attackers use fake voicemails, messages, or scams like cryptocurrency fraud to trick victims into revealing information or performing actions.
Image-Based Vector
A threat vector using images, such as SVG files containing executable code like HTML or JavaScript, to deliver malicious payloads.
File-Based Vector
Malicious software embedded in files such as PDFs, compressed archives (ZIP/RAR), or Microsoft Office documents with macros to infect systems.
Voice Call Vector
Threats delivered via phone calls, including vishing (voice phishing), spam over IP calls, war dialing, or call tampering.
Removable Device Vector
Threats introduced through USB drives or other removable media that can bypass network security, potentially infecting air-gapped systems.
Vulnerable Device Vector
Exploitation of known or unknown software vulnerabilities in devices or applications that require patching or updating.
Unsupported System Vector
Security risks from outdated systems or software that no longer receive security patches or updates.
Unsecure Network Vector
Security weaknesses within an organization's own network, such as outdated Wi-Fi protocols, rogue access points, or unsecured Bluetooth connections.
Open Service Ports Vector
Risks posed by open TCP or UDP ports on network services that attackers can exploit to gain unauthorized access.
Default Credential Vector
Security vulnerabilities caused by using default usernames and passwords (e.g., “admin”), allowing attackers easy access.
Supply Chain Vector
Threats introduced through third-party vendors or service providers who have access to an organization's infrastructure.
Typosquatting
A type of URL hijacking where attackers register misspelled domain names to impersonate legitimate sites or email addresses, often used in social engineering attacks like pretexting to steal personal information. (professormesser.com example)